Meeting FISMA (M-24-04) Requirements with a Unified Attack Surface Management Strategy

Table of Contents
- A foundation for Zero Trust
- Complete inventory of IoT/OT devices
- Continuous visibility of the external attack surface
- Identify HVAs (High Value Assets) and produce regular risk reports
- Document a risk-based approach to VM and remediation
- Meeting FISMA (M-24-04) requirements with CyberSecurity Asset Management
At the end of 2023, the Office of Management and Budget (OMB) released the FY24 FISMA Guidance (M-24-04) with a broad focus on securing the entire attack surface and specific action items for agencies pertaining to High Value Assets, IoT/OT devices, and internet-connected assets.
In reference to recent supply chain attacks, zero-day exploits, terrapin attacks, and a host of other risks associated with previously trusted systems, the Administration calls for “modernization of Federal systems in accordance with zero trust principles that acknowledge threats must be countered both inside and outside traditional network boundaries.”
The requirements turn a critical eye toward agencies’ attack surface management programs—calling for 100% visibility of cyber assets (including IoT/OT and external assets), risk assessment of HVAs (High Value Assets), and a foundation for Zero-Trust Architecture.
Qualys customers are uniquely positioned to comply with the requirements and secure their attack surface using a single platform. This post will address the primary requirements point-by-point.
Join our webinar on June 20, 2024 to learn how to jumpstart FISMA (M-24-04) leveraging the Qualys Enterprise TruRisk Platform.
Let’s separate the memo into subject areas pertaining to attack surface management. There are five primary focus areas that we will explore.
A foundation for Zero Trust
M-24-04 builds from M-22-09, requiring agencies to implement benchmarks according to the NIST Cybersecurity Framework (CSF) Zero Trust strategy. More specifically, “The Federal Government no longer considers any federal system to be ‘trusted’ unless that confidence is justified by clear data; this means internal traffic and data should be considered at risk.”
To satisfy that mandate, agencies must have three things that CSAM provides:
- Comprehensive visibility—including internal and external-facing assets, on-prem, cloud, IoT/OT.
- Complete business context—such as asset criticality and dependencies, user privileges, owner, department, location, environment, etc.
- Cyber risk assessment—associated vulnerabilities, EoL/EoS, risky ports, missing security agents, etc.
The Federal Government describes Zero Trust by saying, “…confidence must be justified by clear data.” With CSAM, agencies can provide that justification by answering the following questions for every device:
- What is the device?
- What software/OS is it running?
- What vulnerabilities and misconfigurations are on the device?
- Is the device under management?
- Who is the user?
- Does the user have access?
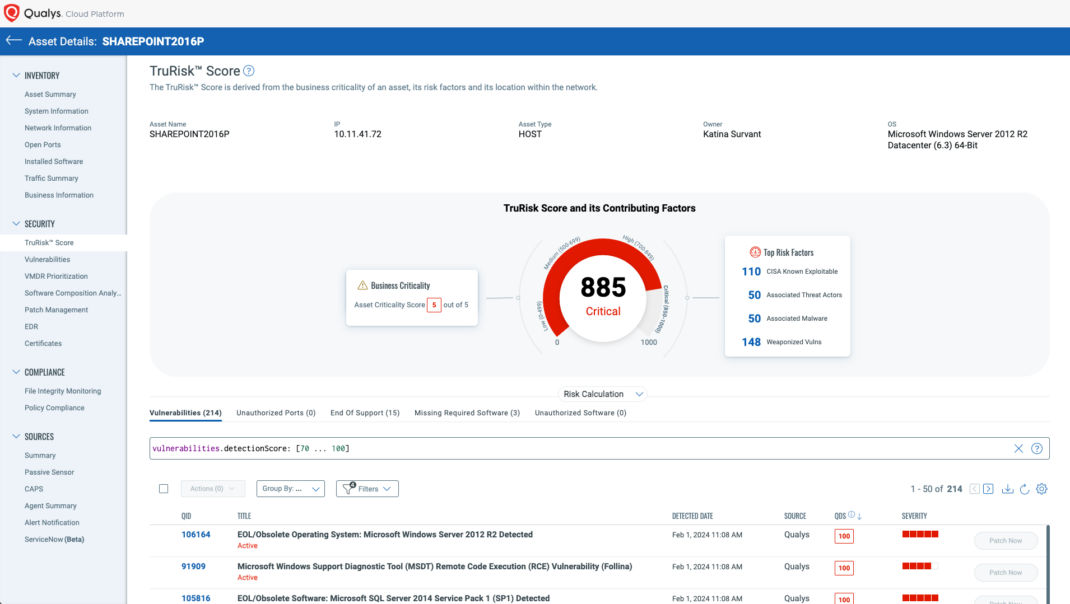
These are essential questions for your attack surface management program and set the foundation for agencies to implement federally required Zero-Trust policies.
Complete inventory of IoT/OT devices
Section 2 of the memo directs agencies to demonstrate a “clear understanding of devices connected within their information systems to gauge cybersecurity risk.” OMB spells out, in no uncertain terms, that by the end of 2024, agencies must maintain a real-time inventory of IoT and OT devices along with these specific attributes:
- Asset Identification
- Asset Description
- Asset Categorization
- Device Owner
- Vendor/Manufacturer Info
- Software/Firmware Versions
- Network Connectivity and Integrations
- Security controls
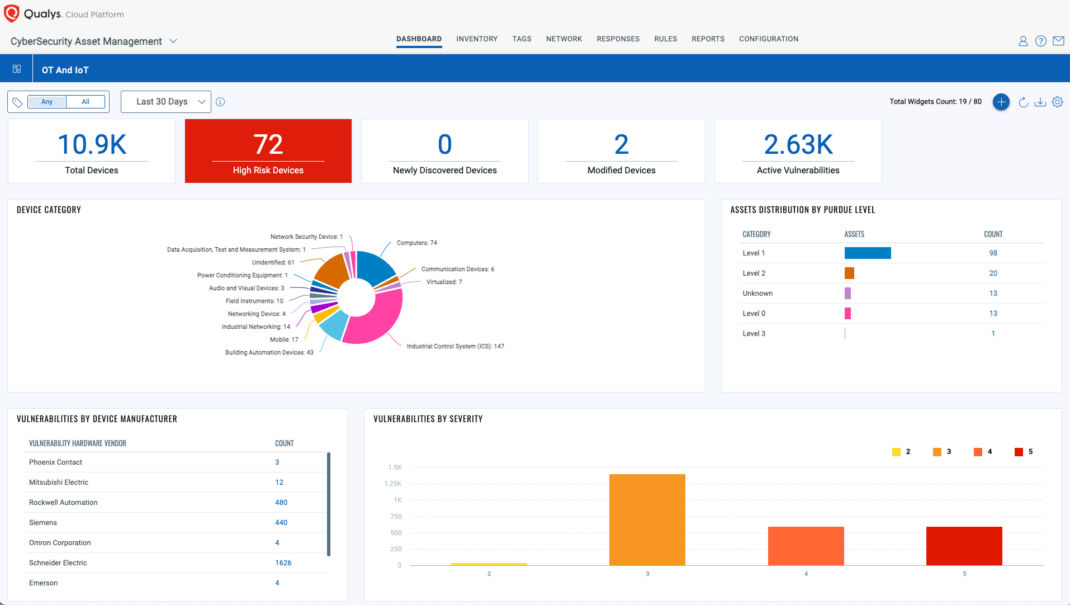
Many organizations struggle with visibility into IoT and OT devices. CSAM has recently bolstered coverage for these devices with Cloud Agent Passive Sensing, discovering IoT and rogue devices connecting to the network in real time. Qualys customers can also leverage OT passive sensors to cover all attributes above for OT devices.
The key for maintaining a real-time inventory is to combine coverage from numerous discovery methods. Scanning, on its own, won’t satisfy the IoT/OT requirements. The same goes for third-party integrations. Combining these methods with passive sensing will identify all of these devices in the environment along with cyber risk assessment—with data in a machine-readable format for reporting to the federal government.
Continuous visibility of the external attack surface
In alignment with BOD 19-02, agencies must provide CISA “a complete list of internet-accessible Federal information systems, including static IP addresses for external websites, servers, and other access points, and DNS names for dynamically provisioned systems with 5 business days of any changes.” This translates to real-time visibility of external assets along with machine-readable reporting to CISA.
Just as there are data collection and reporting requirements for IoT/OT devices, there are similar guidelines for internet-facing assets. In addition to a complete inventory, agencies must provide:
- Static IP addresses for external websites, servers, or other access points
- DNS names for dynamically provisioned systems
- Notice of changes to IP ranges within 5 days of the change
That requires agencies to maintain (close to) real-time inventory of external assets from subsidiaries, hybrid work, BYOD, and all other sources of potentially unknown assets.
External Attack Surface Management (EASM) is built natively into CSAM and has already discovered over 100,000 domains and nearly 3 million subdomains for thousands of Qualys customers. That means agencies can continuously identify previously unknown systems, including DNS and WHOIS records, to meet CISA reporting requirements for “internet-accessible Federal systems.”
Identify HVAs (High Value Assets) and produce regular risk reports
OMB and CISA are “using CIO metrics reporting to track implementation of NIST standards,” requiring agencies to update metrics outlined in previous OMB memos and Executive Orders. M-24-04 specifically references OMB Memo M-19-03 and BOD 18-02 as they pertain to reporting on High Value Assets (HVAs). Here are the areas that agencies need to quantify for CISA:
- A complete inventory of HVAs with business/agency context
Designated HVAs must be reported to DHS and participate in assessments. CSAM can track critical assets (designated or tagged as HVAs) in a CISO dashboard to remain audit-ready. - Quantified risk to critical assets
Risk to HVAs might include unauthorized software, risky ports, missing security agents, EoL/EoS, critical vulnerabilities, or other misconfigurations. CSAM incorporates these risk factors into an overall TruRisk Score for every asset, which leads to the next requirement. - A means of prioritizing risk to the agency
Agencies must focus on critical risk, especially as it pertains to HVAs that could compromise agency security or data privacy. TruRisk Scoring allows agencies to measure, communicate, and eliminate risk with a clear understanding of risk factors and dependencies for each individual HVA. - Reporting on risk reduction
Many agencies currently struggle to quantify risk reduction. They can report on patches deployed and specific actions, but TruRisk allows them to measure their improvement in security posture across the org and as it pertains to groups of assets (such as HVAs). CSAM allows you to share remediation reports to your CMDB tool and create custom dashboards for HVA risk over time for federal compliance.
Document a risk-based approach to VM and remediation
OMB specifically cites “the Administration’s shift in focus from compliance to risk management.”
That means agencies need a risk-based approach to attack surface management, vulnerability management, and remediation.
“Risk-based Vulnerability Management” is a major emphasis for Qualys and the Enterprise TruRisk Platform, with a focus on measuring, communicating, and eliminating risk across the organization.
CSAM provides a complete asset inventory along with risk assessment—this is the measure component of Risk-based Vulnerability Management. For government agencies, this means monitoring and measuring risk to HVAs, including vulnerabilities, misconfigurations, and other risk factors covered earlier in this post.

Communicating that risk to internal stakeholders, compliance auditors, and Homeland Security is another key element for agencies. CSAM provides out-of-the-box CISO dashboards, compliance reports, EASM reports, and risk reduction reports—along with data mapping to CMDB tools. All reports can be scheduled and shared in machine-readable format to meet OMB and NIST requirements.
Of course, Eliminating cyber risk is the ultimate goal of federal mandates, which is why Qualys provides one-click workflow to VMDR, Patch Management, and CMDB tools to streamline and report on the remediation of business-critical risks. Government agencies can easily track and document risk reduction to HVAs with Qualys.
Meeting FISMA (M-24-04) requirements with CyberSecurity Asset Management
OMB emphasizes risk profiling and reduction of the complete attack surface, with a specific focus on IoT/OT and external assets. In order to meet federal mandates, agencies need a consolidated approach that includes external discovery scanning, passive sensing for network metadata, and detailed risk profiles of all cyber assets—especially critical or High Value Assets. Rather than piecing together point solutions and mismatched data for different asset types, government agencies should consider the strongest consolidated solution to build a complete asset inventory.
In addition to providing versatile discovery methods, CSAM is built natively into the Enterprise TruRisk Platform, which includes VMDR, Policy Compliance, and Patch Management. By consolidating their cybersecurity program with this foundation, agencies have achieved the following:
- Up to 80% reduction in data breaches related to IT/OT and High-Value Assets
- 55.5% average reduction in cyber risk
- 92% reduction in MTTR (90 days to 7 days)
- 30% improvement in compliance with regulatory requirements
- 20% reduction in cost and operating deficiencies
Try CSAM at no cost for 30 days
Additional Resources
Learn more about Cloud Agent Passive Sensing for IoT
Request a tailored External Attack Surface Management Report for your agency