Qualys Research Alert: OpenSSL 3.0.7 – What You Need To Know

Table of Contents
- What is OpenSSL?
- What is OpenSSL Vulnerability CVE-2022-3786 & CVE-2022-3602?
- Vulnerable Versions
- What Should Organizations Do?
- How Can Qualys Help?
- Discover Vulnerable Instances Using Qualys VMDR
- Discover Vulnerable Container Images Using Qualys Container Security (CS)
- Discover Vulnerable Instances Using Qualys Web Application Scanning (WAS)
- Patch Vulnerable Systems Using Qualys Patch Management (PM)
- Initiate Endpoint Response Actions Using Custom Assessment and Remediation (CAR)
- We encourage our customers to leverage our Vulnerability Detection Pipelineto track new vulnerability detection development and status.
- Frequently Asked Questions
On Tuesday, November 1, 2022, the OpenSSL project released version 3.0.7 of OpenSSL, an update that patches two buffer overflow vulnerabilities which can be triggered in X.509 certificate verification. These vulnerabilities only apply to OpenSSL 3.x.
Both these vulnerabilities are rated as HIGH and downgraded from CRITICAL as initially rated in the pre-notification.
What is OpenSSL?
OpenSSL is the core open-source library that implements SSL and TLS protocols which makes it possible to securely communicate over the internet.
What is OpenSSL Vulnerability CVE-2022-3786 & CVE-2022-3602?
A buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking. Note that this occurs after certificate chain signature verification and requires either a CA to have signed a malicious certificate or for an application to continue certificate verification despite failure to construct a path to a trusted issuer. An attacker can craft a malicious email address in a certificate to overflow an arbitrary number of bytes containing the `.’ character (decimal 46) on the stack. This buffer overflow could result in a crash (causing a denial of service).
In a TLS client, this can be triggered by connecting to a malicious server. In a TLS server, this can be triggered if the server requests client authentication and a malicious client connects.
Vulnerable Versions
OpenSSL versions 3.0 through 3.0.6 are vulnerable. The commonly deployed OPENSSL 1.1.1 is not vulnerable.
What Should Organizations Do?
Organizations should prioritize inventorying and scanning all systems with vulnerable versions of OpenSSL.
How Can Qualys Help?
Inventory OpenSSL Using Qualys CSAM
Qualys CSAM makes it easy to identify assets containing OpenSSL. The following QQL query will identify assets with OpenSSL installed.
Software Query: software:(name:OpenSSL and version>=3.0 and version< 3.0.7)
The QQL below will help identify assets that have vulnerable versions of OpenSSL installed.
Query: software:(name:’OpenSSL’) 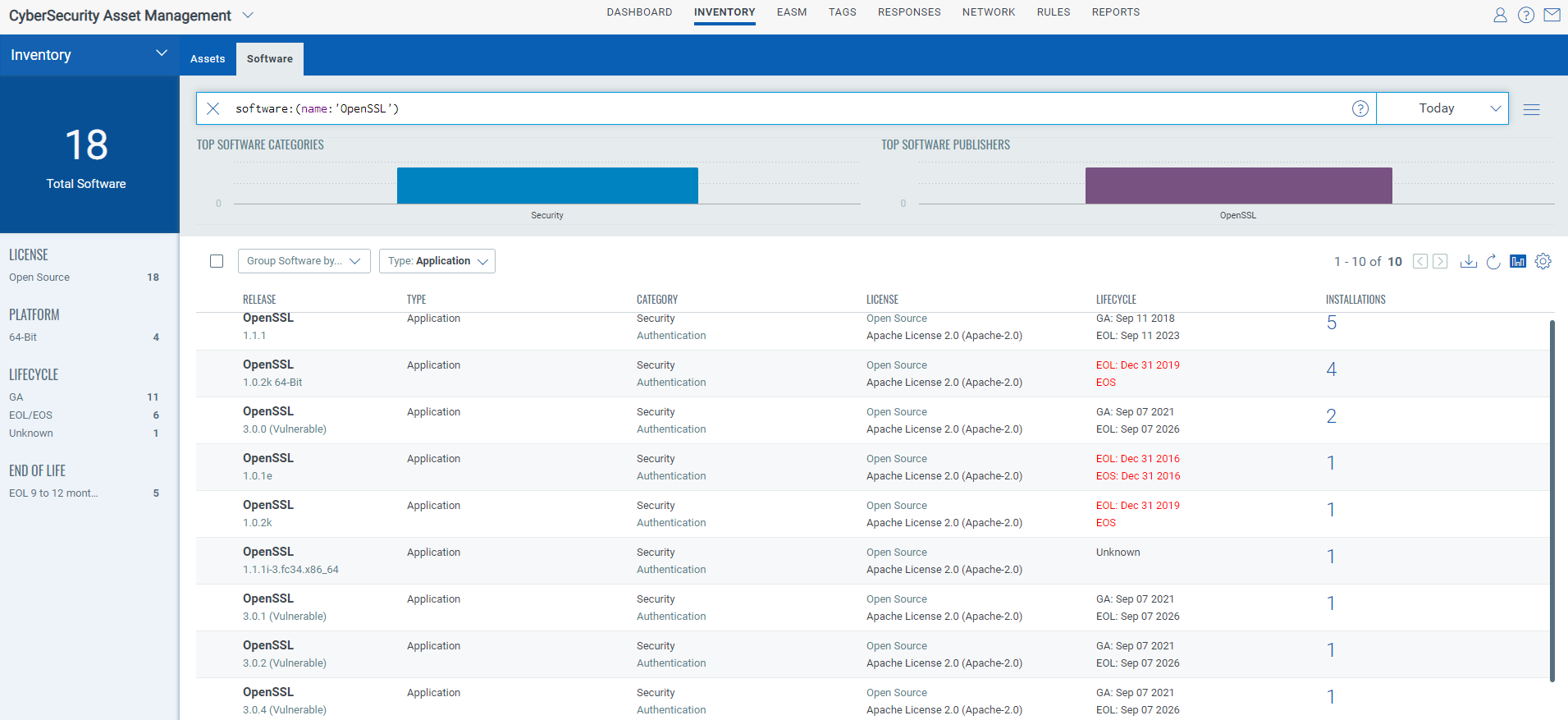
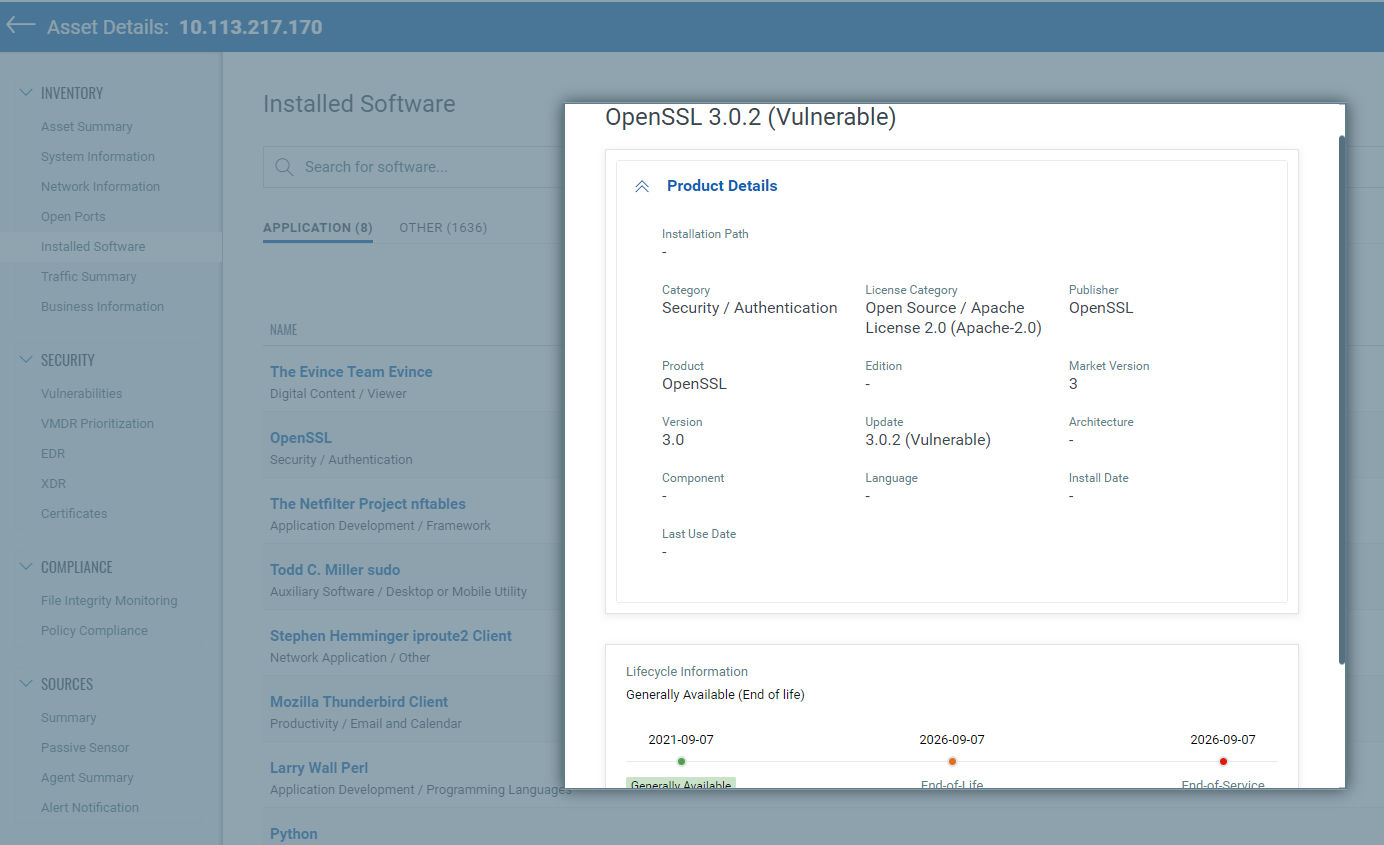
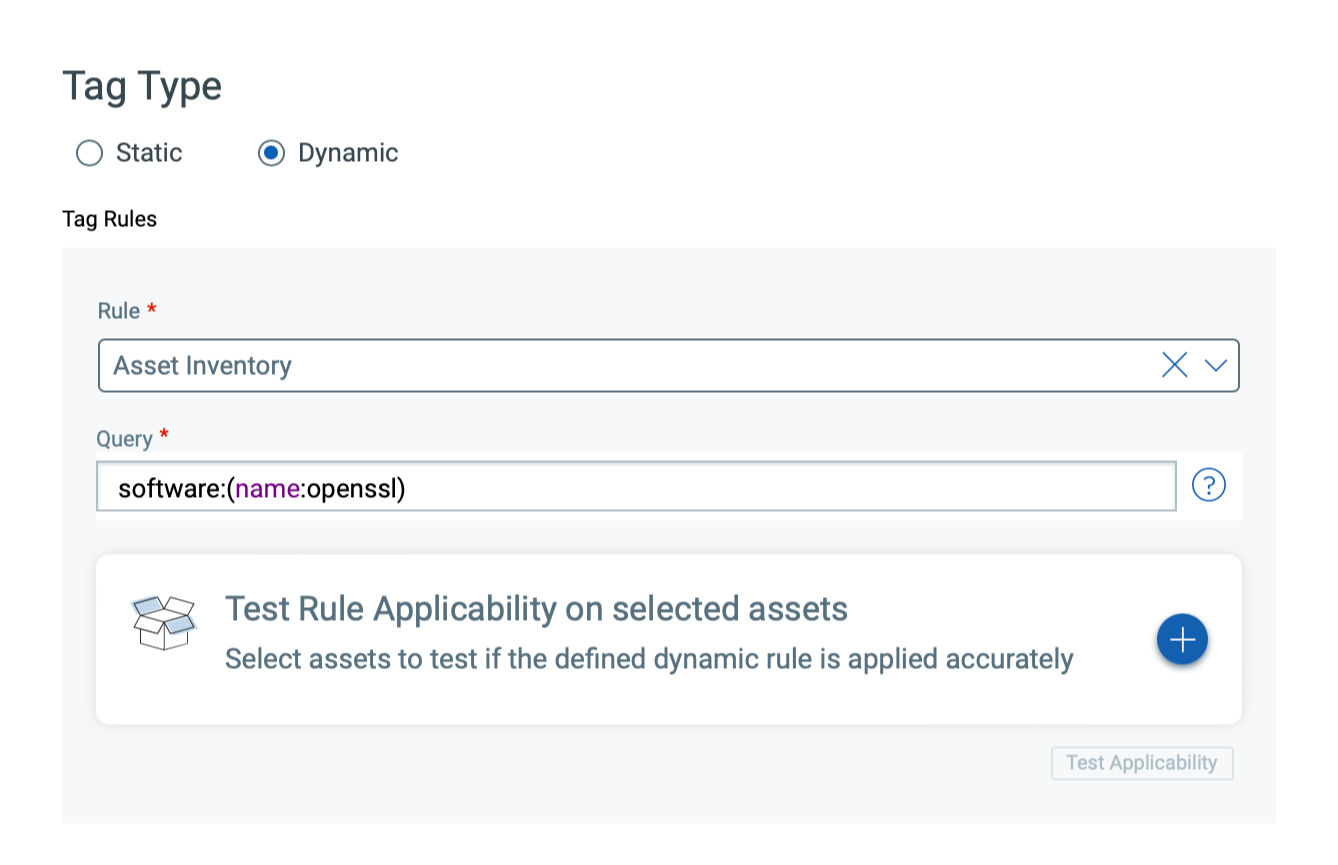
Tag Potentially Vulnerable Assets with CSAM
In addition to identifying the assets, Qualys also recommends customers tag the assets with OpenSSL installed.
Discover Vulnerable Instances Using Qualys VMDR
Qualys QID Coverage
Qualys will be releasing the QIDs in the table below and the first set of QIDs will become available on 11 AM PT on Oct 31st. Vulnsigs and manifest versions will be updated as soon as they are released.
Search for the following QIDs in your subscription to find vulnerable instances.
| QID | Title | Supported On |
|---|---|---|
| 38879 | OpenSSL 3.x < 3.0.7 Critical Vulnerability | Agent + Scanner, Container Security sensor |
| 377733 | OpenSSL 3.x Less Than 3.0.7 Critical Vulnerability (Scan Utility) | Agent + Scanner |
| 520001 | OpenSSL3.x Less Than 3.0.7 Critical Vulnerability | WAS |
| 240798 | Red Hat Update for Open Secure Sockets Layer (OpenSSL) (RHSA-2022:7288) | Agent + Scanner, Container Security sensor |
| 988531 | Rust (Rust) Security Update for openssl-src (GHSA-8rwr-x37p-mx23) | Container Sensor via SCA |
| 988530 | Rust (Rust) Security Update for openssl-src (GHSA-h8jm-2×53-xhp5) | Container Sensor via SCA |
| 752752 | SUSE Enterprise Linux Security Update for openssl-3 (SUSE-SU-2022:3843-1) | Agent + Scanner, Container Security sensor |
| 502587 | Alpine Linux Security Update for Open Secure Sockets Layer3 (OpenSSL3) | Agent + Scanner, Container Security sensor |
| 690972 | Free Berkeley Software Distribution (FreeBSD) Security Update for Open Secure Sockets Layer (OpenSSL) (0844671c-5a09-11ed-856e-d4c9ef517024) | Agent + Scanner, Container Security sensor |
| 710678 | Gentoo Linux Open Secure Sockets Layer (OpenSSL) Multiple Vulnerabilities (GLSA 202211-01) | Agent + Scanner, Container Security sensor |
| 199012 | Ubuntu Security Notification for Open Secure Sockets Layer (OpenSSL) Vulnerabilities (USN-5710-1) | Agent + Scanner, Container Security sensor |
| 160191 | Oracle Enterprise Linux Security Update for Open Secure Sockets Layer (OpenSSL) (ELSA-2022-7288) | Agent + Scanner, Container Security sensor |
| 160192 | Oracle Enterprise Linux Security Update for Open Secure Sockets Layer (OpenSSL) (ELSA-2022-9968) | Agent + Scanner, Container Security sensor |
| 283270 | Fedora Security Update for Open Secure Sockets Layer (OpenSSL) (FEDORA-2022-502f096dce) | Agent + Scanner, Container Security sensor |
Please note, once the vulnerability is disclosed on Nov 1st each vendor will probably release back ported patches for the vulnerability. Qualys research team is closely tracking the vulnerability and will release QIDs to detect those backported versions.
Discover Vulnerable Container Images Using Qualys Container Security (CS)
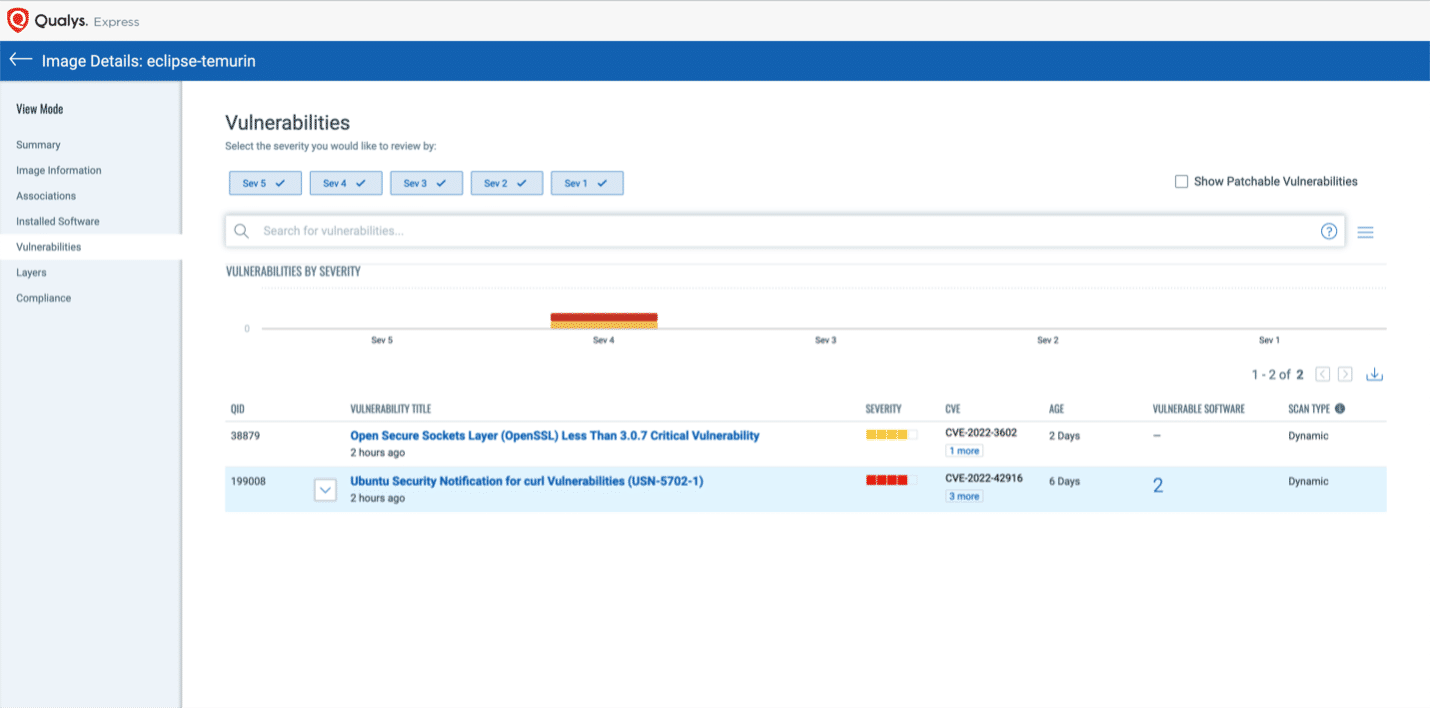
Qualys Container Security (CS) can detect vulnerable versions of OpenSSL 3.0 though 3.0.6 with the following QID: 38879
To see all the images impacted by these vulnerabilities, navigate to the Container Security application, go to Assets > Images, and search using the following QQL query:
vulnerabilities.qid: `38879` 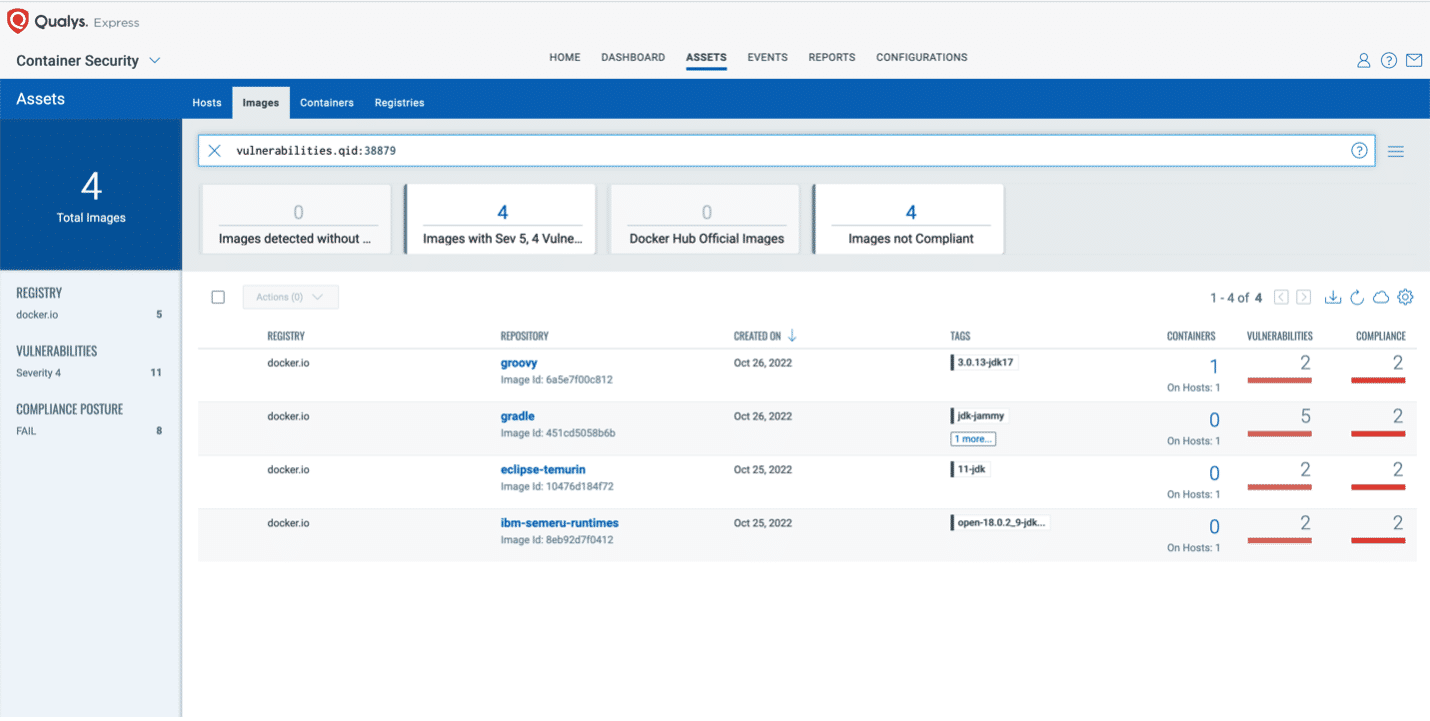
Select the image and navigate to the Vulnerabilities tab to view details of the vulnerability.
Discover Vulnerable Instances Using Qualys Web Application Scanning (WAS)
Qualys WAS QID Coverage
Qualys Web Application Security (WAS) can detect vulnerable versions of OpenSSL 3.0 though 3.0.6 with the following QID:
| QID | Title |
|---|---|
| 520001 | Open Secure Sockets Layer (OpenSSL) Less Than 3.0.7 Critical Vulnerability |
QID 520001 is a passive check that identifies vulnerable versions of OpenSSL by extracting any OpenSSL version information from http response header.
Please stay tuned for more updates. Qualys Research team will be regularly updating the blog as more details become available.
Patch Vulnerable Systems Using Qualys Patch Management (PM)
Once all OpenSSL vulnerabilities are found in the environment, customers can use Qualys patch management to patch vulnerable applications.
As OpenSSL is a library used by many OSes and applications, it is safe to assume that in the near future many of those applications will issue a patch to fix this OpenSSL vulnerability. Qualys patch management can be used on both Windows and Linux to patch those applications.
Qualys patch management also offers a way to execute PowerShell scripts on Windows and shell scripts on Linux machines. It can be leveraged to quickly create mitigation steps.
Initiate Endpoint Response Actions Using Custom Assessment and Remediation (CAR)
Time is a critical factor in such zero-day situations. Any delays in detection and remediation leave organizations vulnerable to security risks. Qualys CAR capabilities allow security practitioners to quickly create and execute custom scripts to collect data and initiate response actions on endpoints.
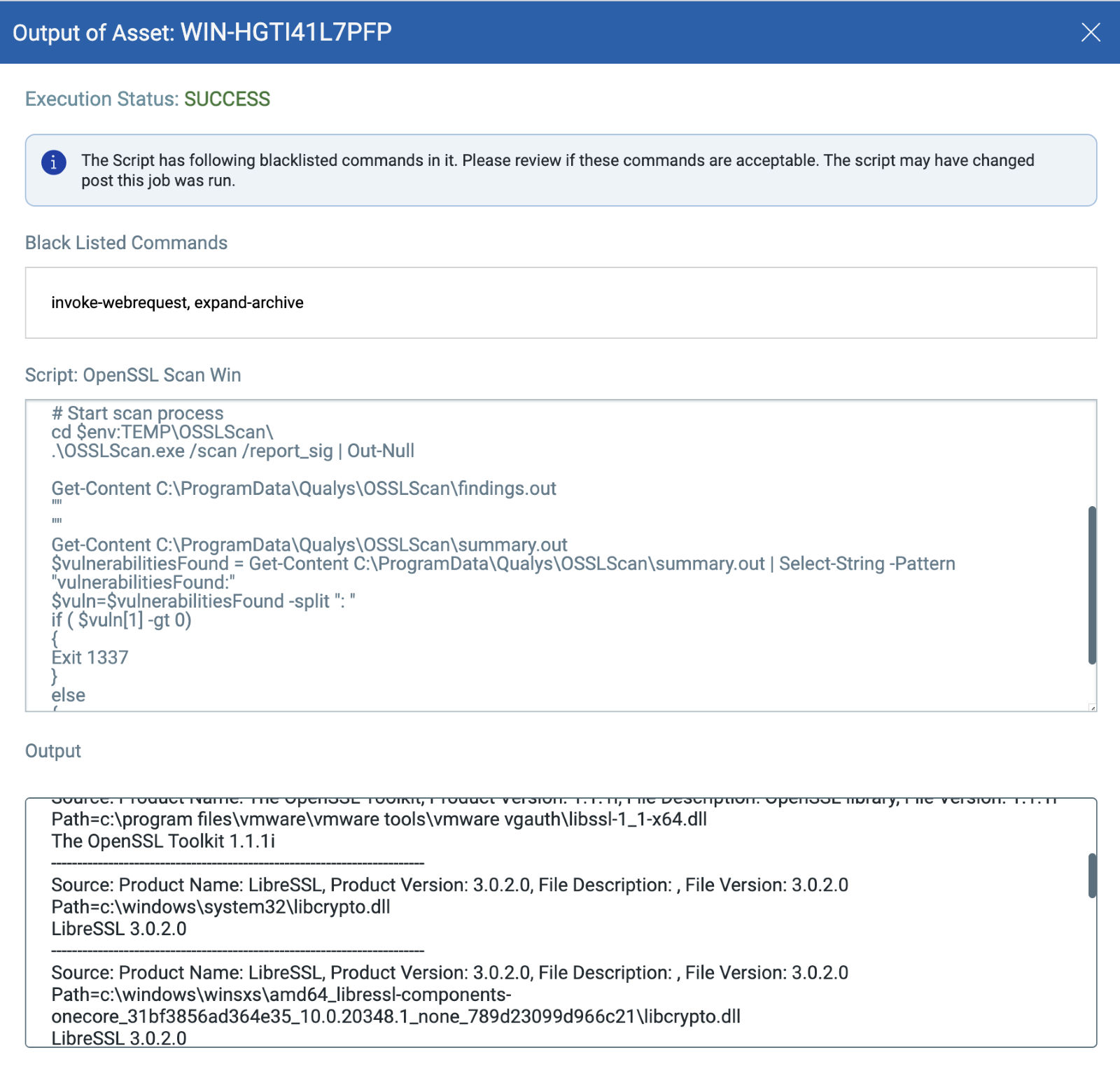
Qualys CAR customers can execute this out-of-band detection utility for OpenSSL on required assets/asset tags. This tool will help find all vulnerable instances regardless of OpenSSL binaries as it will scan the entire hard drive(s) and the utility will output its results to a console and to "%ProgramData%\Qualys\ OSSLScan\findings.out".
As the utility performs a “deep” search on the entire hard drive which is a time-consuming and CPU-consuming task. As such, we recommend running this tool “out-of-band”.
QID 377733: Open Secure Sockets Layer (OpenSSL) Less Than 3.0.7 Critical Vulnerability (Scan Utility) will be flagged based on the output of the utility (“%Pr Qualys\OSSLScan\findings.out”).
Please stay tuned for more updates. Qualys Research team will be regularly updating the blog as more details become available.
We encourage our customers to leverage our Vulnerability Detection Pipeline to track new vulnerability detection development and status.
- About the Qualys Vulnerability Detection Pipeline
- Qualys Vulnerability Management New QID Development, Prioritization, and New QID Feature Request Process
- Qualys Vulnerability Detection (QID) Recurring Vendor and Product Support Index
- Qualys Customer Service Portal (CSP) | Vulnerability Management New QID Feature Request Case Creation Process
Frequently Asked Questions
Is Qualys Cloud Platform impacted by CVE-2022-3786 or CVE-2022-3602?
No. Qualys production environments (shared platforms and private platforms), codebase, customer data hosted on the Qualys Cloud Platform, Qualys Agents or Scanners do not leverage OpenSSL 3.0, and as a result, are not impacted by the vulnerability.
Comments are closed.
Why would this highly publicized CVE be created as a Potential by Qualys?
Because, John, we don’t know what the vulnerability is yet, only that it affects versions GTE 3.0 and LT 3.0.7. As more information becomes available, the Vulnerability Research Team will make updates appropriate to the publically disclosed vulnerability information.
On Tuesday, November 1, 2022, the OpenSSL project will release a new version of OpenSSL version 3.0.7 that will patch an as-yet-undisclosed vulnerability in current versions of OpenSSL.
You’ll find more about our triage process here: Qualys Vulnerability Management New QID Development, Prioritization, and New QID Feature Request Process
Is Microsoft cloud services such as Sentinel are impacted too?
Other detection products are able to identify DLL’s for 3.x and report them as vulnerable. Per the Openssl site, any 3.x version is still a vulnerability ill regardless of the Vendor or not releasing data. As a vulnerability tool, Qualys should report vulnerabilities, not just wait for Vendor data. If I have vulnerable devices in my environment, my CISO wants to know that, not that Qualys is waiting on vendor data while other tools can show the full visibility of systems at risk.