GDPR: The Stakes Are High and Time Is of the Essence
With the General Data Protection Regulation (GDPR) going into effect in under three months, the countdown clock is fast approaching zero for organizations worldwide that handle personal data of EU residents.

GDPR is a very broad and wide-ranging regulation that requires organizations to obtain a lot of legal advice, and to implement business controls. Although these controls exceed the scope of information security, IT security and compliance are a significant subset of the regulation.
A special challenge for InfoSec teams is GDPR’s lack of details about specific security measures and requirements for protecting EU residents’ data.
“The GDPR regulation is extremely vague and doesn’t give any detailed prescriptive requirements of what the expectations are for data protection, but they’re very far-reaching,” Tim White, a Qualys Product Management Director, said during a recent webcast.
GDPR puts a heavier burden of accountability on organizations, forcing them, among other things, to accommodate significant new rights for individuals. For example, EU residents can request that organizations delete, disclose, correct and transfer their personal information.
To comply with these GDPR “subject access requests,” organizations must know what data they have, where it’s stored, with whom they’re sharing it, how they’re protecting it, and what they’re using it for.
Unfortunately, many organizations are far from ready to comply with GDPR.
GDPR readiness: The main due diligence areas
According to White, organizations should focus on these areas for compliance:
- Identify and classify all personal data that your organization is collecting, and who you’re collecting it from. Make sure that you have obtained consent from these EU residents and that you’re processing the data with GDPR requirements in mind.
- Evaluate internal policies, processes, controls and risk. GDPR requirements are written in such a way that they don’t prescribe specific security controls. Rather, GDPR gives organizations leeway to decide what types of controls are appropriate, based on the criticality of the data and on the risk of exposure.
“How this is going to break out into actual fines once GDPR goes live, and how someone is going to assess compliance, is going to be very subjective,” White said. “We expect there’ll be some refinement to the regulation through the courts and other processes as things move forward.”
For now, organizations must take a complete and comprehensive look at their internal IT and security policies, making sure they have the appropriate rules and segregation in place for the data and are protecting it from unauthorized access.
“Implementing those into your existing apps is going to be a significant challenge, so the sooner you start assessing those processes and controls, the faster you can become compliant,” White said.
- Create security and privacy awareness within your organization via training. “You need to make sure everyone in your organization is aware of the rules related to EU data protection in GDPR and that you have ways of detecting when those rules are being violated,” White said.
- Protect systems from unauthorized access and misuse, not only from external hackers but also from internal abuse.
- Verify your third parties meet requirements, because GDPR makes you responsible for any vendor you outsource data processing to, or any partner you share data with. “You must make sure you include language in your contract with them to make them aware of this and hold them liable if they fail to meet GDPR requirements,” White said.
In addition, organizations must do ongoing and continuous assessments of vendors and other third parties to make sure they’re up to speed with GDPR’s different process controls and data processing requirements. If they fall out of compliance, they can expose your organizations to fines and other legal action.
- Test incident response/data breach plans. Data breach notification requirements are significant, so you must be able to quickly identify when a breach occurs. You also need to have the appropriate channels in place to communicate the right information up to your internal data owners and your data security officers, and meet GDPR’s breach notification requirements.
- Build privacy and security by design into your applications. That way, you’ll have a complete assessment of what types of data you’re collecting, what risks are associated with that data, and what security and technical controls are in place to prevent accidental loss or disclosure of that information. This also involves having the appropriate internal processes for how that data will be handled and used, and building that into the entire process.
Having this visibility into data collection, risk and protection is essential in order to comply with the many requests EU residents can make regarding their personal information, including erasing it (the “right to be forgotten”), correcting it and transferring it. “Imagine if you get a ‘right to be forgotten’ request from a customer,” White said. “That can involve a variety of information” located in different systems and across different business units.
How Qualys can help
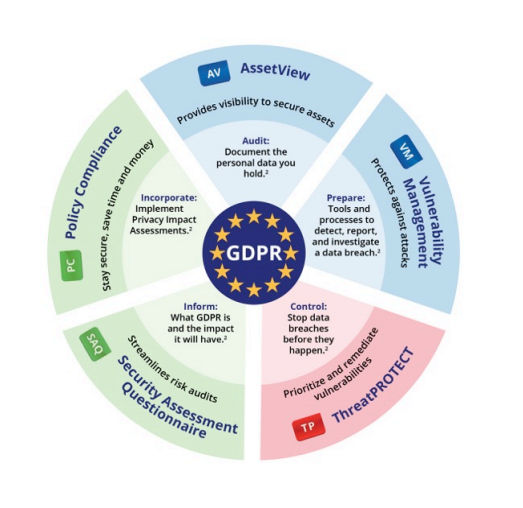
GDPR has very vague and far-reaching requirements for IT and specifically for information security. Implementing these capabilities requires a significant set of tools.
Qualys offers an integrated suite of Cloud Apps that span a broad array of security and compliance functions, and can thus help with multiple elements of GDPR compliance. For example, Qualys can assist you by automating assessment and data gathering; identifying and tracking assets; protecting systems; validating security controls and compliance; and managing vendor risk.
With Qualys, you can gather all that data and see it a “single pane of glass” web-based interface. The data is stored and processed on Qualys Cloud Platform’s highly-scalable architecture that’s hosted in the cloud, always available, self updating and requires very minimal work on your side.
“You can use dynamic tagging to break out and separate out things that are GDPR requirements from other regulatory requirements, and ultimately be able to do the complete end-to-end management of your GDPR readiness from a security perspective through the Qualys Cloud Platform,” White said.
Let’s look at some of these products and their GDPR relevance in some detail.
Security Assessment Questionnaire (SAQ)
With Qualys SAQ, organizations can automate and streamline the process of collecting information about EU residents’ data from both internal teams and external third parties.
Internally, organizations may need to do data privacy impact assessments for individual apps, ensure they have the appropriate records regarding data processing, and document where the data will be stored, where it will be transferred to, and how it will be protected.
Many organizations have hundreds of apps both behind the firewall and exposed via the Internet, so obtaining pertinent information to show GDPR compliance can be a major undertaking.
“It’s a fairly complex task that’ll involve choreographing data collection from dozens or hundreds of individuals inside and outside of your organization,” White said.
With SAQ, organizations can automate assessment and data gathering, perform internal risk and readiness assessments, collect information to classify and validate data, ensure data privacy considerations are applied, and verify procedural controls regularly.
They can do this by building custom questionnaires, or by tapping Qualys SAQ’s extensive content library, which contains a GDPR-specific readiness assessment document, as well as hundreds of templates for assessing vendor risk and for checking compliance with many other audit frameworks such as NIST 800.53.
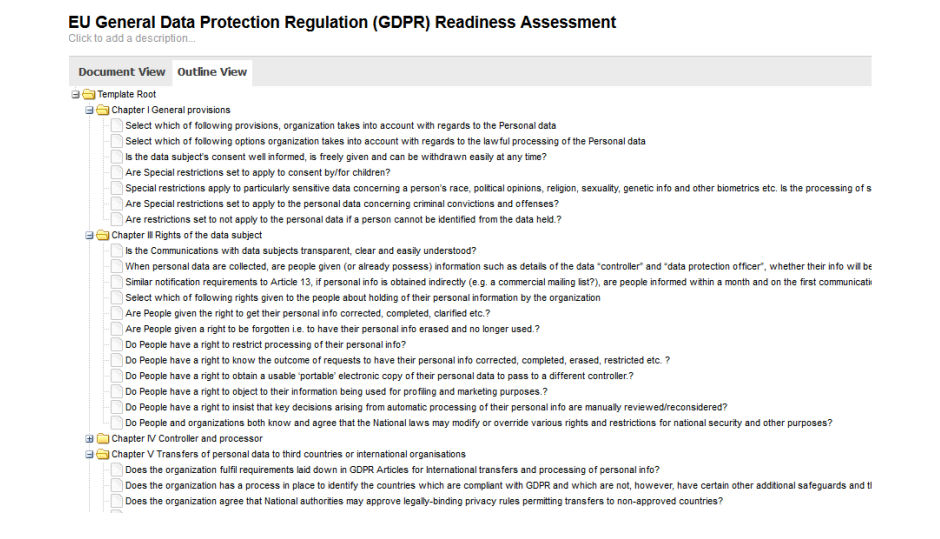
SAQ can also be used to manage vendor risk, which is a major requirement and challenge of GDPR. With SAQ, you can poll your cloud providers, partners, contractors, vendors, suppliers, consultants and other third parties to make sure they’re handling the EU personal information you share with them according to GDPR requirements.
Historically, these polls have been conducted manually, usually by emailing survey questionnaires to the third parties and tracking their responses on spreadsheets.
But distributing questionnaires, collecting answers and aggregating results in this manual fashion is arduous, erratic and costly. For GDPR compliance, you must conduct your third-party risk assessments efficiently, exhaustively, accurately and frequently.
With the cloud-based SAQ, you can scale and accelerate the third-party risk assessment lifecycle, including survey design, response monitoring, data aggregation and report generation.
SAQ automates tedious manual tasks, yields unparalleled accuracy and speeds up campaigns. It lets organizations quickly and precisely identify security and compliance gaps among third parties, as well as internally among its employees.
You can find more information about SAQ and GDPR in this blog post.
Qualys Asset Inventory (AI) and AssetView (AV)
With Qualys AI and Qualys AV, you can identify and track all your IT assets, wherever they reside — on premises, in clouds, and at mobile or remote endpoints — and obtain a comprehensive, unified view of your IT and security data.
Qualys lets you search through all your hardware and software inventory information in seconds, to find systems that may be processing GDPR-related data. For example, you can identify the physical location of assets to determine exactly where data is being held, and identify the applications and software installed on each asset and being used in the processing of confidential and sensitive information. All of this data is presented in a web-based control panel with dynamic and customizable dashboards.
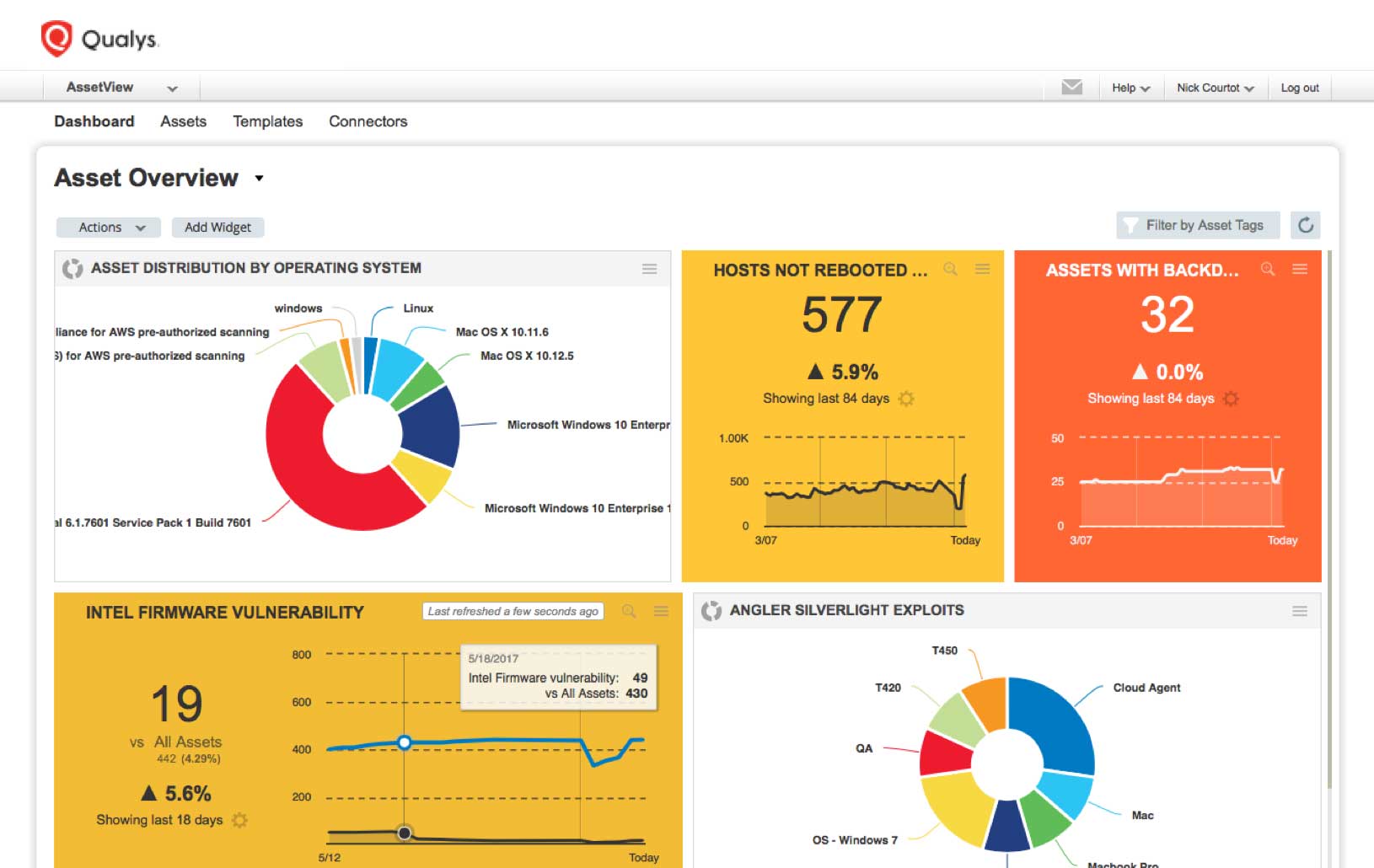
“You can then dynamically organize all your GDPR-related assets into apps and functions so you can apply appropriate security controls leveraging the other capabilities Qualys offers,” White said.
You can find more information about Qualys asset inventory services and GDPR in this blog post.
Qualys Vulnerability Management (VM)
With Qualys VM, you can protect systems against compromise by detecting all the vulnerabilities present in your IT assets, a requirement of just about every regulation.
“Just as with PCI and other regional regulations and requirements, GDPR requires that you do due diligence to protect systems against attack. Vulnerability management is one critical component of that,” White said.
Qualys VM uses both the Qualys Cloud Agents and the Qualys scanners, so you can make sure you have comprehensive vulnerability detection across all of your assets and visibility into the risks that are exposed via those systems.
“Being able to look and verify that you have the appropriate remediation level applied to systems that have confidential or critical GDPR data is very important. That way, you can hold those systems to a higher standard than you hold your internal test systems for example,” White said.
You can find more information about Qualys VM and GDPR in this blog post.
Qualys Threat Protection (TP)
With Qualys TP, you can pinpoint the most critical vulnerabilities impacting your most important IT assets so you can prioritize remediation efforts accordingly. “Everyone knows you need to do vulnerability assessment,” White said. “The challenge is knowing which things to patch.”
Since virtually no organization has the time and resources to patch every single vulnerability on their systems, prioritization is critical, especially with the number of new vulnerabilities disclosed every week.
“Qualys TP gives you the data that you need to know which things are most likely to be exploited, so you can show auditors that you’re doing due diligence and reducing risk in the areas that are most likely to affect data privacy,” White said.
You can find more information about Qualys TP and GDPR in this blog post.
Qualys Web Application Scanning (WAS and Web Application Firewall (WAF)
With Qualys WAS and WAF, which are tightly integrated, you can protect all your web applications by continuously monitoring their security posture and tracking their vulnerabilities.
Qualys WAS has built in templates to let you easily identify and remediate application security and privacy risks, such as the OWASP Top 10. Qualys WAS categorizes your apps to help you prioritize remediation efforts on systems that are most likely to expose confidential information covered by GDPR.
“Web apps are the primary way of delivering services via the Internet, so they need the most focus and security requirements,” White said.
You can use Qualys WAF to virtually patch vulnerabilities detected by Qualys WAS.
You can find more information about Qualys WAS/WAF and GDPR in this blog post.
Qualys Policy Compliance (PC)
With Qualys PC, you can validate security controls and compliance. This cloud app lets you track permissions and privileges for critical files and databases, so you can make sure that only authorized people access to systems with GDPR-protected data.
It also lets you enforce security management best practices and ensure due diligence around those systems. You can also verify data security controls and make sure that systems aren’t being left open, and that you have the appropriate policies in place. Furthermore, Qualys PC gives you the full capability to lock down application settings for web services, web servers and web app services, as well as databases.
You can find more information about Qualys PC and GDPR in this blog post.
The webcast goes into more detail about GDPR requirements and best practices, discusses additional Qualys products, and features questions from the audience.
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr.