How to Rapidly Identify Assets at Risk to WannaCry Ransomware and ETERNALBLUE Exploit
In what may be the first public weaponizing of April’s Shadow Brokers dump of NSA exploits, a ransomware attack has crippled IT systems globally and disrupted operations at major organizations, including patient services at UK hospitals.
About 80,000 infections have been detected in about 100 countries at the time of this writing, and the attack, which uses the WannaCry (WanaCrypt0r 2.0) ransomware, continues to spread.
The rapid weaponizing of newly disclosed nation state exploits for criminal purposes and, in this case, monetary gain, places new burdens on enterprises’ security organizations. They now must deal with destructive and fast-moving cyber attacks such as this one, which requires putting in place systems, tools, and processes to quickly identify, prioritize, and remediate these attacks.
It took just 28 days from the original dump of the Shadow Brokers dump of NSA exploits targeting newly disclosed vulnerabilities (MS17-010) to yield a fully operational and crippling cyber attack.
Enterprises with vulnerability management programs that scan less frequently, such as those performing only monthly scans, providing no coverage of remote user machines or lacking threat-prioritized remediation processes, can be still at risk.
In an unusual move due to the extreme threat of this type of malware, Microsoft has also released patches for some “end of life” (EOL) versions, including Windows XP, Windows 8, Windows Server 2003, and Windows Server 2008.
Identification and Tracking of Remediation
WannaCry utilizes the ETERNALBLUE exploit. Qualys’ Vulnerability Team analyzed the Shadow Brokers dump and made this analysis available to customers subscribed to the Qualys ThreatPROTECT service (see image below). Threat prioritization coupled with continuous vulnerability management across on-premises systems, cloud instances, and remote user endpoints provides full visibility of impacted assets for precise and prompt remediation.
Enterprises running Qualys using scanners or Cloud Agents can verify the presence of these vulnerabilities through QIDs 91345 and 91360 (ETERNALBLUE) as well as 91361, 91359, 91357, 53007, 87284 and focus on infected assets with ThreatPROTECT to prioritize remediation. Customers can also track the remediation progress over time across their global on-premises, cloud, and user endpoints with an AssetView trend widget, as shown below.
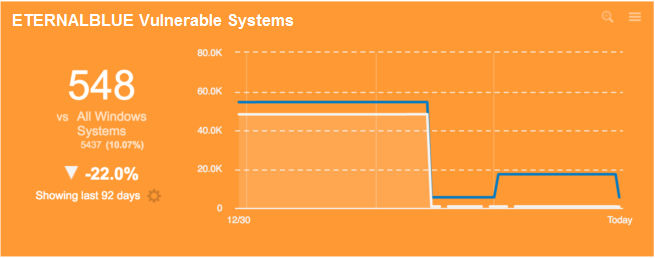
UPDATE: 14 May 2017. Signatures for the following QIDs have been updated to detect the patch released by Microsoft for end-of-life operating systems Windows XP, Windows 2003 and Windows 8. The change is released in VulnSig version 2.4.39-5.
Mitigations for WannaCry
- Apply patches for MS17-010 (ETERNALBLUE and DOUBLEPULSAR)
- Microsoft has also released patches for end of life Windows systems under KB4012598.
- Create a named mutex “MsWinZonesCacheCounterMutexA” (ref:https://twitter.com/gN3mes1s/status/863149075159543808)
- Filter all SMB (TCP/445), NetBIOS (TCP/139), and RDP (TCP/3389)
Detecting Compromised Assets
Qualys has also added QID 1029 WannaCrypt Ransomware Detected to help you identify assets that have already been infected with this malware, which can be leveraged in an AssetView widget. Continuous Monitoring can be used to send a notification if any system is found to be compromised.
Resources
- Detailed walkthrough of how to detect MS17-010 and how to report on it for those new to Qualys.
- Detailed walkthrough of how to build WannaCry dashboards in AssetView. Also available as a webcast.
- De-duping WannaCry detections
- On-demand WannaCry webcast, summary and transcript of participant Q&A showing how to identify at-risk assets and institute threat-prioritized remediation processes for current and future risks.
- First-hand perspective of how one company kept the threat under control (via TechRepublic)
Support Knowledge Center
Technical Resources and Detection Methods for WannaCry related QIDs are found in the WannaCry Support Article: Qualys response for Global Ransomware Attack (WannaCry)
To start detecting and protecting against WannaCry, sign up for a free 30-day Qualys Suite trial, which includes all features described in this article.
Twitter blogger MalwareTech has accidentally stopped WannaCry spread through registering a domain name hidden by hackers in ransomware source code – https://malwareless.com/wannacry-ransomware-attack-temporarily-stopped-accidental-hero/. But they can start again soon if they change ransomware kill-switch mechanism a bit