OpenBSD Local Privilege Escalation Vulnerability (CVE-2019-19726)

Qualys Research Labs discovered a local privilege escalation vulnerability in OpenBSD’s dynamic loader. The vulnerability could allow local users or malicious software to gain full root privileges. OpenBSD developers have confirmed the vulnerability and released security patches in less than 3 hours.
Qualys Research Labs also provided proof-of-concept exploits in the security advisory.
Vulnerability Details
This vulnerability exists in OpenBSD’s dynamic loader versions of OpenBSD 6.5 and OpenBSD 6.6. It is exploitable in the default installation (via the set-user-ID executable chpass or passwd) and could allow local users or malicious software to gain full root privileges. For more technical details on this vulnerability, please see our security advisory. Also refer to our recently published OpenBSD blog post.
Detecting CVE-2019-19726
Qualys has issued QID 372292 for Qualys Vulnerability Management that covers authentication vulnerabilities in OpenBSD. This QID is included in signature version VULNSIGS-2.4.768-4.
QID 372292 : OpenBSD Local Privilege Escalation Vulnerability
This executes “syspatch -l” command to check for the presence of patch applied on the system.
You can search for this new QID in AssetView or within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid:372292
vulnerabilities.vulnerability.cveId:`CVE-2019-19726`
This will return a list of all impacted hosts.
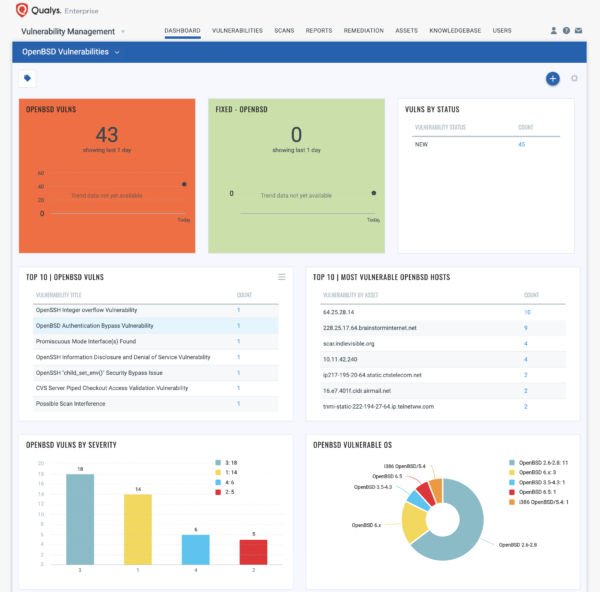
You can also create a Dashboard to track all OpenBSD Vulnerabilities as shown in the template below –
Qualys also provided template information to create OpenBSD Vulnerabilities Dashboard leveraging data in Qualys Vulnerability Management subscription.
Finding Vulnerable Hosts
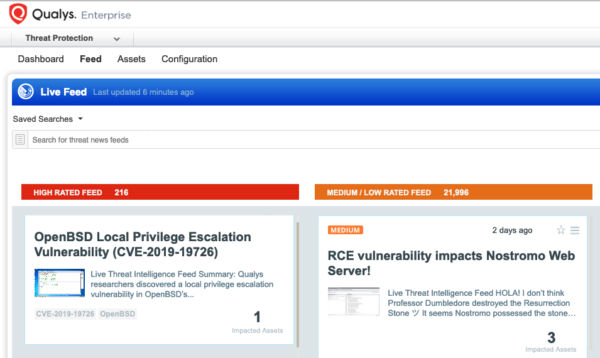
The fastest way to locate vulnerable hosts is though the Qualys Threat Protection Live Feed as seen here:
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Remediation
To remediate this vulnerability, affected OpenBSD users are recommended to install patches for OpenBSD 6.5 and OpenBSD 6.6.
Qualys customers can scan their network with QID 372292 to detect vulnerable assets.