No Auth, Seamless Database Security and Compliance
Table of Contents
- Identify Databases Running on Your Assets
- Activate Assets for Policy Compliance
- Automatically Discover & Assess Database Instances and Other Middleware Technologies Without Credentials
- Content Library for Database Policies
- Search for OS-Dependent Database Controls
- Create/Update Option Profile Instance Database Collection
- Get Real-Time Visibility and Monitor Overall Compliance with New Dynamic Dashboards
- Standardize and Streamline
- Resources:
As data breaches continue to target databases and attack techniques become more sophisticated over time, organizations are looking for dynamic and efficient ways to effectively monitor the compliance posture of the databases in their hybrid environments. They have traditionally used privileged database user accounts in addition to host credentials to authenticate into their database instances running on Unix or Windows hosts. But sharing database credentials with security teams presents a security and governance challenge for organizations, and the teams performing these assessments may not have privileged access to the databases.
To overcome this bottleneck and perform checks more securely, Qualys Policy Compliance now provides the capability to perform database assessment via Qualys Cloud Agent for OS-dependent database controls without logging into the database. This makes assessments simpler and more secure as customers do not need to create any additional restricted user accounts on their databases. The auto-discovery feature in Qualys Cloud Agent identifies and collects information about the database instances running across your network, providing additional visibility for assessing the compliance and posture of all your assets.
Whether compliance information is collected via Cloud Agent or the traditional way via authenticated scans on the database, Qualys Policy Compliance offers assessment support for varied database technologies ranging from traditional Oracle to MariaDB, Cassandra, and many more. It automates the entire process of identifying assets and discovering database instances to their assessment, followed by prioritizing the critical control failures of high-scoped assets with reporting their posture against industry standards.
So, how do you take advantage of host-based authentication for your compliance assessments? Let’s find out!
Identify Databases Running on Your Assets
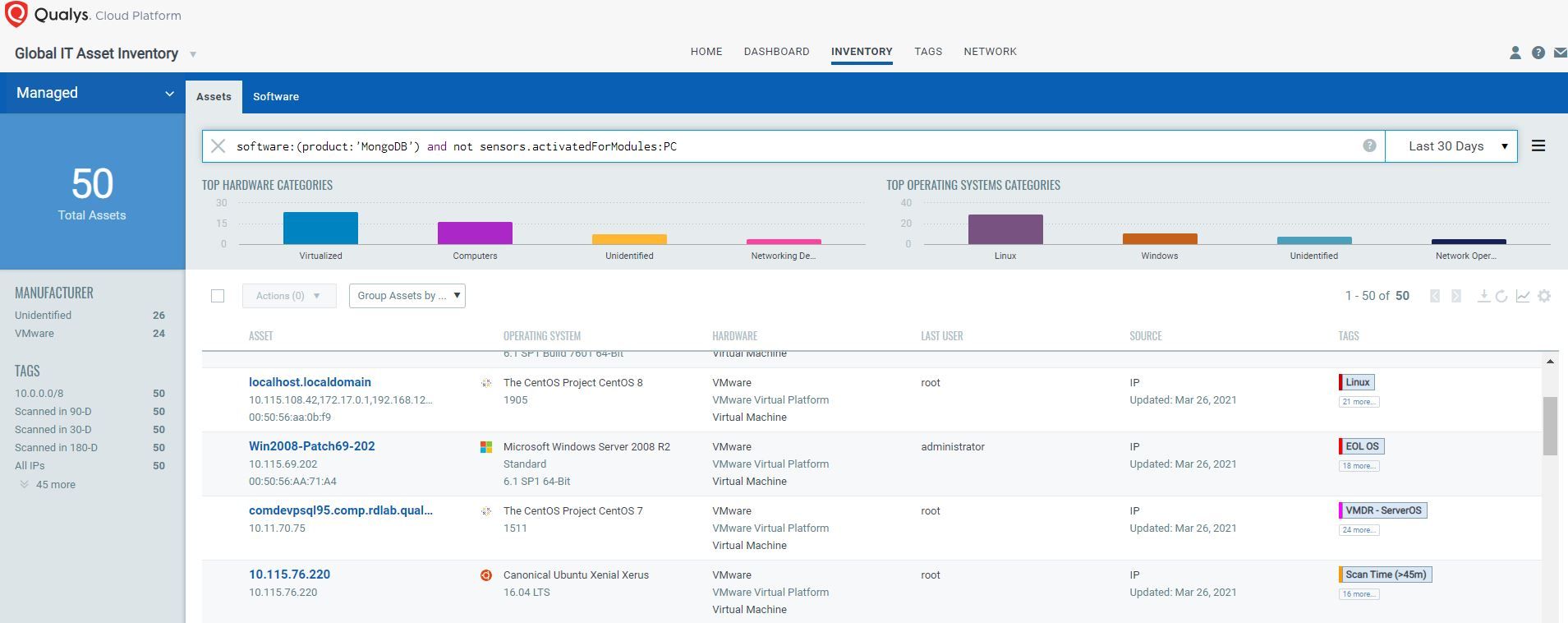
Global IT Asset Inventory makes it easy to identify assets having databases running on your hybrid IT environment. It also makes it easy to identify systems that don’t have Qualys Cloud Agent activated for Policy Compliance, which is required for this feature. For example, here is how to find all such systems with MongoDB:
software:(product:'MongoDB') and not sensors.activatedForModules:PC
Activate Assets for Policy Compliance
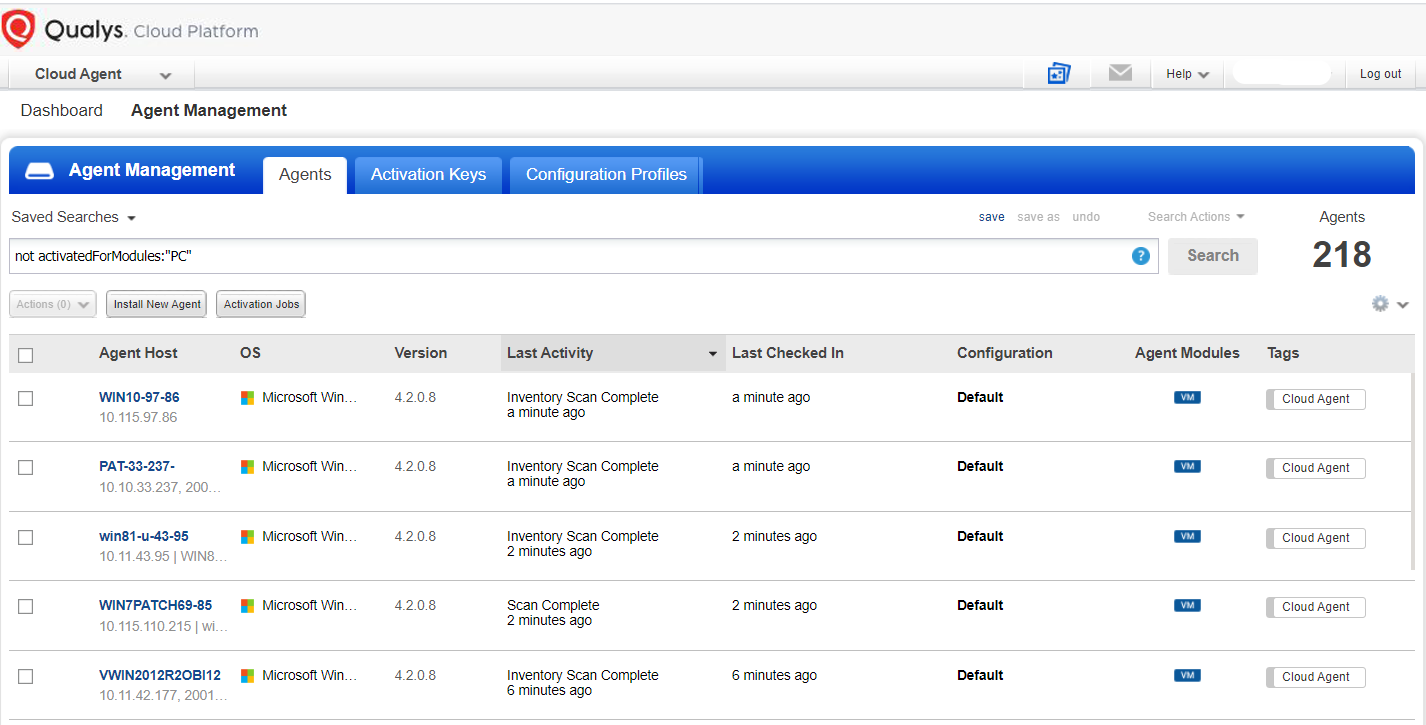
Now that the assets are identified, you can use the Cloud Agent management interface to activate the Cloud Agents running on them for Policy Compliance.
Automatically Discover & Assess Database Instances and Other Middleware Technologies Without Credentials
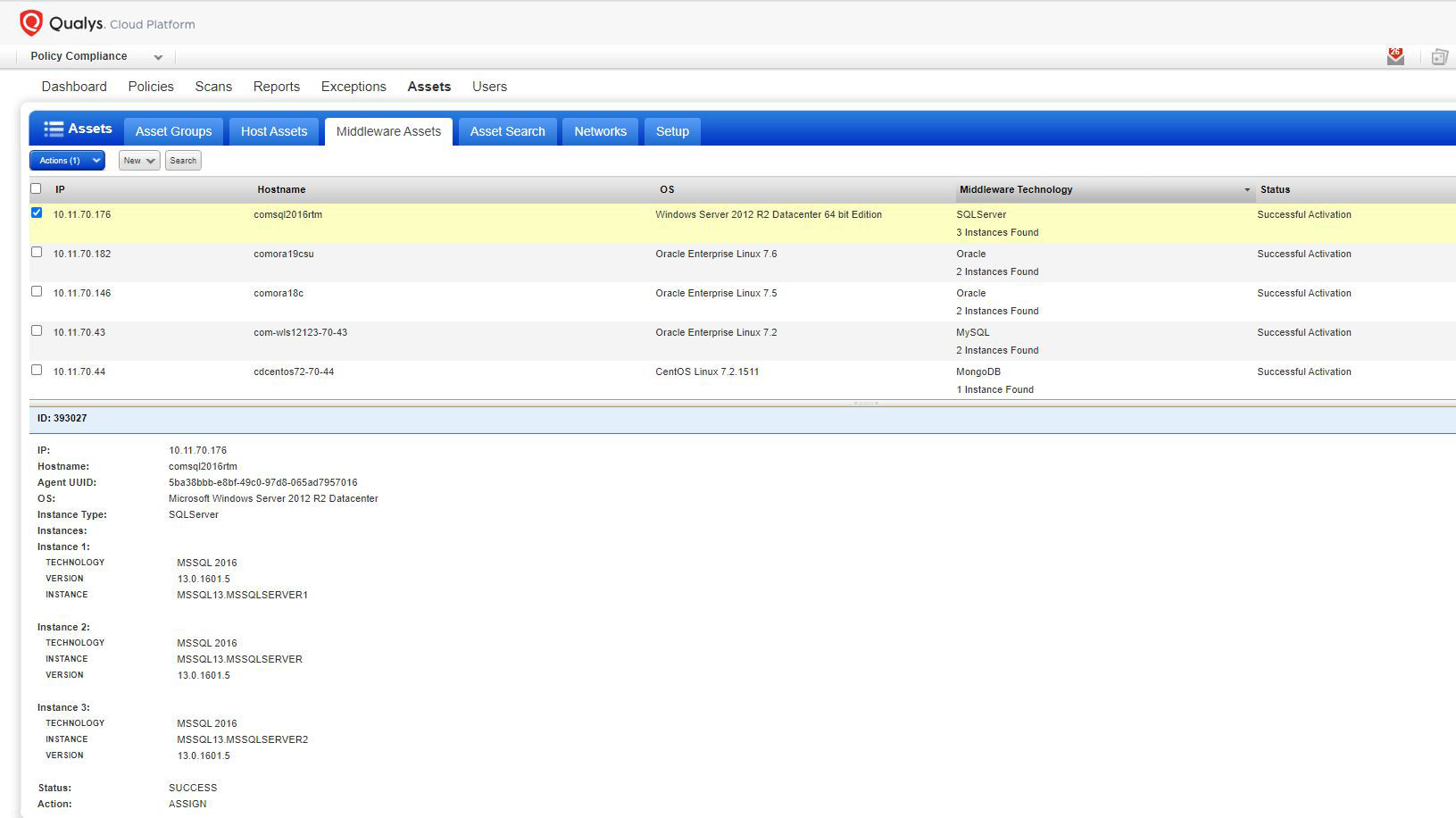
The auto-discovery feature in Qualys Cloud Agent discovers the database instances on the system where Cloud Agent is running. Cloud Agent running on Windows or Unix discovers and inspects the database instances through registry keys or running processes, without logging into the database. Once the assets are discovered and middleware technology details are listed on the Middleware Assets page in Policy Compliance as shown below, you can activate the assets for middleware assessment, either selectively or choose default activation (recommended) for assessment to begin as soon as they are discovered.
If middleware assessment is already enabled, Cloud Agent will auto-discover the database instances and assess for OS-based database controls. No additional user action is required to enable this functionality.
Content Library for Database Policies
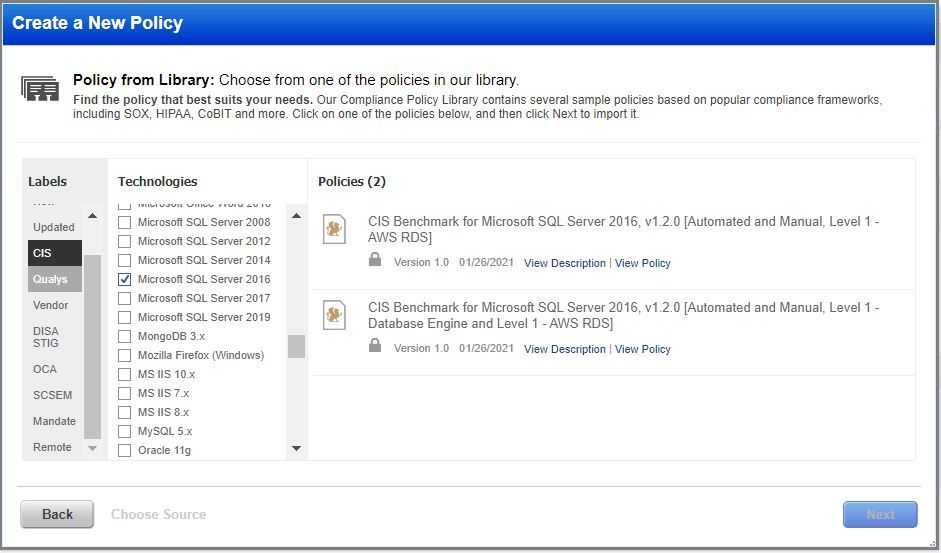
Qualys Policy Compliance supports a rich library of database security policies as a part of its Policy Library. The Qualys security research team researches and regularly updates these database security policies, which are also used by Qualys’s own FedRAMP compliance team. You can simply import the policy for the required technology, assign tags and continue with the assessment.
You also have the option to create your own User-Defined Controls (UDC) for databases and add them to your custom policy, making them available for scanning and reporting.
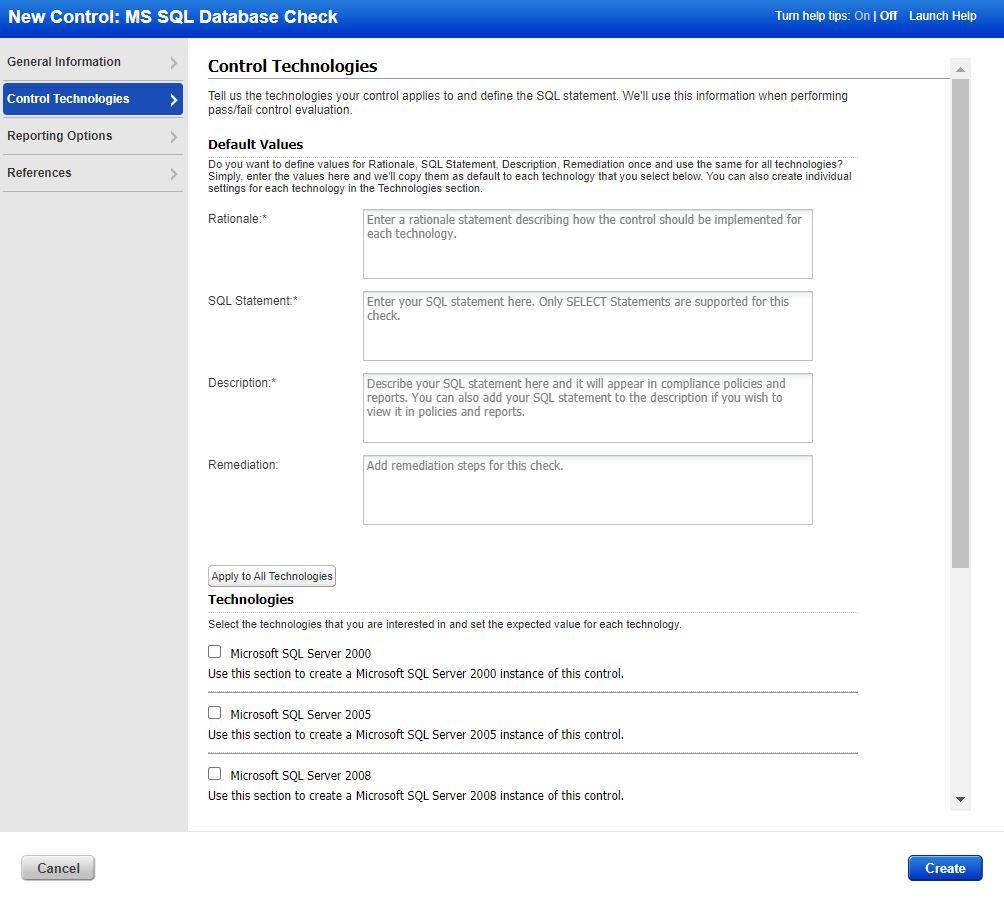
Search for OS-Dependent Database Controls
The newly added option to search for operating system-dependent controls is available under the Controls Search tab in Policy Compliance.
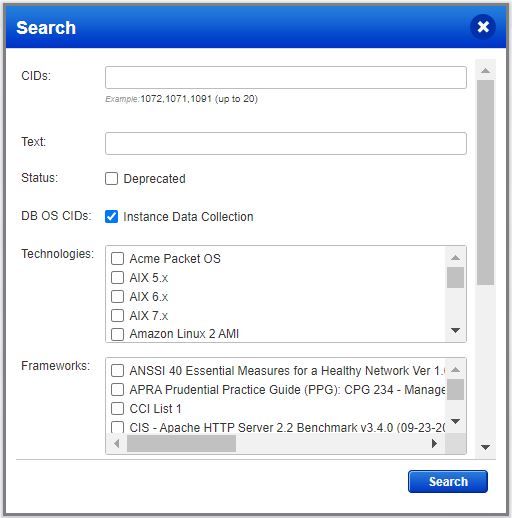
Create/Update Option Profile – Instance Database Collection
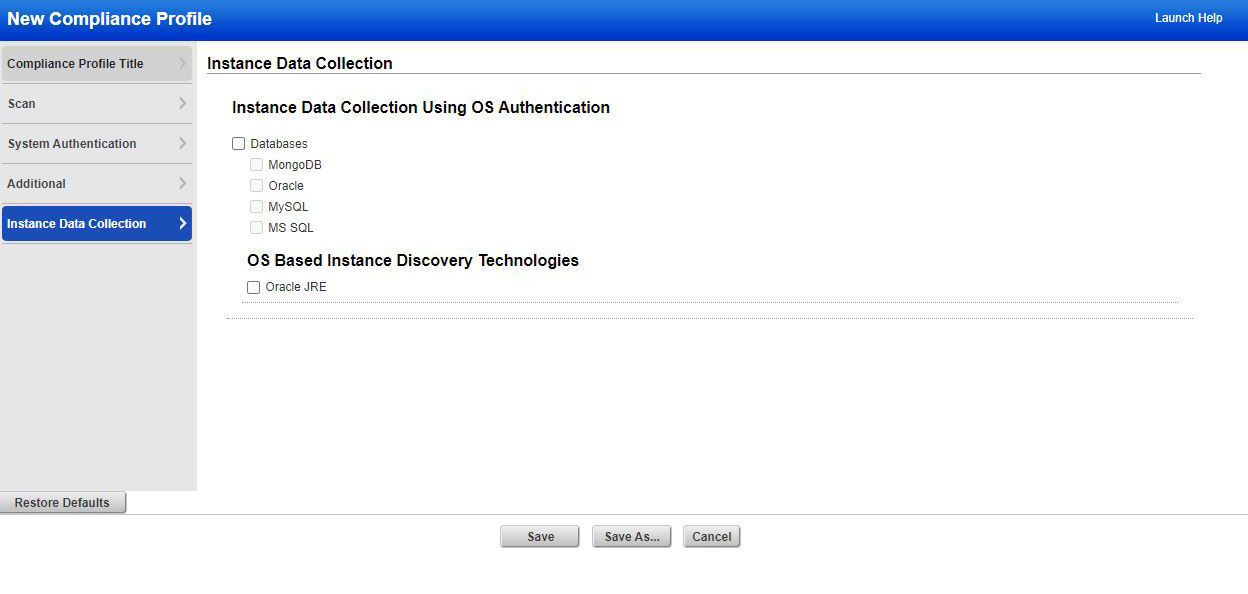
If you are using a scanner, the Compliance Option Profile now has the option to enable OS-based instance data collection. Selecting this option enables data collection for the supported databases using the underlying OS-based authentication records. Once the compliance profile is updated, simply launch compliance scans with this option profile for authenticated scanning.
Get Real-Time Visibility and Monitor Overall Compliance with New Dynamic Dashboards
Utilizing the enhanced capabilities of Policy Compliance Dashboards with customizable widgets, you can easily monitor security and compliance posture at any time. Design the dashboards and widgets according to your organization’s needs and easily monitor the overall compliance of the entire IT infrastructure. The drill-down capabilities of Unified Dashboards make it easier to look into granular details and prioritize assets based on criticality and other factors. Once you gain visibility into the compliance status of all assets, securing database assets becomes a lot easier.
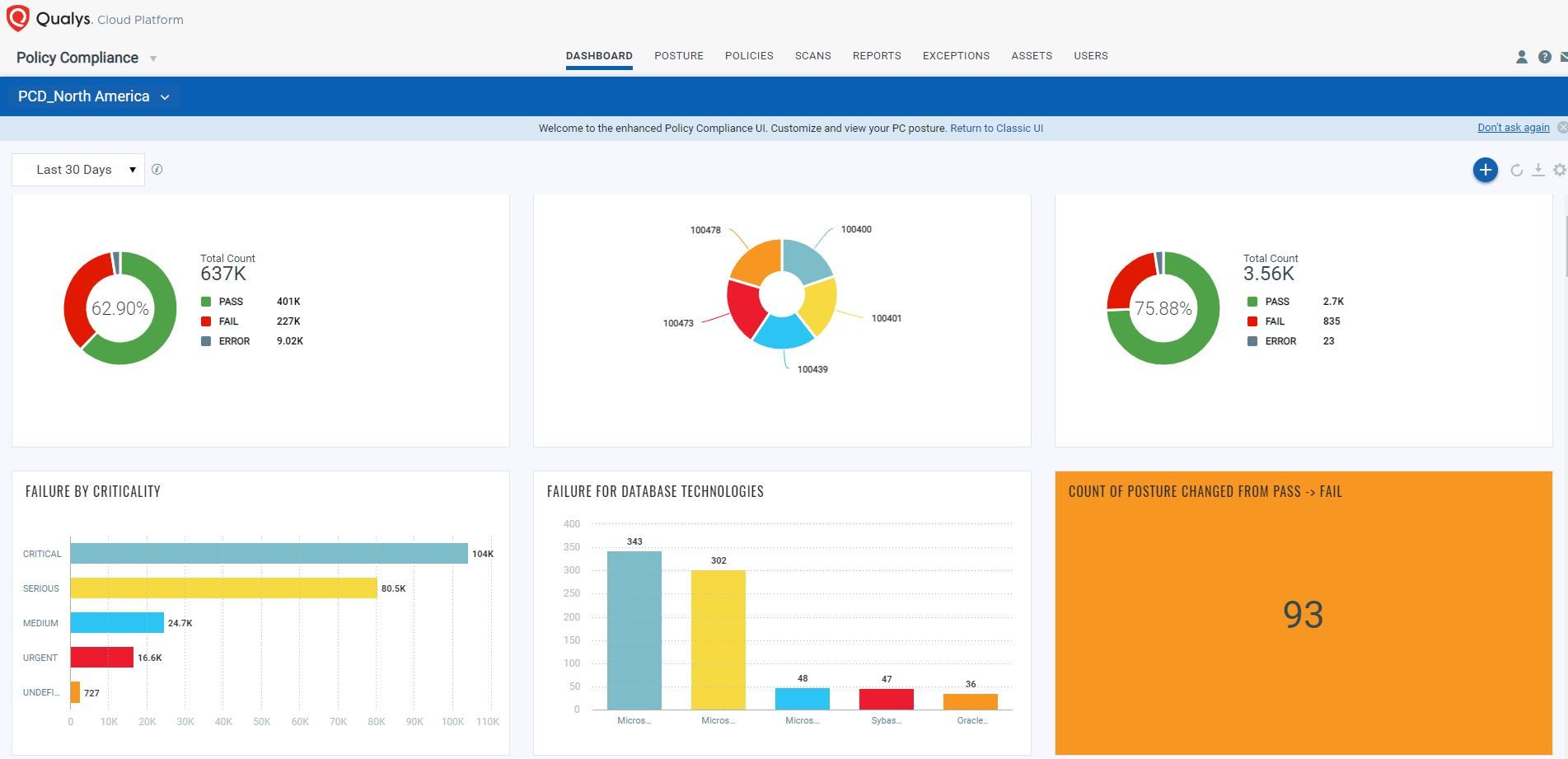
The newly added posture tab enables you to have a quick insight into the compliance posture of database assets and controls without having to run the reports. In addition, you can track compliance posture based on assets, technology, instances, categories, and criticality to quickly prioritize and remediate the high-risk assets. QQL (Qualys Query Language) queries with its advanced search capabilities makes it easier to search for compliance data and view compliance score all in one place.
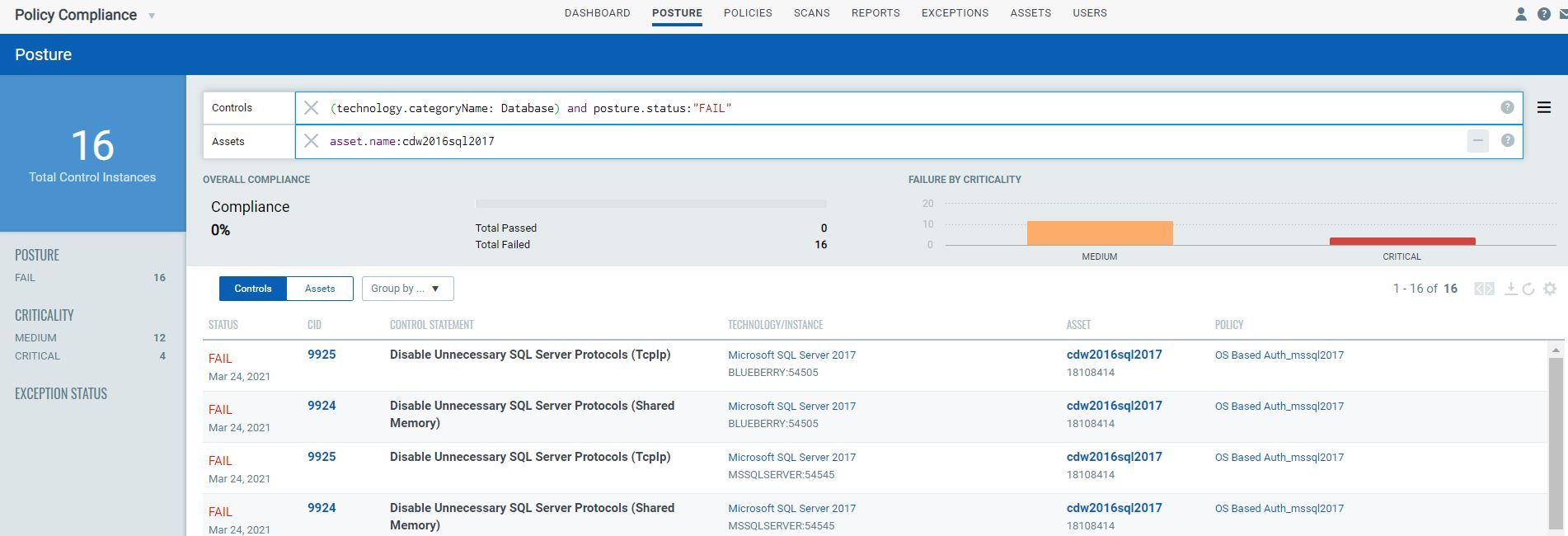
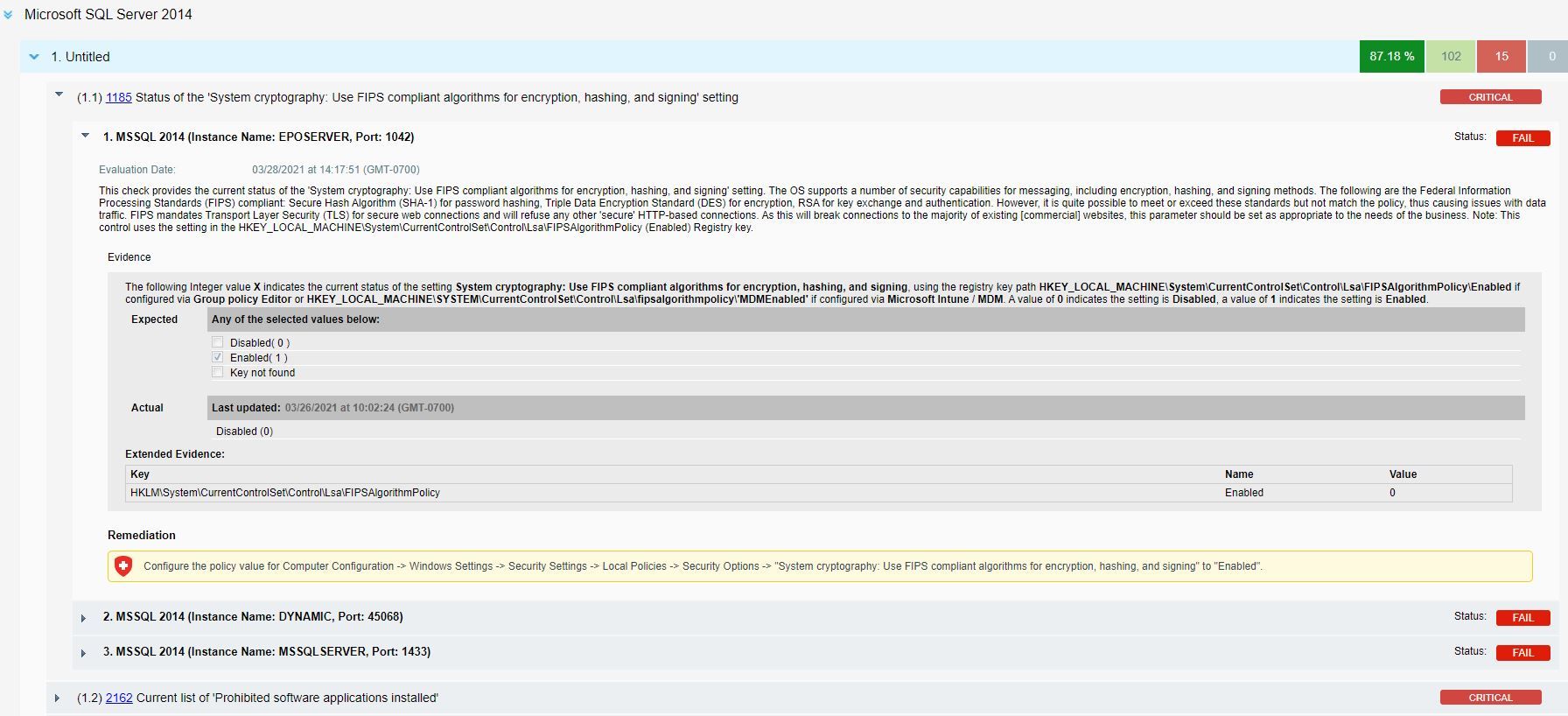
The Policy Compliance report below shows the details of control posture for database instances auto-discovered from assets with quick remediation steps to take action and fix the misconfigurations or errors.
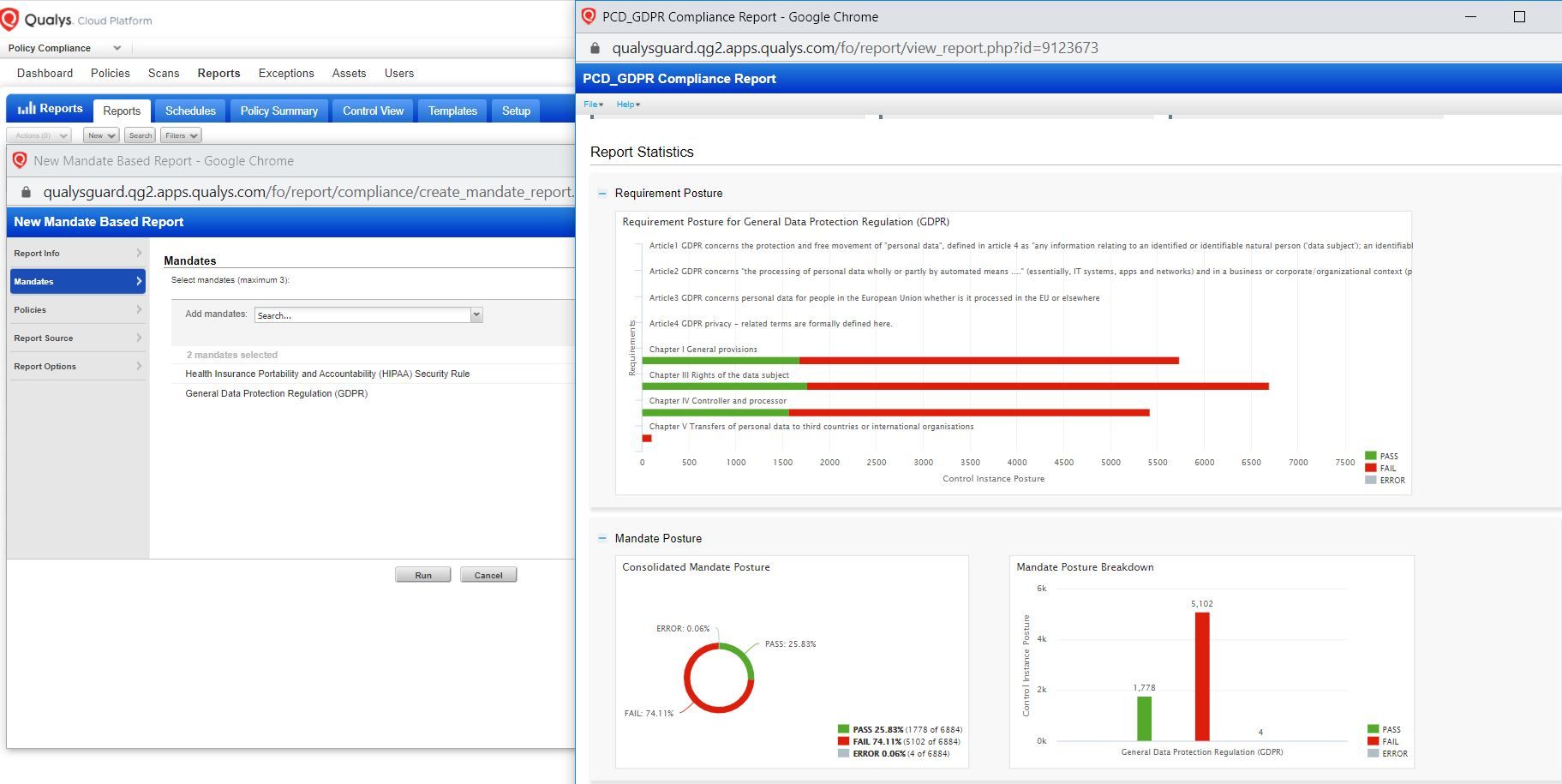
Mandate-based reports in Policy Compliance provide a complete view of the compliance posture of your organization against multiple regulatory mandates. Using this, you can easily identify how your policies and controls are meeting various regulatory compliance database requirements like GDPR, HIPAA, and many more.
Standardize and Streamline
Database security and compliance is a complex process and pivotal to any organization. With Qualys Policy Compliance automated solutions, you have a standardized and streamlined process in place to ensure your database assets are secured and in compliance with relevant regulations at all times. Start your database security assessment by simply sending an email to support@qualys.com or by contacting your TAM.
Good coverage on Database security assessment and compliance. Couple of Qs
1)Would Non-authenticated scan performed by Cloud Agent produce results equivalent to authenticated scans.
2)Can the DB scans be performed via a Prod app or Web app hosted for Public since a Standalone DB scan/results would vary than being performed through Middleware/Web app
3)How does this solution differ from IBM-Guardium