Implementing the CIS 20 Critical Security Controls: Delving into More Sophisticated Techniques
Corden Pharma needed a standardized security program to meet customer requirements. Link3 Technologies wanted to prioritize its network security improvements. Telenet was looking for a road map to implement its ISO-27000 compliance program.
These three companies — a German pharmaceutical contract manufacturer, an IT services provider in Bangladesh and a large telecom in Belgium — all found the InfoSec clarity and guidance they needed in the Center for Internet Security’s Critical Security Controls (CSCs).
They are among the thousands of organizations that over the years have successfully adopted the CSCs, a set of 20 security best practices that map effectively to most security control frameworks, as well as regulatory and industry mandates.
In this blog series, we’re explaining how Qualys Cloud Platform — a single, integrated, end-to-end platform for discovery, prevention, detection, and response — and its Qualys Cloud Apps can help security teams of any size to broadly and comprehensively adopt the CIS controls.
In our first installment, we discussed how Qualys can help organizations slash 85% of cyber attack risk by adopting the first five of the Center for Internet Security’s 20 Critical Security Controls. Last week, we explained the benefits of building upon that “foundational cyber hygiene” with controls 6 to 10.
Now on version 6.1, the CSCs are described by the CIS as “high-priority, highly effective actions” that offer “specific and actionable ways to thwart the most pervasive attacks.” They’re meant to be a starting point for cyber defense improvement using a prioritized approach.
The CSCs, first published in 2008, help organizations prioritize and deal with “the most important things, which are the ones that stop real world attacks,” John Pescatore, a SANS Institute analyst, said in a recent webcast hosted by Qualys.
In today’s installment of our blog series we’ll discuss controls 11 to 15, as we move into the second half of the list, which contains increasingly more sophisticated techniques.
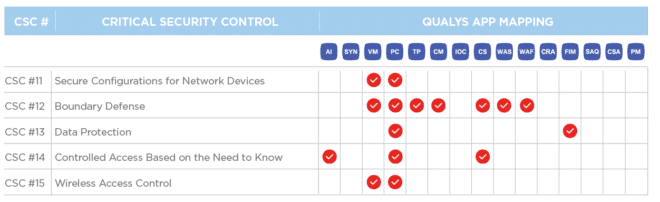
CSC 11
Secure Configurations for Network Devices
Establish, implement, and actively manage (track, report on, correct) the security configuration of network infrastructure devices using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
The default configurations with which vendors ship network infrastructure devices are aimed at simple deployments and ease of use, not security. For example, these devices ship with open services and ports, default accounts or passwords, and support for older, unsafe protocols. When attackers exploit flaws in these devices, they can gain access to networks, redirect traffic on a network, and intercept information.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM continuously discovers and maps each device on the organization’s network, including applications on the perimeter, internal networks, and cloud provider networks, and assesses them for security vulnerabilities. Vulnerabilities can easily be identified and tracked to drive remediation efforts.
Qualys PC provides automated technical control assessment across many network devices from vendors including Cisco, Juniper, and Palo Alto. Customizable out-of-the-box library content based on industry- and vendor-recommended best practices such as CIS Benchmarks and DISA STIG are also provided to fast-track your compliance assessments, or you can establish gold-standard configurations and identify drift from the original hardened configuration settings.
CSC 12
Boundary Defense
Detect/prevent/correct the flow of information transferring networks of different trust levels with a focus on security-damaging data.
Attackers focus on systems that they can reach across the internet, exploit configuration and architectural weaknesses to gain initial access into an organization and then get deeper inside the boundary to steal information or to set up a persistent presence for later attacks. InfoSec teams must control traffic flow through network borders and police content by looking for attacks and evidence of compromised machines.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM can scan remote devices from different network vantage points, including externally, to identify potential openings that put data at risk.
QUALYS CONTINUOUS MONITORING (CM)
Coupled with Qualys CM, recurrent scans can be completed to keep you constantly up to date about new services and ports on internal devices, as well as external devices exposed to the internet.
Adding Qualys TP provides threat intelligence about the latest vulnerability disclosures and maps them to your impacted IT assets whether internal or exposed to the internet. These three apps combined — VM, CM and TP — provide the comprehensive coverage needed to protect your perimeter.
Qualys PC can be used to assess configuration of network devices and firewalls to ensure the boundary is properly protected and help prevent configuration drift for key security settings on such devices. A wide array of out-of-the-box content is available to ensure proper configuration of the perimeter network, which can be customized to fit an organization’s unique needs.
QUALYS WEB APPLICATION SCANNING (WAS) AND WEB APPLICATION FIREWALL (WAF)
Qualys offers a complete solution for web app security with Qualys WAS and WAF, which are natively integrated. With a single, interactive console for web app vulnerability detection (WAS) and attack protection (WAF), you can seamlessly identify and mitigate risks. Qualys WAS is a robust DAST (Dynamic Application Security Testing) product that identifies security holes in web applications, SOAP web services, and RESTful APIs, through continuous web app discovery of HTTP services and detection of vulnerabilities and misconfigurations. Identified vulnerabilities from WAS can be virtually patched in WAF with the push of a button.
QUALYS CONTAINER SECURITY (CS) – BETA
Qualys CS lets organizations discover, track, and continuously protect containers in DevOps pipelines and deployments across cloud and on-premises environments. This helps ensure that the boundary settings of the containers are assessed on a continuous basis.
CSC 13
Data Protection
The processes and tools used to prevent data exfiltration, mitigate the effects of exfiltrated data, and ensure the privacy and integrity of sensitive information.
Since data resides in many places, you need a combination of encryption, integrity protection, and (DLP) techniques to protect it. Care should also be taken to ensure that products used within an enterprise implement well known and vetted cryptographic algorithms, as identified by NIST. Re-evaluation of the algorithms and key sizes used within the enterprise on an annual basis is also recommended to ensure that organizations are not falling behind in the strength of protection applied to their data.
How Qualys Can Help
Qualys PC has a number of out-of-the-box controls for checking the security and permissions on sensitive, critical files and processes, while making sure file transfer options are either restricted or blocked. Qualys PC can also validate that required software such as DLP solutions are in place on critical assets.
QUALYS FILE INTEGRITY MONITORING (FIM)
Qualys FIM monitors and tracks changes to critical files, including changes to important security settings and file attributes to help you detect and track critical changes and incidents, while monitoring the integrity of the sensitive data.
CSC 14
Controlled Access Based on the Need to Know
The processes and tools used to track/control/prevent/correct secure access to critical assets (e.g., information, resources, systems) according to the formal determination of which persons, computers, and applications have a need and right to access these critical assets based on an approved classification.
Organizations should carefully identify and separate their most sensitive and critical assets from less sensitive, publicly accessible information on their internal networks. Once attackers have penetrated such a network, they can easily find and exfiltrate important information, cause physical damage, or disrupt operations.
How Qualys Can Help
Qualys AI can help identify critical systems to ensure they are organized and tracked according to their business purpose. The wealth of inventory data can help ensure that only necessary software is installed for the business purpose to help maintain proper segmentation.
Qualys PC has a number of out-of-the-box controls for checking the security and permissions on sensitive, critical assets (e.g., information, resources and systems in the traditional data centers as well as in the cloud infrastructure) and for making sure access is only provided on a need-to-know basis.
QUALYS CONTAINER SECURITY (CS) – BETA
Qualys CS lets organizations discover, track, and continuously protect containers in DevOps pipelines and deployments across cloud and on-premises environments, ensuring that the data access outside the boundary of the containers is restricted.
CSC 15
Wireless Access Control
The processes and tools used to track/control/prevent/correct the security use of wireless local area networks (LANS), access points, and wireless client systems.
Unsecured access points give attackers convenient entry points into your IT environment, bypassing security perimeters. Attack methods include compromising employees’ wireless devices and using them to enter your network, as well as planting rogue wireless access points in your organization, providing unrestricted access for intruders.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM) AND POLICY COMPLIANCE (PC)
Qualys VM and PC have out-of-the-box content to assess and report on the vulnerabilities and configuration settings of wireless controllers and wireless settings on the systems, to make sure unauthorized connections are disabled, and access is provided in a secure manner.
Stay tuned for the next post in our series, where we will cover the last five controls.
To learn more about how Qualys Cloud Platform can help you drastically reduce your organization’s cyber risk and enhance compliance, download the Qualys Guide to Automating CIS 20 Critical Security Controls.