QScanner: Features, Benefits, and How It Works for Container Image Scanning

Securing container images is more important than ever in the dynamic world of cloud-native technologies. Organizations have long utilized reliable solutions from Qualys to scan their images, ensuring applications run smoothly and securely. These tools have played a crucial role in maintaining the integrity of systems across various environments.
But what if securing your container images could be even sleeker?
Introducing QScanner.
QScanner is a spectacular command-line utility that transforms the way you scan for vulnerabilities. By providing inline vulnerability reports directly in your command-line interface, it integrates effortlessly into your existing workflow. Designed with enterprise needs in mind, QScanner enhances your security measures without adding any extra footprint to your ecosystem.
With QScanner, you’re empowered to maintain robust security while enjoying a more streamlined and efficient scanning process. It’s not just a tool; it’s a new approach to container image security.
Container Security Capabilities of QScanner
Identifying Vulnerabilities and Managing Risk with QScanner
QScanner identifies vulnerabilities in OS and software packages within your container images. Leveraging the same trusted engine with 99.99966% Six Sigma accuracy, maintained by over 35 threat feeds and our remarkable threat research team, QScanner ensures highly accurate and reliable vulnerability detection. It performs comprehensive Software Composition Analysis (SCA), supporting language-based packages for Ruby, Rust, PHP, Java, Go, Python, .NET, and Node.js. This thorough analysis helps you detect and remediate security issues in your software dependencies, ensuring your applications are built on a secure foundation.
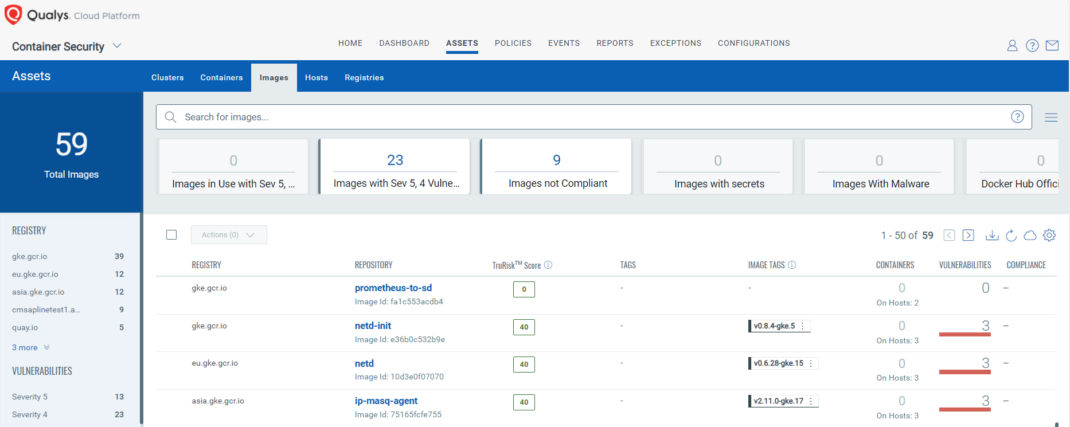
The vulnerabilities detected by QScanner also contribute to calculating the TruRisk™ score for your images. This score provides a quantifiable measure of the risk associated with each container image, allowing you to prioritize remediation efforts effectively. Understanding and acting on the TruRisk score can enhance your security posture and mitigate potential threats more efficiently.

Protecting Container Secrets from Unauthorized Access
Container secrets – such as passwords, API keys, and tokens – are digital credentials that authenticate identity and authorize access to privileged accounts, applications, and services. If these secrets are not properly secured within container images, they can be accessed by unauthorized users, leading to malicious attacks. QScanner proactively scans for exposed secrets, helping you safeguard sensitive data, meet compliance requirements, and reduce the risk of security incidents.

Top 4 features of QScanner
Zero Installation
QScanner is a standalone executable – just download it and start scanning. Unlike traditional tools requiring bulky setup and configurations, no installation or deployment is needed.
Versatile Image Scanning
Local Runtimes: Scan images from Docker, Containerd, or Podman.
Local Archives: Analyze Docker images or OCI layouts from local files.
Remote Registries: Connect to AWS ECR, Azure Container Registry, JFrog, GHCR, and more.
Immediate Results
Get instant vulnerability reports directly in your console with output formats like SBOM, JSON, Table, and SARIF. This flexibility allows you to integrate QScanner seamlessly into various tools and workflows.
Policy Enforcement
QScanner offers centralized policy management through the Qualys Portal without disrupting engineering or DevOps workflows. Security teams can centrally define compliance standards and vulnerability thresholds, ensuring all scans automatically adhere to organizational policies. Developers and DevOps professionals continue using their preferred tools while QScanner enforces these policies in the background. This seamless integration facilitates a shift-left approach, addressing security concerns early without hindering productivity.
The Benefits of Using QScanner for Container Security Scanning
Local Image Scanning
QScanner is perfect for engineers who need to scan container images directly on their desktops. Its standalone nature means you can simply download the executable and start scanning without any installation. Whether you’re using Docker, Containerd, or Podman, QScanner allows you to assess images pulled into your local runtime or analyze local image archives like Docker images or OCI layouts. This immediate access enables developers to identify vulnerabilities, secrets, and malware early in the development cycle, promoting a shift-left approach to security.
> ./qscanner image [your local image name]
CI/CD Integration
Integrate QScanner seamlessly into your CI/CD pipelines to automate security checks during the build and deployment processes. By incorporating QScanner, you can enforce centrally managed security policies without interfering with engineering or DevOps workflows. Security teams configure policies via the Qualys Portal, ensuring all scans automatically adhere to organizational standards. This integration helps catch vulnerabilities and compliance issues before they make it into production, enhancing overall security posture without hindering productivity.
> Policy Evaluation FAILED
> Evaluated Policy "Organization Default Policy" [500fbca7-541e-43b4-aff8-6528bbd6932c]
> Reasons
> - Image has exploitable vulnerabilities. Please check Vuln Report for details.
> - Image has one or more restricted software. Restricted Software: openssh-server
Scan Images from Docker Registries
QScanner supports scanning images stored in remote public or private registries such as Harbor, AWS ECR, Azure Container Registry, JFrog, GHCR, and more. This capability allows security teams to assess images directly from registries without pulling them locally. By scanning images at rest, you can maintain compliance and security standards across all stages of your container lifecycle, ensuring that only secure and compliant images are deployed to your environments.
Custom Workflow Integration
For organizations with unique workflows or custom tooling, QScanner offers the flexibility to fit into your existing processes. Its command-line interface and support for multiple output formats – including SBOM, JSON, Table, and SARIF – make it adaptable to various tools and systems. Whether you’re integrating with custom deployment scripts, specialized monitoring systems, or other automation tools, QScanner can be customized to meet your specific needs without adding complexity.
How to use QScanner to scan container images
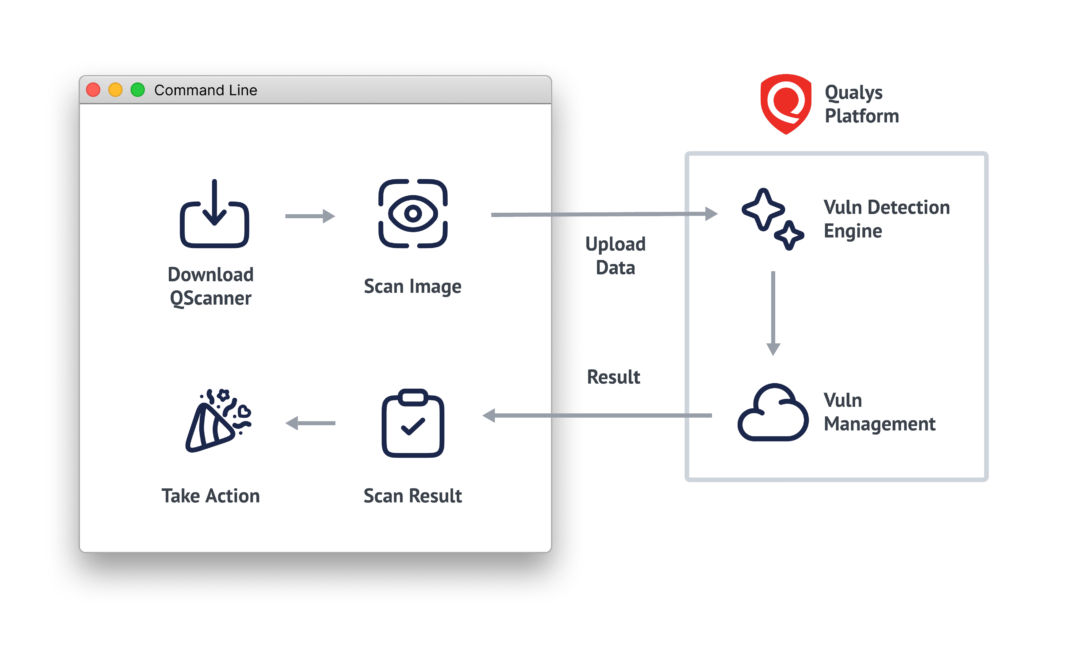
Step 1: Download the Scanner
Simply download the executable; it automatically detects your operating system and architecture. No installation is needed; QScanner is ready to use instantly.
Step 2: Select Your Target Image
Choose the container image you want to scan. QScanner works with:
- Local Runtimes: Docker, Containerd, or Podman images.
- Local Archives: Docker images or OCI layouts on your machine.
- Remote Registries: Images from AWS ECR, Azure Container Registry, JFrog, GHCR, etc.
Step 3: Scan the Image
Run QScanner to analyze the image for vulnerabilities and secrets.
Step 4: Automatic Upload and Analysis
QScanner uploads the scan data to the Qualys platform, where our trusted vulnerability detection engine analyzes it and stores the results in your Qualys Vulnerability Management system.
Step 5: Receive Instant Results
Get immediate feedback in your command-line interface. Choose from various output formats like JSON, Table, or SARIF to suit your needs.
Step 6: Take Action
Use the insights to address any identified issues promptly, enhancing your container security. Optionally, you can provide policy tags to enable policy evaluation. This allows for hassle-free, centralized policy enforcement via the Qualys Portal. Engineers and DevSecOps teams don’t need to worry about compliance – QScanner handles it automatically in the background.
QScanner Makes Container Security Scanning Simple and Fast
QScanner simplifies container image security by offering a zero-installation, standalone tool that fits effortlessly into your workflow. With versatile scanning capabilities, instant results, and centralized policy enforcement, it empowers CISOs, DevSecOps teams, engineers, and developers to secure container images efficiently. Experience the ease and power of QScanner today, which makes container security straightforward and effective.
Resources to get started
- Download QScanner.
- Getting started with QScanner.
- Learn more about Qualys Container Security and discover how it can revolutionize your approach to container security.
- How-to Training Videos