Custom Option Profile To Detect Bash Shellshock
A new option profile in the Qualys Vulnerability Management (VM) Option Profile library can be used to detect instances of the Shellshock vulnerability exposed through the Apache CGI attack vector. This new option profile, called Bash Shellshock Detection, leverages the crawling capabilities available in Qualys Web Application Scanning (WAS) to find Shellshock exposure in CGI scripts in your web applications.
Minor update: The name of this option profile was changed on October 16, 2014 on all three platforms to be more precise: Enhanced Bash ShellShock HTTP-CGI Only Detection.
Why Do I Need It?
The default Qualys VM remote detection for Shellshock uses QID 13038, which identifies the vulnerability in standard locations like /cgi/ and /cgi-bin/. This new option profile gives you more comprehensive coverage by crawling and identifying Shellshock vulnerability in non-standard directory locations within your web application. Specifically, this profile is customized to detect QID 150134 “Shellshock Apache Injection”, described in Using Qualys WAS Scan to Detect ShellShock Vulnerability. The new option profile comes pre-configured with default scanning parameters that make it easier to run out-of-the-box.
If you are using Qualys VM in either a paid subscription or time-restricted trial subscription, this new option profile is the quickest way to get the most comprehensive assessment of your vulnerability to Shellshock. After using this option profile, we recommend you consider getting Qualys Web Application Scanning (WAS), which will give you more control over where you scan for Shellshock vulnerability, and which will also allow you to scan all of your web applications for the many other vulnerabilities that WAS can detect.
For details on the authenticated check (which is not included in this option profile), please see Continuous Protection for Bash Shellshock and Bash Shellshock Command Injection Vulnerabilities.
How Do I Get It?
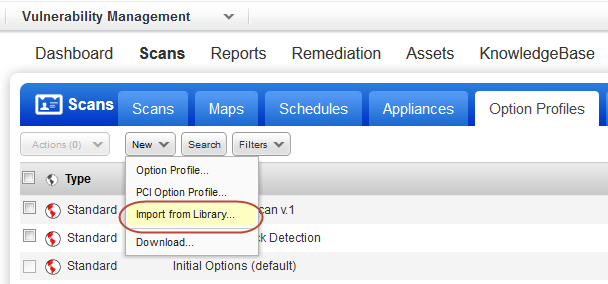
Go to Scans > Option Profiles > New > Import from Library.
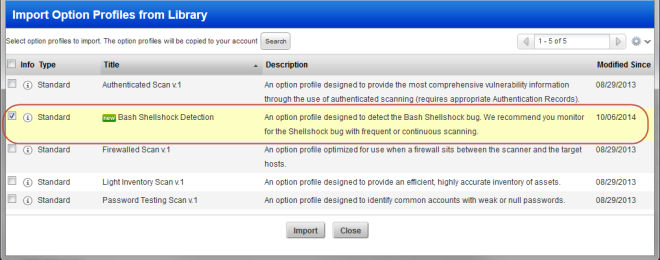
Select the Option Profile “Bash Shellshock Detection” and click Import. That’s it — the option profile is saved to your account and is immediately available for scanning.
Tip – After you import the profile, you’ll notice that you also get a custom search list called “Bash Shellshock Detection” which is used by the option profile.
Can I Edit the Search List?
This is not recommended. The Search List is specially customized for detecting Shellshock QID 150134. Any edits to the Search List will invalidate the customization and the option profile will not work as expected.
Can I Edit the Option Profile?
Yes, you can edit all sections except the “Vulnerability Detection” section. For example, you can add more ports in the Scan>Ports >TCP ports section. Any change to Scans>Vulnerability Detection Section is not recommended. Any edits to the Vulnerability Detection section will invalidate the customization and the option profile will not work as expected.
QIDs Detected
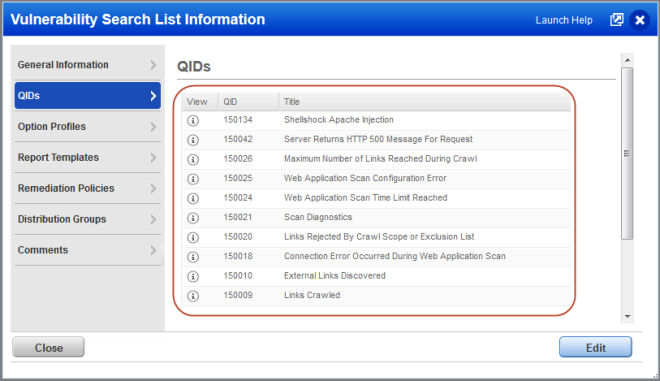
When you use the Bash Shellshock Detection option profile, we’ll scan for the QIDs listed in the Bash Shellshock Detection search list plus basic host information checks. The search list includes QID 150134 “Shellshock Apache Injection” and these information gathered QIDs: 150042, 150026, 150025, 150024, 150021, 150020, 150018, 150010, 150009.
Specifications
Ports scanned: TCP ports 80 and 443.
Authentication: None. Authentication is disabled in the option profile.
Links crawled: A maximum of 300 links.
Availability
The new option profile will be available in the Qualys Cloud Platform
(Application Version 8.1.194-1 and above) on the following dates:
|
Platform |
Availability |
|
Qualys US Platform 1 |
October 9, 2014 |
|
Qualys US Platform 2 |
October 9, 2014 |
|
Qualys EU Platform |
October 10, 2014 |