Reinventing Cybersecurity Asset Management
Because security teams need their own asset inventory solution
In conversations with our customers, it’s very clear that organizations need to establish a comprehensive view of their IT asset infrastructure because you can’t secure what you don’t know or can’t see. But that comprehensive view needs to be specific to the security team, which has a different role than IT teams concerned with inventory, software support and license oversight. Security teams that rely on asset inventory from their IT counterparts are challenged by a lack of visibility into the security context of their assets.
Visibility into security context is needed for prioritizing the overwhelming number of issues security teams need to address. Understanding the risk context of every asset helps them decide what requires immediate action, and what can be done incrementally or mitigated with other changes or ignored as too low risk.
But security teams don’t just want a list of issues. They need monitoring of changes to the security context of their assets, so they can know when new assets with certain characteristics or risk profiles have been introduced, or when existing assets have changed risk. They need automation when they want it, so that action is taken automatically based on the security risk policies they have put in place. Qualys VMDR will detect software vulnerabilities, but what if the software should have never been installed on that system in the first place? These changes need to be monitored.
Adding security context on an ad hoc basis or manually on top of IT asset inventory doesn’t work. With limited resources on security teams, automated tools are required to achieve the scale and scope of managing small- and medium-sized environments, let alone enterprise-scale infrastructure. Simple policies like “No databases should run on webservers” can become a complex challenge to implement.
Adding the Security Focus to IT Asset Inventory
This is why Qualys has made a large investment in asset inventory in the last few years, and AssetView and Global IT Asset Inventory have gained traction among our customers as a solid asset inventory foundation, all from a unified platform.
Today, I’m excited to introduce Qualys CyberSecurity Asset Management (CSAM), which moves the needle further by adding security context to those capabilities and allowing organizations to detect the security gaps in their infrastructure and respond to the risk. CyberSecurity Asset Management is asset management reimagined for security teams, focused to identify all systems comprehensively, detect at-risk assets, and respond with appropriate actions to mitigate risk.
Identify Assets and Sync with CMDB
The starting point of security programs is to know what you have. By combining agent-based and agentless data collection, active scanning to track known assets, passive scanning to identify unknown assets, and APIs for automation, the Qualys Cloud Platform provides comprehensive asset discovery across your entire infrastructure, including on-premises, cloud, container, OT, and IoT.
Asset data is normalized and categorized, so you can identify assets running databases or hardware/software from specific vendors or asset type like printers. Layered on top of that, synchronization with your CMDB provides additional in-context enrichment data, including organization, owner, location, type of asset (e.g., production or test), which helps identify business-critical assets and tag them automatically.
Detect and Monitor Asset Health
To accurately assess risk and detect at-risk assets, security teams need both breadth of asset inventory data and the ability to correlate it in support of decision making. Qualys leverages the collected, categorized data and enriches it via the Qualys Cloud Platform so the inventory information of these assets can be used to track the health of against organizations’ security policies.
CyberSecurity Asset Management detects the following security context attributes:
- Authorized / unauthorized / required software: Manage whitelists and blacklists, and understand which assets are missing required security and monitoring tools or which assets are running software they shouldn’t be running.
- End-of-life (EOL) and end-of-service (EOS) software: Especially when software is EOS and no more security updates are available, risk is high since mitigations are limited or nonexistent. You don’t want an EOL database running on production systems, and you want to automate the identification from a CMDB perspective.
- Attack surface: Qualys external scanning plus integration with third-party sources like Shodan.io gives an outside-in view based on all the IPs owned by your organization, so you can see which assets in your inventory are visible from the internet.
- Asset criticality: Customize and auto-assign criticality to assets based on their attributes.
Mandates like FedRAMP and PCI require you to track unauthorized software installed and report on it, so you can demonstrate compliance. Reporting includes configurable out-of-the-box CSV extract reports, for example to show FedRAMP inventory.
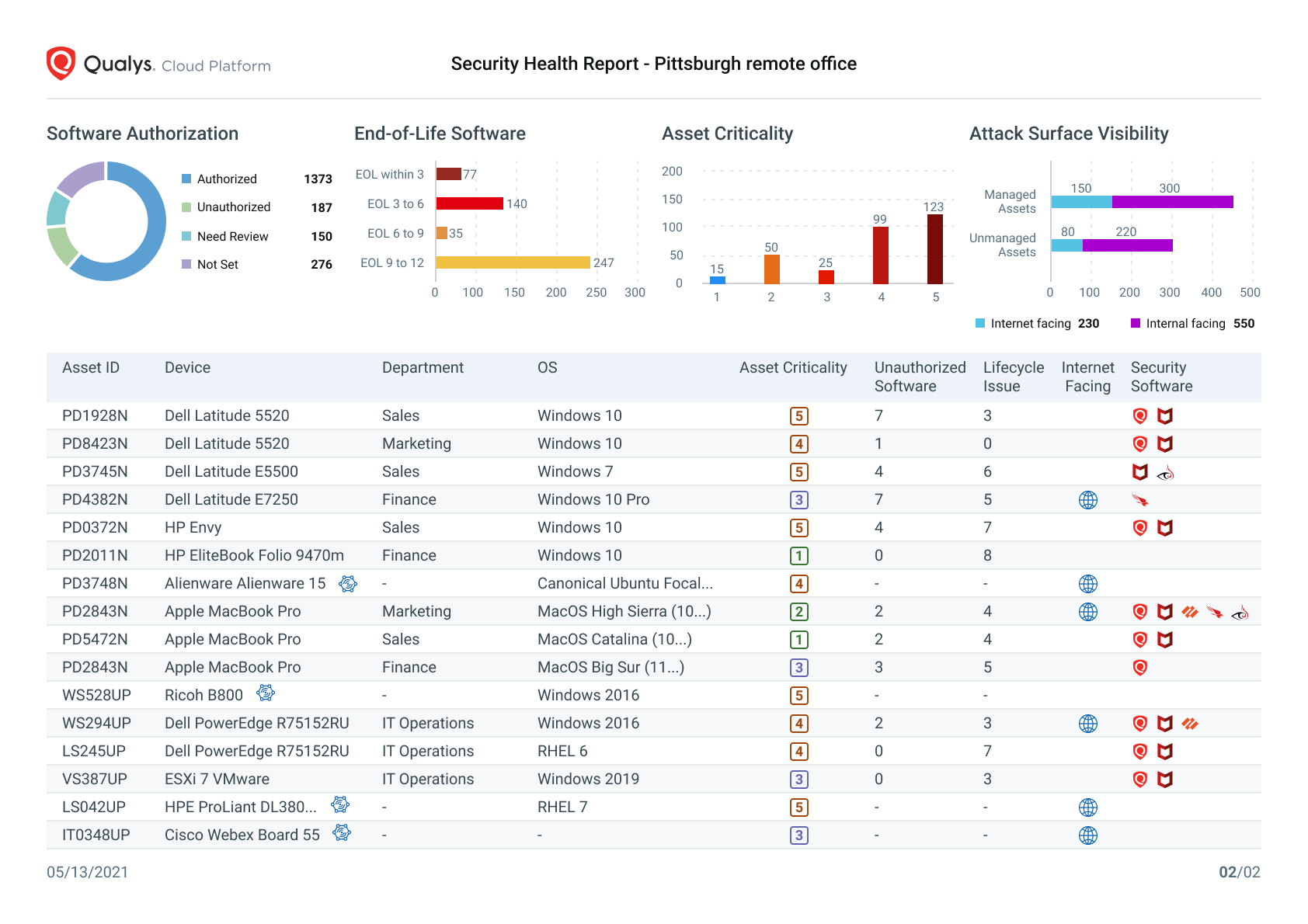
Visual Security Health Reports like the one shown below for an individual company location help to paint the big picture, identify areas for additional analysis, and drive automated alerting.
Respond
Response takes the form of alerts or automated actions. By applying policies to different classes of assets based on their risk and business attributes, you can ensure consistent and immediate response to issues.
Configurable rule-based alerts with out-of-the-box templates send to email, Slack, PagerDuty, etc., so it works however your organization works. Monitoring gives you visibility into changes to key infrastructure and is useful for situations where you want additional analysis before taking action.
To speed response, the next step is to automate the response, especially as teams build confidence after experiencing accurate alerting. If you have a policy that certain software like peer-to-peer or messaging software shouldn’t run on a certain set of production systems, there’s little reason not to automatically uninstall it. Newly found unmanaged assets can be tagged automatically for addition to Vulnerability Management scan jobs.
Simplifying Asset Management for Security
With this announcement, Qualys is simplifying asset management into two components:
Global AssetView is free with any number of agents & passive scanners to give you baseline visibility of your asset inventory.
CyberSecurity Asset Management adds context for security-centric visibility with detection of security gaps and CMDB integration, plus alerting and response.
Because it all runs on the Qualys Cloud Platform with data collected from multiple sensors, your asset inventory is shared across all Qualys apps and provides the foundation for all other security operations you run out of Qualys. You can add additional advanced security visibility with VMDR, patching, and EDR, all from the same Qualys Cloud Agent.
AssetView Live
For a walkthrough of key use cases and a demo of CyberSecurity Asset Management, watch AssetView Live on demand.
Resources
- CyberSecurity Asset Management video
- Technical blog post: Introducing CyberSecurity Asset Management
- Register for a CyberSecurity Asset Management trial
- Watch AssetView Live on demand