From Vulnerability Scanning to Risk Management: The Complete VMDR Advantage
What if your vulnerability management tool did more than just scan and instead helped you take control of cyber risks across your business? CISA defines “vulnerability management” as the process by which organizations identify, analyze, and manage vulnerabilities in a critical service’s operating environment. Note the emphasis on criticality and on the outcome: managing risk. The 2023 Forrester Vulnerability Risk Management Landscape report rightly adds that VM solutions facilitate prioritization and remediation workflows.
One word you don’t see: scanning. There’s no doubt that the strength, accuracy, and versatility of your vulnerability scanning are the backbone of your program, but vulnerability management is about an outcome that goes beyond a list of detections. It’s about prioritizing and removing the most critical risk from your environment.
Since 2019, Qualys VMDR has been helping customers do just that with the leading risk-based vulnerability management solution in the market. For any Qualys customer still using traditional VM or not leveraging VMDR in its full capacity, this blog post will help identify potential gaps in your program to deliver maximum visibility, leading prioritization, and faster remediation of critical business risk.
VMDR: More Than Just a “License to Scan”
With the stakes higher than ever, security teams must ask these questions of their VM program:
- With today’s dynamic attack surface (IT/OT/IoT, cloud and container assets, open-source software, web apps, and APIs, AI models, etc.), how do you know your VM scans cover everything?
- How can you trust that your prioritization engine combines threat intel with unique business context to identify what matters most?
- How do you remove the invisible fence between security and IT to ensure critical risk is removed as quickly as possible?
Qualys VMDR has been recognized as the only “Leader” and “Outperformer” in the market for helping customers answer these questions. It goes beyond traditional tools by combining asset discovery, vulnerability prioritization, certificate lifecycle management, compliance benchmarking, and real-time threat intelligence in one solution. Qualys has empowered organizations to shift from reactive security to proactive risk reduction. This comprehensive approach enables organizations to prioritize risks effectively, providing a clearer view of cyber threats and their potential impact. Additionally, with access to unlimited scanner appliances and a standard API for seamless integrations, organizations can scale their vulnerability management efforts without additional complexity. Our response capabilities enable organizations to remediate risks up to 50% faster, driving significant improvements in security posture. Many VM customers have recognized this advantage early and upgraded to VMDR to strengthen their security programs.
Connect with your Technical Account Manager today to learn more, explore demos, and take the next steps toward upgrading to VMDR.
If you’re still on the fence about upgrading, or if you feel your team can do a lot more to realize the full potential of your VMDR license, refer to the chart below. The remainder of this blog entry will dive deeper into each of the use cases you see.
| Use Case | Solution | Description | VMDR | VM |
| Risk Detection, Scoring and Prioritization | Vulnerability Management (VM) | Identify critical vulnerabilities in real time with our base VM offering | ||
| TruRisk™ | Measure, quantify, and communicate risk for vulnerabilities and assets | |||
| MITRE ATT&CK Mapping | Map vulnerabilities to attack Tactics and Techniques | |||
| Software Composition Analysis (SwCA) | Assess, prioritize, and remediate risk associated with first-party software | |||
| Threat Intelligence | Supercharge your threat intelligence capabilities to determine the impact of new or trending CVEs to your environment | |||
| Detection Responses (Vulnerability Alerting) | Create proactive alerts for key vulnerabilities | |||
| Attack Surface Management | Global AssetView | Get real-time, unified visibility of your entire digital landscape, empowering your teams to discover, monitor, and secure all assets | ||
| Certificate View | Inventory, assess, and renew certificates. Evaluate your SSL/TLS configurations | |||
| Scanner Appliances | Leverage dedicated machine to actively scan for remotely assessing the security posture of network attached devices | Unlimited | Per-License Cost | |
| Network Passive Sensor | Inventory and identify gaps in network connected assets, uncover rogue assets, and shadow IT | Unlimited | Per-License Cost | |
| Cloud Agent, Cloud Connector, Container Security, VMDR Mobile (Inventory Only) | Build a comprehensive digital inventory of IT, cloud, container, and mobile devices across the organization | Unlimited | ||
| Compliance | Secure Configuration Assessment (SCA) | Analyze, measure, and monitor for misconfigurations based on CIS benchmarks | ||
| PCI ASV | Experience seamless compliance testing, reporting, and attestation | Unlimited | ||
| Response | Patch Management (PM) (Detection Only) | Detect missing patches on cloud agent enabled endpoints | ||
| QFlow | Use Low-Code/No-Code public cloud provider resource management automation | |||
| VMDR to ITSM | Create and assign tasks with SLA prioritization to ServiceNow system owners | |||
| VMDR to JIRA | Communicate risk to security, IT, and development teams using Atlassian JIRA | |||
| Standard API | Service that enables seamless integration with custom solutions or third-party tools on the Qualys platform |
Risk Detection, Scoring and Prioritization
Vulnerability Management – Identify Risks on Digital Assets
Discover and identify critical vulnerabilities with an extensive knowledgebase that supports over 85K CVEs, and reduce cybersecurity risk in real-time risk discovery across your internal, external, and public cloud IT domain.
Qualys VMDR Getting Started Guide
TruRisk – Measure Risk in Real Time
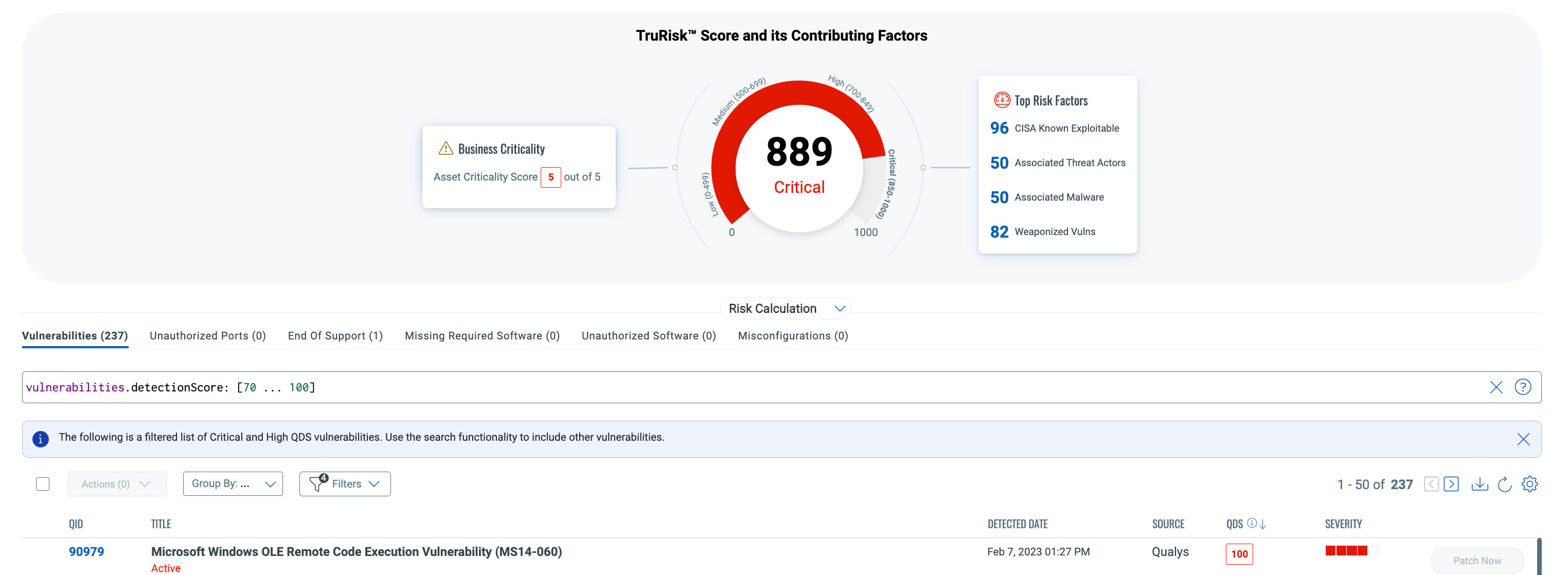
While the number of vulnerabilities continues to rise, the resources available to identify and remediate them often remain limited. This challenge calls for a risk-based approach to vulnerability management that emphasizes returning to the basics. With TruRisk, we quantify the risk associated with all digital assets and attack surfaces, empowering organizations to prioritize and measure the material impact of vulnerabilities more effectively.
Using CVSS or EPSS to measure the likelihood of vulnerability exploitation lacks business context and up-to-date threat intelligence. Our vulnerability-level scoring incorporates threat intelligence from over 25 sources, recalculated daily, to provide a more accurate view of exploit likelihood.
Even if your current prioritization approach relies on CVSS or Qualys severity scores, these can be used alongside the Qualys Detection Score (QDS) to refine your remediation efforts. Over 51% of CVSS vulnerabilities are rated high or critical. However, QDS provides actionable insights by identifying which of those vulnerabilities have active exploits, are being leveraged in the wild, are trending on social media, or appear on the CISA Known Exploitable Vulnerabilities list along with established remediation deadlines. You’ll also gain visibility into vulnerabilities linked to ransomware and malware campaigns, as well as the threat actors behind them.
A Deep Dive into VMDR with Qualys TruRisk™
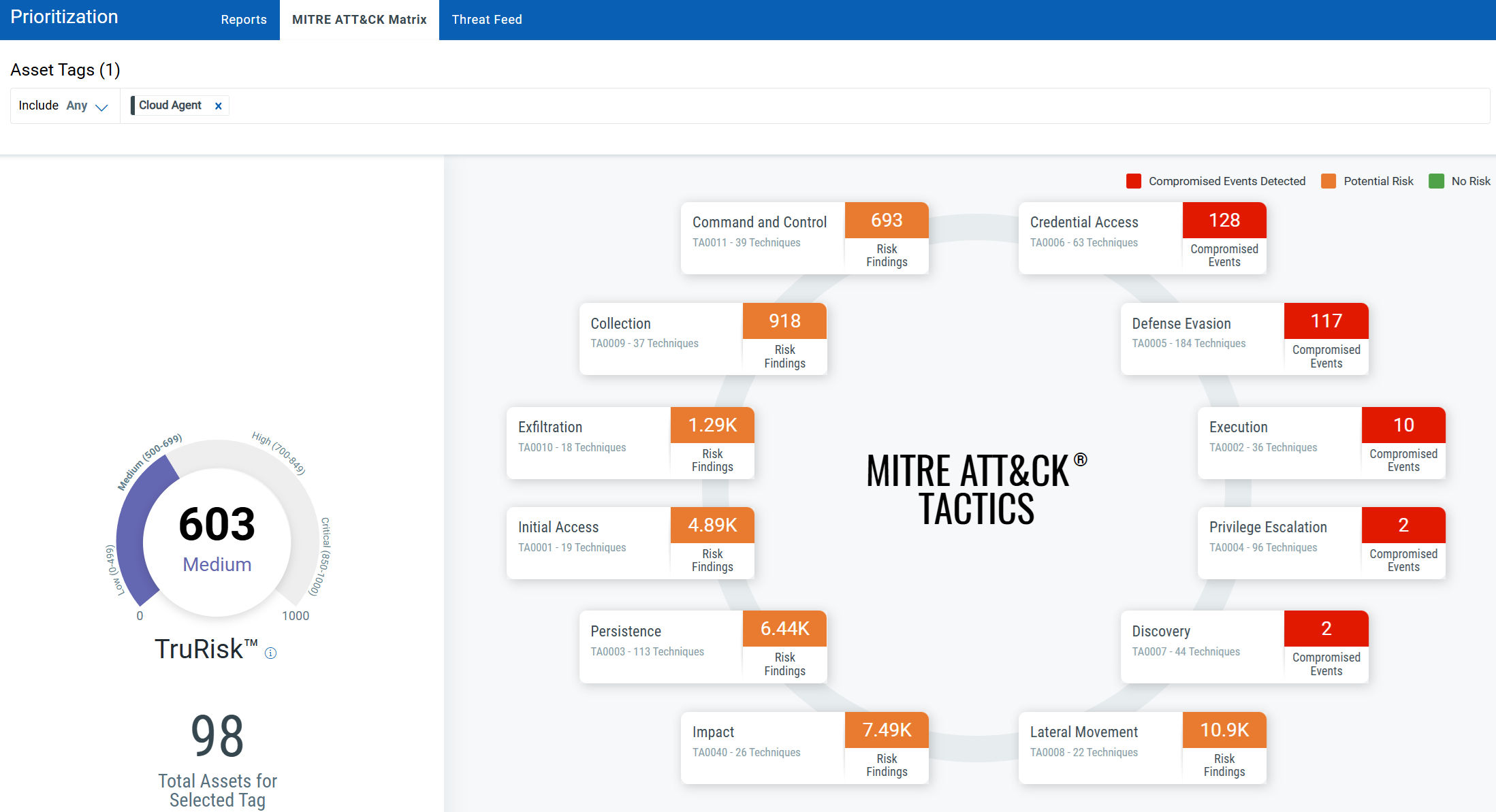
MITRE ATT&CK – Map Vulnerabilities to Behaviors of Attackers and Enhance Defense Strategies
Understanding how attackers think is key to an effective defense, which is why VMDR maps detected vulnerabilities to the MITRE ATT&CK framework, revealing the most critical attack vectors. This framework organizes the Tactics, Techniques, and Procedures (TTPs) commonly used by attackers during exploitation. Leveraging this approach enables organizations to prioritize the remediation of vulnerabilities based on the attack vectors employed. For instance, vulnerabilities associated with TA0001 – Initial Access represent techniques attackers use to enter a network, such as exploiting weaknesses on a public-facing web server. Remediating these vulnerabilities on internet-facing machines should be a top priority.
Qualys MITRE ATT&CK Matrix User Guide
Combine Qualys TruRisk™ and MITRE ATT&CK to Adopt Threat-Informed Defense to Reduce Risk
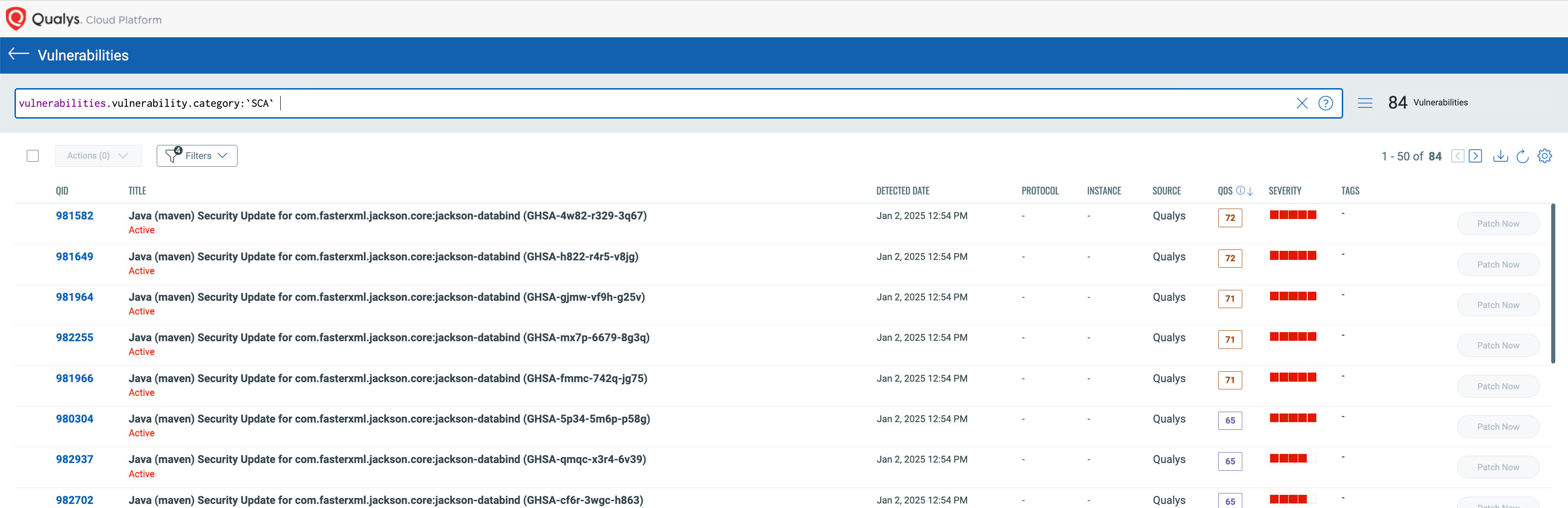
Software Composition Analysis – Detect Vulnerabilities in Open-source Libraries Used in First-party Software
Internally developed software applications often rely on open-source components to build proprietary systems essential for business operations. However, these open-source components may contain known vulnerabilities that often go unnoticed. With Qualys Software Composition Analysis (SwCA), you can assess the risk in first-party applications, providing full visibility into the vulnerabilities within custom-built software.
Runtime Software Composition Analysis (SwcA) User Guide
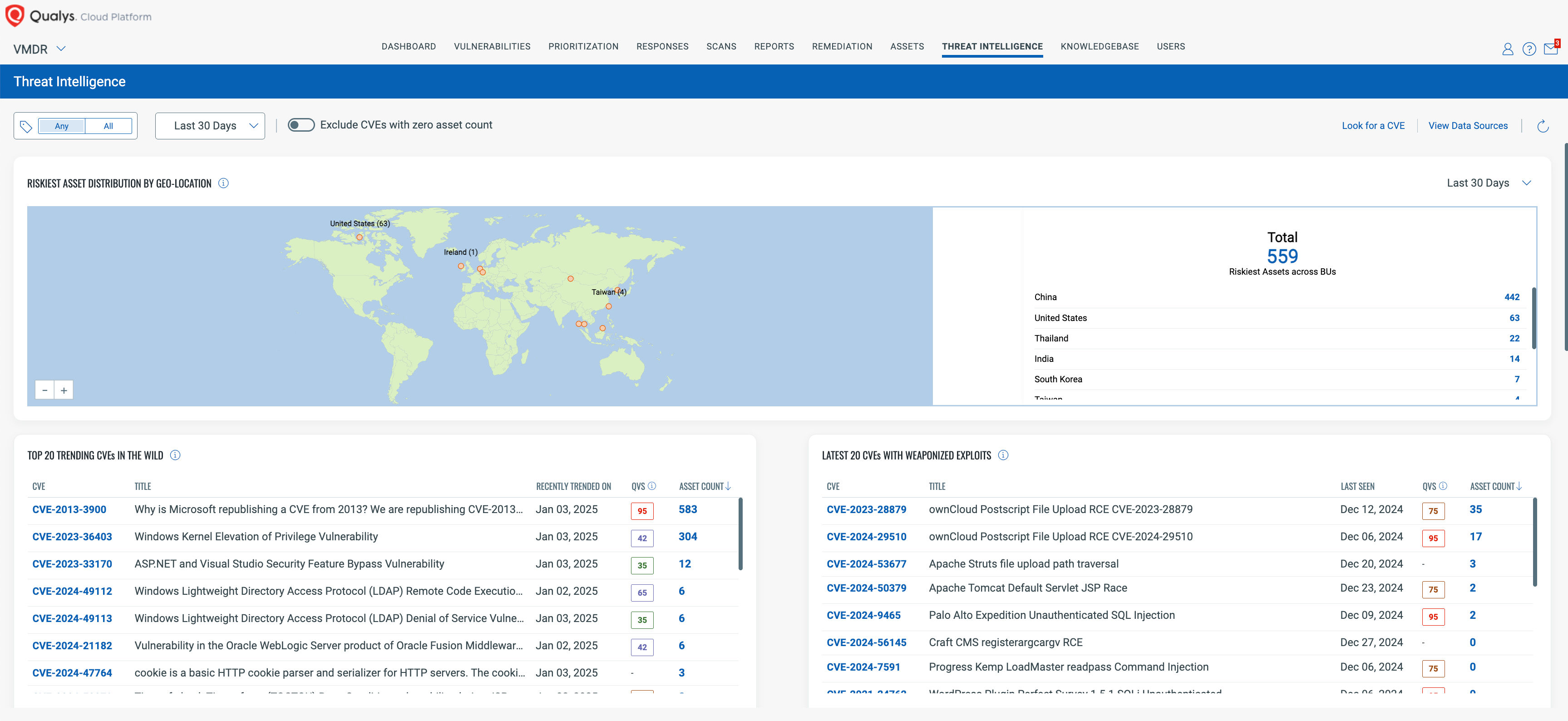
Threat Intelligence – Proactively Research and Respond to Emerging Threats with Real-Time Insights
Use real-time threat intelligence to determine the impact of the latest CVEs, threat actors, and ransomware campaigns. Identify the impact of the latest threats by geo-location, trending CVEs, weaponized exploits, exploits by malware, and threat actor groups. Gain additional insights from our Qualys research team through our threat feeds, offering up-to-date information on exploits, vulnerabilities, and adversaries. Threat intelligence is seamlessly integrated into your vulnerability management process, enabling faster decision-making and enabling you to take a proper risk-based approach to remediation.
Qualys Threat Intelligence User Guide
Detection Responses – Proactive Alerting for Risk Items
Continuous monitoring acts as a vigilant sentinel, working in tandem with VMDR to safeguard your attack surface by detecting network changes that may expose your organization to risk. You will receive real-time alerts for expired certificates, critical vulnerabilities, CVEs, etc., empowering you to take swift, proactive action via email, Slack, PagerDuty, or ServiceNow. This feature helps you stay informed of key risk items within your environment and fine-tune alert settings to prioritize high-risk issues while minimizing noise from less critical alerts.
Create Rules and Actions from Responses
Attack Surface Management
In a traditional vulnerability management program, breadth of coverage is achieved when the ratio of assets assessed for vulnerabilities matches an agreed-upon source of truth, such as an IPAM or CMDB. These assets can meet the coverage standards with an active scan from a scanner appliance or receive an agent. Qualys extends beyond these traditional approaches by offering a suite of advanced capabilities to ensure complete asset visibility across your environment. It can discover and inventory ephemeral assets that might otherwise go undetected. These methods provide continuous visibility into your attack surface, even in highly dynamic environments, ensuring that no asset goes unnoticed, whether on-premises, in the cloud, or in remote locations.
Global AssetView – Unified Visibility of Your Digital Assets
Qualys Global AssetView provides a centralized, real-time inventory of all IT assets across on-premises, cloud, container, and remote environments, discovered through Qualys sensors and modules. By identifying and cataloging hardware, installed software, operating systems, and associated metadata, it delivers a comprehensive view of your entire digital landscape. Enhanced visibility ensures you can monitor, categorize, and secure all assets because you cannot defend what you cannot see.
Global AssetView Quick Start Guide
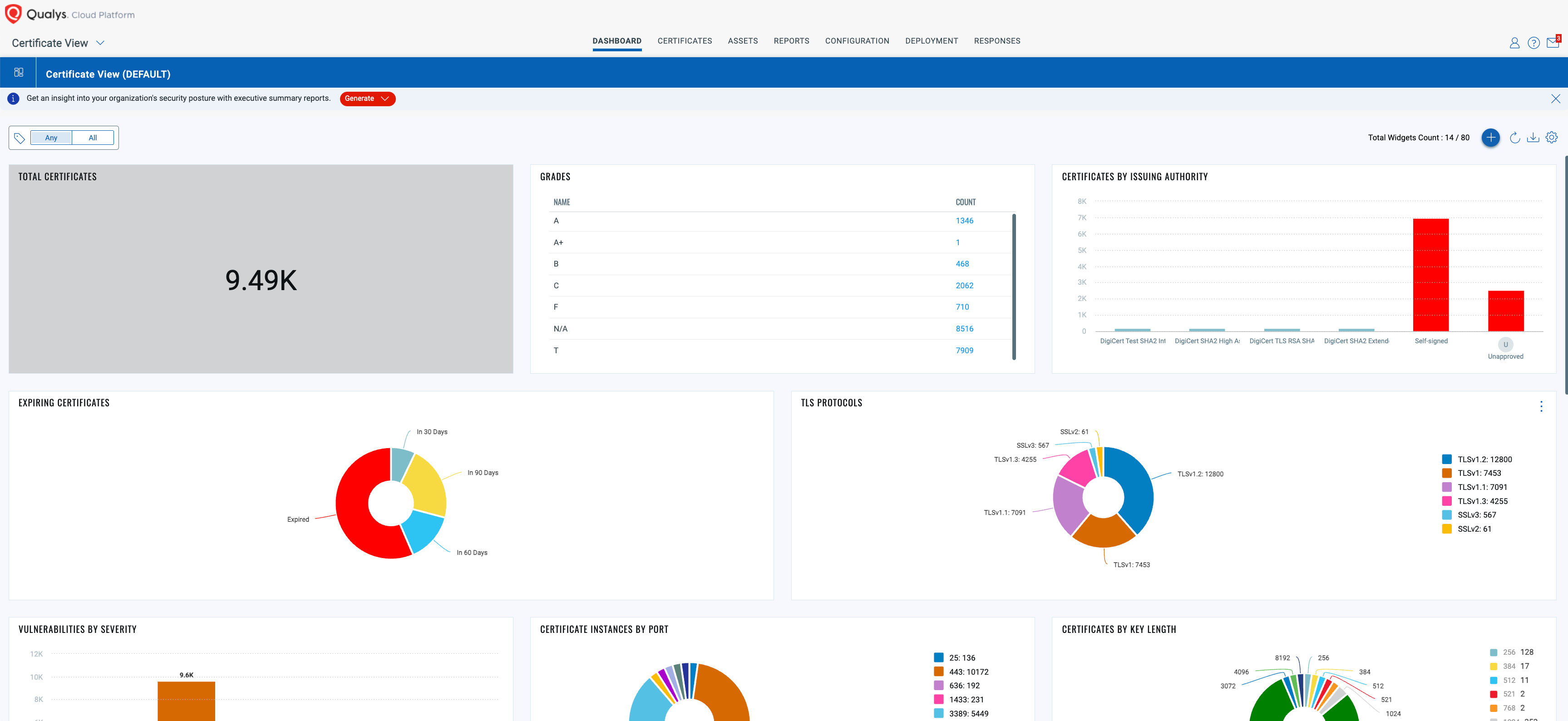
Certificate View – Inventory, Assess, and Renew Certificates
In one interface, you can review all the certificates discovered during the course of VMDR scanning. Each implementation is graded to evaluate whether SSL/TLS configurations certificates are supporting organizational protocols and the best encryption available.
Certificates can be set up to renew or generate new certificates with compatible certificate providers such as Digicert and Let’s Encrypt!
Get Started with Certificate View
Cloud Agents – Monitor Security Posture in Real Time
The Qualys Cloud Agent is available to both VM and VMDR customers, providing access to key features across the Qualys platform. Built with a pluggable architecture, the agent is designed for minimal impact on system performance and operates efficiently across a wide range of hardware. With unparalleled support for diverse platforms, including physical, virtual, and cloud-based assets, the Cloud Agent ensures seamless integration, offering flexibility and scalability to align with your organization’s security needs.
Cloud Agents can be deployed on unlimited assets for inventory purposes at no additional cost, enabling comprehensive visibility across your environment. To activate advanced capabilities such as Vulnerability Management, Secure Configuration Assessment (SCA), or Software Composition Analysis (SwCA) scans, each asset must have the appropriate VMDR entitlements.
Appliance Scanners – Identify Vulnerabilities on Network-Connected Devices
The traditional Qualys scanner appliance is essential for identifying risk across the network. It discovers active assets, detects open ports, performs service discovery, and identifies vulnerabilities associated with those services. The active scanner plays a critical role in building a comprehensive inventory of active and potentially rogue assets while also identifying associated risks. Additionally, this appliance is used for secure configuration analysis of remote systems. It is particularly effective for network-connected assets that cannot support an agent, such as routers, firewalls, and load balancers.
VMDR customers can deploy unlimited virtual scanners, providing flexible, scalable coverage tailored to their unique network segmentation and redundancy needs, ensuring comprehensive visibility across the entire environment.
Network Passive Sensor – Discover Transient and Unmanaged Devices
After investing significant effort in building a comprehensive inventory of assets using traditional methods, Network Passive Sensors can help identify any assets that might have been missed during operational data collection. These sensors are particularly valuable in OT environments, where active inventory data collection may pose additional risks, as they provide a safe and effective means of inventorying and identifying assets. Additionally, Network Passive Sensors excel at uncovering rogue assets and shadow IT that may have been introduced outside of standard business processes.
Network Passive Sensor Getting Started Guide
Cloud Connectors – Continuously Inventory Cloud Provider Resources
Gain access to public cloud accounts with the Qualys Cloud Connectors. These API gateways perform two key tasks: first, they gather information about all Infrastructure as a Service (IaaS) virtual instances running in the account and dynamically integrate them into VMDR for scanning. Second, they inventory all Platform as a Service (PaaS) resources, such as RDS databases, S3 buckets, and security groups. Qualys Cloud Connectors support major cloud providers, including AWS, Azure, Google Cloud Platform (GCP), and Oracle Cloud Infrastructure (OCI), ensuring comprehensive visibility across multi-cloud environments.
Container Security – Inventory Registry and Running Containers
Qualys container sensor modules that are installed as a daemon set will enumerate images, registries, associated containers, and hosts. These sensors seamlessly integrate into containerized infrastructures to deliver real-time insights into container activity.
Get Started with Container Security
VMDR Mobile – Inventory all Mobile Android, IOS/iPadOS Endpoints
VMDR Mobile helps you inventory and normalize all Android and iOS endpoint device data, including operating system, applications, certificates, device location, and system data.
Compliance
Secure Configuration Assessment – Automated system configuration hardening assessments
This feature measures system configurations against established CIS benchmarks, ensuring that systems are deployed with proper security settings. By addressing unnecessary attack surfaces and minimizing risk, it supports both existing and new system deployments.
PCI ASV – Safeguard Cardholder Data and Ensure PCI Compliance
Through this capability, you can create unlimited Qualys PCI ASV merchant accounts to meet Payment Card Industry Data Security Standard (PCI-DSS) requirements. Each account offers independent user management and streamlines PCI compliance workflows, including scanning and quarterly attestation reporting.
PCI Compliance Getting Started Guide
Risk Remediation
Patch Management (Detection Only) – Detect Missing Patches on Cloud Agent-enabled assets
Identifying cyber risks on your network is just the first step; the next critical action is to reduce those risks by applying necessary patches. VMDR provides comprehensive insights into missing patches across operating systems and third-party applications, enabling you to remediate vulnerabilities effectively, including those commonly exploited in ransomware attacks.
Activate PM Detection in Cloud Agent Configuration Profile
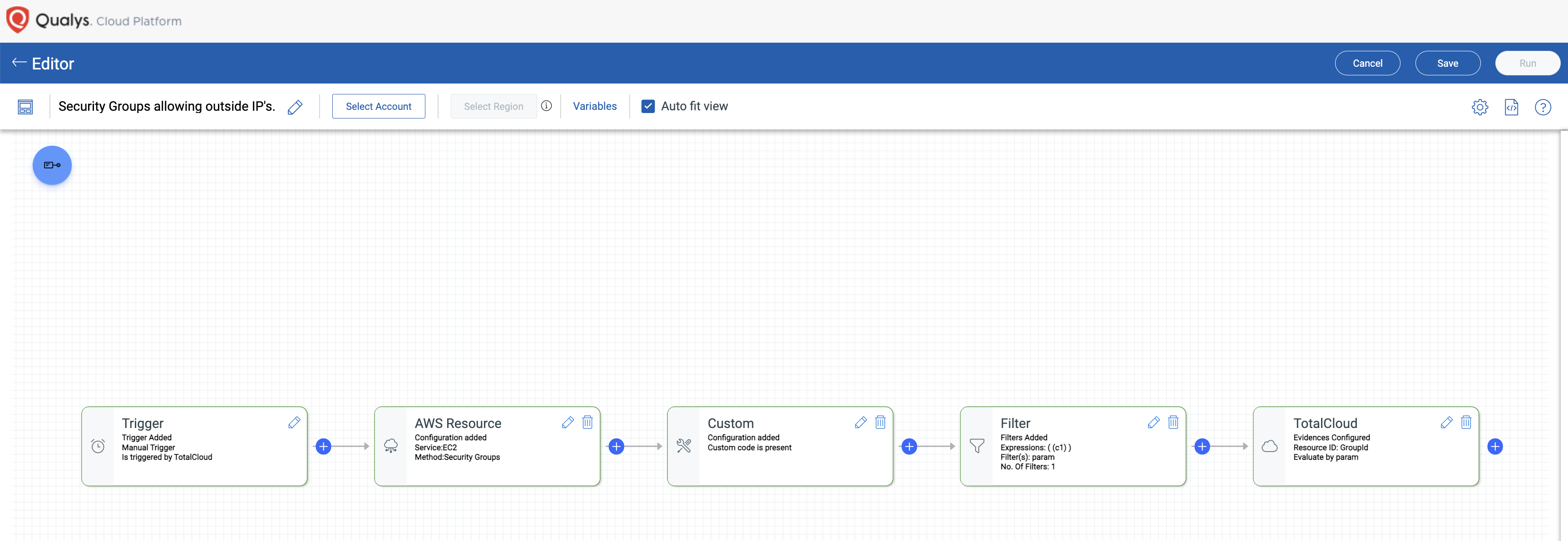
Qualys Flow (QFlow) – Create customized workflows to manage public cloud resources
Create customized workflows to automate public cloud management processes without the need for scripting expertise. QFlow allows you to easily orchestrate actions based on your public cloud service provider’s API, enabling compliance checks, remediation, and proactive actions. With its intuitive, no-code interface, you can design workflows that streamline complex tasks. Pre-defined templates that help you quickly automate actions, such as identifying security groups with open access to port 22, locating publicly accessible RDS instances, or finding Lambda functions with outdated runtime versions. This level of automation not only accelerates response times but also establishes consistency and efficient risk management across your entire cloud environment.
Get Started with Qualys Flow (QFlow)
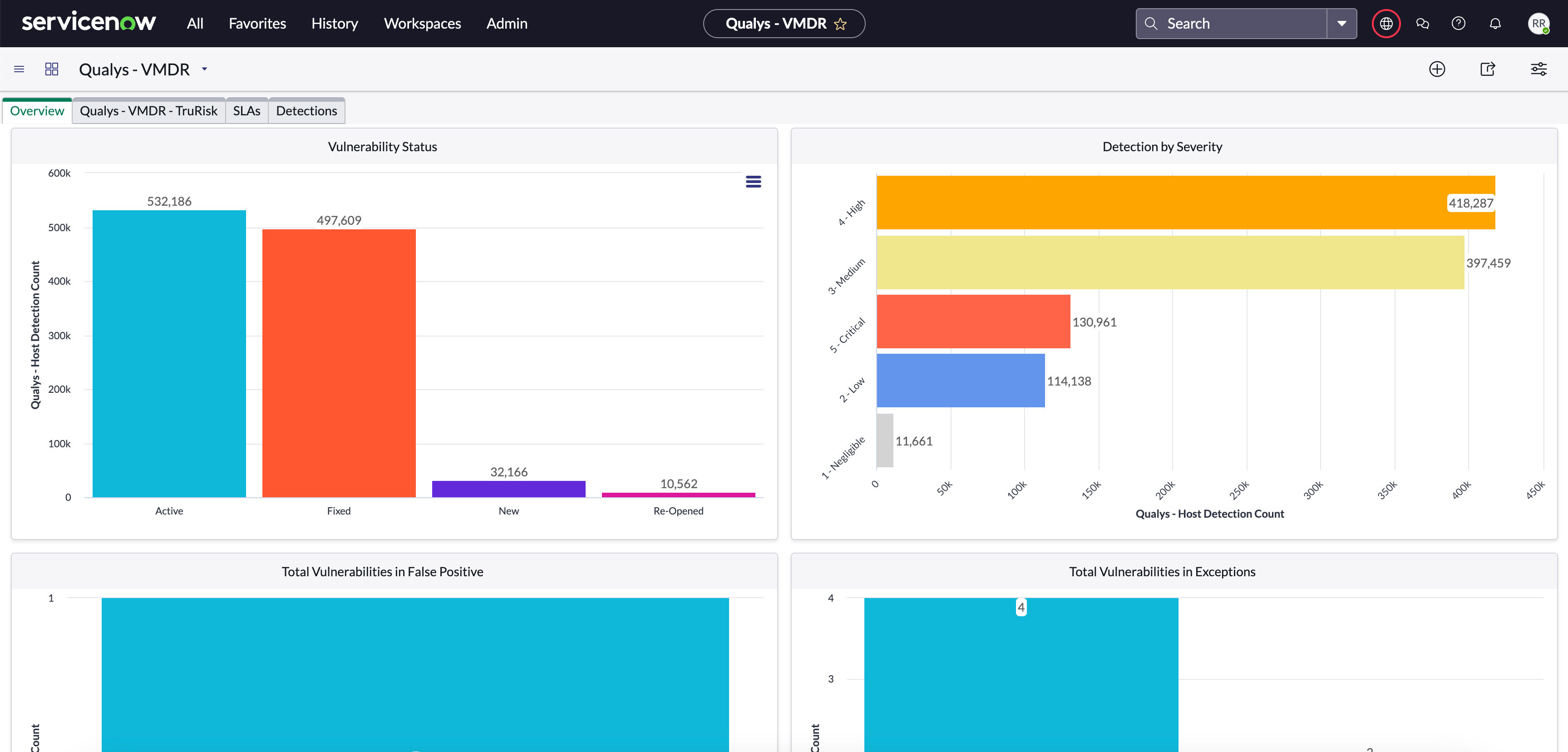
VMDR to ServiceNow ITSM – Accelerate Risk Communication to Stakeholders and Supercharge Remediation with Automated Task Creation
Our integration with ServiceNow streamlines the vulnerability remediation process by automating task creation and assignment for selected detected vulnerabilities based on customized rules. By leveraging TruRisk scoring and SLA assignments, remediation teams can effectivley prioritize tasks, resolve vulnerabilities based on risk, and address the most critical issues first. Teams can also revert ticket statuses and introduce them into exception, false positive, and change management workflows. Furthermore, change management workflows can deploy automated patch management jobs for customers subscribed to our patch management-enabled Cloud Agents.
Get Started Qualys VMDR to ITSM User Guide
VMDR to Atlassian JIRA – Communicate Risk to Remediation Teams and Stakeholders
Many teams already use JIRA for tracking, and the integration with Qualys VMDR streamlines these processes by automating tasks and bringing in vulnerability context. This enhancement fosters collaboration between security, IT, and development teams.
The integration enables customers to track vulnerabilities from discovery to remediation, providing full visibility into the process through multiple ticketing schemes. Whether you’re using a cloud-based or on-premises JIRA installation, this solution empowers teams to prioritize remediation based on risk, ultimately reducing mean time to remediation.
Qualys VMDR & JIRA Integration Now Available
Get Started JIRA Connector User Guide
Standard API – Seamlessly Integrate with the Qualys Platform
The Qualys API allows users to automate workflows, create custom solutions, and integrate with third party solutions. The standard tier includes two concurrent connections and supports up to 300 API calls per hour.
If you are not already using VMDR to measure, communicate, and eliminate risk, we invite you to start a risk-free trial for thirty days.
Conclusion
Qualys VMDR enables organizations to transcend traditional vulnerability management with an integrated, comprehensive approach to cybersecurity. Whether upgrading to VMDR or maximizing its potential, the capabilities highlighted in this blog showcase how VMDR increases the maturity of your organization’s risk management processes and accelerates the elimination of risks through automation. Leverage VMDR’s full suite of features to strengthen your security posture and stay ahead of evolving cyber threats.
Contributors
Anthony Williams, Subject Matter Expert, VMDR
Ramesh Ramachandran, Principal Product Manager, VMDR
Chris McManus, Senior Manager, Marketing