Akira Ransomware Analysis Origins Tactics and Detection Strategies
Table of Contents
- What is Akira Ransomware? An Overview
- Tactics, Techniques, and Procedures (TTPs) Used by Akira
- Analyzing Akira Ransomware Samples
- How to Detect Akira: Threat Hunting Approaches
- Wrapping Up: Key Takeaways on Akira Ransomware
- Akira Ransomware in the MITRE ATT&CK Framework
- Indicators of Compromise (IoCs) for Akira
What is Akira Ransomware? An Overview
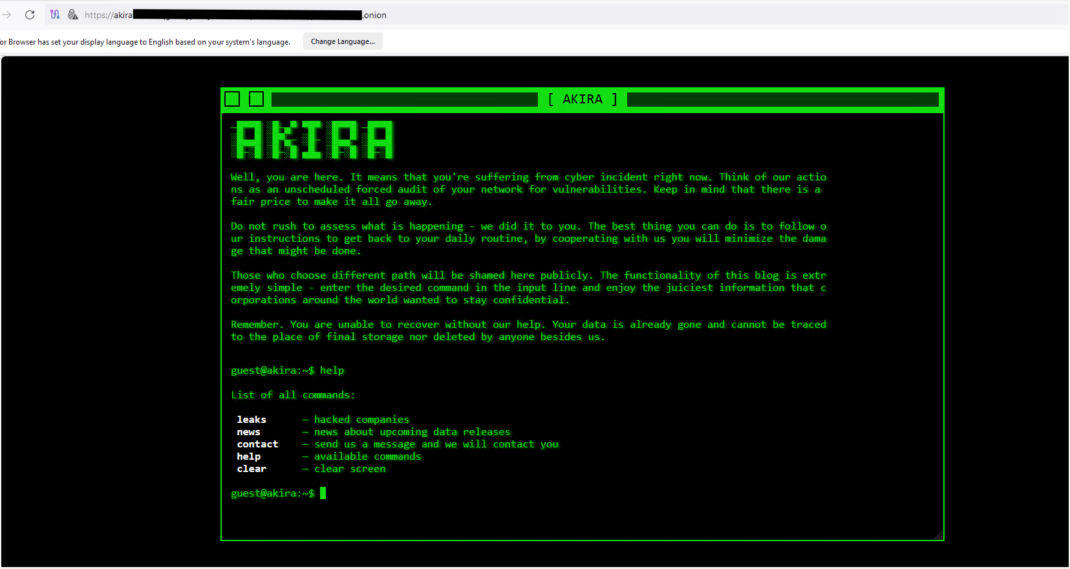
Akira is a prolific ransomware that has been operating since March 2023 and has targeted multiple industries, primarily in North America, the UK, and Australia. It functions as a Ransomware as a Service (RaaS) and exfiltrates data prior to encryption, achieving double extortion. According to the group’s leak site, they have infected over 196 organizations.
When looking at the history of Akira, one must go back to the Conti group. They suffered a massive leak that divulged their source code, chat logs, playbooks, and storage servers in March of 2022. The group then ceased operations in May 2022. This resulted in many of its members and affiliates resurfacing later under distinct brands such as Black Basta, BlackByte, and Krakurt. Akira is another such ransomware that not only has code overlap with Conti but also has had operators that mingled funds with Conti affiliated wallet addresses. This shows that there is a clear overlap between Conti and Akira.
Tactics, Techniques, and Procedures (TTPs) Used by Akira
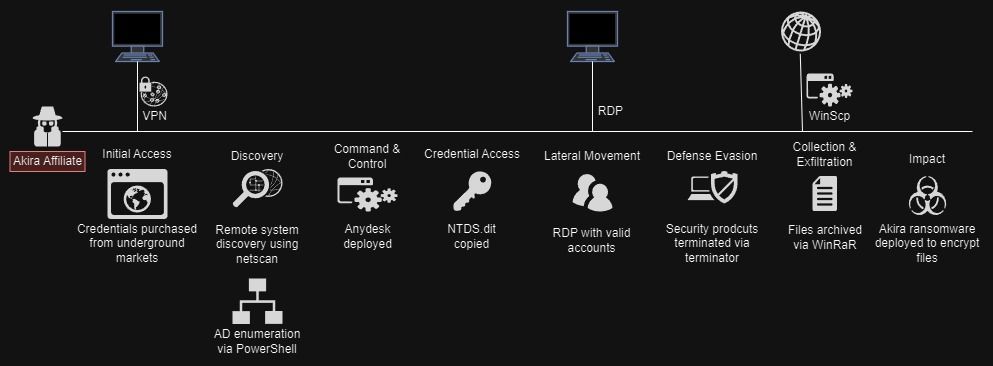
The TTPs used by actors associated with RaaS are similar, and Akira is no different.
A typical campaign starts when Akira affiliates use compromised credentials or vulnerabilities to gain initial access to a victim’s environment.
| Initial Access | Compromised credentials, likely purchased from initial access brokers for entry points that did not use MFA. |
| Exploiting vulnerabilities such as CVE-2021-21972, CVE-2019-6693, CVE-2022-40684 and CVE-2023-20269 |
They then generally perform reconnaissance by gathering details from the Active Directory and scan the network to identify machines for Lateral Movement.
| Discovery | Get-ADUser, Get-ADComputer |
| AdFind | |
| SoftPerfect Network Scanner (netscan.exe) | |
| PCHunter | |
| Advanced IP Scanner | |
| SharpHound | |
| MASScan | |
| reconftw |
The actors have also been observed using several different tools and persistence techniques to expand and maintain their access.
| Command & Control | RSAT-AD |
| SystemBC | |
| NetCat | |
| Anydesk | |
| Radmin | |
| Cloudfare Tunnel | |
| Mobaxterm | |
| Ngrok | |
| RustDesk | |
| SSH |
| Persistence | Scheduled tasks |
| Newly created accounts | |
| Compromised valid accounts |
Credentials are dumped via the following tools and methods.
| Credential Access | Comsvcs.dll dumping lsass |
| Mimikatz | |
| Lazagne | |
| NTDS dump |
Lateral Movement is achieved via RDP with valid accounts or via remote shares.
| Lateral Movement | RDP |
| Network shares | |
| Psexec |
Akira affiliates have used several interesting methods to bypass defenses.
| Defense Evasion | Disabling windows defender and adding exclusions. |
| Userlist registry modification to hide accounts on login screen. | |
| DisableRestrictedAdmin registry modification to allow login without credentials. | |
| Terminator used to perform BYOVD attacks to disable security products. | |
| Creation of new VM to hide adversary behavior. |
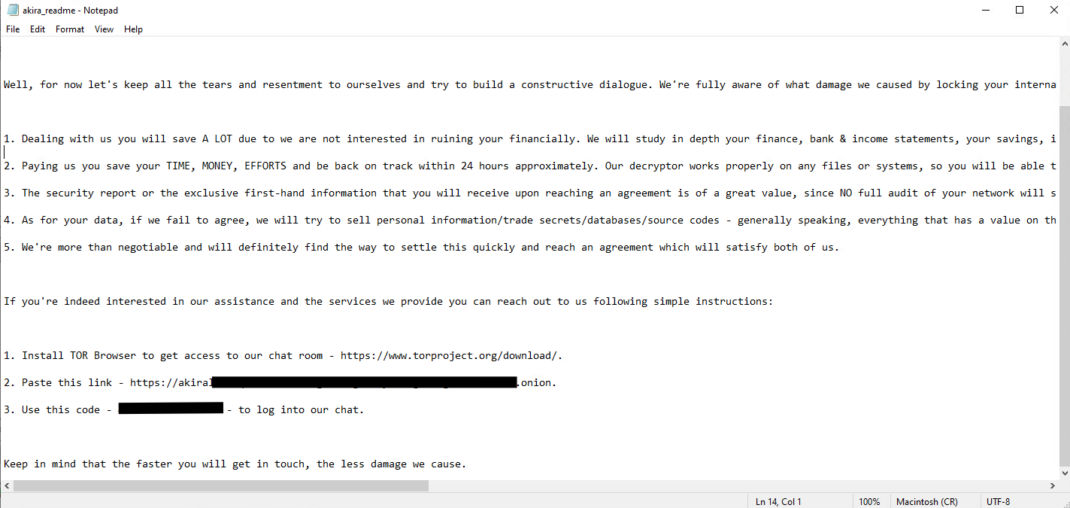
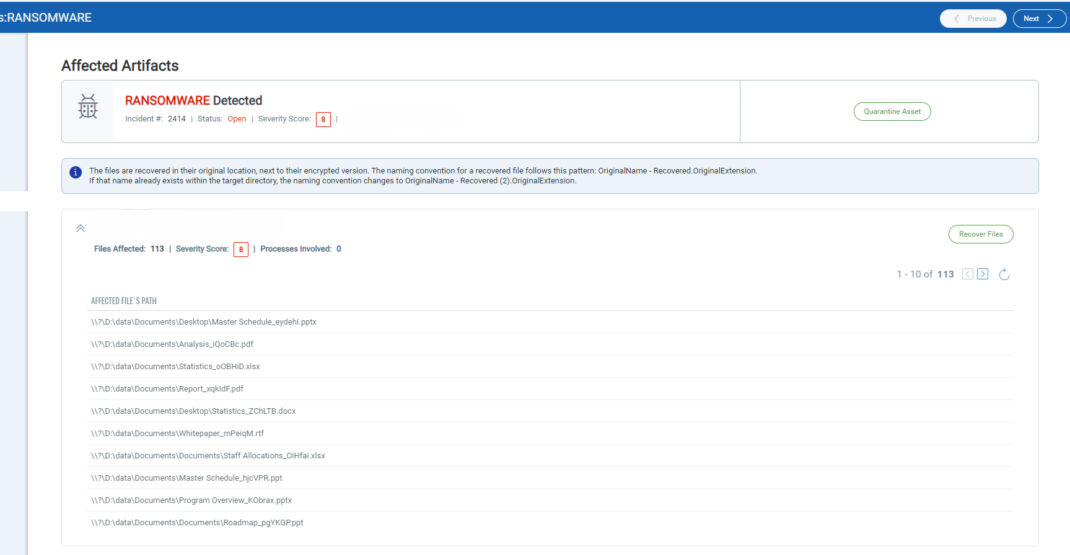
They then collect files, archive them, and exfiltrate them. This data is leaked on Akira’s TOR site if the victims do not make payments.
| Exfiltration | WinScp |
| FileZilla | |
| Rclone |
System backups are also destroyed prior to data encryption.
| Impact | Veeam backups deleted |
| Shadow copies deleted | |
| Data encrypted |
Analyzing Akira Ransomware Samples
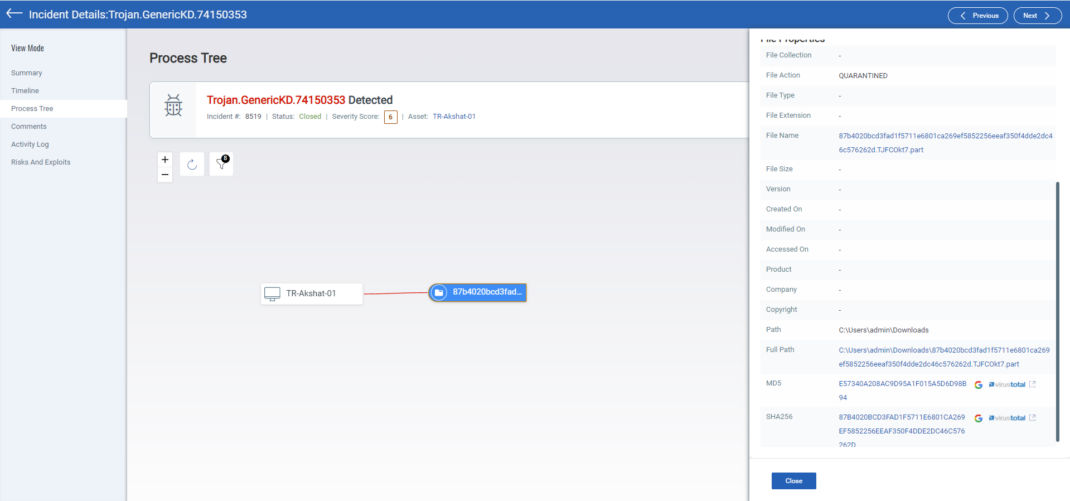
MD5: e57340a208ac9d95a1f015a5d6d98b94
Qualys’s TRU recently acquired a new Akira sample that has been active in the wild. We will focus on some interesting aspects of this sample.
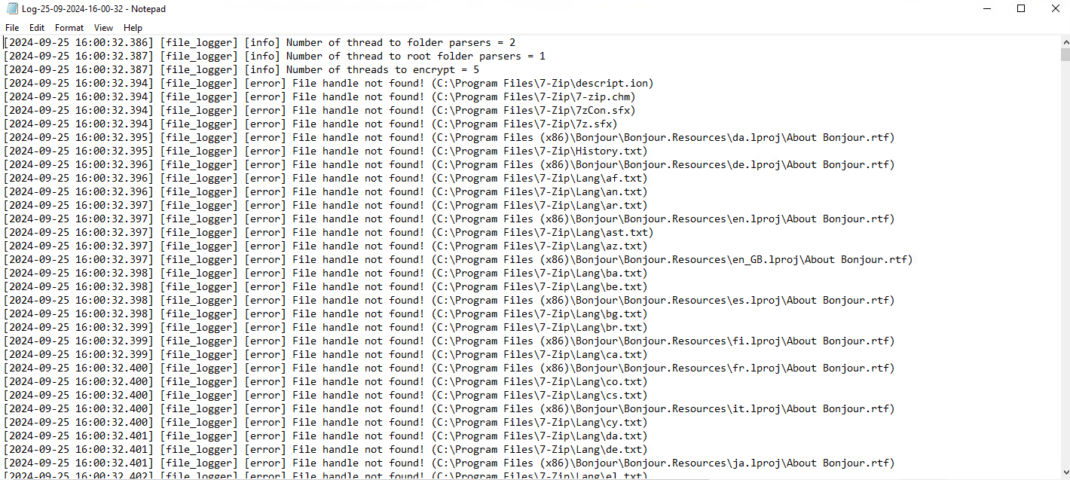
The ransomware creates a log file of its execution of the format Log-date-month-year-hour-minute-second.txt.
Akira takes several command line arguments that define its behavior.
| Argument | Description |
| –encryption_path, -p | Targeted path for encryption. |
| –share_file, -s | Targeted network drive for encryption. |
| -n, –encryption_percent | Defines how much of the victim’s files will be encrypted. |
| -localonly | Only target local files. |
| -e, –exclude | Files to exclude from encryption. |
| -l | Display log file. |
Akira deletes shadow copies by using the command
powershell.exe -Command “Get-WmiObject Win32_Shadowcopy | Remove-WmiObject”
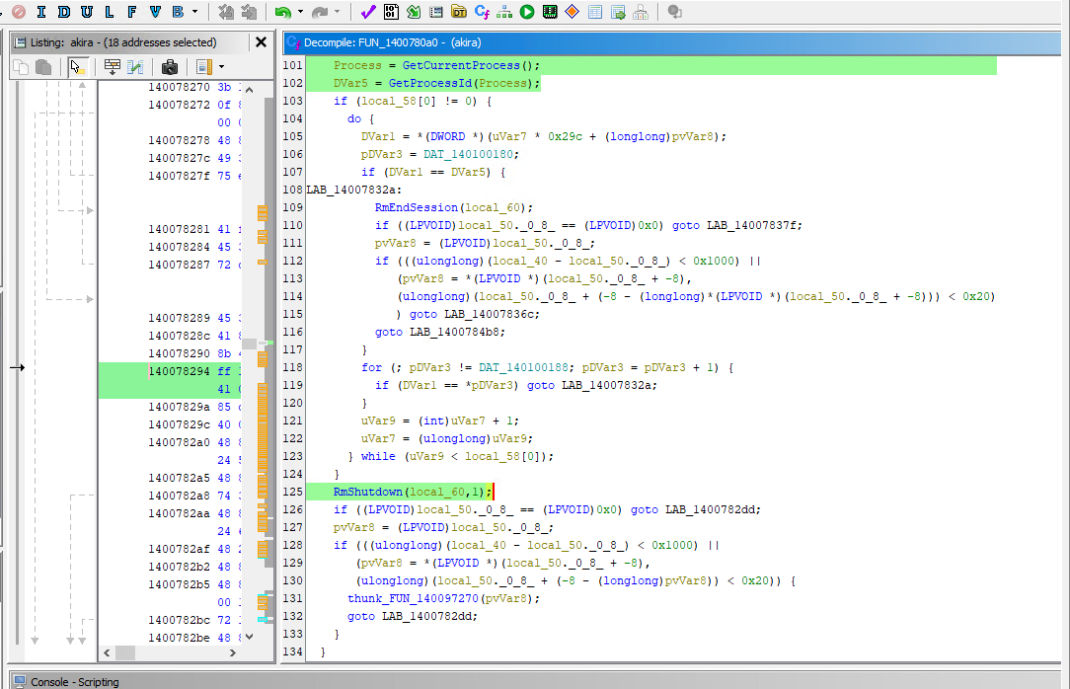
Akira uses the Windows restart manager APIs to kill processes to free up targeted files for encryption.
Like Conti, Akira also uses the ChaCha algorithm for file encryption. Another interesting fact is that the encryption notes contain a code that victims use to log in to Akira’s chat messenger.
How to Detect Akira: Threat Hunting Approaches
Qualys’s EDR & EPP offering provides comprehensive coverage against advanced threats. Akira is detected and quarantined as soon as it is downloaded on the victim’s machine.
Qualys also provides advanced ransomware protection that prevents encryption of personal or sensitive files by automatically creating backup files that are restored after the malware is blocked.
Qualys’s EDR also has several behavioral detections to identify such threats. Existing customers can use the following Threat Hunting QQLs to search their environment for Akira TTPs.
| Description | Query |
| PowerShell deleting shadow copies. | mitre.attack.technique.id:”T1490″ and process.name:”PowerShell.exe” and process.arguments:”Win32_Shadowcopy” |
| All T1490 tagged events in the last 7 days. | mitre.attack.technique.id:”T1490″ and event.dateTime:[now-7d .. now-1s] |
| All T1486 tagged events in the last 7 days. | mitre.attack.technique.id:”T1486″ and event.dateTime:[now-7d .. now-1s] |
| Remote access tool activity in the last 3 days | mitre.attack.technique.name:”Remote Access Software” and event.dateTime:[now-3d … now-1s] |
| New user creation via net | process.name:”net.exe” and process.arguments:”user” and process.arguments:[“/dom”,”/add”] |
Wrapping Up: Key Takeaways on Akira Ransomware
RaaS has emerged as a significant threat in the landscape because it enables even low-skilled actors to deploy highly sophisticated ransomware attacks. Akira continues to steadily result in more victims as it continues to spread. Organizations should secure their perimeter by using defenses like multi-factor authentication (MFA) and rely on an EDR product to protect against such threats on the endpoint.
Akira Ransomware in the MITRE ATT&CK Framework
| Technique | ID |
| Exploit Public-Facing Application | T1190 |
| External Remote Services | T1133 |
| Valid Accounts | T1078 |
| File and Directory Discovery | T1083 |
| Remote System Discovery | T1018 |
| System Information Discovery | T1082 |
| Hide Artifacts: Hidden Users | T1564.002 |
| Hide Artifacts: Run Virtual Instance | T1564.006 |
| Remote Services: Remote Desktop Protocol | T1021.001 |
| OS Credential Dumping | T1003 |
| Archive Collected Data | T1560 |
| Remote Access Software | T1219 |
| Automated Exfiltration | T1020 |
| Data Encrypted for Impact | T1486 |
| Defacement: Internal Defacement | T1491.001 |
Indicators of Compromise (IoCs) for Akira
| Name | Indicator |
| Akira | e57340a208ac9d95a1f015a5d6d98b94 |
| Akira | e8139b0bc60a930586cf3af6fa5ea573 |
| Akira | a1f4931992bf05e9bff4b173c15cab15 |
| Akira | 08bd63480cd313d2e219448ac28f72cd |
| Akira | 4aecef9ddc8d07b82a6902b27f051f34 |
| Akira | ab9e577334aeb060ac402598098e13b9 |
Subscribe to the Qualys blog to get notified of the latest threat intelligence, vulnerabilities, and cybersecurity updates.