Effectively Measure, Communicate, and Eliminate Cloud Risks with TotalCloud

Cloud is a dynamic and ever-evolving environment characterized by transient workloads and an expansive attack surface. This inherent nature of cloud infrastructure contributes to the ongoing complexity and challenges in maintaining robust security measures. According to the 2023 Qualys TotalCloud Security Insights Report, several critical insights emerged:
- Compliance with CIS benchmarks, which are essential for maintaining basic cloud hygiene, is not achieved approximately 50% of the time.
- Despite nearly two years since the initial discovery of the Log4Shell vulnerability, a staggering 70% of these security flaws remain unresolved.
- The prevalence of malware within cloud ecosystems is on the rise, with new variants being specifically engineered to enable lateral movement across networks.
These patterns highlight ineffectiveness in measuring, communicating, and eliminating cloud risk and help explain the frequent incidence of security breaches within the cloud. During our 2023 Qualys Security Conference (QSC) taking place in Orlando, Florida, November 6-9, 2023, attendees learned how Qualys TotalCloud provides an effective platform for implementing and managing Cloud Native Application Protection Platform (CNAPP) in a modern enterprise. But let’s first explore some of the challenges that contribute to these patterns in the first place.
Challenge 1: Measurement
A siloed view of risk across hybrid environments
The siloed view of risk across on-premises, multi-cloud, and SaaS environments presents two significant challenges: visibility and prioritization. When assets are spread across multiple cloud services and tools and teams do not communicate, achieving a 360-degree view of risk is difficult. Additionally, with so many different risks, it is difficult to prioritize effectively without a holistic view of the landscape. These challenges are compounded in multi-cloud environments, where organizations must manage different technologies and philosophies of risk. This can lead to a false sense of security, as organizations may be unaware of the risks outside their siloed view.
Challenge 2: Communication
Infective communication of risk across on-premises, multi-cloud, and SaaS environments
Imagine the difficulty of presenting a comprehensive risk report to the board and management, distilling complex data from hybrid systems to guide strategic decisions. Developers, operations staff, and DevOps groups often face the challenge of receiving disjointed communications that obscure urgent issues. Additionally, the need for clear and unified compliance reporting to auditors adds complexity, potentially stretching your team’s resources thin. These communication barriers are more than just obstacles; they can weaken your overall risk management.
Challenge 3: Elimination
Lengthy remediation processes that take months
In the fast-paced domain of cloud security, the duration of the remediation process is critical. Delays in addressing misconfigurations, vulnerabilities, or threats can provide windows of opportunity for attacks. Accelerating the identification and rectification of issues is vital, as is the need to expedite the risk-elimination process. Automation, one-click, and the ability to integrate ITSM tools to assign tickets automatically emerge as crucial elements that can transform risk mitigation from a reactive process to an efficient and proactive operation.
These challenges underline the need for a robust cloud security mechanism, and Qualys TotalCloud is the AI CNAPP solution that bridges these gaps.
Introducing Qualys TotalCloud
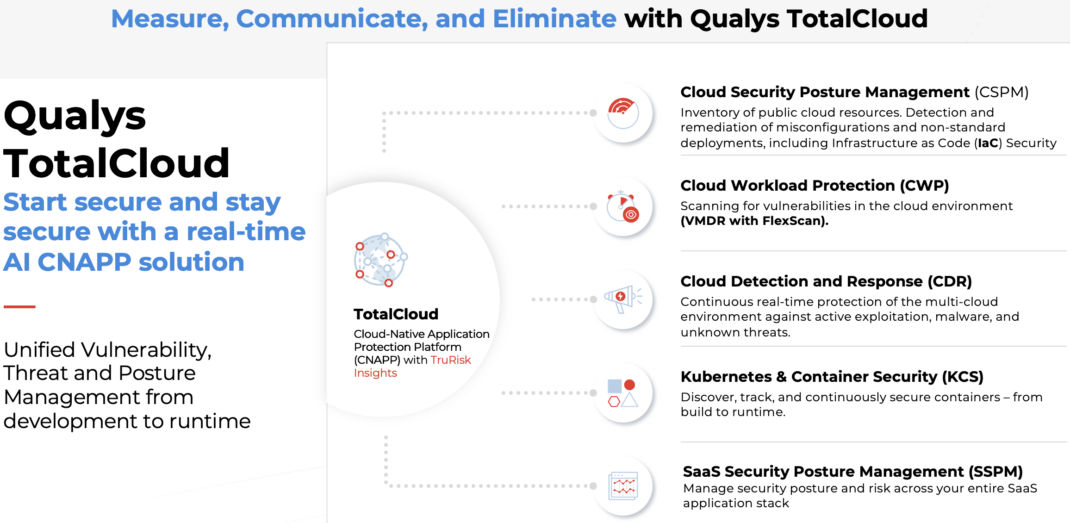
TotalCloud is a comprehensive Cloud-Native Application Protection Platform (CNAPP) solution that provides unified vulnerability, threat, and posture management from development to runtime and measures, communicates, and eliminates risks across multi-cloud environments, including:
- Flexible, continuous, and quick scanning capabilities: Qualys FlexScan provides continuous scanning for vulnerabilities using agentless techniques and agents. It supports multiple scanning methods, including API-, Snapshot-, Agent-, and Network-based scanning to provide continuous, quick, and comprehensive visibility into vulnerabilities across a multi-cloud environment. This flexible approach allows security teams to identify potential vulnerabilities within minutes in a continuous manner. FlexScan can scan workloads using the fastest available scanning method (results available in under 10 minutes), such as API-based scanning, and then leverages a more comprehensive scanning method, such as agent-based scanning, for a more in-depth assessment.
- TruRisk Insights provides one prioritized view of risk: TruRisk Insights sheds light on the critical concept that risks in the cloud are not merely additive — they are multiplicative. A vulnerability, when paired with a misconfiguration and compounded by internet exposure, escalates into a significantly higher threat. This toxic combination demands immediate and prioritized remediation. TruRisk Insights consolidates critical indicators from diverse Qualys sources, such as Cloud Workload Protection (CWP), Cloud Security Posture Management (CSPM), and Cloud Detection and Response, into a cohesive, actionable dashboard. Additionally, it integrates data from your External Attack Surface Management (EASM) solutions, giving you visibility into how external threats may perceive and target your cloud assets. By unifying these varied data streams, each with its own set of priorities, TruRisk Insights offers a singular, prioritized view of your cloud risk landscape.
- Managing the security posture and risk across your entire SaaS application stack: Qualys SaaS Security Posture Management (SSPM) brings the same level of security awareness and control that you already have in your cloud infrastructure to the SaaS applications that are critical to your business processes. It helps you protect your SaaS applications from cyberattacks and ensure compliance with industry regulations. Qualys SSPM automatically inventories all your SaaS application users and user groups (internal and external) and the files and folders they own and have access to. It also gathers detailed information on endpoints, such as asset details, location, running services, installed software, etc. This information helps manage users and data access rights effectively, identify and remediate misconfigurations in your SaaS applications and monitor user activity and data access to detect suspicious behavior and one-click remediation. Additionally, TruRisk Insights can now provide you with a prioritized view of security findings for your SaaS applications.
- Deep learning AI to detect known and unknown threats in real time: Qualys Cloud Detection and Response (CDR) uses deep learning AI to detect malware in real-time across the entire cloud kill chain, including reconnaissance, exploitation, installation, command and control, actions on objectives, and lateral movement. This helps organizations manage and reduce cloud security risk by scanning cloud infrastructure at runtime and in a cloud-native manner, including container images. With CDR’s AI-based approach, security teams can now detect both known and unknown malware from development to runtime, preventing stealthy attacks and reducing the risk of a cloud breach. CDR’s ability to continuously self-learn from new data means that it becomes more efficient at identifying false positives over time, thereby reducing the burden on security teams and allowing them to focus on genuine threats.
- Automated, one-click, and custom remediations and ITSM tool integration: Qualys offers a variety of remediation options, including automated, one-click, and custom remediation. Qualys also provides complete evidence and clear steps to drive remediation.
- Automated Remediation: Qualys offers no-code, drag-and-drop workflows to simplify time-consuming operational tasks, such as assessing vulnerabilities on ephemeral cloud assets, alerting high-priority threats, remediating misconfigurations, and quarantining high-risk assets.
- One-Click Remediation: Qualys offers out-of-the-box, one-click remediation for over 50 highly exploited misconfigurations. This allows you to remediate and control misconfiguration on a single resource or multiple resources with a single click, improving your compliance score.
- Custom Remediation: You can also customize remediation by creating your own workflows based on your business requirements, or you can use Qualys-provided workflows that you can customize.
- Integrations with ITSM Tools: Qualys offers integrations with ITSM tools to automatically assign tickets and enable orchestration of remediation to reduce MTTR.
- Flexible licensing provides lower total cost of ownership (TCO) and higher return on investment (ROI): Qualys delivers a modular and flexible licensing model that gives customers the flexibility to deploy what they want and when they want and the ability to move licenses when they want and how they want. This results in lower TCO and higher ROI because customers start with what they need without unused licenses going to waste. It also allows moving licenses without opening new POs or getting finance approval. This is not just about convenience; it’s about the intelligent allocation of resources. The absence of a need to re-license for different features means that customers can pivot their focus as their security demands change without additional financial overhead.
In summary, TotalCloud offers a robust solution for accurately measuring, communicating, and mitigating risks within multi-cloud environments. However, the true test of its capabilities is through firsthand experience. Click here to see TotalCloud in action and engage with our cloud security specialists, who can evaluate your cloud infrastructure and provide you with personalized strategies suited to your specific cloud environment.