Beating the Challenge of Cloud Detection and Response with Qualys TotalCloud Deep Learning AI

Table of Contents
- Limitations of Traditional Endpoint Security Tools in the Cloud
- Growing Threats & Malicious Activities in Cloud
- Hard-to-Detect Modern Cloud Risks
- Managing and Reducing your Cloud Risk with Qualys TotalCloud Deep Learning AI
- Qualys TotalCloud Approach: Applying Deep Learning AI and Analytics to Cloud Security
- Detecting Sophisticated Malware in Containers with Qualys TotalCloud Container Security
- Protecting the Production Environment with TotalCloud Cloud Detection & Response (CDR) at Runtime
- Qualys TotalCloud: A Solution for Detecting Advanced Malware and Network Threats
Let’s go beyond the limitations of configuration management-only, non-cloud-native EDR tools for threat detection & response using deep learning AI.

The global adoption of cloud technology has supercharged agile innovation in virtually every business sector. As a result, organizations are now reaping the benefits of the cloud with scalable, cost-effective solutions that enhance collaboration and mobility, streamline IT management, enable business continuity, and leverage advanced analytics for new business opportunities.

We selected Qualys TotalCloud because of its forward-looking approach to securing multi-cloud environments with unparalleled threat detection capabilities based on advanced deep-learning AI technology.
Mark Wootton
Head of Threat and Vulnerability Management
Centrica
Limitations of Traditional Endpoint Security Tools in the Cloud
Unfortunately, current cloud security approaches that address cloud misconfigurations and vulnerability management do not protect enterprises from active threats. For example, it can take days to patch a vulnerability, and an active threat can target such a vulnerability.
Legacy threat detection solutions, such as endpoint protection platforms (EPP) or endpoint detection and response (EDR), are not cloud-native and require software agents that do not scale in dynamic cloud environments. They are also cumbersome to deploy in the cloud. Qualys has already presented a comprehensive view of vulnerability management addressing similar concerns in this blog.
Threat actors see global cloud adoption as a huge opportunity and seek every feasible way to breach your cloud environment. They may steal sensitive information, demand a ransom, sabotage your operations, or ‘borrow’ your virtual computing resources to mine crypto coins.
Organizations using legacy tools should be concerned about the growing specter of sophisticated cyber threats – especially those with advanced malware. An ELF virus is a malicious piece of code that targets Executable and Linkable Format executables (ELF). This and other hard-to-detect malware challenges traditional security measures and leaves enterprise clouds vulnerable to attack. Many organizations only focus on misconfigurations and vulnerability management, but detection and response of threats must be added for a more complete security solution.
This article describes how Qualys TotalCloud manages and reduces cloud security risk using deep learning artificial intelligence (AI) for advanced threat detection. The solution scans the cloud infrastructure at runtime and in a cloud-native manner, including the container images. With an AI-based approach, security teams can now detect both known and unknown malware from development to runtime, preventing stealthy attacks and reducing the risk of a cloud breach. TotalCloud helps organizations go beyond performing basic cloud vulnerabilities and misconfiguration assessments.
Growing Threats & Malicious Activities in Cloud
Exploitation is often the turning point in most adversary narratives. When the potential gains outweigh the risks, exploitation becomes an inevitable consequence. Data delivered in the 2023 Qualys TotalCloud Research Insights whitepaper reveals that primary threats to cloud assets include crypto mining and malware. Both can establish a foothold within the enterprise cloud environment or enable lateral movement.
Damage caused by crypto mining stems primarily from the wasted use of a compromised organization’s cloud computing cycles. Cryptominers aim to use your cloud resources to generate cryptocurrencies without intending to deposit the coins into your account. An unmitigated crypto mining attack may potentially cost organizations millions due to the associated energy and cloud resource allocation fees. It also disrupts your legitimate use of the resources you are paying for.
Excluding generic coin mining software like XMRig, the most prevalent categories of malware observed in cloud infrastructures include AndroxGh0st/Legion RCE, Denonia, and SCARLETEEL. Findings indicate that the most threatening malware to insecure cloud assets comprises various crypto miner variants.
Hard-to-Detect Modern Cloud Risks
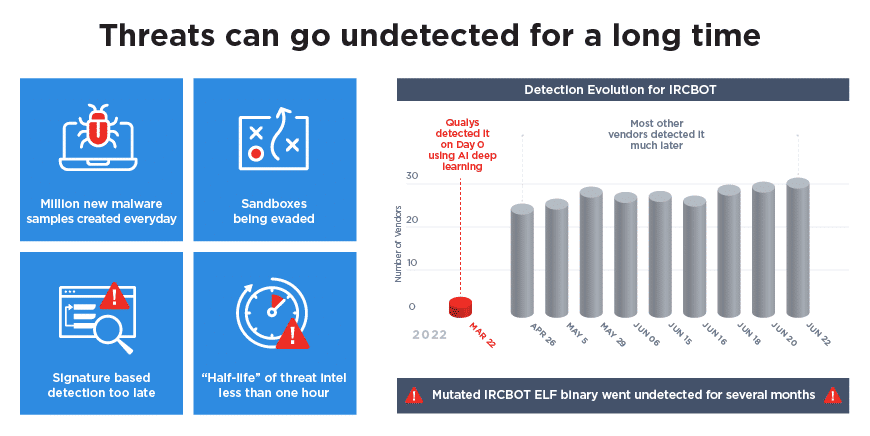
Stealthy ELF malware, commonly found in Linux containers, often evades detection for months (See Figure 1).
The detection time lag underscores the malware’s growing sophistication and highlights the need for more robust detection and mitigation strategies. ELF variants add to the challenge of already difficult-to-detect malware created and unleashed by adversaries. Malware reporting databases, such as VirusTotal, note hundreds of thousands of new malware variants daily. Legacy signature-based techniques simply cannot create and deploy signatures fast enough to prevent malware from infiltrating enterprise clouds.
A new approach is required to address this challenge.
To protect cloud assets from the damaging impact of crypto mining and malware, Qualys AI can detect these threats in less than a second without using legacy signature-based tools.
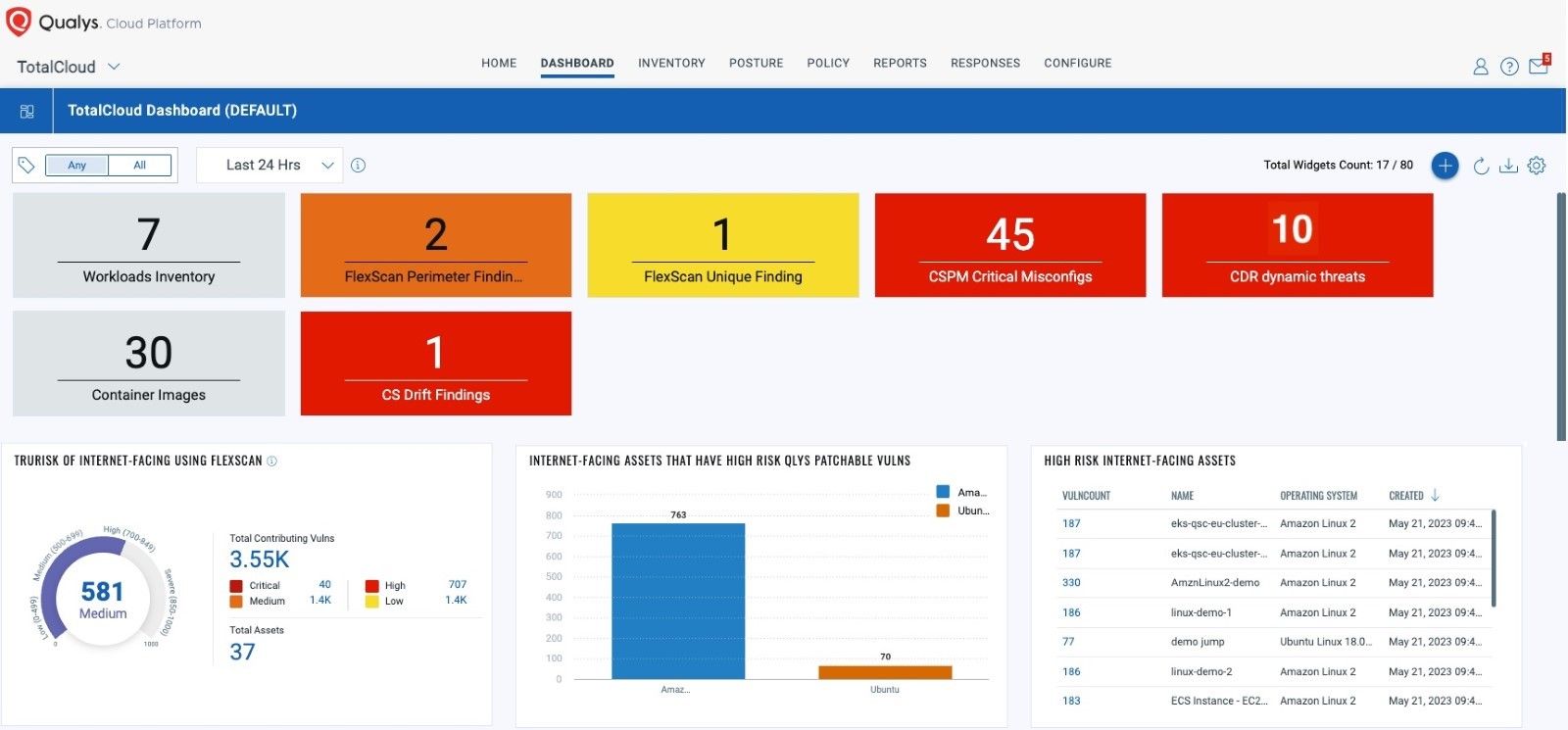
Managing and Reducing your Cloud Risk with Qualys TotalCloud Deep Learning AI
Last November, we introduced Qualys TotalCloud, a CNAPP solution, which is a unified vulnerability, posture, and threat management solution designed to significantly reduce risk for any organization adopting the cloud. TotalCloud use cases include:
- Cloud Workload Protection (CWP) through Qualys Vulnerability Management, Detection & Response (VMDR) with FlexScan
- Cloud Security Posture Management (CSPM)
- Infrastructure as Code scanning (IaC)
- Container Security (CS)
- Cloud Detection and Response (CDR) for active threat detection
powered by deep learning AI.
This article focuses on describing how deep learning AI is used for threat detection in container security and cloud detection and response. As an end-to-end, AI-based cloud security solution, Qualys TotalCloud dramatically improves cloud protection from development to runtime.
The solution uses deep learning AI to detect both known and unknown threats, bypassing the limitations of signature-based systems. Using deep learning AI techniques, TotalCloud can detect unknown malware in less than one second with more than 99% accuracy. As a result, it helps organizations detect and reduce the impact of malware infiltration. Better still, it reduces threat meantime-to-detect (MTTD) to less than a second, radically improving the risk profile for any organization.
Rapid, proactive threat detection has two distinct advantages: Qualys TotalCloud now detects threats using deep learning AI by scanning containers for threats before they are launched. And an agentless deployment allows cloud-native protection at runtime for active threats.
Qualys TotalCloud Approach: Applying Deep Learning AI and Analytics to Cloud Security
Deep learning AI technology is integral to domains such as image recognition, speech processing, and natural language understanding. The technology is also the basis for generative AI and has been used for other predictive use cases.
In the context of cloud threats, Qualys leverages this technology to detect and combat the sophisticated challenges posed by malware embedded in containers. By taking this approach, Qualys can help organizations analyze complex network traffic for malware and network threats.
Deep learning AI’s architecture draws inspiration from the structure and functionality of the human brain. It consists of interconnected artificial neural networks that mimic the intricate connections between neurons in the brain. This empowering architecture can detect elusive cloud threats when applied to cloud security. By training on extensive datasets across diverse examples of malware and normal network behavior, deep learning AI algorithms can identify subtle indicators of malicious activity – even for rapidly evolving malware variants.
This adaptability and capacity for learning from complex data enable deep learning AI to surpass the limitations of conventional, signature-based approaches. It is vital to enabling the sub-second detection of advanced, zero-day malware, which refers to previously unknown and unseen malicious software that exploits vulnerabilities in cloud systems. For network threats, Qualys utilizes this technology and advanced analytics to detect stealthy attacks, such as beaconing.
With these algorithms and advanced analytics, TotalCloud Container Security can help organizations detect malware in containers before containers are executed. TotalCloud CDR can also help them detect real-time malware and network threats.
Detecting Sophisticated Malware in Containers with Qualys TotalCloud Container Security
Organizations can effectively mitigate risks and protect their cloud environments by understanding the container lifecycle and the importance of scanning registries. Qualys Container Security detects malware early in the container lifecycle by scanning container registries using deep learning AI-based malware inspection.
The Container Lifecycle and the Role of Registries
Containers are pivotal in modern cloud environments, enabling applications’ efficient deployment and scaling. The container lifecycle involves several stages: development, testing, packaging, distribution, and deployment. Container registries are repositories for storing container images, allowing easy access and sharing across various cloud platforms. They are integral to the container lifecycle and ensure the availability and integrity of containerized applications.
The Significance of Scanning Container Registries
Scanning container registries is a crucial step in maintaining robust cloud security. Organizations can detect and mitigate potential threats by analyzing container images before deployment. This proactive approach prevents the propagation of malicious or compromised containers, thereby protecting the overall cloud infrastructure. Scanning is crucial for images from public registries. With container registry scanning, organizations can identify security risks and take remedial actions before applications are launched in their production environments.
Container Registries Supported by Qualys Container Security
- AWS Elastic Container Registry (ECR): AWS ECR is a fully managed container registry service that enables developers to store, manage, and deploy container images on the Amazon Web Services (AWS) platform.
- Azure Container Registry (ACR): Microsoft Azure provides a cloud-based container registry that offers secure storage and management of container images for Azure-based applications.
- Google Artifact Registry (GAR): GAR is Google Cloud’s next-generation container registry, designed to host, manage, and deploy container images for applications running on the Google Cloud Platform (GCP).
- Docker Hub: Docker Hub is a public container registry that provides a vast repository of container images and serves as a centralized hub for developers to share and distribute containerized applications.
- JFrog Container Registry: JFrog Container Registry is a universal, hybrid Docker registry that offers centralized control and security for container images. It also supports integration with various cloud platforms and DevOps tools.
The integration of Qualys TotalCloud’s deep learning AI with container registry scanning enables organizations to identify malicious content before deploying containers. Once the malware is detected in the scanned container image, a security team can easily identify the detected malware image and ask stakeholders to fix and remediate this issue. Early detection of malware in the ‘Registry’ stage also prevents the overhead of malware remediation and saves resources, such as time and labor.
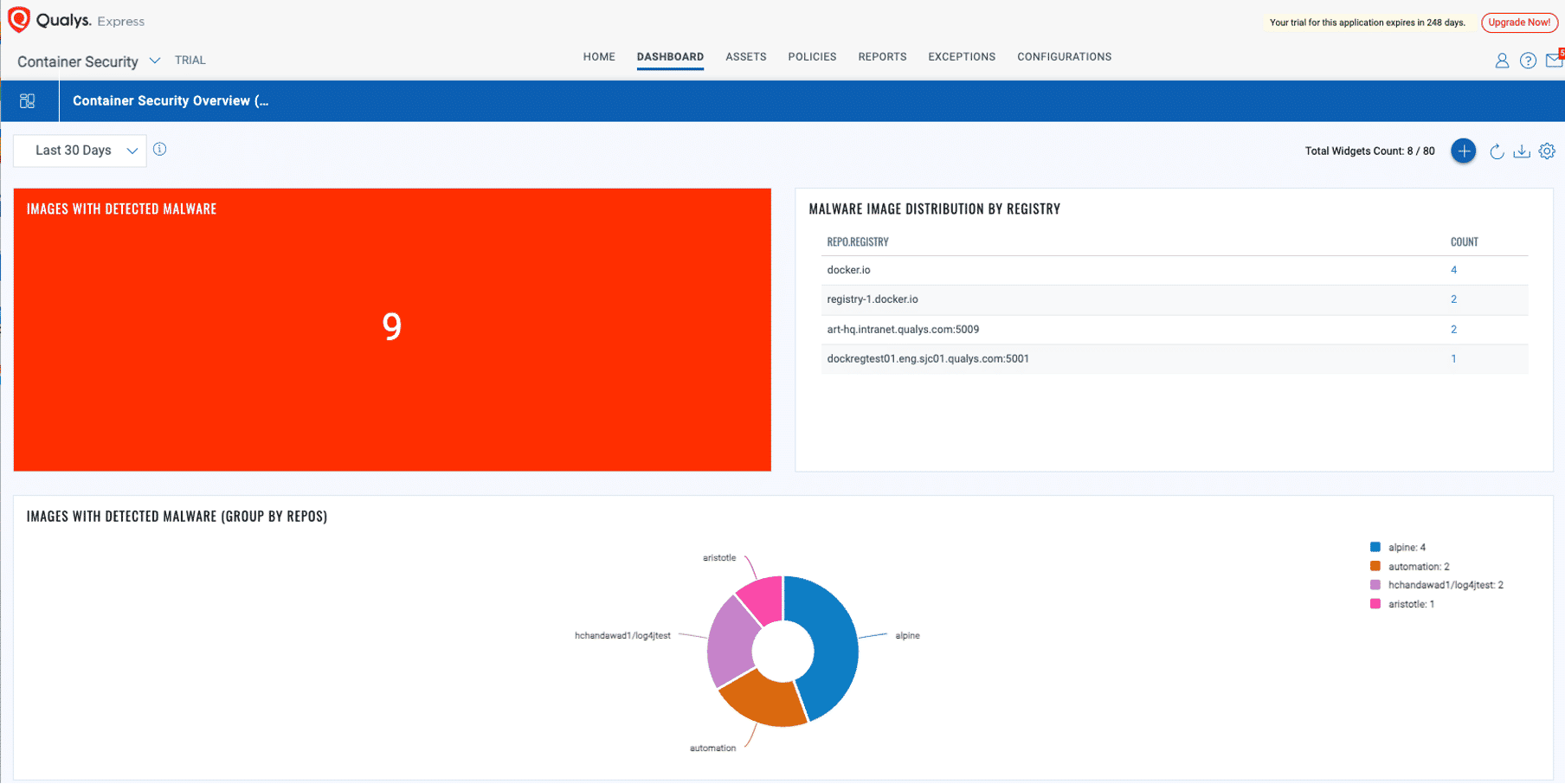
Protecting the Production Environment with TotalCloud Cloud Detection & Response (CDR) at Runtime
Qualys TotalCloud also offers advanced threat detection capabilities that extend beyond pre-deployment scanning. During virtual machine operation, Qualys Cloud Detection and Response (CDR) leverages deep learning AI to analyze network traffic and immediately detect potential threats.
CDR provides a comprehensive view of the cloud kill chain, detecting threats by using deep learning AI across all parts of the chain:
- Detection of suspicious communications includes horizontal and vertical port scans. With Qualys TotalCloud, you can determine if the virtual machine also has critical vulnerabilities that require prioritizing its remediation ahead of others.
- Detection of unauthorized activity, such as brute-force attacks on ssh and RDP, and port scans indicating lateral movement. This feature allows you to detect lateral movement in the organization when an attacker is attempting to infiltrate other virtual machines.
- Detection of cryptominers that attempt to use cloud resources to mine cryptocurrencies. Qualys TotalCloud CDR identifies the cryptominer.
- Detection of command-and-control communications, including subtle and stealthy beaconing attacks. Qualys TotalCloud CDR can even detect communication to malicious servers that may not be well known or exist in most databases.
- Detection of malware downloaded, including zero-day and malware variants. The exact deep learning AI-based detection we use in container security is used in Qualys TotalCloud CDR.
Beaconing attacks involve periodic and discreet communication between compromised hosts and command-and-control (C2) servers. To obfuscate their activities, attackers often employ Domain Generation Algorithms (DGAs) to dynamically generate numerous domain names. These domains serve as rendezvous points for malware-infected systems to receive instructions from the C2 servers. Such malicious beaconing detection is not based on prior knowledge of malicious domains.
Qualys CDR excels at recognizing subtle patterns associated with low- and slow-beaconing activities, even when DGAs are involved. By detecting and analyzing these behaviors, Qualys TotalCloud provides an additional layer of protection to enable prompt identification and response to potential threats during runtime. Once such workloads have been identified, it is critical to stop these workloads immediately. The Qualys TotalCloud dashboard provides a remediate action that allows you to point to the identified workloads and prevent them from running to reduce any further damage to running workloads.
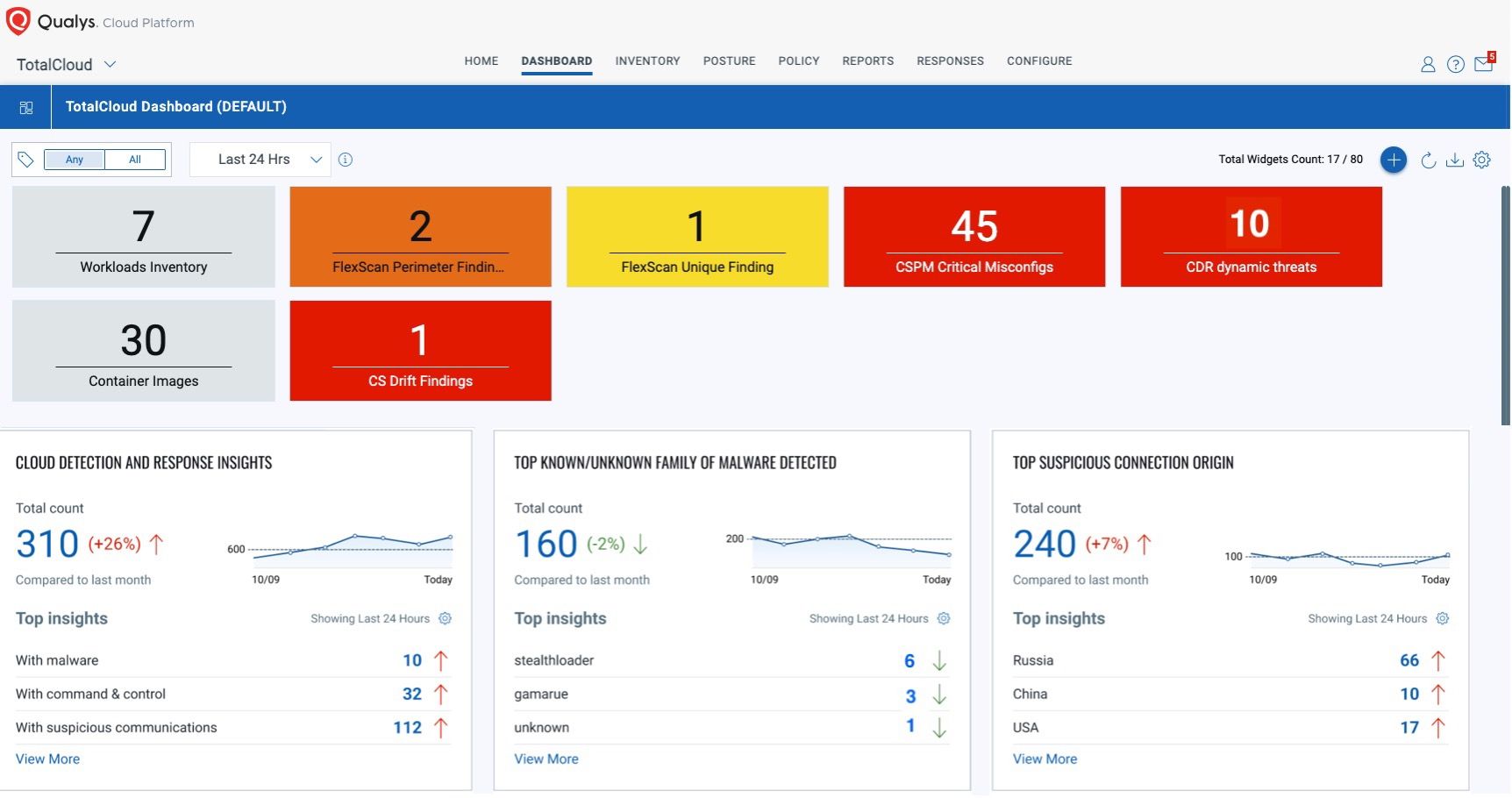
Using deep learning AI, Qualys CDR can detect malware across your cloud environment. For example, if an active virtual machine downloads any type of malware, including backdoor, ransomware, or Trojan, it will then continue to download other malware to cause further damage. All these types of malware can be detected in less than a second using Qualys TotalCloud’s dashboard for rapid response. Typically, such malware can take hours and sometimes days to detect, as shown in Figure 1.
Qualys TotalCloud: A Solution for Detecting Advanced Malware and Network Threats
By leveraging deep learning AI capabilities in Qualys TotalCloud, organizations can enhance their cloud security posture by proactively detecting and mitigating advanced threats. With Qualys TotalCloud Container Security, organizations can detect malware in container registries prior to execution. And with Qualys TotalCloud CDR, organizations can detect malware downloads on workloads and network activity, such as beaconing attacks in real-time.
Keep ahead of threat actors. Sign up for a TotalCloud trial and see how Deep Learning AI can protect you.
Start your free trial today—no software to download or install.
Email us to request a quote, or call us at 1 (800) 745-4355.
Hi Nayeem – great blog. I wonder how Qualys TotalCloud CDR deep-learning approach detect a malware that does not infiltrate by being embedded in a container image but rather via. a zero-day vulnerability in a library used by an application container which is exposed by application API and abused by a malicious actor?