New Features in Qualys Vulnerability Management and Policy Compliance
Today we are excited to announce several new features, workflows, and new technology support in Qualys Vulnerability Management and Policy Compliance.
These new features will be deployed as a part of QWEB 10.0 and Portal 3.0 release versions.
Vulnerability Management
Launch and Schedule scans directly against FQDNs, use new tokens to narrow down your vulnerability searches, and group by Real-time Threat Indicators within the new VM Dashboard.
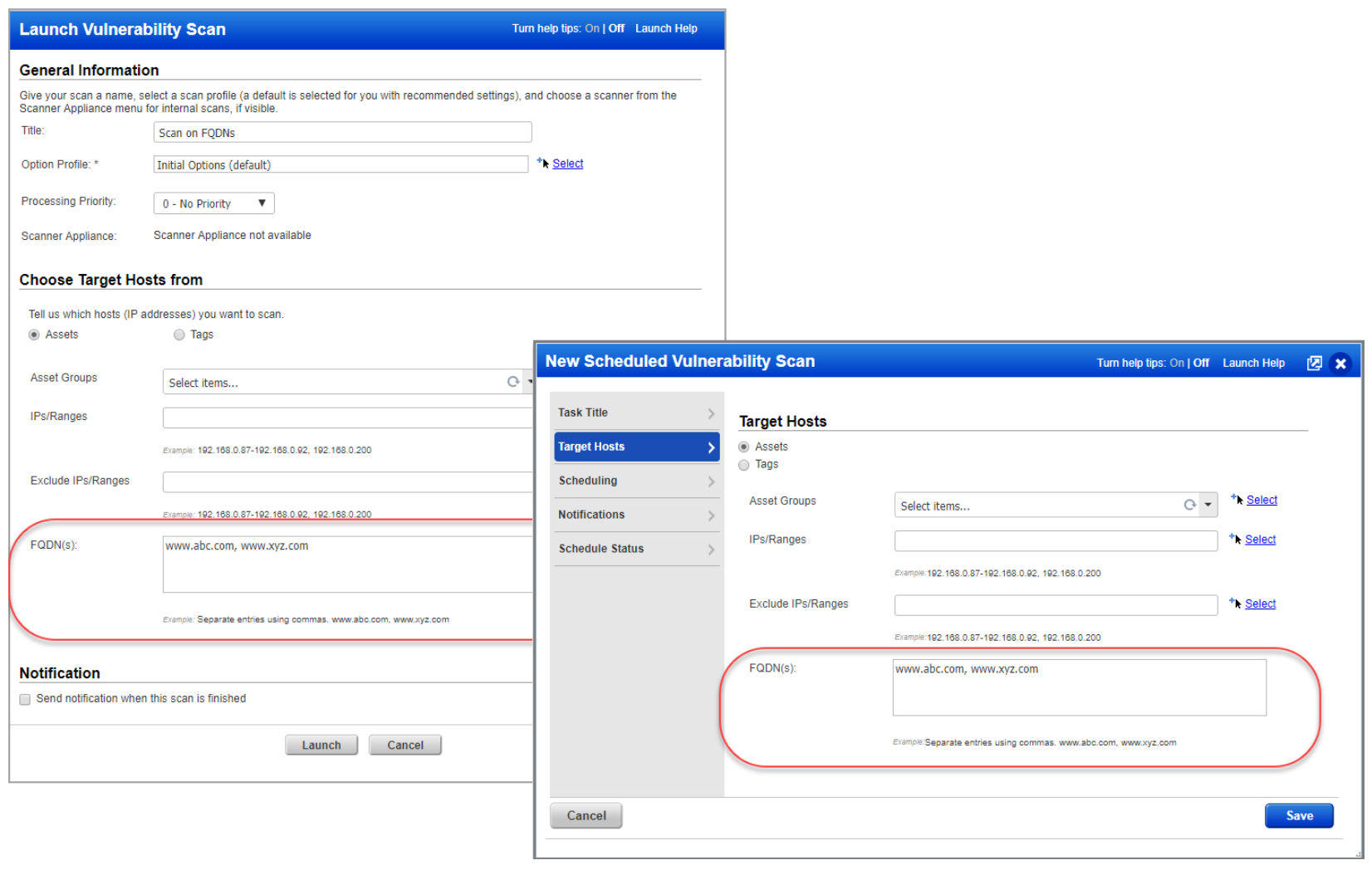
Launch/Schedule Vulnerability Scans on FQDNs: With this release, users can launch and schedule vulnerability scans on Fully Qualified Domain Names (FQDNs). When defining the scan target, users can enter the FQDN in the new FQDN input field.
A user with a Manager’s role can enable this feature by going to Scans > Setup > DNS Tracking and checking the Enable DNS Tracking for hosts option. When launching and scheduling scans, enter one or more FQDNs when defining the target hosts. FQDNs can be entered in combination with asset groups and IPs/ranges but not with asset tags. The scanned FQDN must resolve to an IP address in one’s VM account to successfully scan it and view the results.
Vulnerability Management Dashboard
The following features apply to all subscriptions that are currently using the Vulnerability Management Dashboard beta. With this release, the beta label has been removed and this GA version will be rolled out to all subscriptions over the coming weeks.
“Exists” Searching supported in Tokens: Search Tokens in the Vulnerability Management Dashboard now support the ability to use wildcards (*) to search for hosts or vulnerability detections that have data, such as vulnerabilities.port:* to find all vulnerabilities that were discovered on any open port.
Acceptable Risk Factors (ARF) tokens: Narrow down your vulnerability search query to include only exploitable vulnerabilities with following new search tokens: vulnerabilities.nonExploitableService, vulnerabilities.nonExploitableConfig, and vulnerabilities.nonExploitableKernel. Set these to “false” to filter out vulnerabilities found on non-running kernels, non-running services, and configurations that are not exploitable.
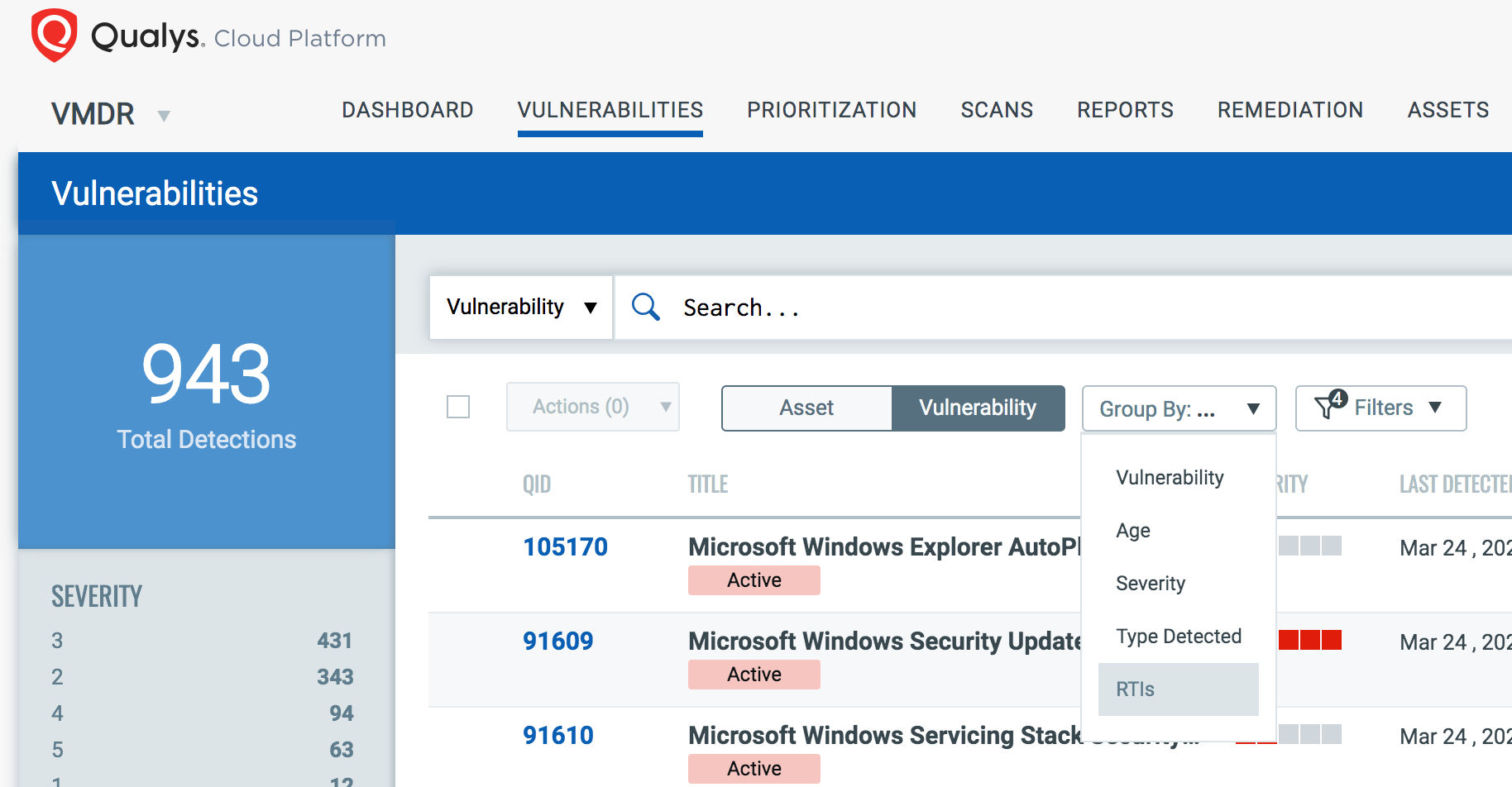
Group by RTI in Search and Widgets: Threat Protection subscribers can now group vulnerabilities by Real-time Threat Indicators (RTI) in both Vulnerabilities search and dashboard widgets, allowing you to see all threats that impact vulnerabilities in your search.
Vulnerability Management and Policy Compliance
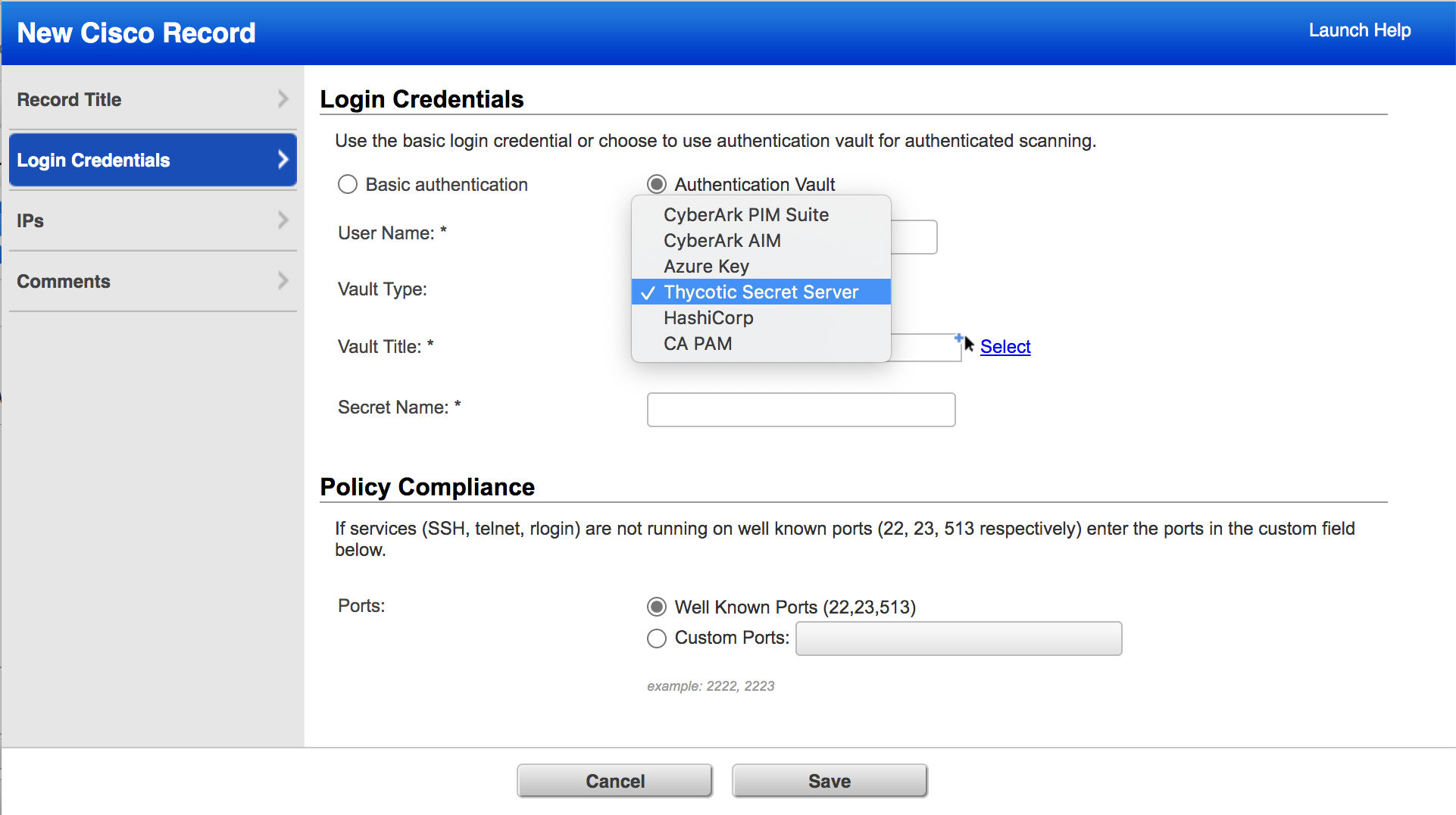
Thycotic Secret Server vault supported in Cisco & Checkpoint Firewall: With this release, users can choose the Thycotic Secret Server vault type in the Cisco and Checkpoint Firewall authentication records.
Policy Compliance / Secure Configuration Assessment
Assess your SharePoint servers and Pivotal Greenplum databases for insecure configurations through Policy Compliance, leverage Posture API support for Secure Configuration Assessment, and merge your Agent data with Scan data for tracking compliance within a single asset record.
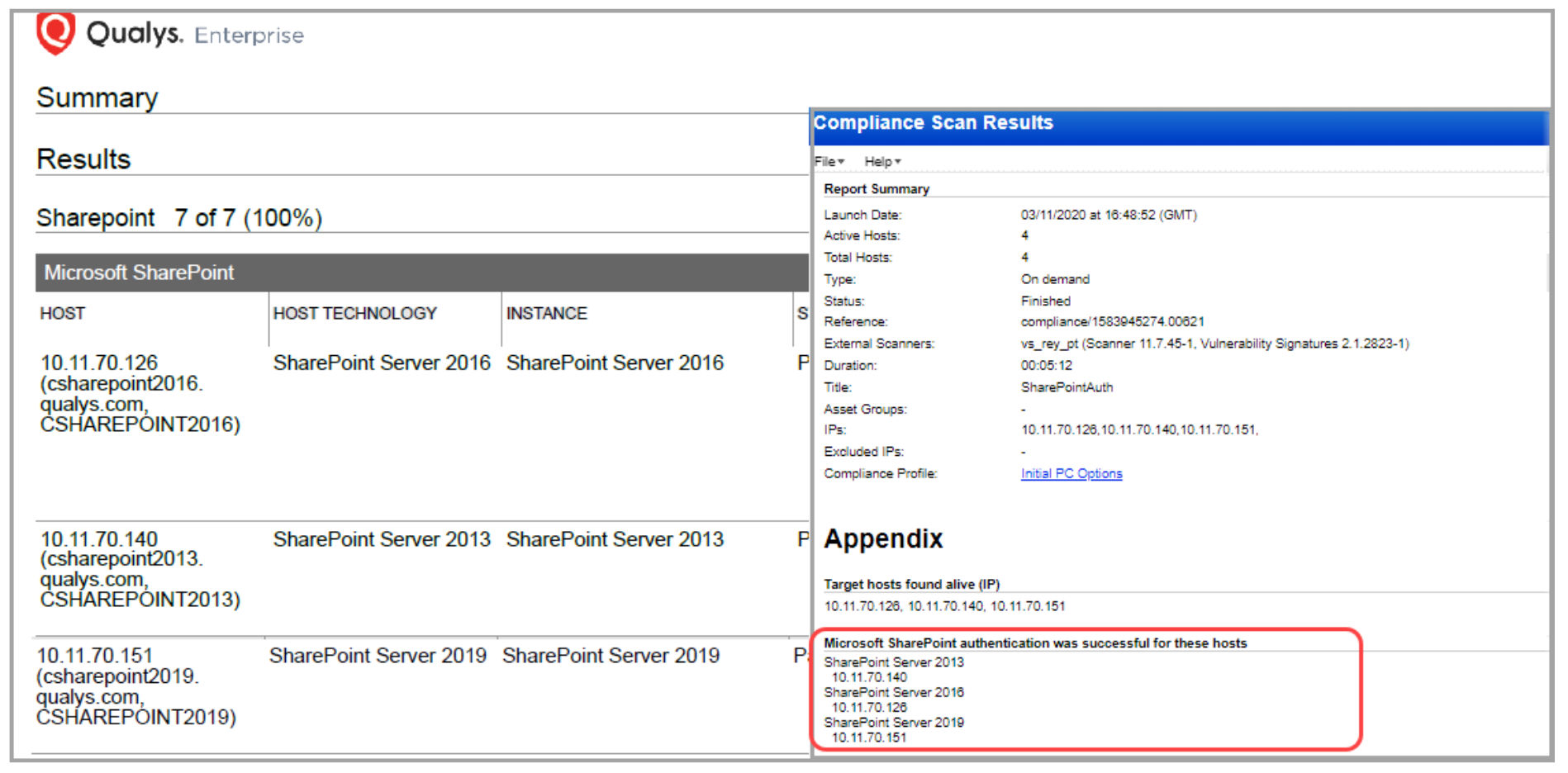
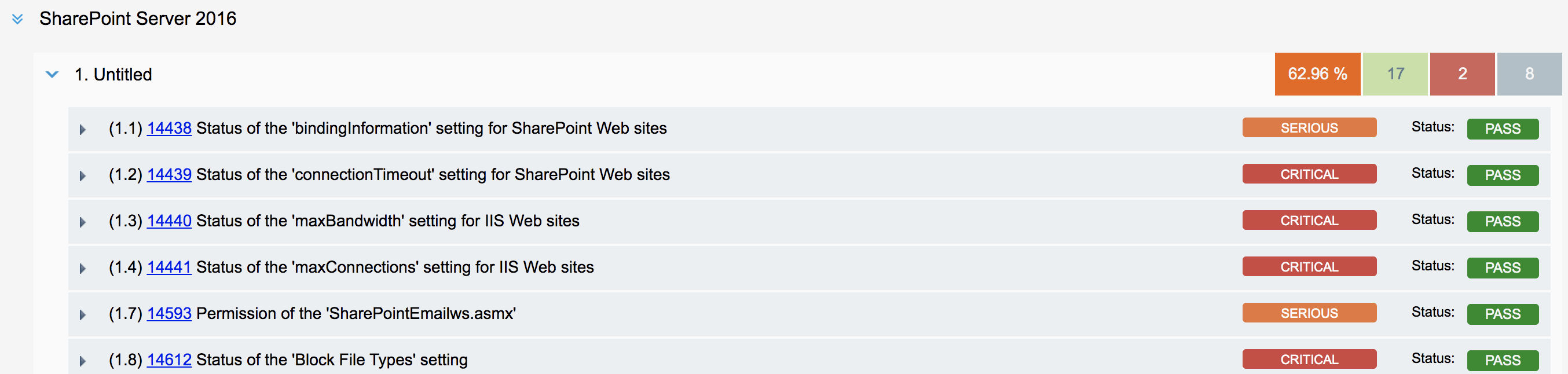
Microsoft SharePoint Authentication Support: Qualys now supports Microsoft SharePoint Server 2010, 2013, 2016, and 2019 for configurations and compliance management.
SharePoint instance will be auto discovered through the Windows Authentication Record. To connect to the MS SQL server, you’ll need to provide information under MS SQL Login credentials in Microsoft SharePoint Record.
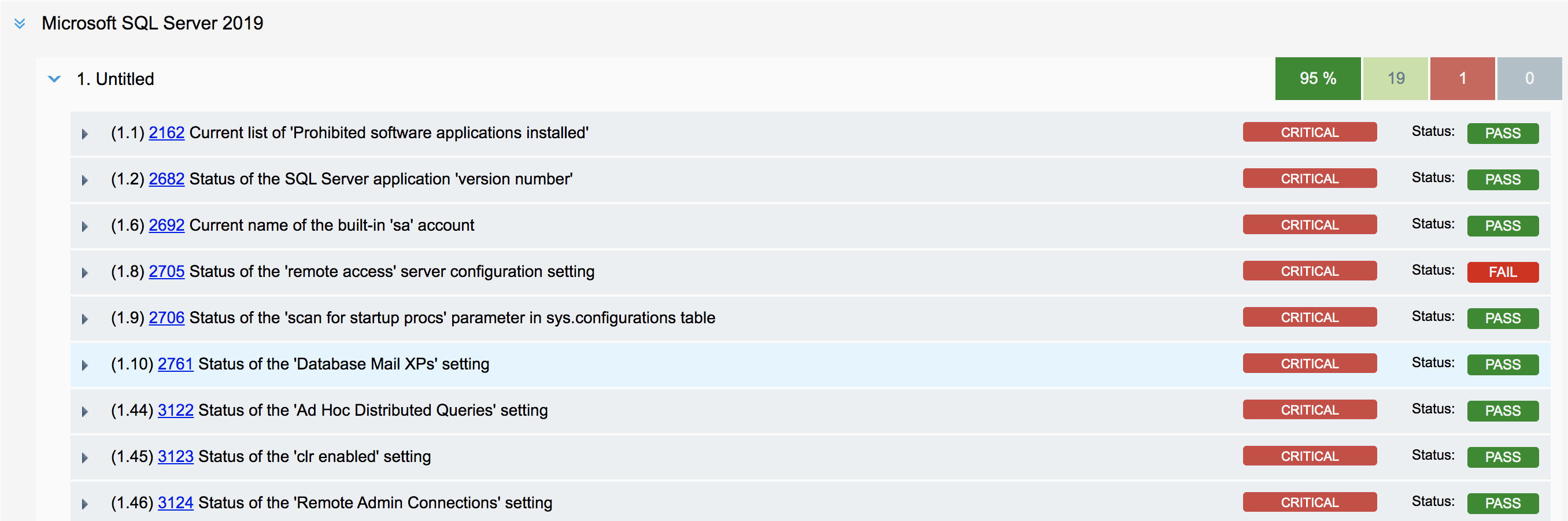
Microsoft SQL Server 2019 Support: Qualys has extended its support for MS SQL Server authentication to include Microsoft SQL Server 2019.
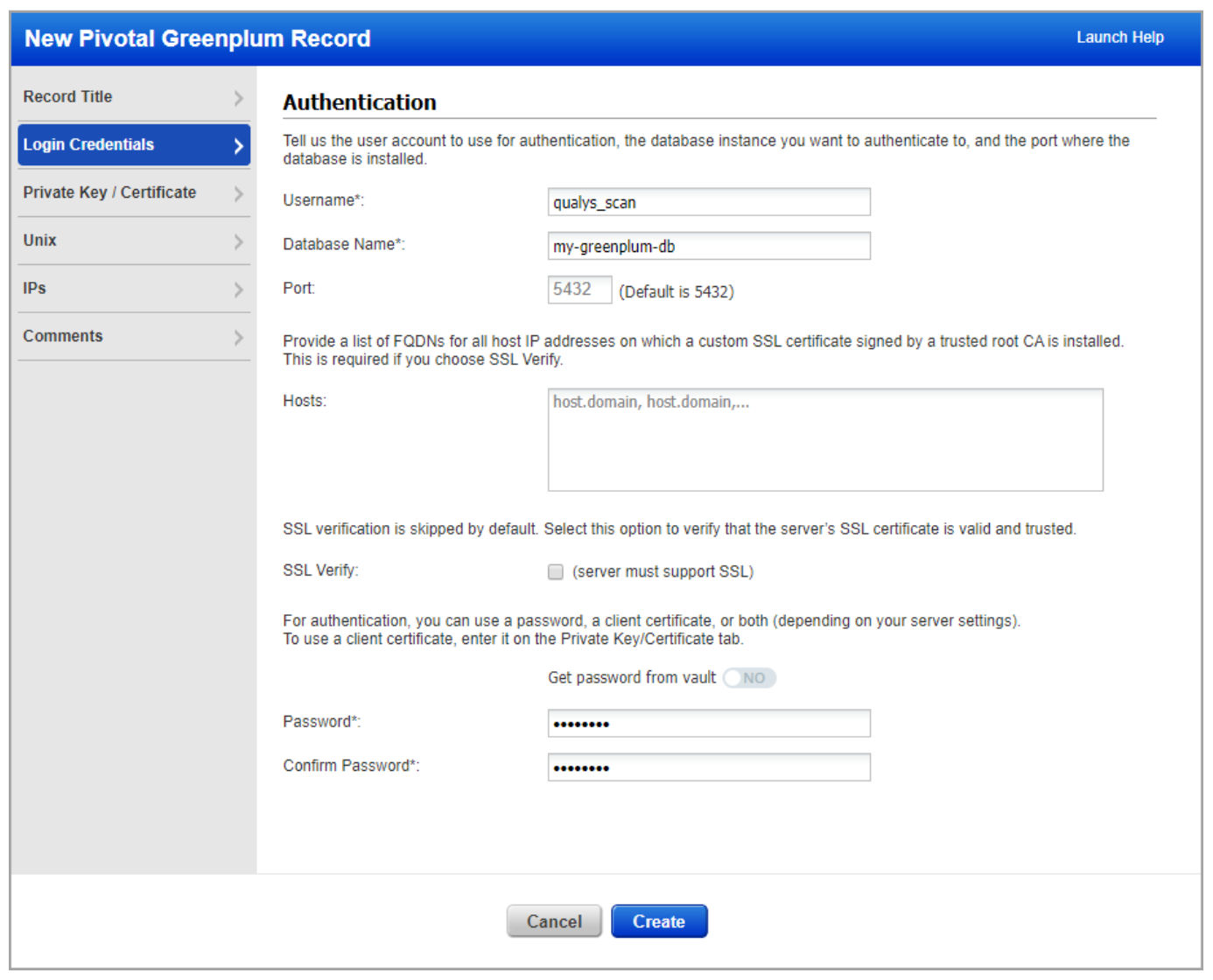
Pivotal Greenplum Authentication Support: Qualys now supports Pivotal Greenplum for versions 5.x and 6.x for configurations and compliance management on Unix hosts.
Note: Users need a Pivotal Greenplum authentication record to authenticate to a Pivotal Greenplum database instance running on a Unix host, and scan it for compliance.
Merge Agent PC Data: Host results from scans and agents are displayed separately in reports and asset views by default. One can choose to merge host results to get unified views of the assets by performing the following steps:
- Run scans using Agentless Tracking
- Enable the Merge Agent Data feature
For PC, prior to this release, there was an additional step required by Support to configure a customer’s account to allow the merging of PC data. This step is no longer required. Now you can set everything up without this additional configuration by Support.
For customers with the PC agent addon, you’ll see the following change when you use this feature: Previously, your VM data from scans and agents was reported on the same asset, which is agent tracked. Your PC data from scans and agents was previously reported on separate assets. Now your PC data will be merged on the same asset, which is agent tracked.
VMDR Customers with SCA now have access to Posture APIs: With an upgrade to VMDR, customers with Security Configuration Assessment (SCA) can run Posture APIs even if they haven’t subscribed to Qualys PC. This is true as long as the subscription has VMDR, SCA, and the API addon. Also, the user making the API call must have API access.
Note: This feature is not available for accounts with VMDR experience and for the ones that haven’t been upgraded to VMDR.
PC APIs are available in these scenarios:
- Customer has PC and the API addon
- Customer has PC, SCA and the API addon
- Customer has VMDR, SCA and API addon
For detailed information, refer to the Qualys API (VM/PC) User Guide.
PostgreSQL Support for Windows: Qualys has extended its support for PostgreSQL 9.x, 10.x, 11.x, and 12.x for configuration and compliance management to include Windows hosts. PostgreSQL on Unix hosts is already supported.
The specific day for deployment will differ depending on the platform. Release Dates will be published on the Qualys Status page when available.
For more details about the above features – please review the release notes. Release notes will be posted as soon as they are available on the Qualys Platform Release Notes page.