Processor Vulnerabilities – Meltdown and Spectre
UPDATE 1/4/2018: Qualys has released several QIDs for detecting missing patches for these vulnerabilities.
UPDATE 1/5/2018: Pre-built AssetView dashboards to visualize impact and remediation progress.
Vulnerabilities potentially impacting all major processor vendors were disclosed today by Google Project Zero. These vulnerabilities have been named Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 & CVE-2017-5715). Organizations should inventory their systems by processor type, apply vendor patches as they become available, and track their progress. This article describes how Qualys can help in all three areas.
Overview
Meltdown allows any application to access all system memory, including memory allocated for the kernel. Mitigation for this vulnerability will require operating system patches and potentially firmware updates. Patches for this vulnerability may have a performance impact on systems. So far, only Intel chips and one ARM processor have been shown to be vulnerable. ARM has also discovered another variant (3a), which is similar to Meltdown and impacts several more of their processors.
Spectre allows an application to force another application to access arbitrary portions of its memory, which can then be read through a side channel. This vulnerability will require microcode updates in order to fully mitigate, in addition to software patches. According to Google Project Zero, this vulnerability impacts Intel, AMD, and ARM chips.
Mitigations
Microsoft has issued patches for all supported versions of Windows. Microsoft has also issued a guidance document for mitigations on client devices, and another for Windows servers. Please note that the patches released by Microsoft may be incompatible with certain antivirus software.
Microcode updates have been released by Intel to mitigate Spectre, and several Linux distributions have packaged the microcode in standard OS patches. It is not yet known if Microsoft will release microcode updates via Windows Update. Hardware vendors are expected to release the new microcode in the form of BIOS updates.
MacOS 10.13.2 mitigates some of the disclosed vulnerabilities, but MacOS 10.13.3 will enhance or complete these mitigations.
Processor vendor links:
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
https://www.amd.com/en/corporate/speculative-execution
https://developer.arm.com/support/security-update
Other software vendor patches:
https://www.vmware.com/us/security/advisories/VMSA-2018-0002.html
https://access.redhat.com/security/vulnerabilities/speculativeexecution
https://www.suse.com/support/kb/doc/?id=7022512
Customers with Qualys Vulnerability Management
Qualys has released several QIDs that detect missing patches for these vulnerabilities across several operating systems. A list of currently-released QIDs is being maintained in this Qualys Support article. The QIDs are supported by both authenticated scanning and the Qualys Cloud Agent.
- QID 43113 : Processor Information for Windows Target System
- QID 43110 : Apple Macintosh Processor Architecture
- QID 115048 : Processor Information for Unix Target
- QID 45177 : Processor Information for Solaris Target
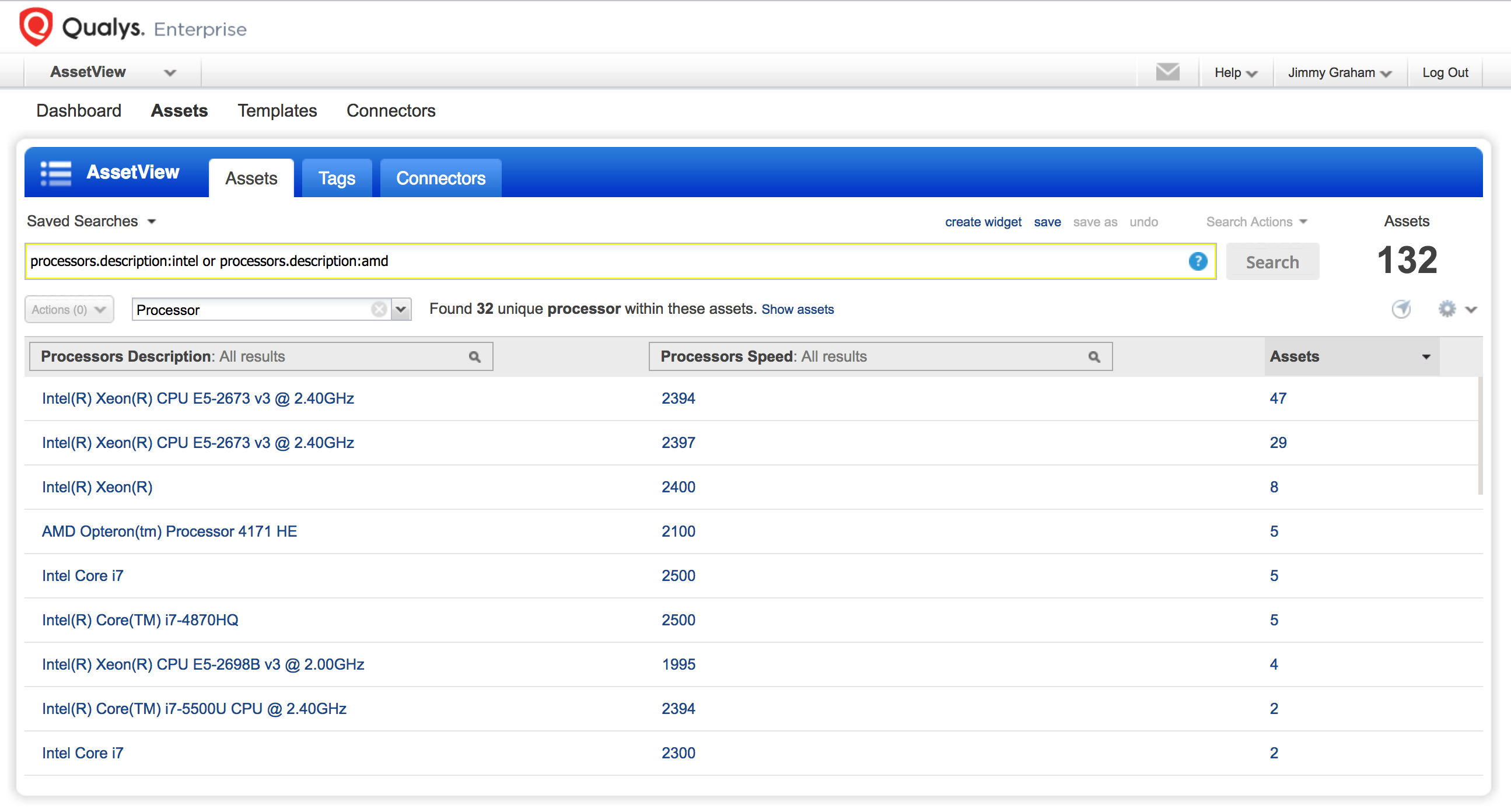
The Qualys Cloud Agent can be used to determine processor types by searching with AssetView on the processors.description field like this:
processors.description:intel or processors.description:amd
The results can also be grouped by processor type:
Get Started Now
To start detecting and protecting against critical vulnerabilities, get a Qualys Suite trial. All features described in this article are available in the trial.
The VIA Eden (C3/C7) processors do not have out-of-order execution so no they cannot be vulnerable to this issue. The problem needs the processor to execute instructions before it knows for certain that it needs to, if it eventually finds that it shouldn’t have executed those instructions it throws away the results. The problem is that there are remaining traces that it did actually execute the instruction.
Thanks a lot for the comment, Robert!
So i guess my VIA Epia M with C3 cpu is not vulnerable.
Thanks a lot.