A New Approach to Discover, Monitor, and Reduce Your Modern Web Attack Surface

Table of Contents
- Why Web Application Attacks Occur
- Three Strategies to Protect Web Application Assets and Services
- Web Application Discovery and Protection Challenges
- Introducing Qualys External Attack Surface Management (EASM) + Web App Scanning Better Together
- Providing Leading Capabilities with Qualys Web Application Scanning
- Conclusion
Web applications reign the internet universe, but also bring new risks that let attackers poke holes in an ever-expanding attack surface. Stolen credentials have been the historical culprit. Recent analysis saw a spike in exploits targeting web applications directly through specially-crafted attacks against vulnerable source code. According to Verizon in their most recent Data Breach Incident Report (Verizon DBIR 2022), web application attacks are the second most common vector leading to network breaches.
Why Web Application Attacks Occur
Web applications are everywhere, and are targets for theft of personally identifiable information (PII), financial crimes, corporate espionage, spreading malware, and social hacktivism. With 24/7 availability, vulnerable web applications are always at risk of attack by:
- Overlooked Common Web Application Vulnerabilities
Web applications can be pierced in many ways, such as injection attacks and other OWASP Top 10 vulnerabilities. Testing web applications is essential to identify vulnerabilities before they are exploited by malicious actors. - The Forgotten Web Server
As marketing campaigns end, and public-facing web services reach end life, expiring web servers face significant risk. If they are not shut down or software updated, forgotten websites become easy targets for malicious actors. - Unsecured Web Assets and Services
Attackers are constantly searching for vulnerable web assets, and missing just one security flaw could result in a successful attack. Even relying on web application firewalls can be costly as new bypass techniques are routinely shared by criminals online.
Three Strategies to Protect Web Application Assets and Services
Defending modern web applications requires a multi-step plan within an organization’s comprehensive Application Security (AppSec) program. A key new ingredient includes a capability called External Attack Surface Management (EASM). These components enable IT, security and application teams to:
- Build an inventory of all web assets
Effective protection of web assets requires an inventory of all your web applications, including all the domains and their respective subdomains. Many organizations discover that 20-40 per cent of their web assets are not protected by their AppSec program. Quite often teams simply did not know about these assets. With full visibility, you can proactively add the newly discovered web assets to your AppSec program and stop malicious actors in their tracks - Prioritize critical services and web applications
Web applications perform many different business functions, and their categorization can be tailored to specific business needs. By creating appropriate definitions of business-specific categorization of web applications, security and application teams can correlate and understand the business criticality of these apps, and prioritize the largest exposed risks for faster remediation. - Remove vulnerabilities and deploy security measures
Organizations must remediate vulnerable source code to protect their applications from attack. Additionally, many features are designed to protect not only the application but end users as well. Applying these security configurations is paramount to maintaining secure applications.
Web Application Discovery and Protection Challenges
Most organizations today have standalone siloed tools for discovering internal and external web apps. Other related tools may be part of the AppSec program. This melange of so-called “solutions” leads to manual, laborious, and inaccurate ways of correlating data across different tools. As a result, the AppSec team unintentionally misses finding vulnerabilities in critical web apps, which creates more cyber risk.
Discovering all internal and external web assets and operationalizing them in the AppSec program with naively-integrated solutions is the prerequisite to reducing total-cost-of-ownership while reducing mean-time-to-repair.
Introducing Qualys External Attack Surface Management (EASM) + Web App Scanning – Better Together
Qualys CyberSecurity Asset Management (CSAM) continuously discovers and monitors your entire attack surface, including internal known and previously unknown internet-facing assets, across your on-premises, cloud, and multi-cloud environments.
A key component of Qualys CSAM is External Attack Surface Management (EASM). Using your company name or top-level domain (TLD) as a starting point, EASM continuously identifies and monitors all your assets created by subsidiaries, mergers, and acquisitions – including all your web asset domains and subdomains. The information is enhanced with “WhoIs” information, DNS records, and SSL certificate details, which provide the context necessary to understand what these assets are when they were created, and who may manage them.
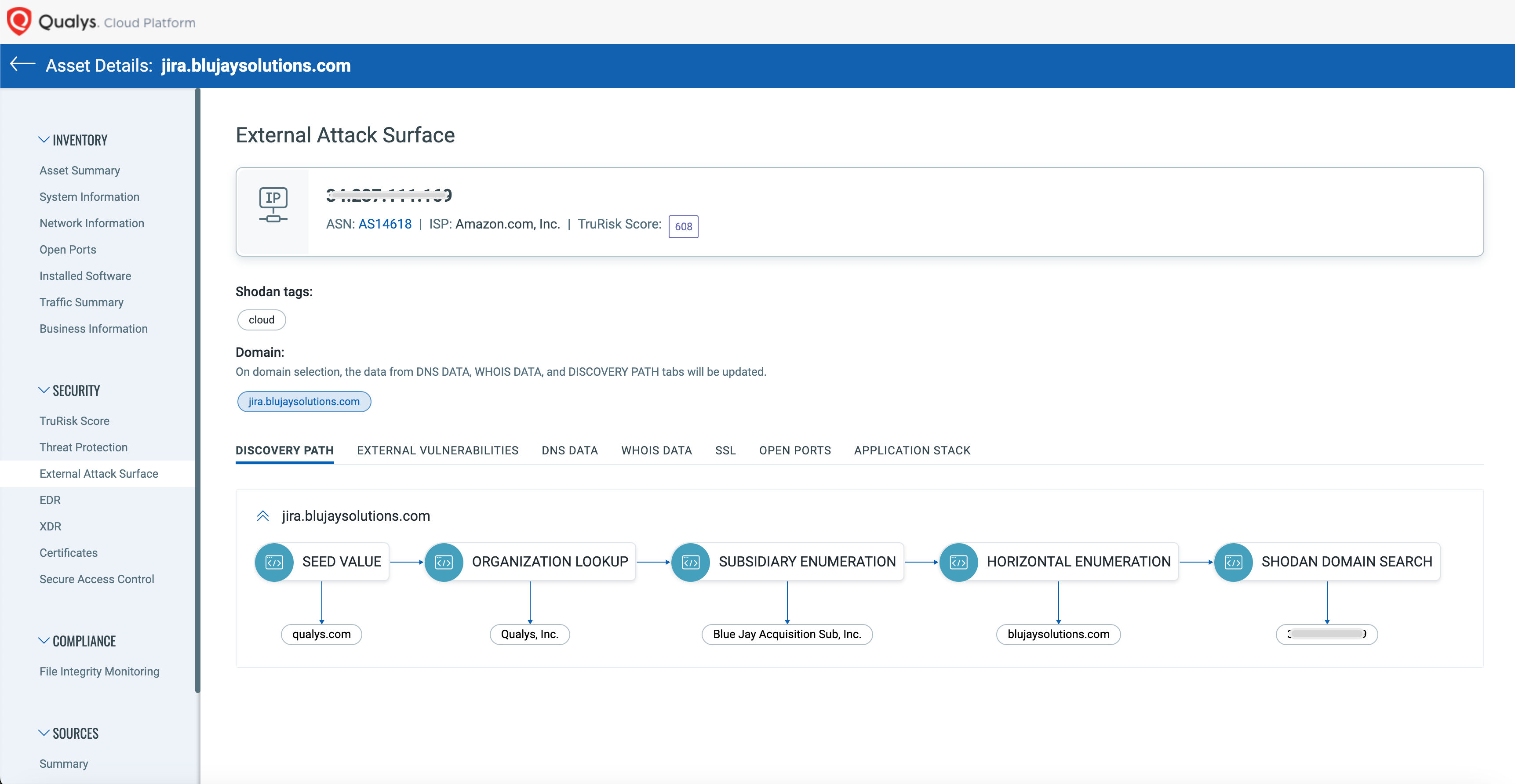
CSAM synchronizes bi-directionally with the enterprise CMDB (Configuration Management Database), enabling IT and security teams to share a single source-of-truth about their assets and applications. Missing assets can be added to your CMDB, while business information about known assets and services, such as ownership and business criticality, can be brought to Qualys to enrich your vulnerability management program.
CSAM categorizes and provides quick visibility of all your web servers by default, both internal and internet-facing external devices.
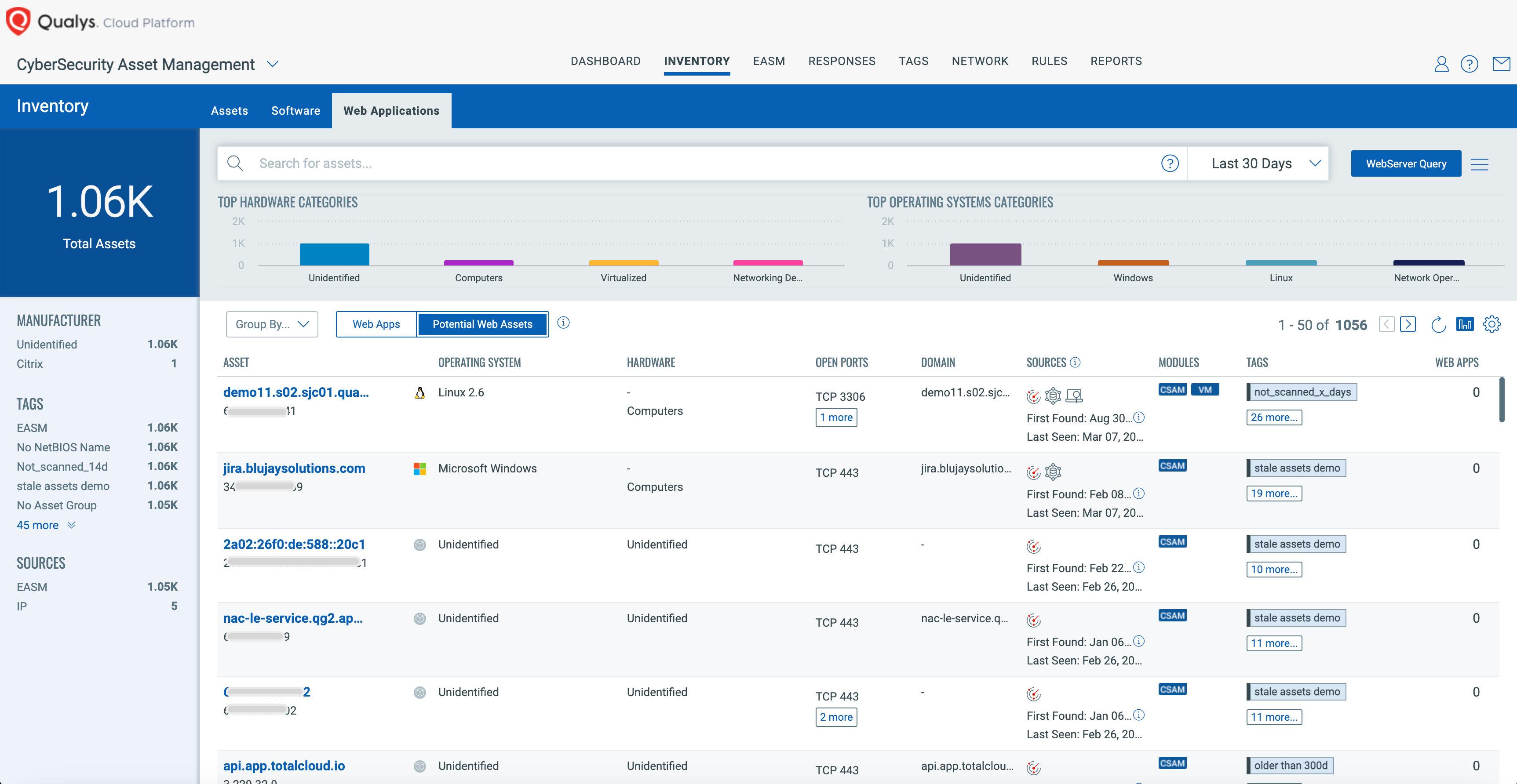
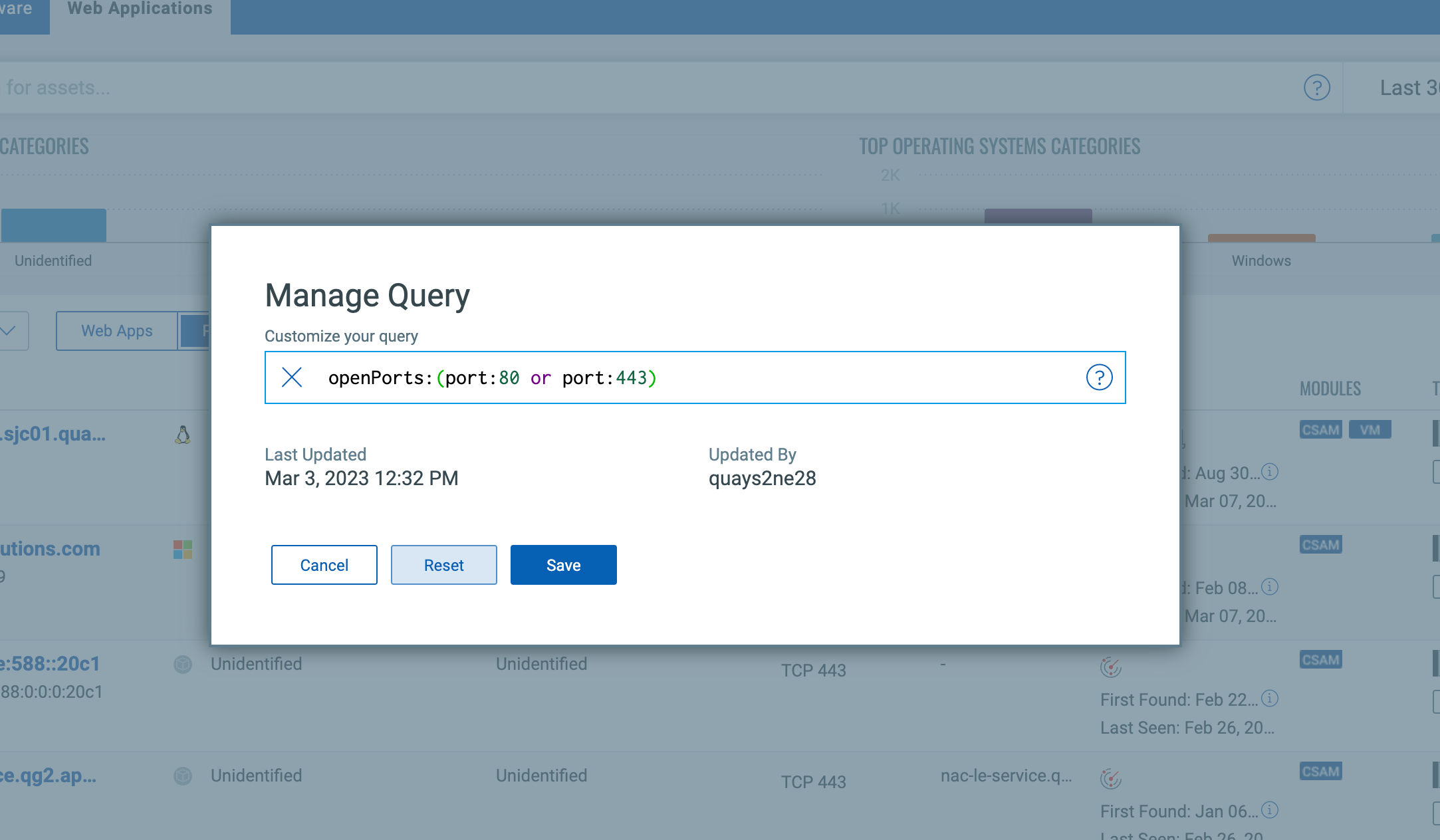
You can easily configure the “Web Server” default filter. For example, listing only Web Servers that are internet-facing and that have an infrastructure risk score of 600 and above.
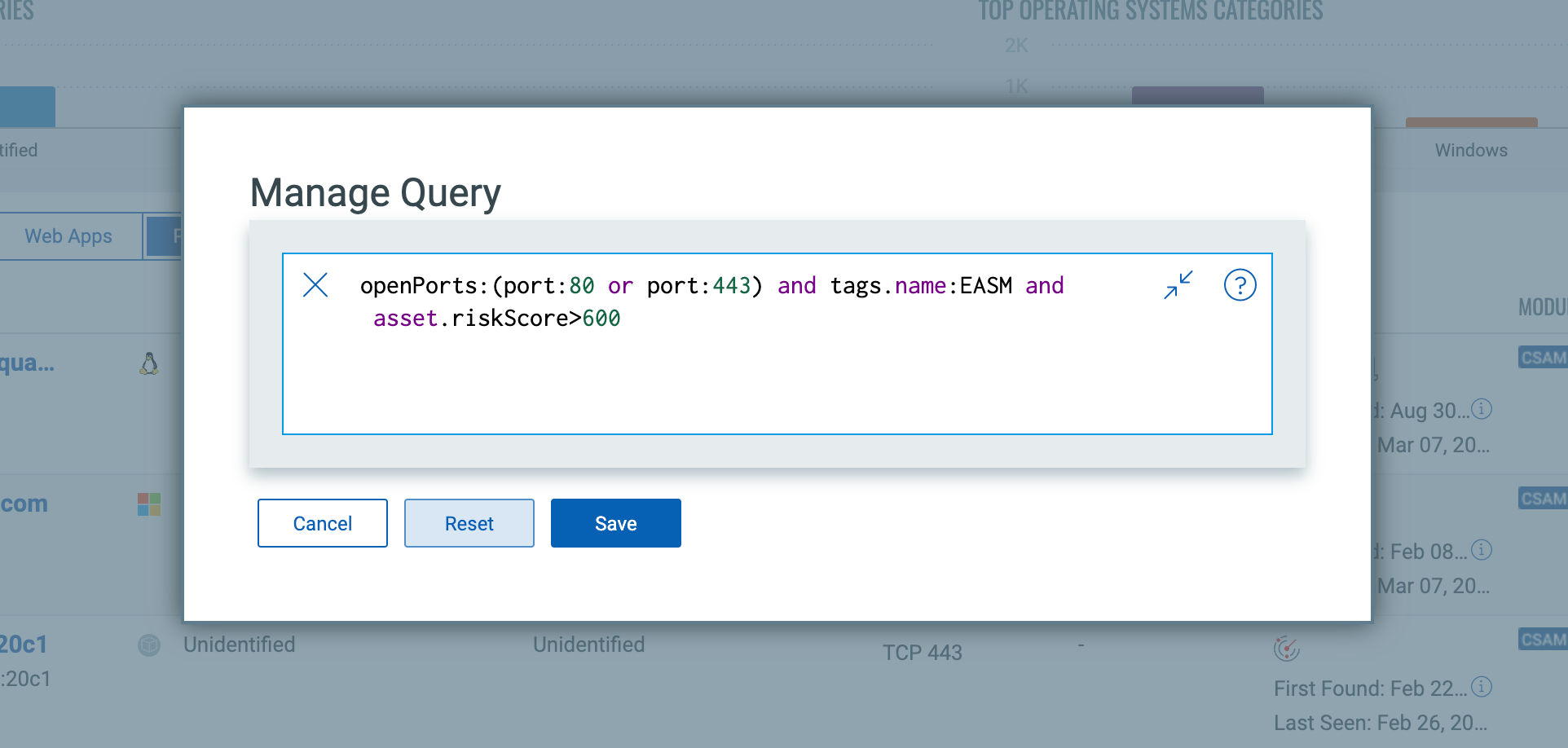
From this prioritized list of Web Servers, CSAM users can easily activate their critical web servers for Qualys Web Application Scanning (WAS).
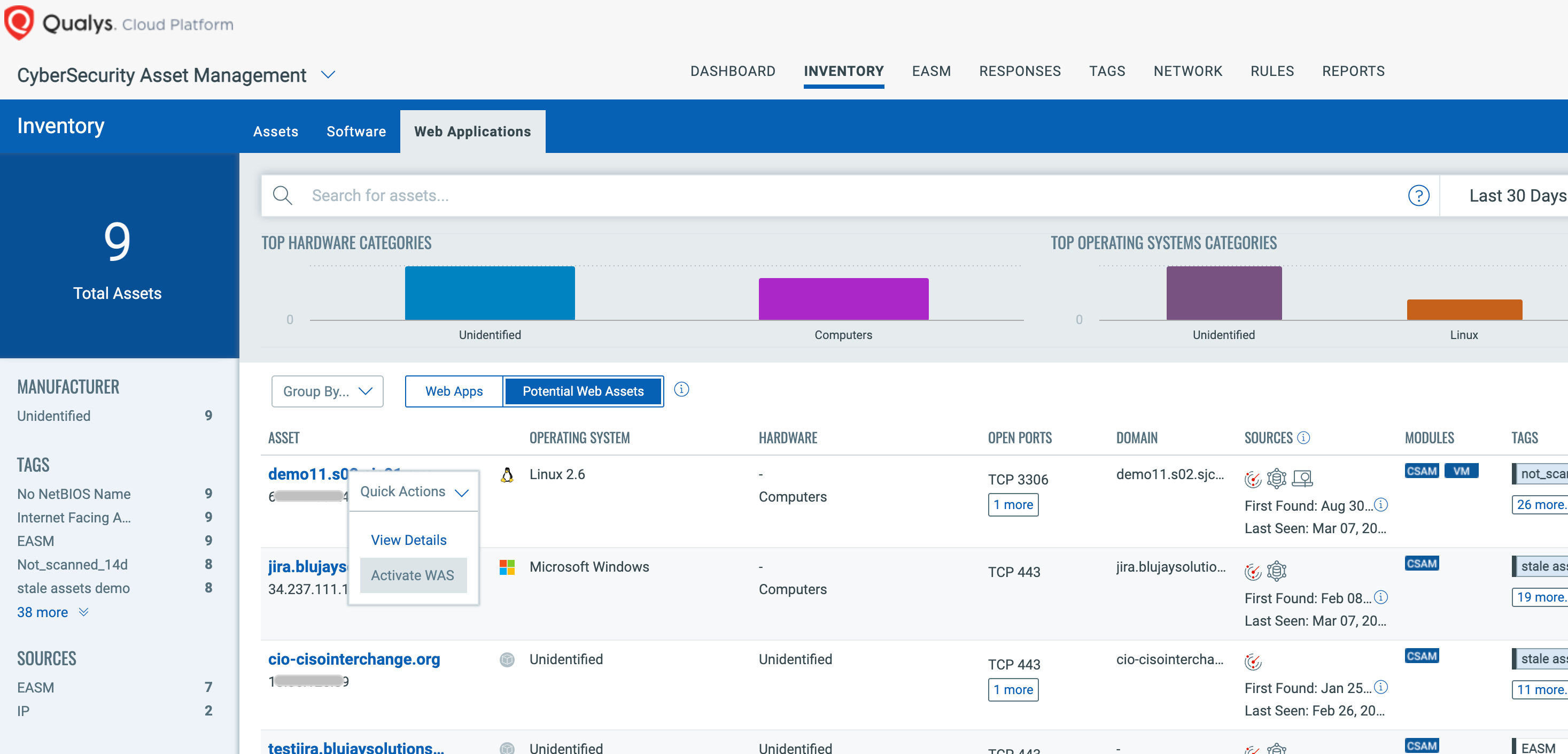
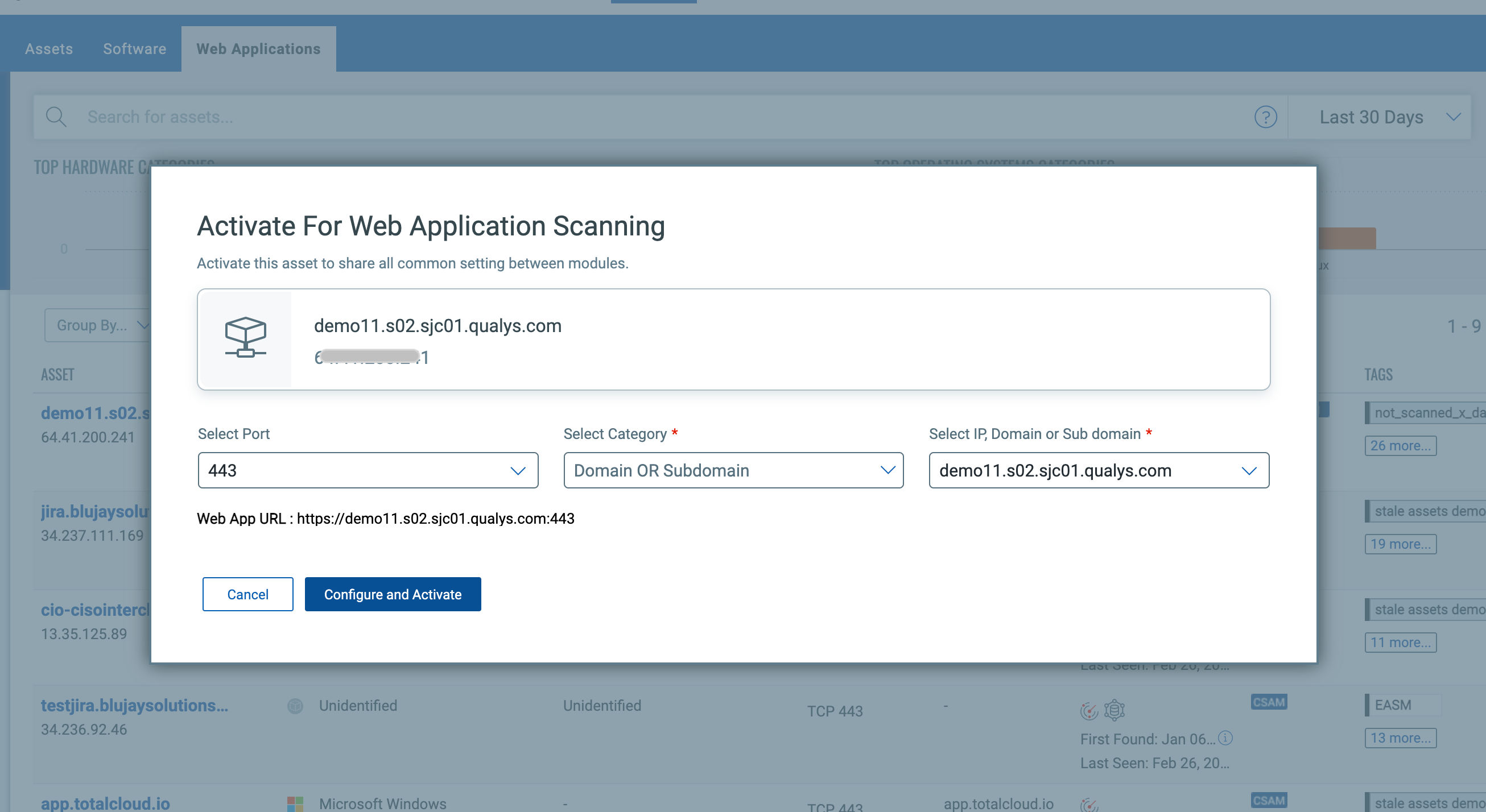
Providing Leading Capabilities with Qualys Web Application Scanning
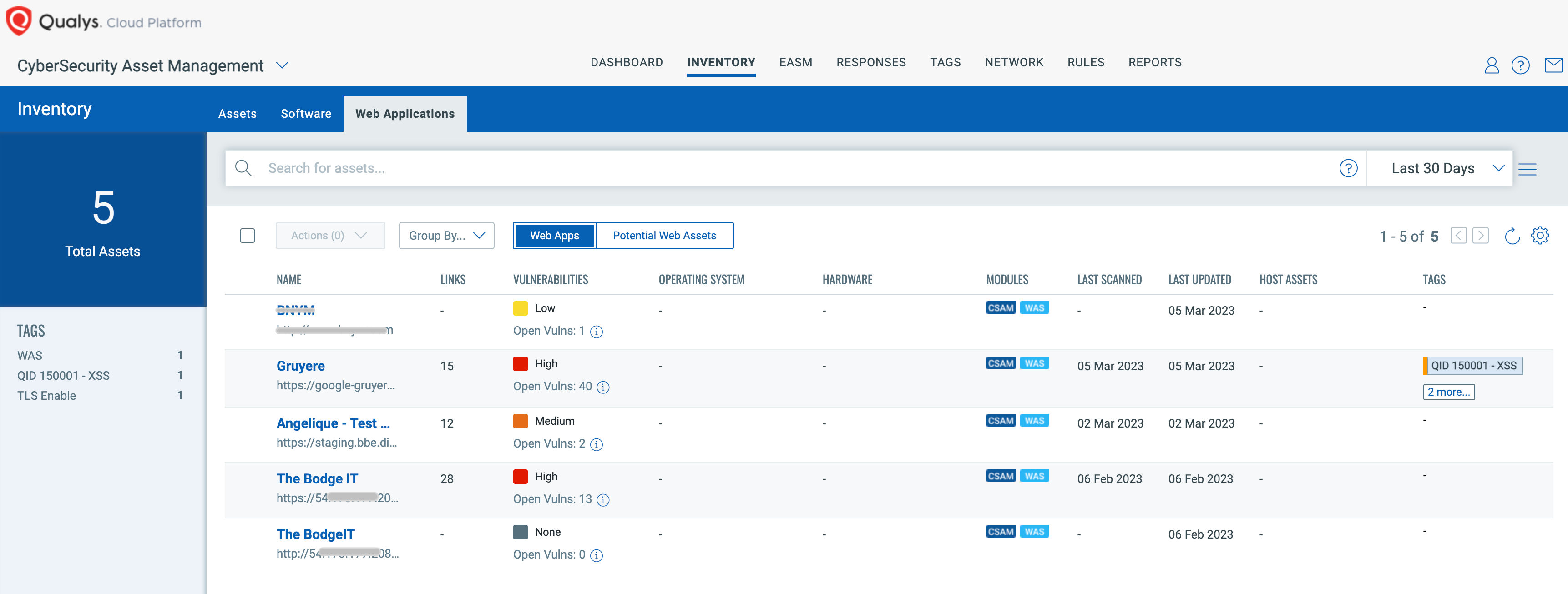
Qualys Web Application Scanning (WAS) provides security and application teams with rich functionality to automatically identify vulnerabilities and guide remediation.
Deep Scanning of Applications
Identify vulnerabilities and security misconfigurations in web applications, such as SQL and XSS attacks as well as other OWASP Top 10 vulnerability categories. In 2022 alone, WAS found over 5 million instances of Broken Access Control (OWASP A01), 4 million instances of Injection (OWASP A03), and over 14 million Security Misconfigurations (OWASP A05) in our customer base.
Perform Dynamic Testing of APIs for Runtime Vulnerabilities
Over 80% of all web traffic is now API traffic, and testing APIs is critical in keeping organizations safe from attack. Identifying API endpoints and their operational methods and requirements is essential for proper testing. WAS quickly and easily imports your OpenAPI / Swagger Files or Postman Collections for complete testing of all API endpoints.
PII Data Collection Detection
Not only will WAS identify exposed PII on web applications, but it can also help discover applications collecting PII. Knowing where PII is collected can help organizations manage their risk to PII exposures by ensuring appropriate logging and monitoring is in place.
Malware Detection
Identify malware infections to protect customers, site visitors, and your company’s reputation. Signatures and reputation checks identify known malware while our proprietary heuristics and behavioural analysis ensure that even new threats are identified and reported.
Conclusion
With Qualys Cybersecurity Asset Management + Web Application Scanning, organizations can secure not only their external attack surface but also their web applications, web servers, and open ports — eliminating all visibility gaps. Get started with protecting your external attack surface and web scanning with a fully integrated solution today to defend all your public-facing assets.
Get Started with CyberSecurity Asset Management with External Attack Surface Management and Integrated Web App Scanning.