Risk Fact #1: Speed Is the Key to Out-Maneuvering Adversaries
Qualys Blog Series – Threat Research Unit Report
The 2023 Qualys TruRisk Research Report from the Qualys Threat Research Unit (TRU) provides detailed research insights that are organized into five separate Risk Facts. In this blog, we look at Risk Fact #1 – Speed is the key to out-maneuvering adversaries.
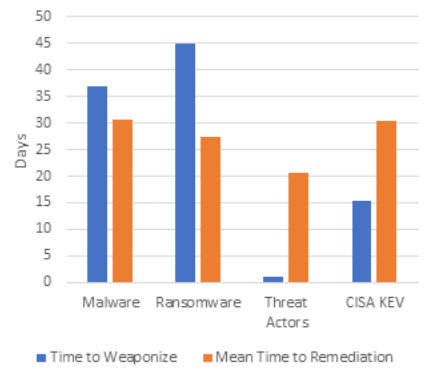
The main lesson from Risk Fact #1 is obvious yet striking. On average, it takes an average of 30.6 days to patch weaponized vulnerabilities. Since vulnerabilities weaponize 10 days faster than that (19.5 days to be exact), organizations are exposed continuously to an enormous level of cyber risk . For the vulnerabilities on the U.S. Cyber Security and Infrastructure Security Agency’s (CISA) Known Exploited Vulnerability list, the disparity between the Time to Weaponize vs. Mean Time to Remediate (MTTR) vulnerabilities is even more significant.
Whether the lag in patching is due to cybersecurity tooling, talent, or time, two takeaways are clear from the data.
- Security teams are disadvantaged in their fight against threat actors.
- A better approach to vulnerability management is sorely needed, including prioritization, faster remediation, and ongoing monitoring.
Let’s focus on the second point and what you can do about it.
Vulnerability Prioritization vs. Patch
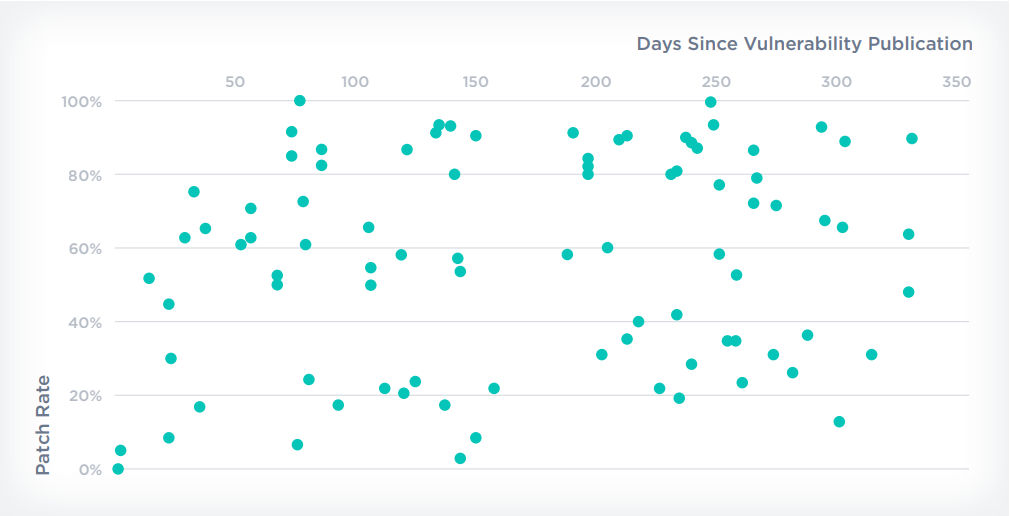
With vulnerabilities spilling in by the minute, security and IT teams need to know what’s critical, and why. This information informs fast and targeted remediation workflows allowing for security-IT collaboration and reduced MTTR. However, attributing vulnerabilities to a named threat actor is often time-consuming and difficult. On average, attribution happens 95 days (about three months) after a vulnerability is published and 74.3 days (about two and a half months) after the CVE is patched. In addition, attribution does not always indicate faster patching. For example, the scatter chart below compares the age vulnerabilities to the remediation completion in percentages of 34 different products. These results are literally all over the map!
However, what happens when we filter vulnerabilities and patches down to two product categories only? For example, Windows and Chrome?
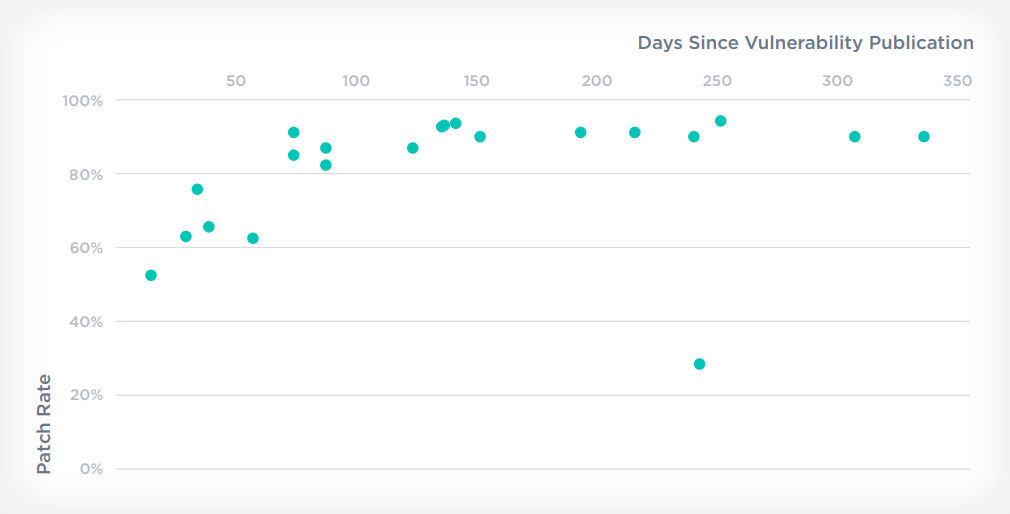
After filtering vulnerabilities down to those associated with Windows and Chrome only, patches are deployed to approximately 90% of the organization’s infrastructure before the next wave of monthly patching begins. This is good news!
The reason for this positive change is that the number of vulnerabilities that these two products receive is significantly higher than most, making vulnerability prioritization more accurate and efficient for security stakeholders. Second, both Windows and Chrome patches are easily automated, allowing security and IT teams to catch up to the faster attack speed of threat actors. The recipe for success is two-fold: 1. Good data inputs and, 2. Data-informed automation.
Regarding Risk Fact #1, the research from Qualys TRU underscores how a unified approach to vulnerability management and patch management can improve vulnerability prioritization and automated response. The level of accessible and actionable threat intelligence can be directly correlated with remediation success rates.
Malicious actors make it their business to understand the vulnerabilities that can render the most damage to their targets. At Qualys, it is our business to shift the asymmetric access to threat knowledge away from threat actors to CISOs and their security teams. Stay tuned here for more practical insights from the Qualys TRU Research Report.
Unlock Unparalleled TruRisk Insights
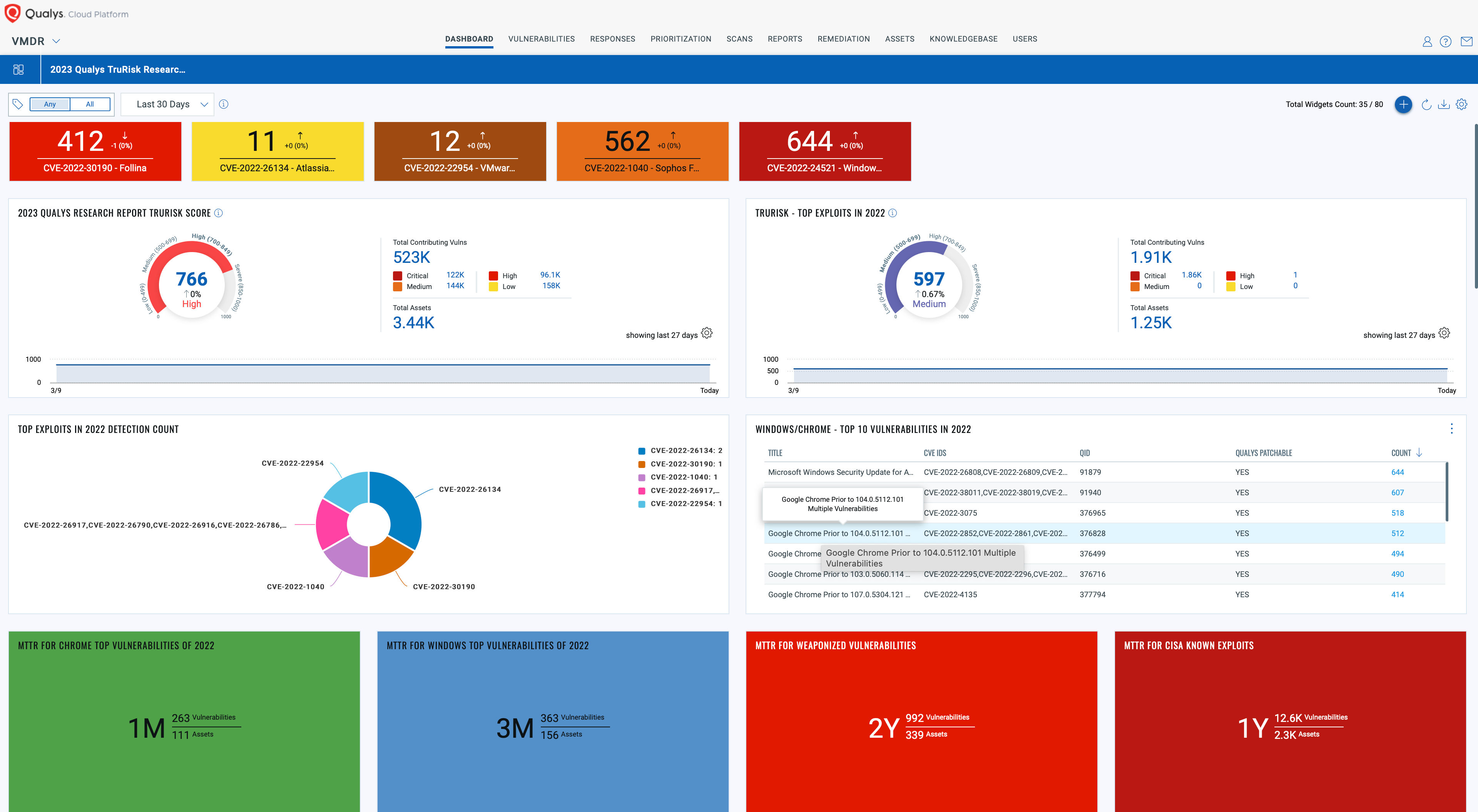
Download and import the Qualys 2023 TruRisk Research Report into your Qualys VMDR subscription today!
This comprehensive dashboard sheds light on your organization’s exposure to risks highlighted in the report, empowering you to make informed decisions and bolster your defenses. Don’t miss out on the opportunity to improve your cybersecurity posture with the cutting-edge research and analysis from the Qualys Threat Research Unit (TRU).
Read the next blog in this series: Automation Is the Difference Between Success and Failure
Get the full 2023 Qualys TruRisk Research Report and learn about all five Risk Facts now.