GDPR Is Here: Put File Integrity Monitoring in Your Toolbox
In this latest post of our series on the EU’s General Data Protection Regulation, we’ll explain how file integrity monitoring (FIM) can be crucial in helping organizations comply with this severe regulation.
GDPR, which went into effect in May and applies to organizations worldwide that handle EU residents’ personal data, provides few details of specific security technologies and processes organizations should adopt.
However, it’s clear from the GDPR text that the regulators expect organizations to demonstrate that they’re doing all they can to protect their EU customers’ personal data from malicious and accidental misuse. For InfoSec teams this means providing a rock-solid security foundation that gives their organizations superior data breach prevention and detection.
File integrity monitoring (FIM) specifically provides security controls in three key areas for GDPR:
- Ensuring integrity of data stored in filesystems
- Protecting confidentiality of data by detecting changes to filesystem access controls
- Detecting breaches
What is FIM, anyway?
File integrity monitoring systems can help you to promptly detect a variety of changes stemming from normal IT activities, compliance and change control violations, or malicious acts such as malware attacks and configuration tampering. FIM systems use snapshot data and real time detection on the endpoints to identify when files on a system are changed, and when necessary, log the file changes so system administrators, compliance teams, and incident response teams can verify the events and determine if the activity was normal, a policy violation, or a sign of compromise.
Aside from compliance and breach detection use cases, FIM can be invaluable in making sure scripts used for automation and critical application configurations are not changed without proper change control and approval. That way, organizations can prevent downtime and enable fast recovery, both key to ensuring availability of critical applications.
How can FIM help with GDPR?

GDPR not only requires that you protect data from breaches of confidentiality, but also requires that you ensure data integrity. This can include a variety of use cases for data stored in filesystems, ranging from protecting the OS and applications, and the tools used for automation, to metadata in the filesystem, or the data itself.
A list of security measures that compliant organizations are expected to implement (see GDPR’s Article 32) includes items where we can see the relevance of FIM, such as:
- the ability to ensure the ongoing confidentiality, integrity, availability, and resilience of processing systems and services;
- the ability to restore the availability and access to personal data in a timely manner in the event of a physical or technical incident;
- a process for regularly testing, assessing, and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing.
This article also stresses that organizations must take into account “the risks that are presented by processing, in particular from accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to personal data transmitted, stored or otherwise processed.”
Let’s look at some examples.
Protecting the integrity of information stored in filesystems
Personal data is usually stored in more complex structures, such as within a relational databases. Whether temporarily storing data records in a filesystem for staging to transmit to a partner, or dumping records out to archives on less expensive media while keeping it available, we need to make sure that data in this state is not changed. This is especially true if it lacks the application layer controls that are in place in the applications and databases where it was originally collected.
Protecting the confidentiality of data
Individual files, data stores, databases, and logs, in addition to OS-related binaries and configurations, are all protected by the OS by leveraging various access control techniques. Identifying changes to permissions or file audit settings is critical to ensuring they are working as intended and not being circumvented by a malicious activity or an insider. Filesystem access controls vary in complexity, but usually change infrequently once in place. Detection of a change to security settings or related metadata is often a serious warning sign that must be verified urgently.
Detection of a breach by identifying changes in binaries
Whether OS binaries, configuration files, or application data, critical files and changes made to them should be reviewed to determine if they are normal activities, change control violations, or if they are potentially malicious in nature. The GDPR has strict data breach notification requirements, and citizens must notify the appropriate authorities within 72 hours of a data breach discovery, and EU residents “without undue delay” (according to Articles 33 and 34). These requirements can vary dramatically from country to country.
While patching and configuration changes are a normal part of the day in the life of all IT professionals, comparing known or approved changes with actual change behavior can shorten downtime from misconfiguration and reduce the impact of breaches by early detection.
Implementing proper controls to detect changes to application code, web content, and scripts used for IT automation
Automation in IT remains on the rise as organizations adopt DevOps to speed delivery of new features to applications and processes. There are more places than ever where malicious code can be hidden — possibly by a disgruntled employee or a financially motivated insider. Once scripts and code are verified, it is important to make sure they remain unchanged when in production, and that any change to this data is closely compared to change control approvals and verified to match the intended content — especially for scripts and automation used for patching systems and distributing configuration files. Whether detecting defacement or preventing back doors into data warehouses, real-time detection is a critical control in a layered defense.
Qualys FIM
The highly scalable Qualys File Integrity Monitoring (FIM) Cloud App can be an integral part of your overall information security program, and a useful tool for your GDPR compliance efforts by helping your organization fulfill its data integrity, access, and protection requirements.
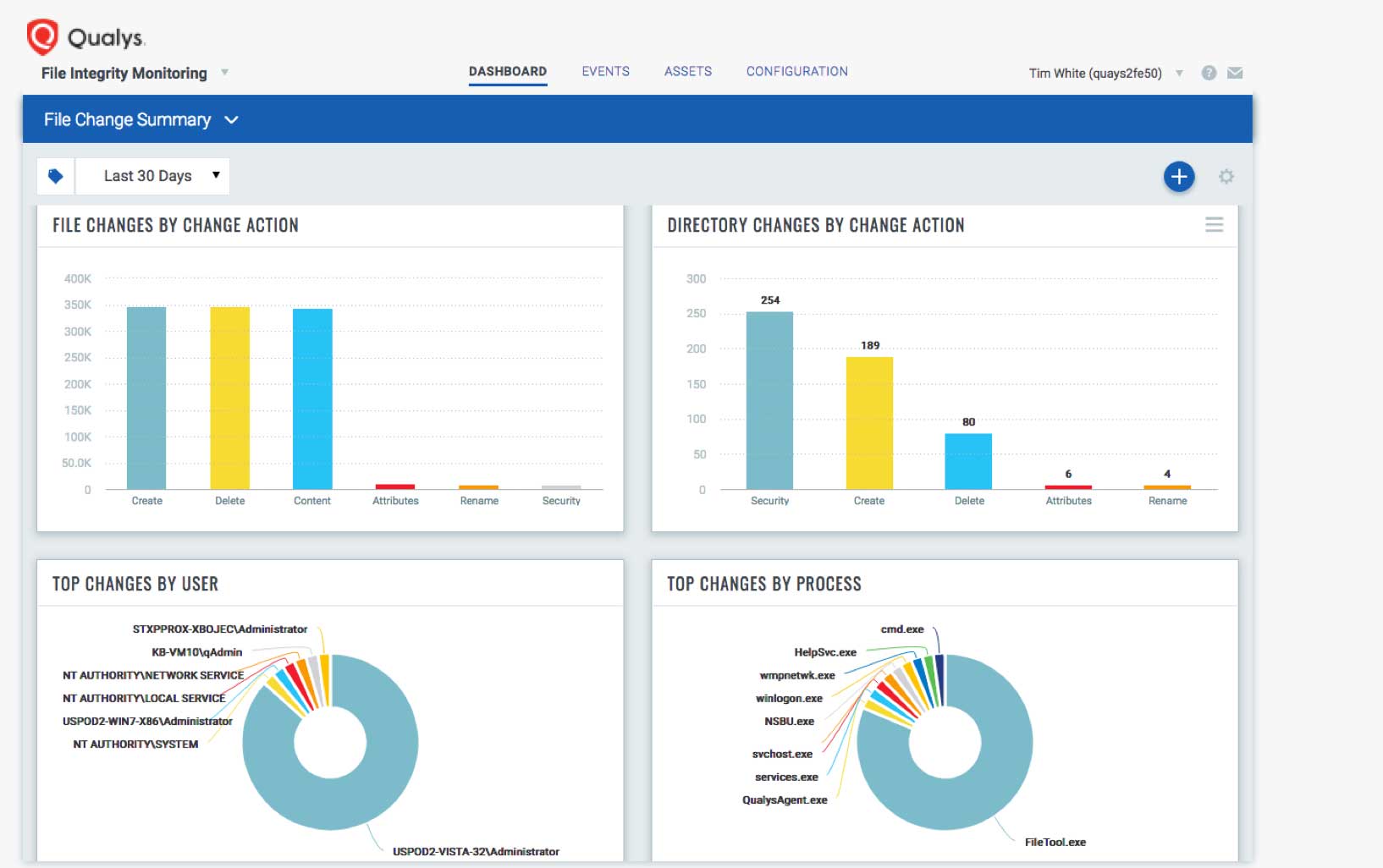
Qualys FIM monitors for changes locally with minimal impact to the endpoint. Qualys Cloud Platform allows you to scale to the largest environments, without having to purchase expensive server software, hardware and storage. Performance impact on the endpoint is minimized by efficiently monitoring for file changes locally using a real-time detection driver and sending the data to the Qualys Cloud Platform. That’s where all the heavy work of analysis and correlation occur. The Qualys Cloud Agent is self-updating and self-healing, keeping itself up to date with no need to reboot.
Because Qualys FIM is based on the Qualys Cloud Platform and shares the same Qualys Cloud Agent as other Qualys Cloud Apps, it allows organizations to easily scale their efforts while consolidating security solutions to reduce the cost and complexity associated with multiple point products.
In our next post in this blog series, we’ll look into the importance of indication of compromise (IOC) within the realm of your GDPR readiness efforts.
(Tim White is a Director of Product Management at Qualys)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
GDPR Is Here: Assess Risk from Vendors and from Internal Teams
GDPR Is Here: Assess the Security Configurations of Your IT Systems