Extending your FedRAMP Program to Container Infrastructure with the Qualys Cloud Platform
Following the recent release of the FedRAMP Vulnerability Scanning Requirements for Containers, FedRAMP-authorized systems that make use of containers have one month from March 16, 2021 to submit a plan for compliance with the new requirements. Organizations with a need to certify their services and infrastructure for FedRAMP compliance are looking to extend their existing vulnerability and security program to container infrastructure security assessment, and report their container security posture as a part of FedRAMP Plan of Actions and Milestones (POA&M).
Challenges
FedRAMP defines five core requirements for Cloud Service Providers (CSPs) that use containers to implement their services:
- Container Pipeline: Use of automated tools to build, test and deploy containers to production.
- Image Hardening: Hardening of container images in accordance with National Institute of Standards and Technology SP 800-70.
- Registry Scanning & Pre-Deployment Gating of Images: Container registry monitoring and pre-deployment checks to ensure only scanned and hardened images are deployed to production as running containers.
- Periodic Container, Image Scanning: Either scanning of all container images every 30 days for vulnerabilities prior to deployment, or use of sensors to scan deployed containers every 30 days.
- Container Asset Management & Tracking: Use of unique asset identifiers to track system inventory for every class of image that corresponds to one or more deployed containers to ensure that every production-deployed container does not deviate from the image from which the deployed container originated.
Taken together, adherence to these requirements is very difficult for an organization to implement from scratch. This is due to the need for dedicated tools to meet multiple requirements – inventory of assets from multiple tools and unified reporting/management of the same. And now these tools need to be FedRAMP-compliant/authorized as well. Organizations are confronted with a need for a comprehensive product that can be leveraged to perform the required activities and produce evidentiary results so that assessors may verify FedRAMP compliance.
Leveraging Qualys for Compliance with FedRAMP Container Requirements
Today many organizations leverage the Qualys Cloud Platform to continuously assess FedRAMP requirements for asset inventory, vulnerability management, compliance, and file integrity monitoring in a unified manner. Now they can also leverage Qualys Container Security (CS), natively built on the Qualys Cloud Platform, to continuously assess new FedRAMP requirements for container security. Qualys CS makes the assessment and reporting required for POA&M seamless and unified across their hybrid infrastructure.
Qualys Container Security offers the following services which allows Cloud Service Providers (CSPs) to maintain their compliance requirements:
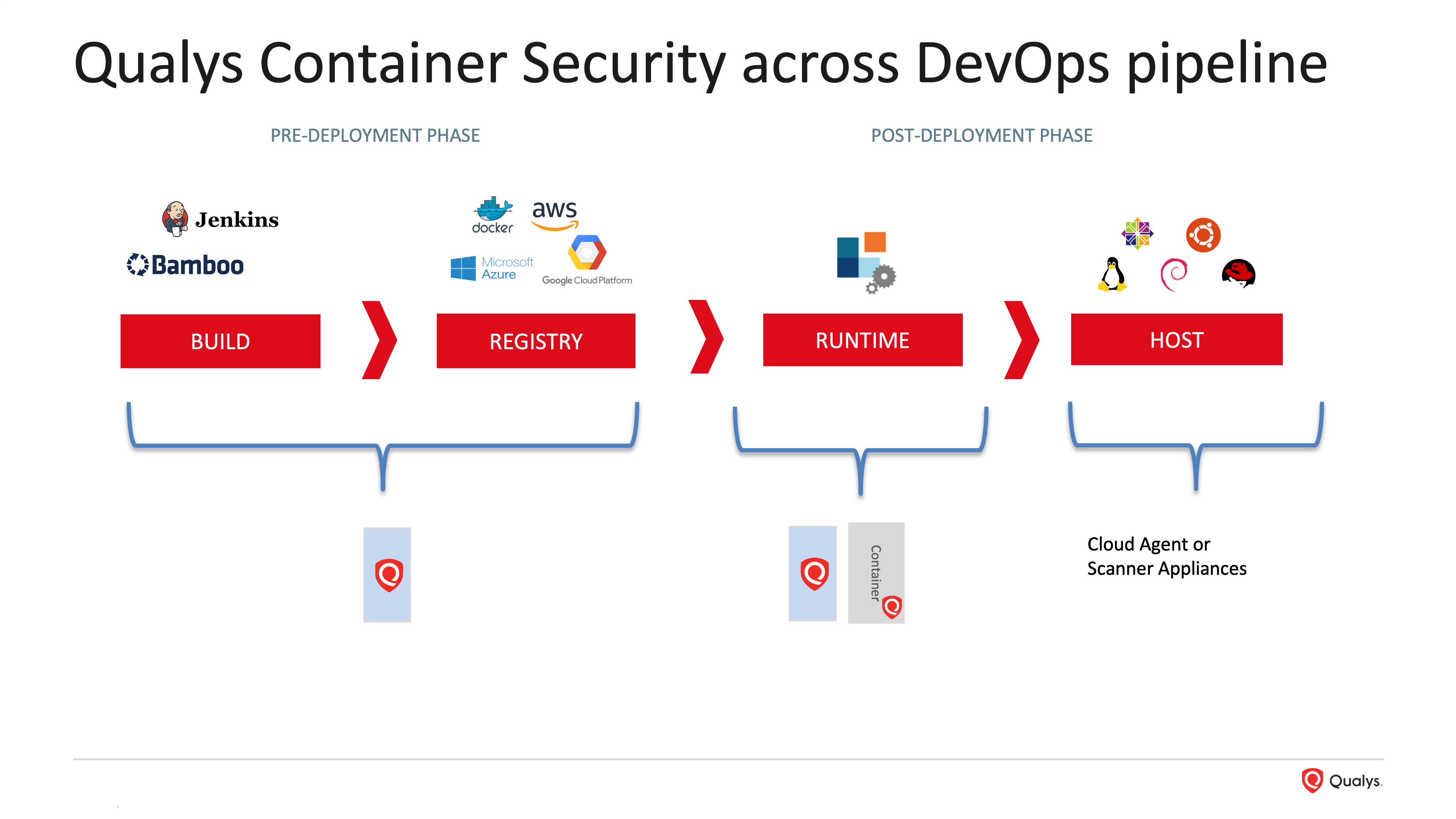
1. Container Pipeline
Qualys Container Security (CS) offers lightweight sensors to non-intrusively scan container images, running containers across the Build-Ship-Run container lifecycle. Qualys provides this capability across a wide diversity of the evolving container ecosystem (standalone Docker-based, self-managed/cloud-provider orchestration environments like Kubernetes, container runtimes like Docker, containerd, CRI-O). Overall, this allows customers to scan both images at rest and running containers for security posture (vulnerabilities, misconfigurations). Additionally, with lightweight in-container instrumentation, Qualys CS offers the ability to monitor and prevent container drift.
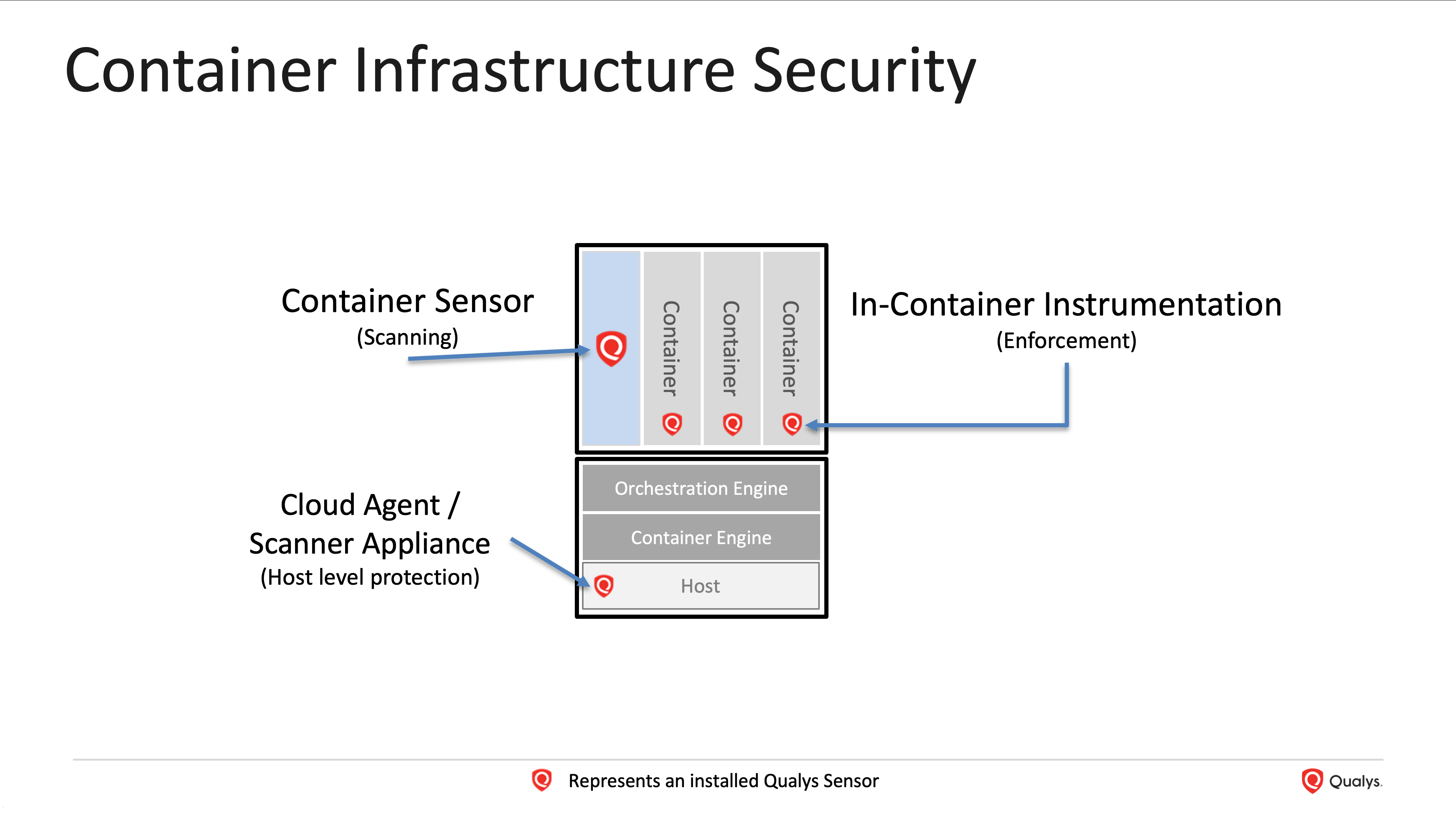
2. Image Hardening
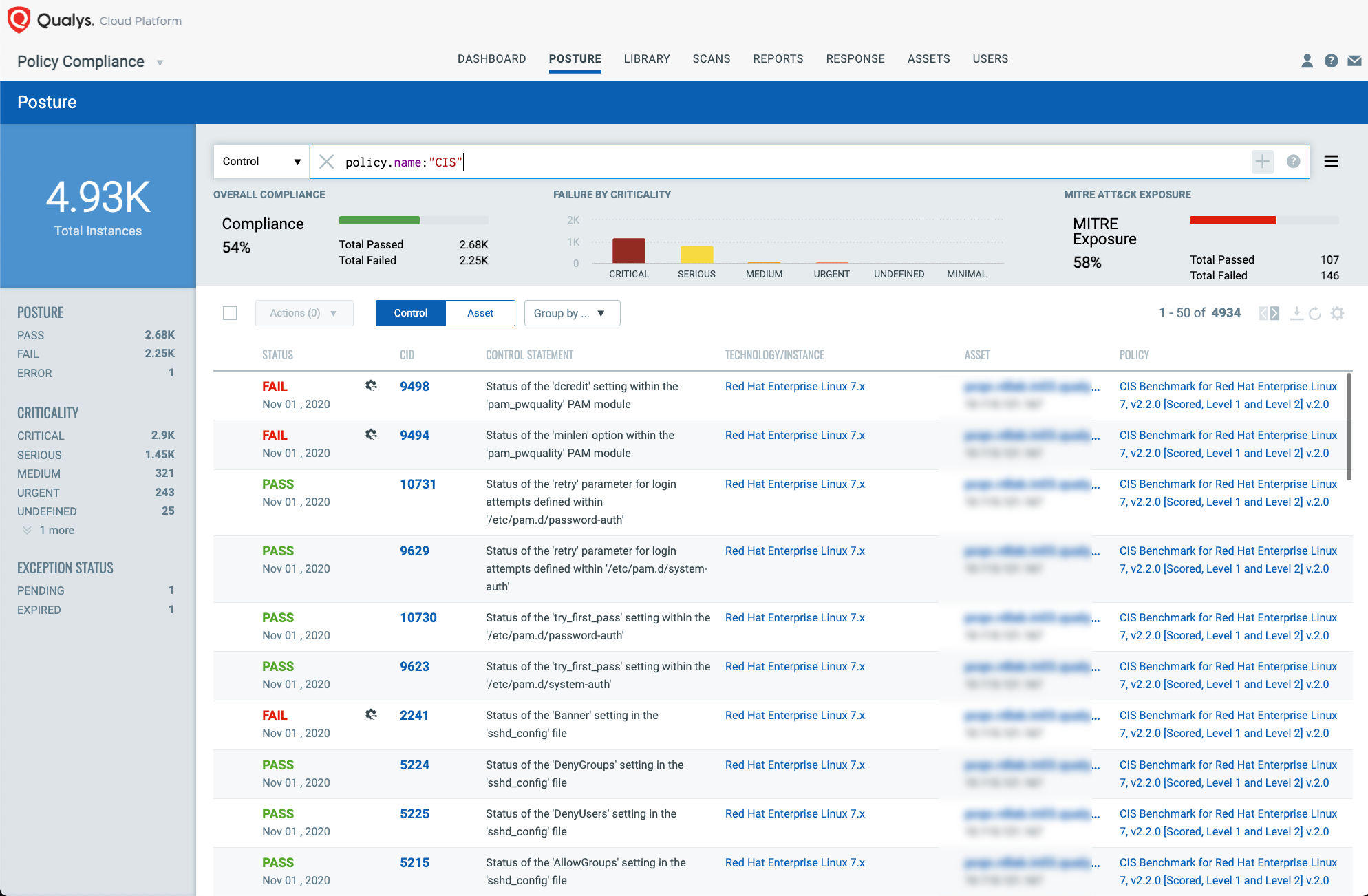
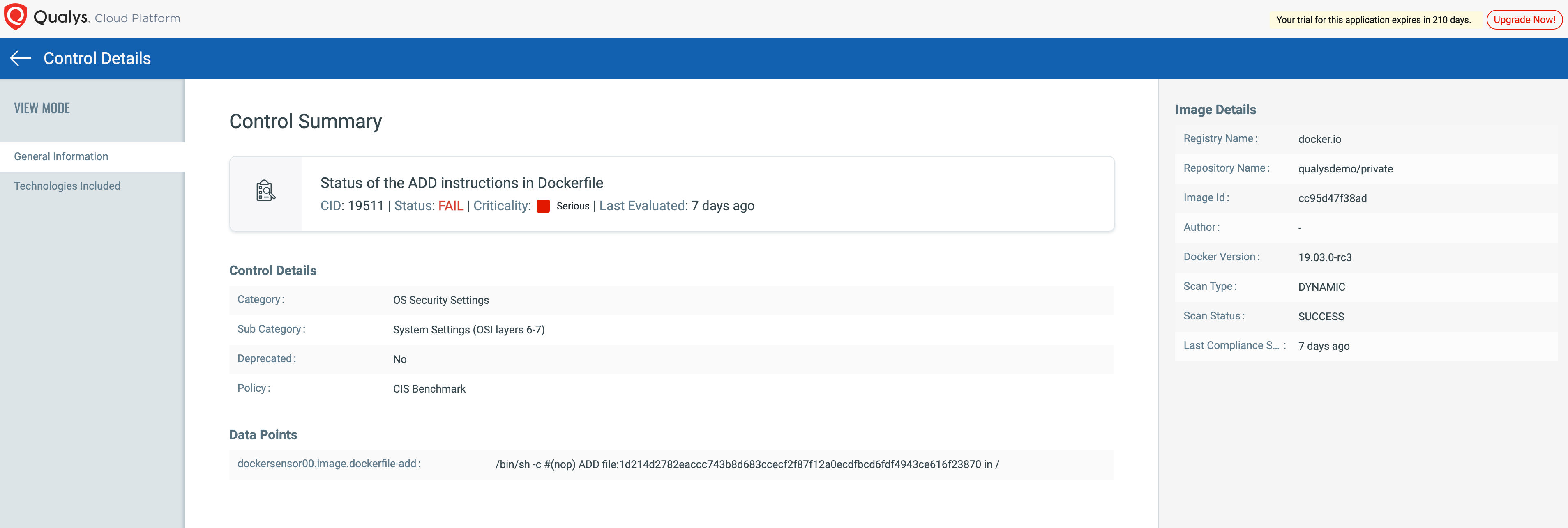
The use of hardened container images is a FedRAMP requirement for the use of container technology for CSPs. Qualys Policy Compliance and Container Security provide for assessing hybrid IT container infrastructure for hardening checks via various industry standard benchmarks like CIS.
3. Registry Scanning & Pre-Deployment Gating
Qualys Container Security supports scanning a wide variety of industry-standard container registries. Customers can set up registry scan jobs to scan images in their registry according to various criteria (repository, tags, date, schedule). As registries are not a control/enforcement point from a container lifecycle perspective, customers can implement the following high-level items in their operational processes for container registries and registry scanning.
a. Ensure registry hygiene by regularly pruning/archiving unused images or images that have not been rebuilt/refreshed.
b. Regularly scan images in their registry with Qualys CS. Customers can either use the built-in registry scanning workflow or build custom DevSecOps workflows leveraging the Qualys CS sensor and API-based scripting.
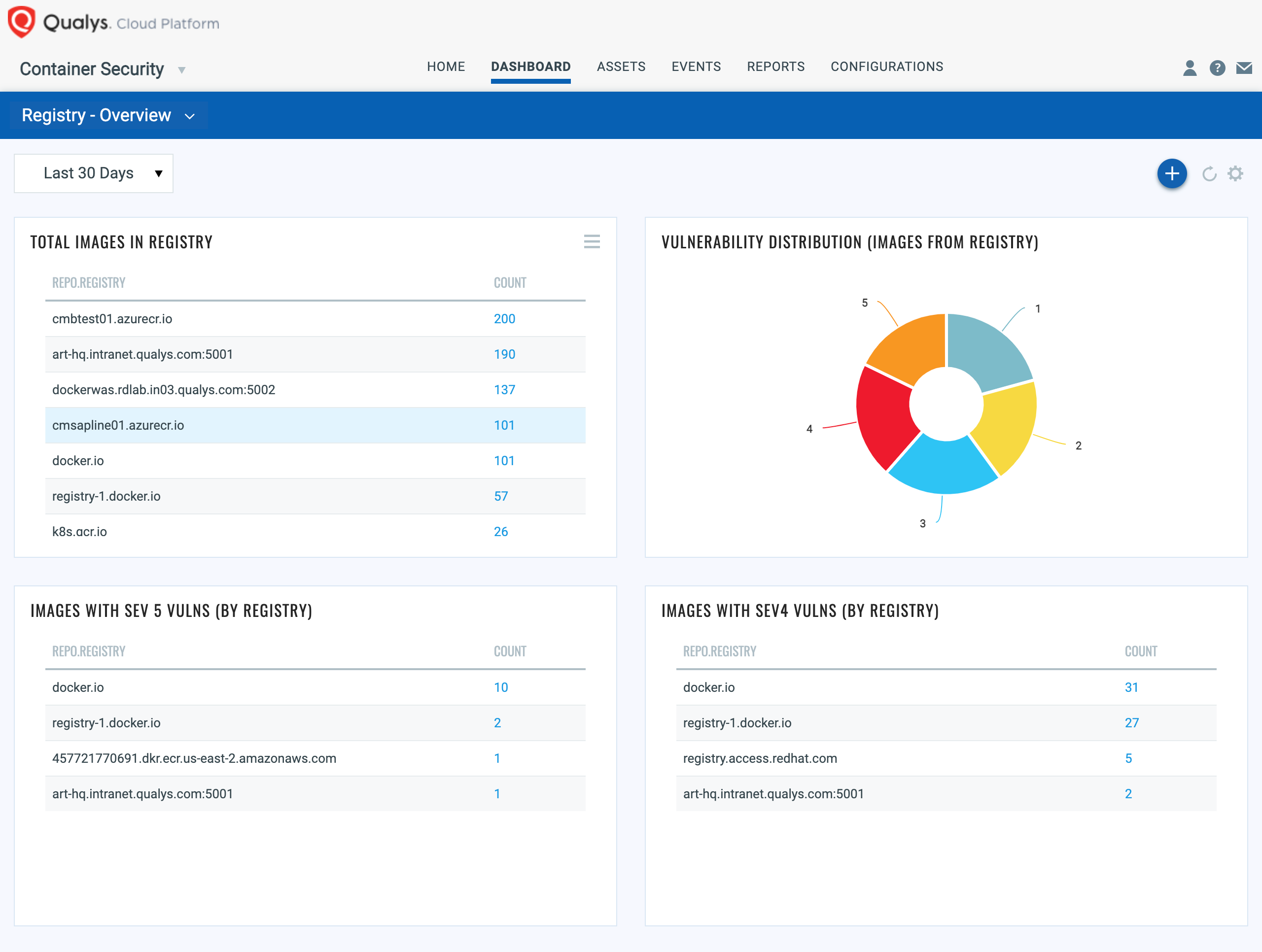
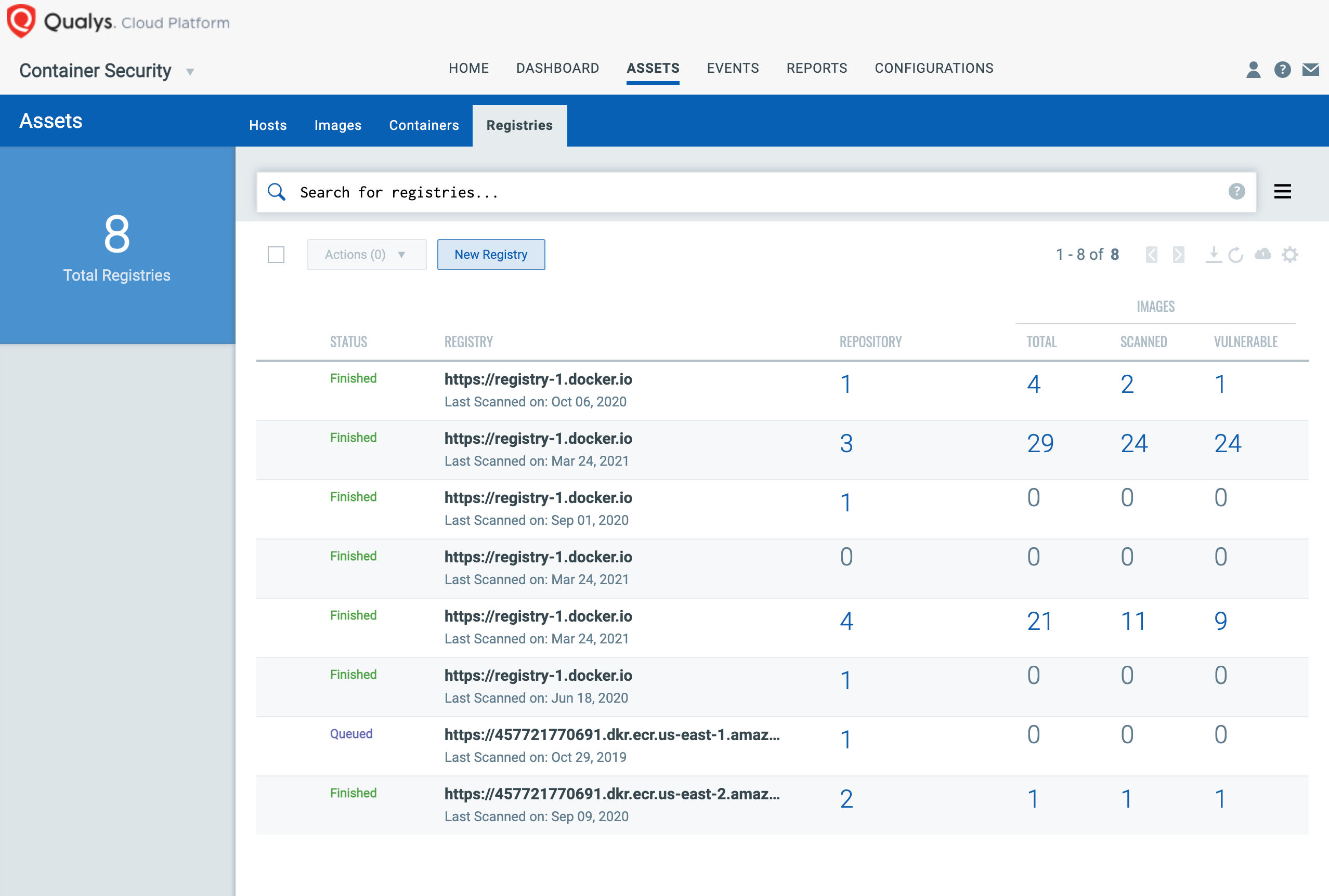
Customers can gate the promotion of images to production registries and to deployment with image scan checks in Qualys CS . Qualys CS provides integration into a wide variety of build pipeline tools such as Jenkins and Bamboo and performs policy-driven image gating in the build and image promotion process. Additionally, Qualys CS provides for integration with data aggregation, monitoring, and visualization tools such as Splunk.
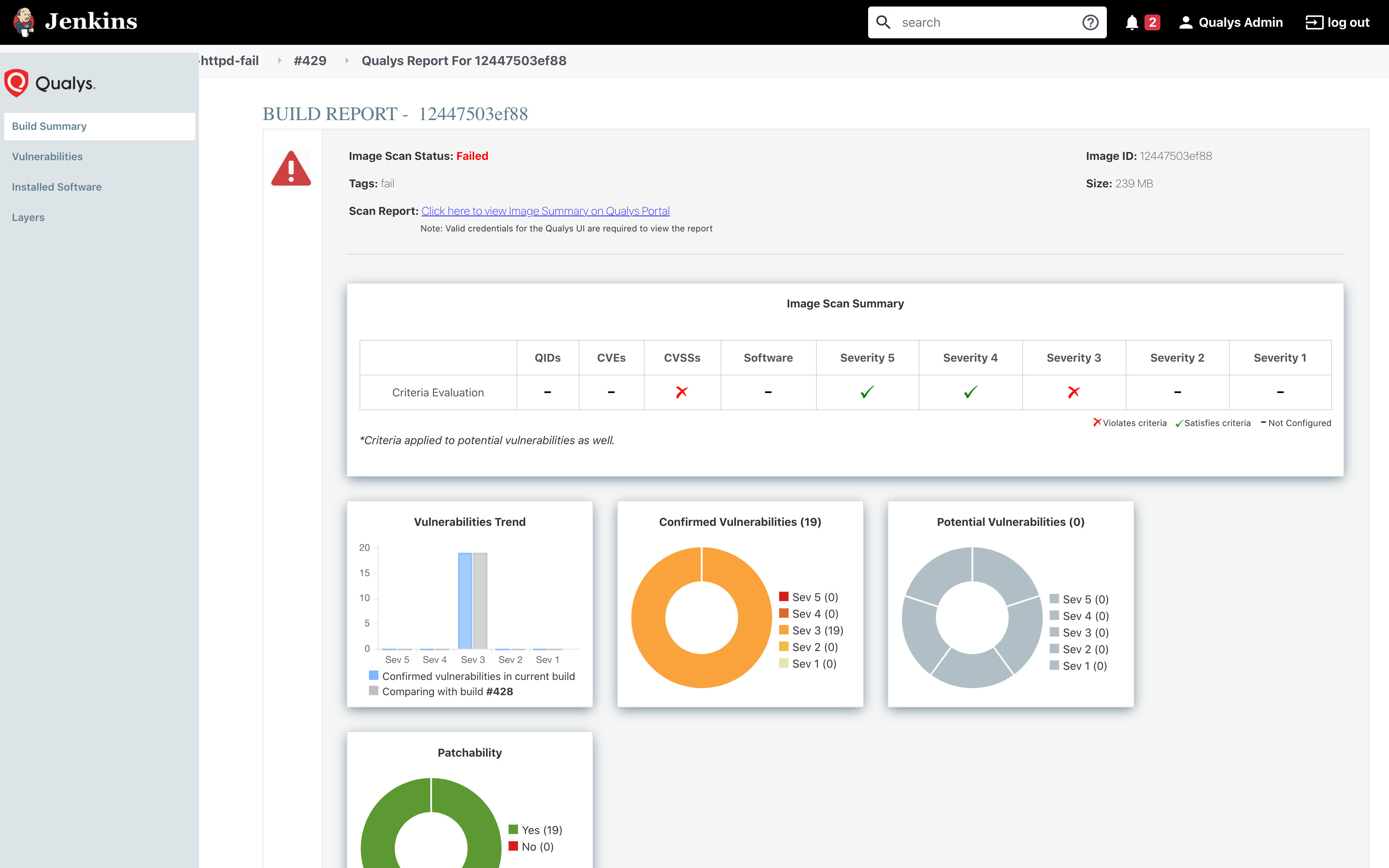
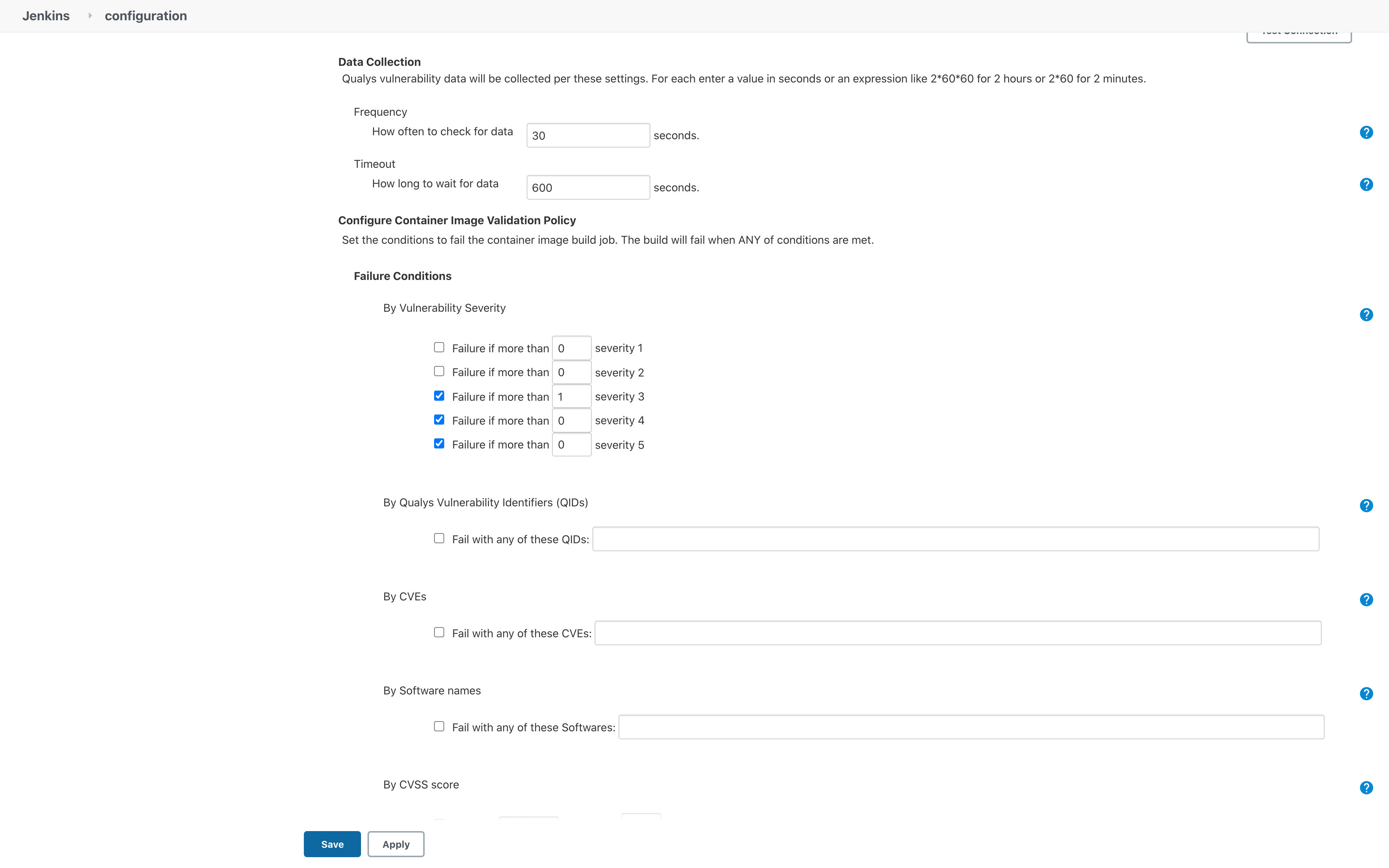
4. Periodic Container, Image Scanning
With Qualys CS, container images can be scanned regularly across the build, ship, run container lifecycle. With the CS sensor in general scan mode, it can be deployed in running container nodes, and it will scan running containers and images regularly in near real time. This ensures customers have an up-to-date security posture for their container deployment based on various real-world conditions (e.g. new deployments, updates from Qualys for new vulnerabilities, configuration, and compliance checks). Qualys CS can also perform drift detection on running containers vs. the underlying image. With in-container instrumentation, in-container behavior and drift can be monitored and prevented.
With the registry scanning, build pipeline integration options with Qualys CS, customers can adhere to the FedRAMP-defined 30-day scan requirements of images and ensure only recently scanned, compliant images are deployed to production.
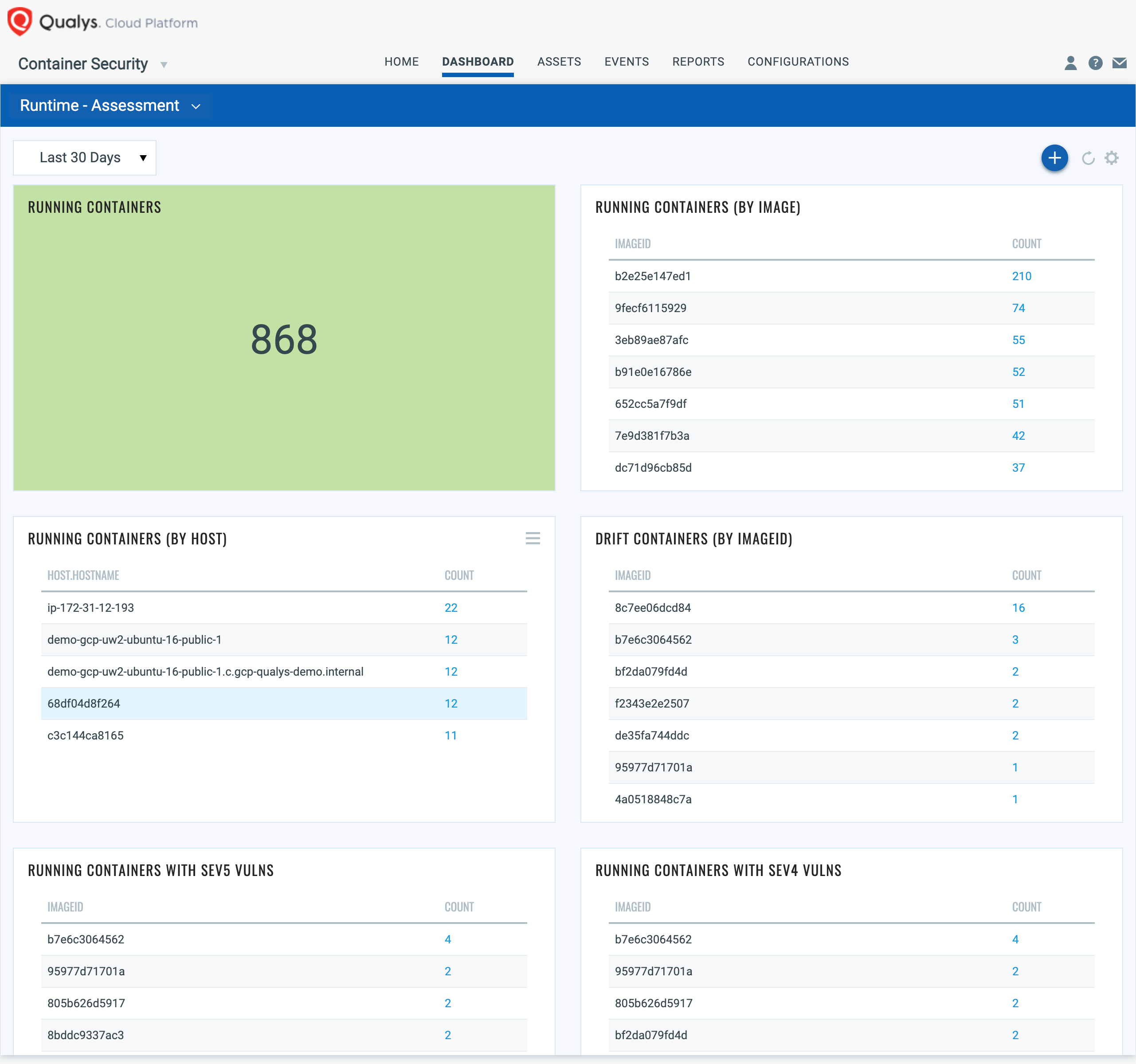
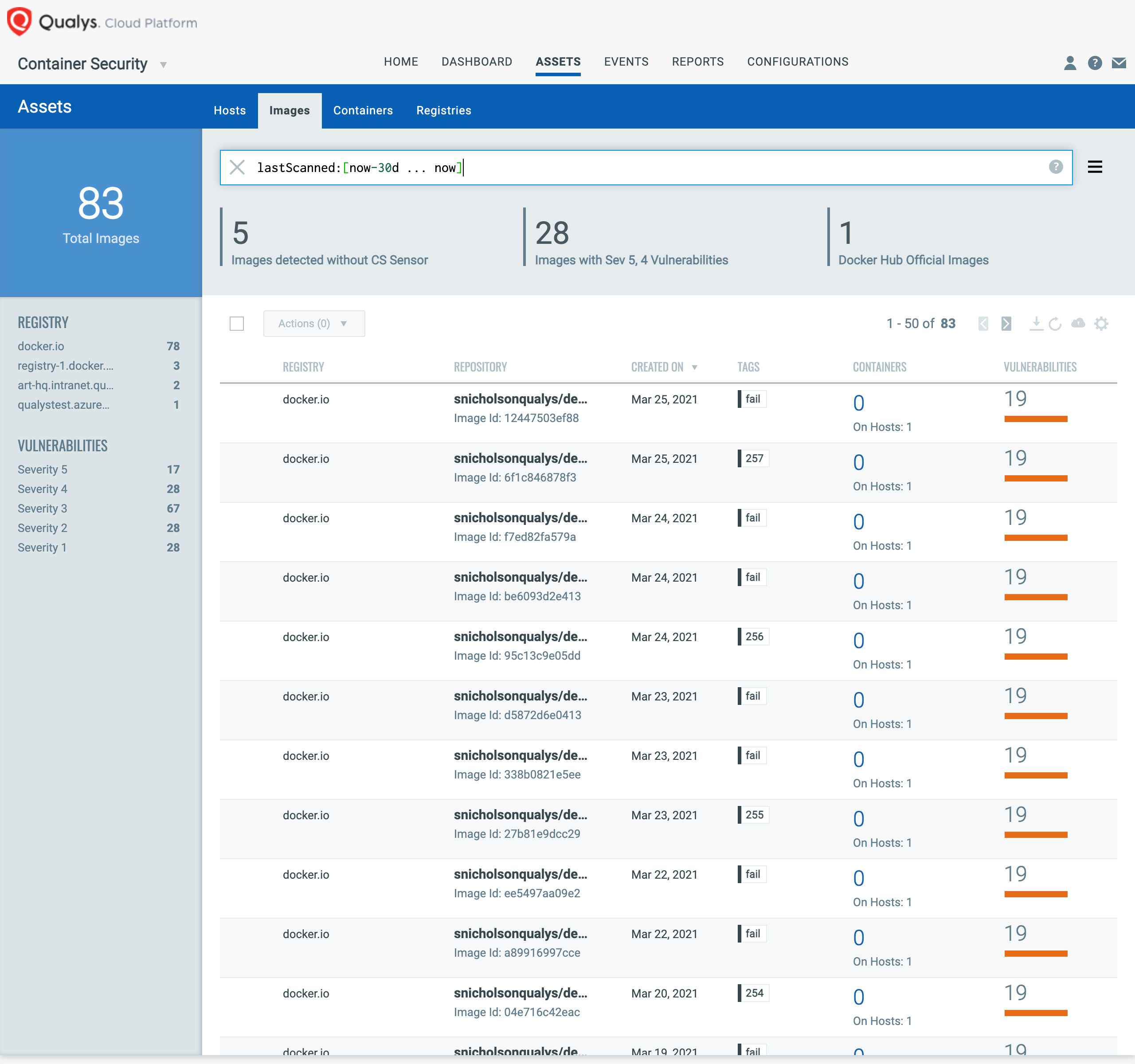
5. Container Asset Management & Tracking
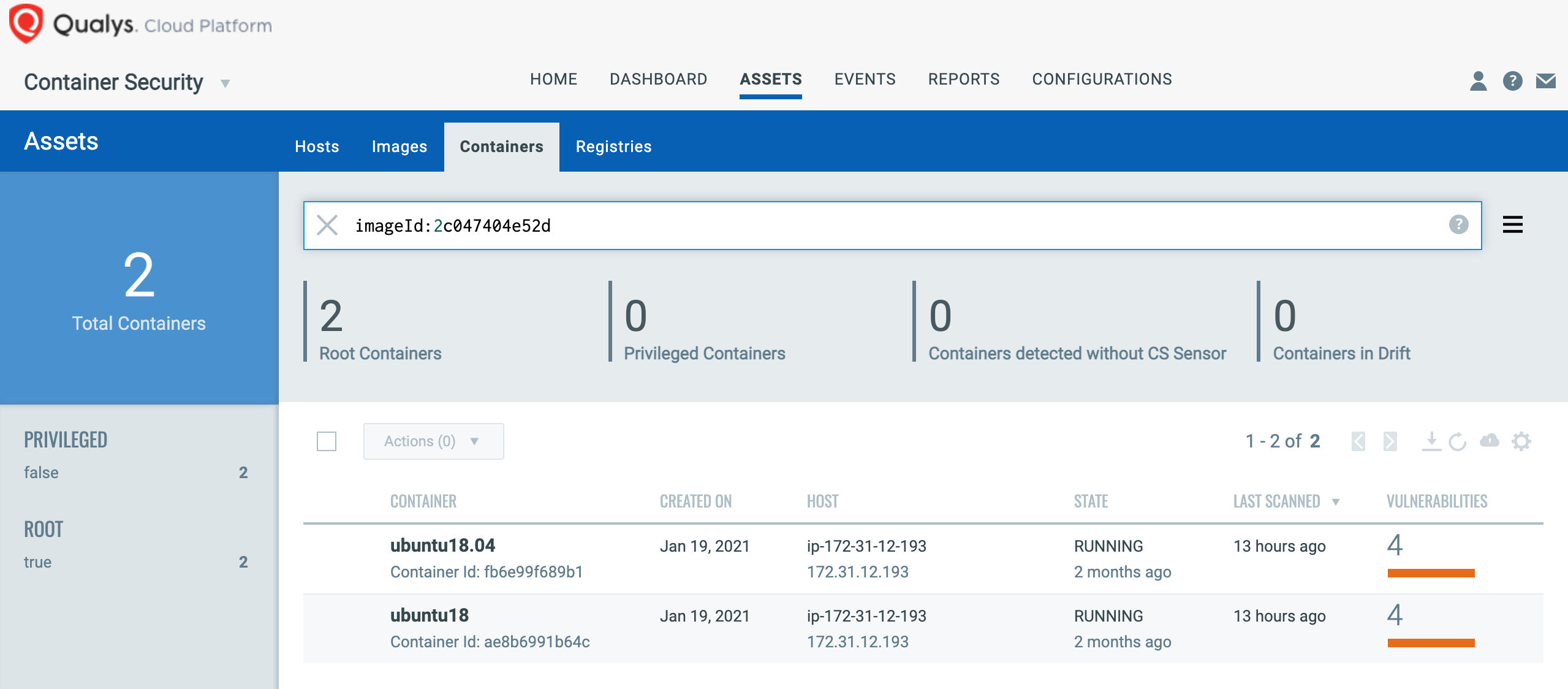
Qualys CS provides for unique identifiers for each image or container scanned and additionally provides for query capabilities for container/image data based on associated metadata (e.g., image tags/labels, Orchestration environment metadata). This ensures that containers and images that have been scanned and are compliant may be tracked across their life cycle, which meets FedRAMP requirements around maintaining an accurate and complete container image inventory.
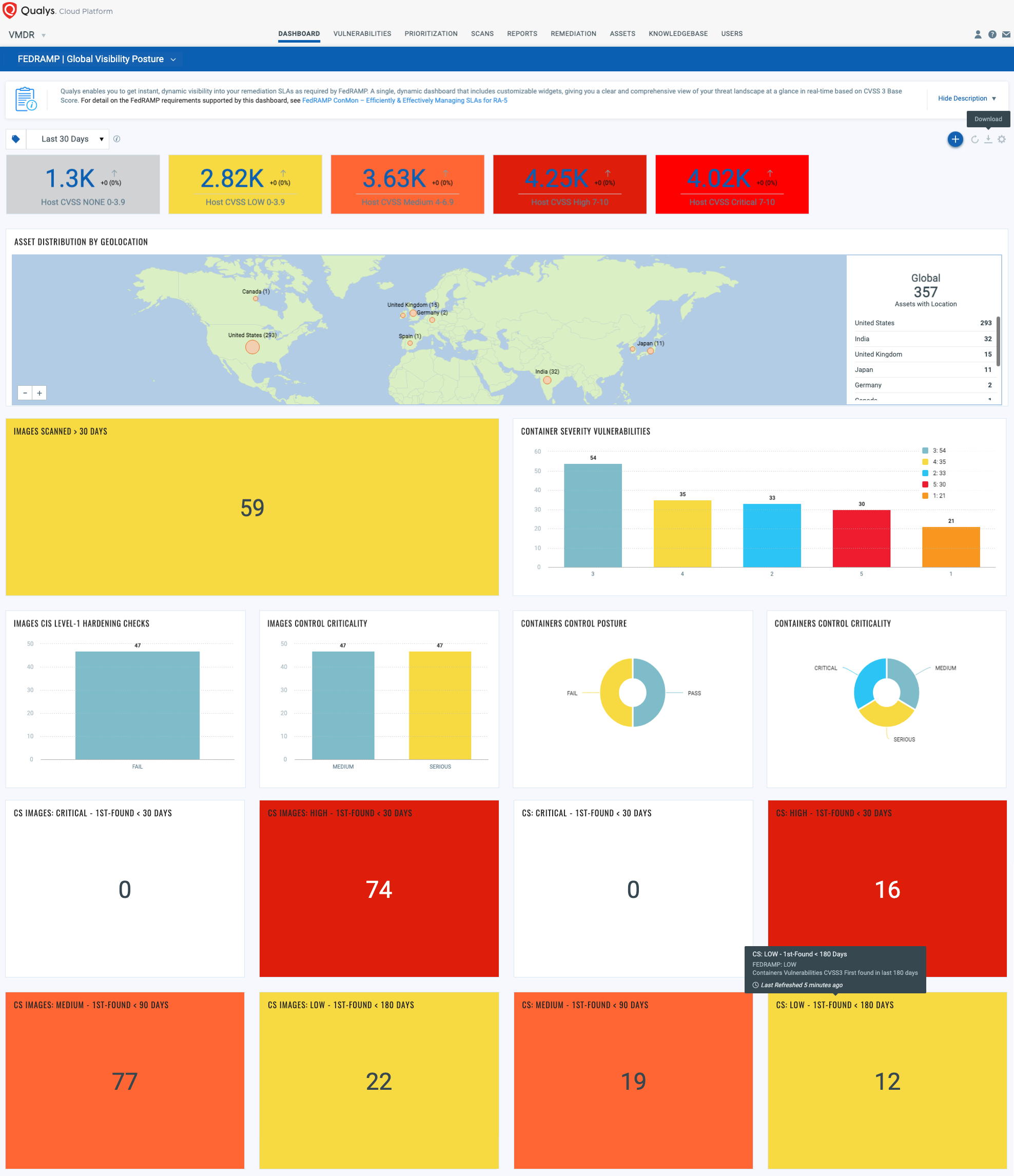
FedRAMP-Authorized Vulnerability and Compliance Management
The Qualys Cloud Platform, the only FedRAMP-authorized comprehensive vulnerability and compliance management solution, has one of the highest numbers of authorizations and enables organizations to expand their FedRAMP security program to container infrastructure.
Contact your Qualys TAM or email fedramp@qualys.com to discuss how you can leverage Qualys to extend your FedRAMP program to include your container deployments.
Resources
- FedRAMP Vulnerability Scanning Requirements
- FedRAMP Vulnerability Scanning Requirements for Containers
- Qualys on FedRAMP Marketplace
- Qualys Container Security
Co-Author
Samuel Aydlette, Principal Analyst, Compliance Programs at Qualys, and former contributing author to FedRAMP documents on container security and vulnerability scanning requirements, co-authored this blog post.