Risk Fact #2: Automation Is the Difference Between Success and Failure
Qualys Blog Series – Threat Research Unit Report
Organizational leaders dread the consequences of a successful cyber-attack, which can be devastating due to data loss, reputational damage, and legal repercussions. Under the hood, security professionals are acutely focused on finding technical means to discover and remediate the risks – and keep pace with adversaries.
Consequently, cybersecurity strategy typically incorporates reactive and proactive elements, which entail the use of specialized tools, processes, and skills of cybersecurity professionals. To help beat the pace of attackers, automation of security processes has become vital, especially automated patching of vulnerabilities in critical IT assets and applications.
However, as recent research from the Qualys Threat Research Unit (TRU), has shown, many businesses still rely on outdated and manual methods for patching their systems.
In this blog, we examine Risk Fact #2 from the 2023 Qualys TruRisk Research Report: “Automation is the difference between success and failure.”
Read the previous blog in this series: Speed Is the Key to Out-Maneuvering Adversaries
Read more: Risk Fact #2: Automation Is the Difference Between Success and FailureDefensive Security through Patching
For patching and vulnerability remediation, automation has become a synonymous requirement. With well-curated and threat-data-tuned automation actions, security and IT teams can better work in concert. Data-guided patch automation eliminates previously manual tasks and keeps an organization more secure by reducing the time in which threats roam free within the modern hybrid environment.
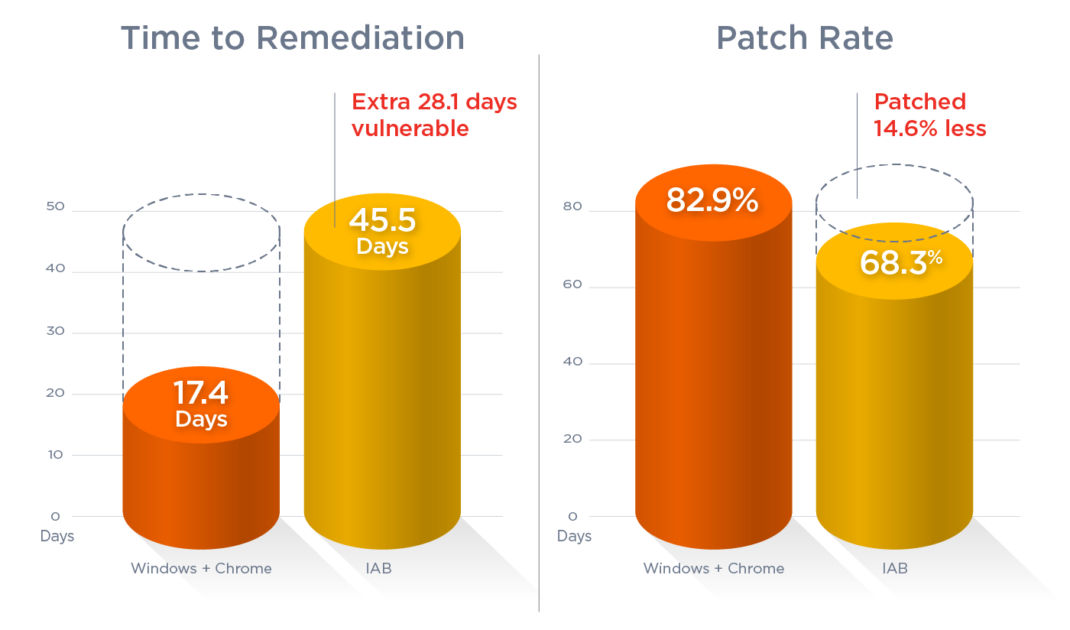
In the first blog in this series, we examined weaponized vulnerabilities associated with Chrome or Windows due to their prevalence in networks worldwide. With these two products, the mean time to remediation (MTTR) is 17.4 days, with an effective patch rate of 82.9%. Interestingly, when you consider that Windows and Chrome are patched twice as fast and twice as often as other applications, the takeaway is alarming. Organizations are patching too slowly.
Automated Patching Speeds Remediation
On the bright side, the report also reveals that patches that can be automated are deployed 45% more often and 36% faster than those that must be done manually. Stakeholders must understand that automation isn’t just convenient; it is a substantial defensive security feature for getting critical assets quickly into the safety zone.
Want more proof?
Vulnerabilities that can be automated with an automated patch management solution have a mean time to remediation of 25.5 days, while manually patched vulnerabilities were remediated in 39.8 days. The patch rate for the automatable set was 72.5% compared to 49.8% for those in the manual set.
Overall, the report highlights the importance of automation in successful patching, as well as the need for organizations to prioritize the patching of Windows and Chrome vulnerabilities. We invite you to learn more about this topic and discover additional insights from the report. Download the full report from Qualys and stay up to date with the latest information on cyber security. Getting this timely study will help you to protect your business and its assets from the risks of cyberattacks.
Unlock Unparalleled TruRisk Insights
Download and import the Qualys 2023 TruRisk Research Report into your Qualys VMDR subscription today!
This comprehensive dashboard sheds light on your organization’s exposure to risks highlighted in the report, empowering you to make informed decisions and bolster your defenses. Don’t miss out on the opportunity to improve your cybersecurity posture with the cutting-edge research and analysis from the Qualys Threat Research Unit (TRU).
Read the next blog in this series: Initial Access Brokers Attack What Organizations Ignore
Get the full 2023 Qualys TruRisk Research Report and learn about all five Risk Facts now.
Free Trial
Leverage the power of the Qualys Threat Research Unit (TRU) and threat intelligence from 25+ external sources.
About Qualys TRU
Advanced technologies are revolutionizing lives and economies around the world. Cyberthreats are growing at a similar pace, endangering access to the services that improve lives everywhere.
By empowering others with our research and insights, we can secure and defend the digital world from bad actors who create chaos and erode trust.
We are the Qualys Threat Research Unit (TRU). Our shield is your shield.