December 2013 Patch Tuesday Preview – Update
Update: Microsoft confirmed the fix for the TIFF 0-day and also that the local 0-day will not get an update next week. Best defense is to update your Adobe Reader installation.
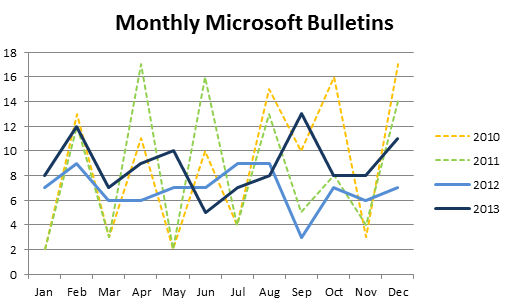
Original: Today, Microsoft has pre-announced this year’s last Patch Tuesday lineup. We will have 11 security bulletins covering Internet Explorer, Windows operating systems and Microsoft Office software. This brings the overall count of security bulletins for 2013 to 106, up quite significantly from last year’s count of 83, but roughly in line with 2011 (100 bulletins) and 2010 (106 bulletins). Microsoft has also maintained the more continuous release of bulletins started in 2012 with an average of just under 9 bulletins per month rather than the more bursty bi-monthly nature of previous years. The steady, more predictable release cycle is helpful to IT administrators as it helps them prepare for the workload necessary for each Patch Tuesday.
There were a significant number of 0-day vulnerabilities this year, mostly centered around Internet Explorer, which had 0-day fixes in January with MS13-008, in March with MS13-021 and October with MS13-080, plus the ActiveX-based 0-day fixed in November with MS13-090. Currently there are two open 0-days: one in Windows and Microsoft Office in the TIFF graphics library documented in the beginning of November as KB2896666; and a local 0-day in the Windows Kernel that Microsoft acknowledged in KB2914486 just a week ago on November 27. Both have workarounds available that we recommend implementing.
Microsoft blogged that the TIFF 0-day will get addressed with the patch in Bulletin #1 next week, but that they are still working on a patch out for the local Windows 0-day. The best defense at the moment is to close the currently known attack vector – a patched vulnerability in Adobe Reader – by updating to the latest patch level of that product that is APSB13-25, but at least APSB13-15.
Regarding 0-days, Microsoft has consistently pointed out that the additional security toolkit EMET (Enhanced Mitigation Experience Toolkit) has been effective against all of the 0-day problems this year. We believe it is a proactive security measure that organizations should evaluate and consider as an additional layer in their defensive measures. EMET is a free tool by Microsoft and in the last year has significantly matured in terms of manageability and deployability.
But back to our upcoming December release: There will be six Remote Code Execution bulletins:
- Bulletin #1 will address the TIFF 0-day in the affected versions of Windows, Office and Lync.
- Bulletin #2 will bring a new version of Internet Explorer.
- Bulletin #3 and #4 are aimed at Windows.
- Bulletin #5 is a server side bulletin for Microsoft Exchange and will probably include the new Outside In library from Oracle that was released during October’s Critical Patch Update.
- Bulletin #6 is for Microsoft Office and is only rated important, but it will still deserve your full attention due to the Remote Code Execution possibilities, most likely through file format vulnerabilities.
The remaining bulletins deal with local elevation of privilege vulnerabilities in Windows and Microsoft Developer Tools, plus an information disclosure and security feature bypass in Office.
Please come back to this blog next Tuesday when we will have more information on the exact nature of each of the bulletins.