Introducing CyberSecurity Asset Management
With the rapid expansion of new IT technologies and their growing adoption rate, organizations face an increasing problem in securing their myriad on-premises, virtual & cloud-based assets. Add to that the explosion of intelligent devices on the corporate network and you have a huge landscape to manage. Given the fundamental axiom that ‘you can’t secure what you can’t see’, it is critical for companies today to first be able to inventory their full IT environment, then to detect and monitor specific security risks and finally actively respond to those risks. Failing this, companies are subject to increasing security jeopardy brought on by end-of-support software, obsolete hardware, unknown internet-exposed devices, unauthorized software and more. In addition, governing organizations like HIPAA, PCI, & FedRAMP are now requiring a comprehensive asset management & security program to be compliant, using standards from CIS, NIST and others.
In a recent example, a PC gaming vendor accidentally misconfigured a server to make it visible and accessible from the internet. The server was left exposed for over a month until the company was notified of the issue by an outside security researcher and in that time customer data from an estimated 100,000 users was exposed. In these situations, multiple risk factors can compound the issue. If that server had been running any end-of-service software, then unpatched vulnerabilities could have enabled even deeper access into the company’s network.
So how do we address these issues? Traditional IT inventory tools are constrained in their security context, and cybersecurity point solutions rely on third parties or siloed technologies to collect data. This requires clients to implement multiple tools to effectively address their full IT inventory and security needs across today’s hybrid environments, causing administration, integration and internal security policy headaches.
Today we are introducing CyberSecurity Asset Management, which builds on Global AssetView and moves the needle beyond inventory by adding security context and response. It is asset management reimagined for security teams, focused to identify all systems comprehensively, detect at-risk assets, and mitigate with appropriate actions. This offering fills the gap between traditional IT inventory and the core security functions by overlaying key business and asset criticality data, establishing unauthorized and authorized software lists, applying current and upcoming EOL/EOS data, providing an outside-in view of the organization’s internet-facing assets, highlighting security endpoint blind spots, monitoring the result with policy-based alerts, and facilitating appropriate response with software uninstall. It represents a security foundation on which organizations can deploy and build before easily moving to vulnerability management, endpoint detection & policy compliance using our single agent.
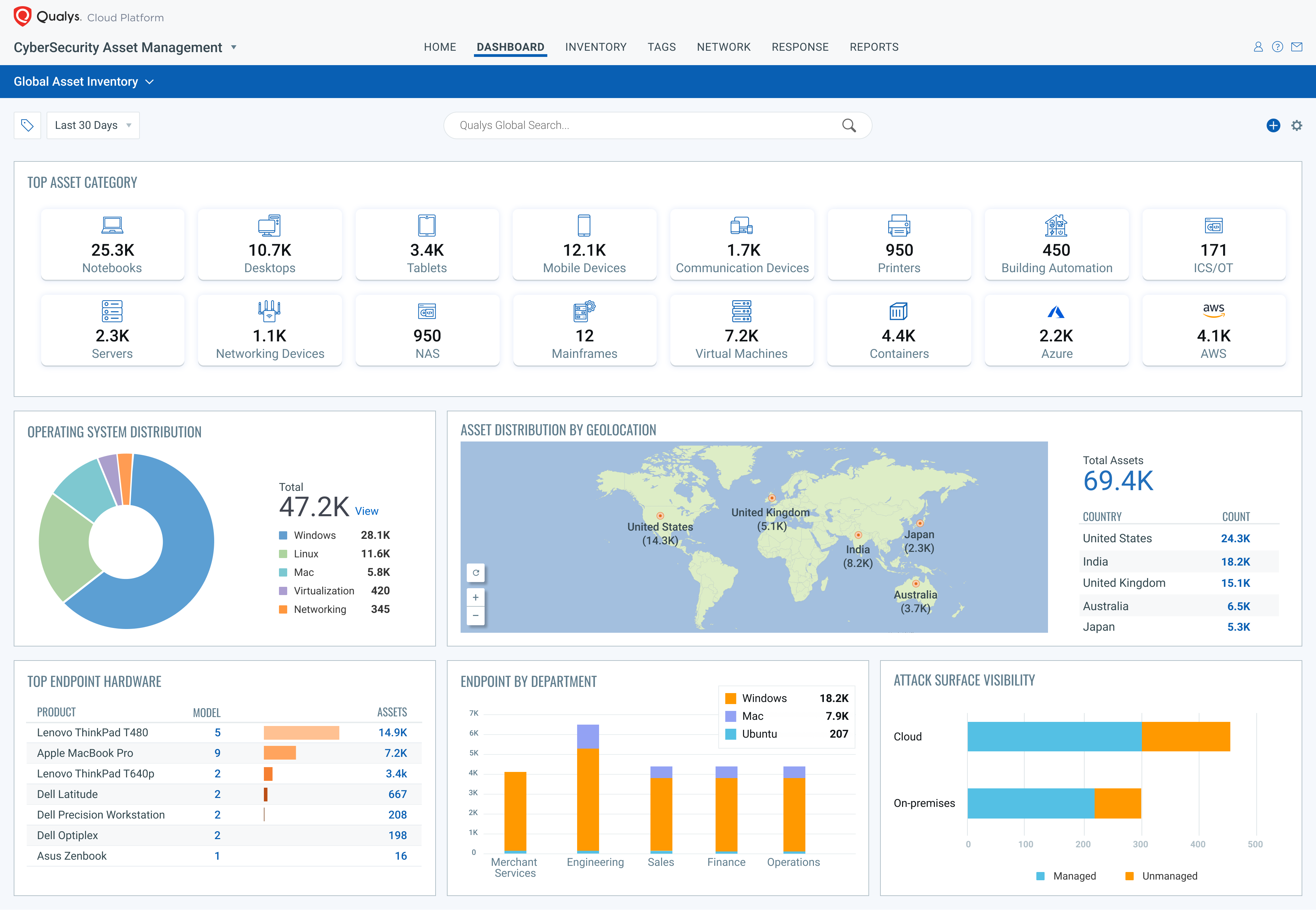
Build a Comprehensive Asset Inventory (free Global AssetView app)
Knowing what’s in your global hybrid-IT environment is fundamental to security. Global AssetView automatically discovers and classifies all IT assets including software, on-prem devices and applications, mobile, clouds, containers, and enterprise IoT devices using both agent and agentless methods. It works in conjunction with the Qualys Cloud Platform and Qualys sensors (scanners, cloud connectors, container sensors, cloud agents, passive sensors and APIs) to continuously discover assets. This unique multi-threaded approach to inventory ensures that Qualys provides the most comprehensive view of your IT environment.
Automated categorization and classification of asset data maps raw asset data to the Qualys product catalog to obtain clean and reliable data. The product catalog is continuously curated with a focus on completeness, relevance, and data quality. This process transforms the global IT asset inventory into multidimensional and structured information for better business decision-making.
A powerful search engine lets you craft simple or advanced queries combining multiple asset criteria returning results instantly. Your stakeholders also need the right perspective of the underlying data so that they can act on insights to prevent and address threats. Qualys Global AssetView’s interactive, customizable dashboards let you visualize and share the security, configuration, and compliance status of IT assets.
Enterprise IoT, those connected devices like printers, security cameras, VoIP phones, smart boards, and building automation that you increasingly find on your organization’s network, is growing at a massive rate. Qualys Passive Sensor, part of Global AssetView, listens to network traffic to identify all IP-connected devices in real time, dissects multiple protocols to fingerprint, and uniquely identifies thousands of IoT devices. With this release, Qualys significantly extends its enterprise IoT fingerprinting library and profiling capability for tens of thousands of additional devices, across key categories prevalent within customer networks, including:
- VoIP Phones & Video Conferencing
- Building Automation, such as HVAC Control, Lighting, Power & Energy Monitoring
- Access Control and Badge Readers
- Intrusion Detection & Security Cameras
- Connected Audio and Media devices, such as smart TVs and speakers
- IoT Gateways and Access Points
- Network Printers
- Smartphones and Tablets
Visibility is the core element in securing your environment, and Qualys’ ability to track and identify IoT devices is a key element to ensuring that visibility. Moreover, having a single, consolidated view of ALL assets across the entire network, on-premises, cloud, IoT and mobility is vital.
Sync with CMDB and Assign Risk Profile
Use the ServiceNow Sync app to populate the CMDB with asset data from Qualys and update Qualys assets with relevant CMDB attribute data.
2-Way CMDB Updates (with CMDB Synch app)
Qualys CMDB Sync populates ServiceNow CMDB with detailed inventory of new and changed IT assets, categorized and enriched with lifecycle data. It eliminates unidentified and misclassified assets and gives you real-time, comprehensive visibility into your IT asset inventory to immediately flag security and compliance risks. The solution also enables customers to import into their Qualys Subscription any missing ServiceNow IP addresses for Vulnerability Assessment and Policy Compliance scans and collect inventory.
Business & Organizational Data Enrichment
Collect and assign key attribute data from the CMDB. Not all IT assets are of equal value or importance to an organization and to the security perspective. Pulling in business and organizational data allows organizations to better understand how their assets are being used and focus their security efforts on mission critical elements.
This capability, an extension of our current CMDB Synch app:
- Pulls in key attribute data from ServiceNow CMDB, including:
o Status (e.g. operational, in-repair, lost/stolen)
o Organization (e.g. Company/Business Unit/Department)
o Owned By/Managed by/Supported by – who owns, manages or supports the asset
o Environment (e.g. Prod/Lab/Test)
o Assigned Location (Country, City, and location name)
o Business App/Service name (Banking App, HR-intranet)
o Asset Criticality - Allocates the data as asset attributes
- Enables search through queries and access through APIs
Asset Criticality Measure
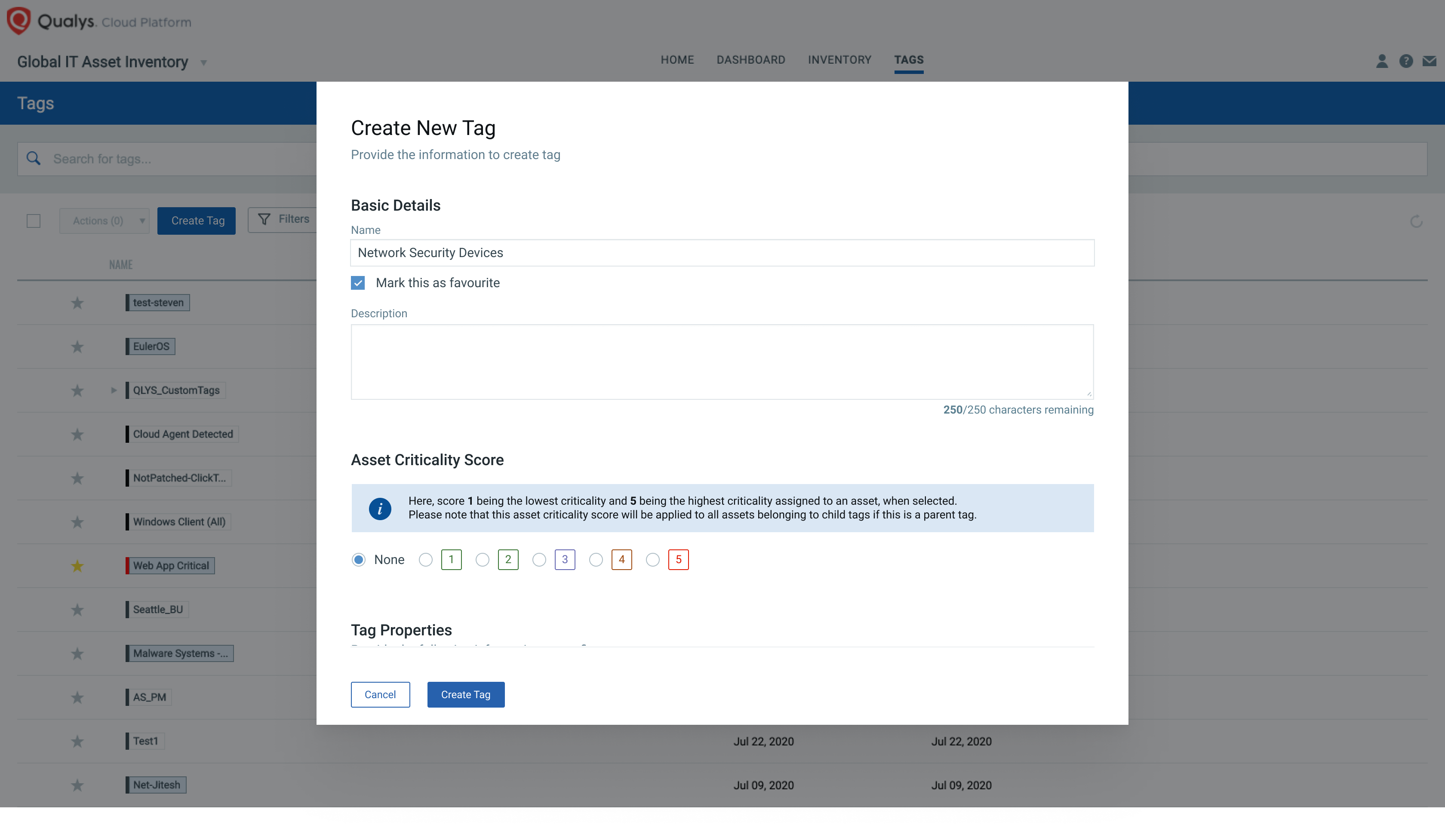
Focus your security prioritization efforts on high-importance and high-risk assets, by defining a key business and technical context. Asset Criticality is a user-defined measure of asset function, environment, and service and includes the following:
- User optionally selects a criticality score on a Tag which is then applied to one or more assets
- An Asset attribute is assigned the highest criticality score among allocated asset tags
- If pulling data from CMDB, the asset criticality score is automatically assigned to a tag and the corresponding asset
Detect and Monitor Security Gaps
When considering your IT inventory from a security perspective, it is not sufficient to just have a comprehensive view of your environment. Qualys CyberSecurity Asset Management (CSAM) applies multiple layers of in-context technical and business data to establish a security view of your IT inventory that enables easy identification of at-risk assets.
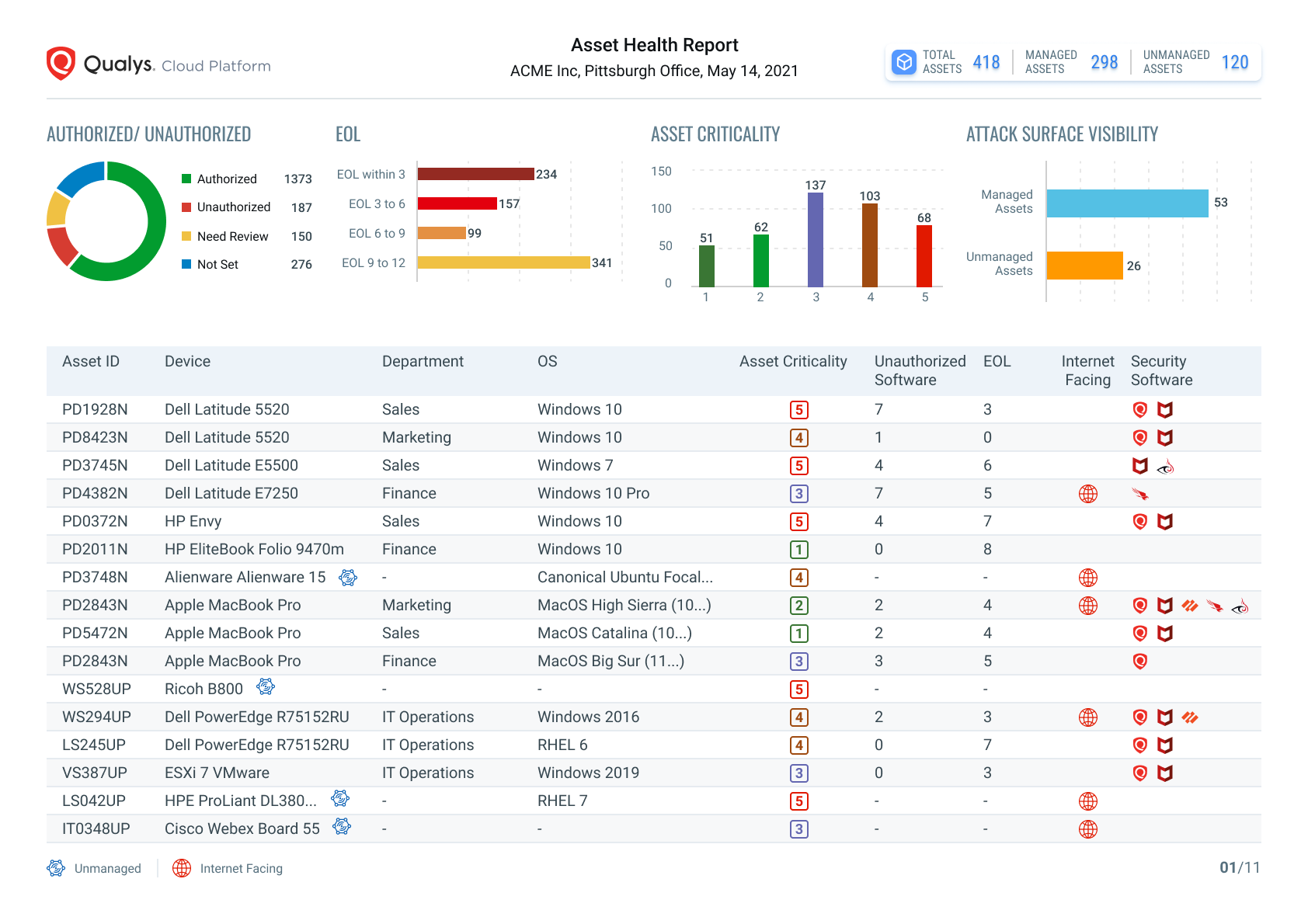
Authorized/Unauthorized Software
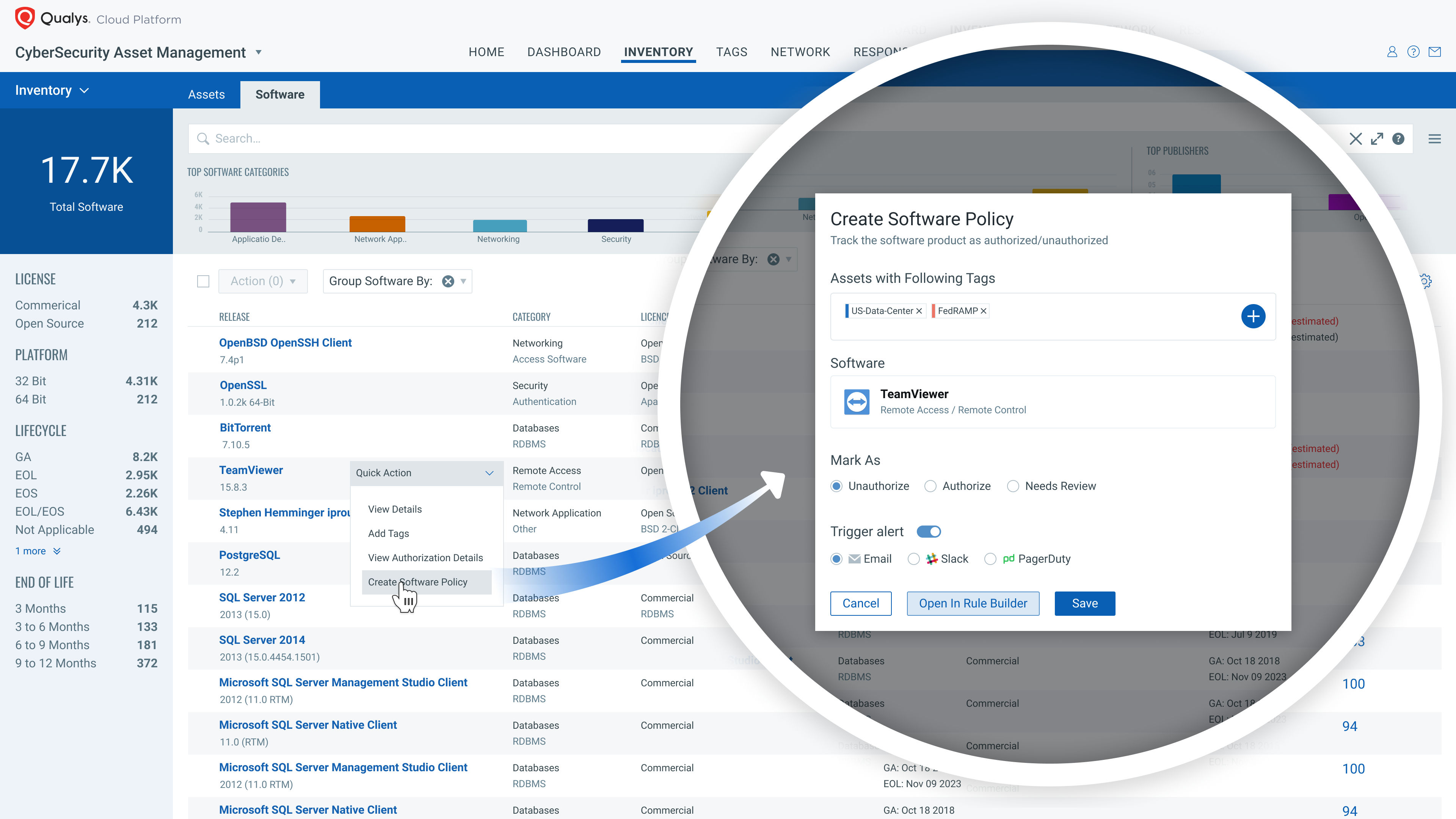
Define and create lists of both Authorized and Unauthorized software and track the result in your IT environment. Proactive tracking of unauthorized and authorized software is a key tool to reduce security risks and improve the health of your inventory. This capability:
- Tracks and reports installations of Unauthorized software based on user defined lists
- Manages Authorized software lists and identifies software not on the list
- Enables the selection of a ‘golden’ image as the basis of your Authorized Software list
- Provides for the creation and assignment of multiple lists based on asset type, location, criticality, and usage
Attack Surface Visibility
Extend Global AssetView’s existing capability of targeted external scans with zero-touch continuous monitoring using Shodan.io data. This uses an outside in view to find assets exposed to the internet, flagging known ‘managed’ assets and as importantly, identifying unknown assets, enabling security risk assessment. This capability:
- Pulls customer-specific public data from sources like Shodan.io
- Displays it in the Asset Inventory and Asset Details
- Creates Unmanaged Assets to track newly identified endpoints
- Enables contextual queries
Identify Blind Spots
Knowing which assets have what security and monitoring tools installed, and which don’t, is an important element of establishing a security position. CSAM can track and identify numerous security endpoints and highlight through dashboards and health reports the breadth of coverage and key assets with missing installations.
Report
Create curated reports and deliver extracted copies to satisfy multiple regulatory requirements. Many governing and standards organizations require structured reports to maintain compliance. Failure to adhere to these requirements can have material impacts on the organization’s ability to continue to work with and operate alongside federal agencies and member organizations.
- Generate a formatted FedRAMP Asset Inventory and Security report
- Create custom reports to satisfy company and regulatory needs, defining asset scope and required attributes
- Schedule reports for periodic generation
Alert, Respond and Monitor
Use configurable policy-based alerts to automatically notify interested parties of at-risk assets. Once the layers of security context are added, the next step is to focus on identifying hardware and software of particular note.
Alerts
Define, schedule and run policy-based alerts on any assets and software in the environment using applied in-context enrichment data to home in on high risk areas. This capability:
- Enables the user to select an asset or set of assets based on hardware & software attributes, e.g. open ports, volumes, hardware and software attributes, then create an alert to notify interested parties.
- Utilize out-of-the-box templates to simplify the creation process
- Send email, Slack or PagerDuty notifications
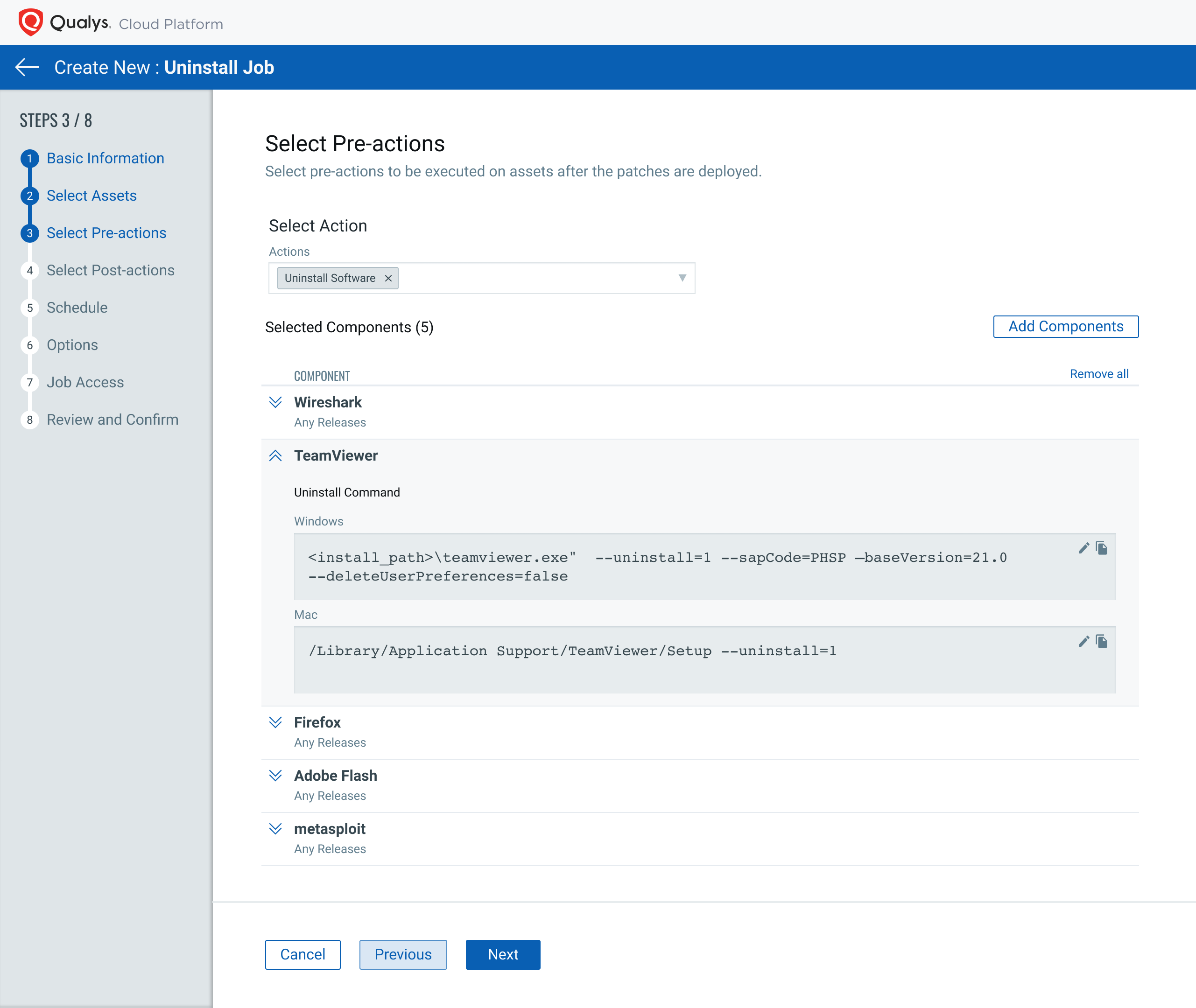
Application Uninstall
Take immediate action to uninstall unauthorized or end-of-life, end-of-service software directly from the CSAM application. Once high-risk software has been identified the next step is to address the issue. One key response is to uninstall the offending application instance.
Remove the application either as a manual one-time action or as part of a policy-based rule. This capability enables the user to:
- Select at-risk software based on Asset Inventory search queries
- Create an Uninstall Job, with multiple steps, including running pre-uninstall and post-uninstall steps, and choosing schedule with blackout windows.
- Enable the user to see the pending Uninstall action
- Enable Policies to periodically and automatically uninstalled designated software
Reinventing Asset Management for Security
With its active and passive inventory sensors, extensive software library and strong query and dashboarding capabilities, CSAM delivers a comprehensive inventory view. Add to that the multiple layers of in-context data and a true security view of your assets, and you get an unmatched visibility into areas of potential risk. Policy based monitoring allows you to focus on the areas of highest need and our uninstall capability lets you respond quickly and easily. Qualys CyberSecurity Asset Management provides a uniquely strong tool for IT security professionals.
Additional Resources
- View the CyberSecurity Asset Management video
- Read our CEO’s blog on CyberSecurity Asset Management
- Details on the Qualys Cloud Platform
- Register for a CyberSecurity Asset Management trial
- To see a demo, watch AssetView Live on demand