Automatically Discover, Prioritize and Remediate Microsoft SMBv3 RCE Vulnerability (CVE-2020-0796) using Qualys VMDR

This month’s Patch Tuesday, Microsoft disclosed a critical “wormable” remote code execution (RCE) vulnerability in Microsoft Server Message Block 3.1.1 (SMBv3) protocol. The exploitation of this vulnerability opens systems up to a ‘wormable’ attack, which means it would be easy to move from victim to victim.
Qualys released a blog post earlier on how to identify SMBv3 vulnerability in your environment:
Microsoft Windows SMBv3 Remote Code Execution Vulnerability (CVE-2020-0796)
Here we describe how to resolve it with Qualys VMDR®.
Identify Assets, Discover, Prioritize and Remediate using Qualys VMDR®
Qualys VMDR, all-in-one vulnerability management, detection and response enables:
- Identification of known and unknown hosts running vulnerable SMBv3 servers and clients
- Automatic detection of vulnerabilities and misconfigurations for SMBv3 servers and clients
- Prioritization of threats based on risk
- Integrated patch deployment
Identification of Assets with SMBv3 Server or Client
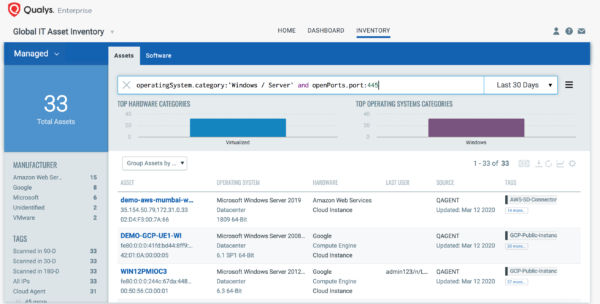
The first step in managing vulnerabilities and reducing risk is identification of assets. VMDR enables easy identification of hosts with SMBv3 Server/Client with open port “445” –
operatingSystem.category:`Windows/Server` and openPorts.port:445
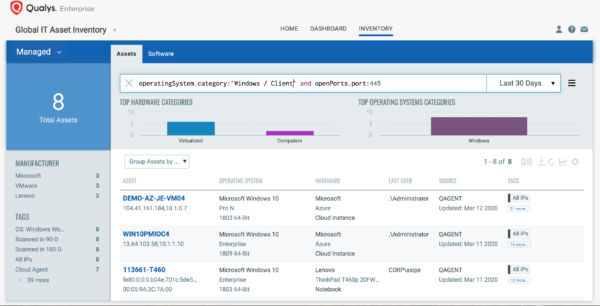
operatingSystem.category:`Windows/Client` and openPorts.port:445
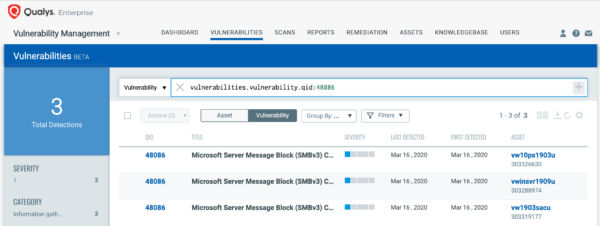
Using VMDR, you can also identify SMBv3 is enabled on the host via Qualys IG QID 45262 as shown below:
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’, eg – SMBv3. This helps in automatically grouping existing hosts with SMBv3 Server/Client as well as any new host spins up with SMBv3 server. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover SMBv3 RCE Vulnerabilities and Misconfigurations
Now that the hosts with SMBv3 Client/Server are identified, you want to detect which of these assets have flagged the CVE-2020-0796 vulnerability. VMDR automatically detects new vulnerabilities like CVE-2020-0796 based on the always updated Knowledgebase.
You can see all your impacted hosts for CVE-2020-0796 (or by Qualys ID: 91614 or 91616) for your ‘SMBv3’ asset tag in vulnerabilities view by using QQL query:
vulnerabilities.vulnerability.cveIds:`CVE-2020-0796`
This will return a list of all impacted hosts.
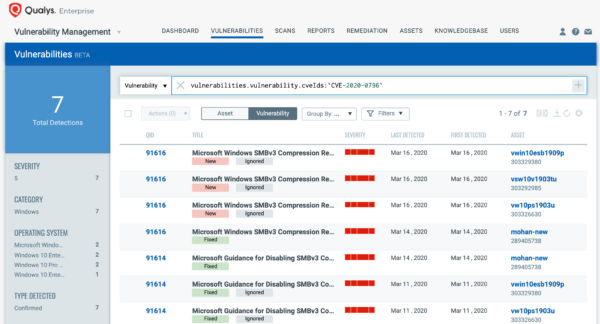
QID 91616 helps identify assets with patch (KB4551762) applied and QID 91614 helps identify assets with SMBv3 workaround applied for CVE-2020-0796 across all impacted operating systems using authenticated scanning or the Qualys Cloud Agent.
Along with the two confirmed vulnerability QIDs, Qualys released the following IG QID 48086, to help customers track assets on which they have the mitigation applied. This QID can be detected via remote unauthenticated and authenticated scans or via Qualys Cloud Agent.
QID 48086: Microsoft Server Message Block (SMBv3) Compression Disabled.
VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
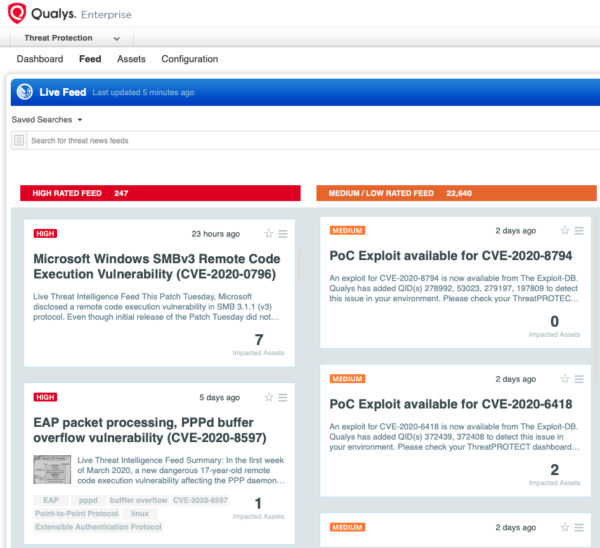
Simply click on the impacted assets for the SMBv3 threat feed to see the vulnerability and impacted host details.
With VM Dashboard, you can track SMBv3 vulnerabilities, impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of SMBv3 RCE vulnerability trends in your environment using Microsoft RCE SMBv3 Vulnerability Dashboard –
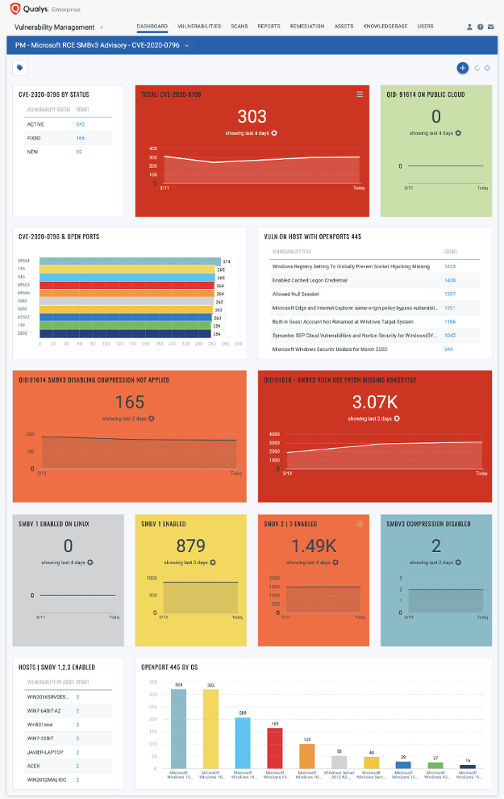
Configuration management adds context to overall vulnerability management
To overall reduce the security risk, it is important to take care of SMB server misconfigurations as well. Qualys VMDR shows your SMBv3 misconfiguration posture in context with your vulnerability posture, allowing you to see which hosts have SMBv3 RCE vulnerability. It also shows SMBv3 misconfigurations, elevating the risk for these hosts compared to the hosts for which there may be a vulnerability but where the default port 445 is not used or the configuration is already hardened.
With Qualys Policy Compliance module of VMDR, you can automatically discover open ports or firewall restricted port 445 and if they have misconfigurations in context to CVE-2020-0796 vulnerability.
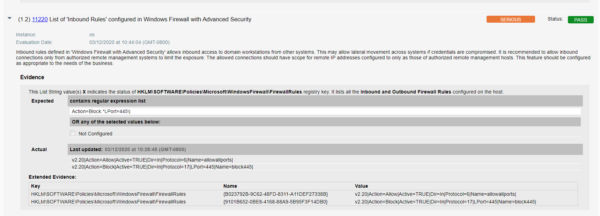
- Qualys configuration ID – 11220 “List of ‘Inbound Rules’ configured in Windows Firewall with Advanced Security” would be evaluated against to identify if port 445 is blocked in windows firewall inbound rules as shown below –
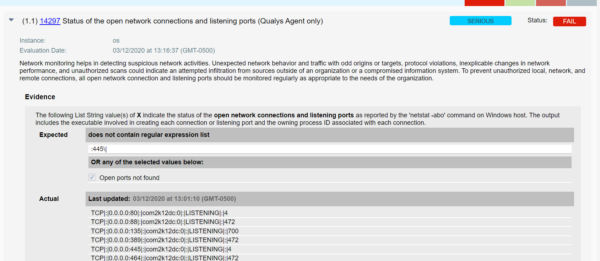
- Qualys configuration ID – 14297 “Status of the open network connections and listening ports” would be evaluated to identify if port 445 is open and listening as shown below –
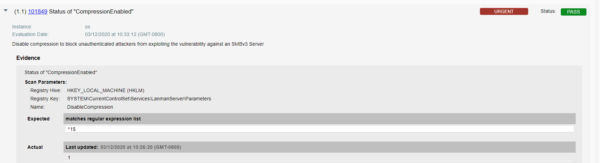
- Qualys UDC configuration ID – 101849 “Status of ‘CompressionEnabled’” (UDC type: “Registry Value Content Check”) would be evaluated to verify if the value of “DisableCompression” is set to “1” as shown below:
Risk-Based Prioritization of SMBv3 RCE Vulnerability
Now that you have identified the hosts, versions and context of detected vulnerabilities and misconfigurations, you may want to prioritize your remediation based on the risk, as each vulnerable asset might not pose the same risk.
High Risk:
- Hosts with SMBv3 enabled and patch or workaround not applied are at high risk.
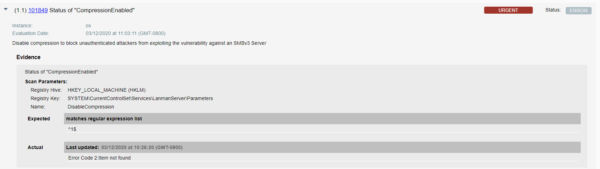
- If due to the business reasons it is not possible to apply the patch on the hosts for which CVE-2020-0796 is detected. Customers can check for misconfigurations (CIDs 14297 and 101849 controls are failing) as shown below-

Medium Risk:
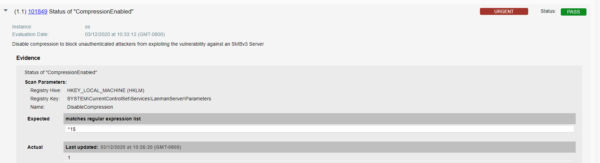
- Hosts with SMBv3 enabled for which CVE-2020-0796 is detected, however, the configuration 101849 is detected as hardened are at medium risk.
Response by Patching and Remediation
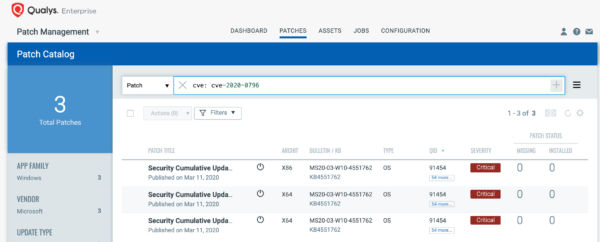
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select “cve:`CVE-2020-0796`” in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – SMBv3.
For proactive, continuous patching, you can create a daily job with a 24-hour “Patch Window” to ensure all hosts will continue to receive the required patches as new patches become available for the emerging vulnerabilities.
Users are encouraged to apply patches as soon as possible.
In cases where due to business reasons, it is not possible to apply patches, it is recommended that you reduce your security risk by remediating the related configuration settings for all running SMBv3 servers as provided in Qualys Policy Compliance by applying following workarounds:
- Disable SMBv3 compression
You can disable compression to block unauthenticated attackers from exploiting the vulnerability against an SMBv3 Server with the PowerShell command below –
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force
- Block TCP port 445 at the enterprise perimeter firewall
TCP port 445 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability.
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching critical SMBv3 RCE vulnerability CVE-2020-0796.