Risk Fact #3: Initial Access Brokers Attack What Organizations Ignore
Qualys Blog Series – Threat Research Unit Report
“Divide and Conquer” is an emerging and winning strategy for cyber criminals who split responsibilities to improve execution of the attack process. Some threat actors specialize in the back end, which often is ransomware deployed at scale. The front end of attacks – planning and executing penetration of vulnerable IT – is increasingly done by a different threat actor called an Initial Access Broker (IAB). In the 2023 Qualys TruRisk Research Report, Risk Fact #3 addresses the urgent need for organizations to quicken the pace of patching vulnerabilities leveraged by IABs for successful penetrations.
Read the previous blog in this series: Automation Is the Difference Between Success and Failure
How Initial Access Brokers (IABs) Gain Access
Initial Access Brokers (IABs), sometimes called “affiliates,” can follow multiple paths to execute a successful breach. Vulnerabilities may exist in many places along these paths, and like all attackers, IABs welcome whatever vector offers the quickest and easiest path into an organization’s network and IT assets.
The illustration shows two of these optional attack paths discovered by Qualys Threat Research Unit (TRU) research. In the top lane is where IABs seek to exploit the perimeter devices of their intended target, such as firewalls and web applications. IABs seek misconfigurations such as default passwords or exposed services to find a way in or exploit vulnerabilities for unpatched systems. Another path is leveraging valid credentials and gaining direct access to the environment. IABs will either attempt to steal the credentials, buy them in the dark web which were stolen from other breaches, or guess/brute force the passwords. IABs may also execute phishing attacks to achieve the same result. By leveraging valid accounts, the threat actor can move around the environment with more stealth than relying on exploitation.
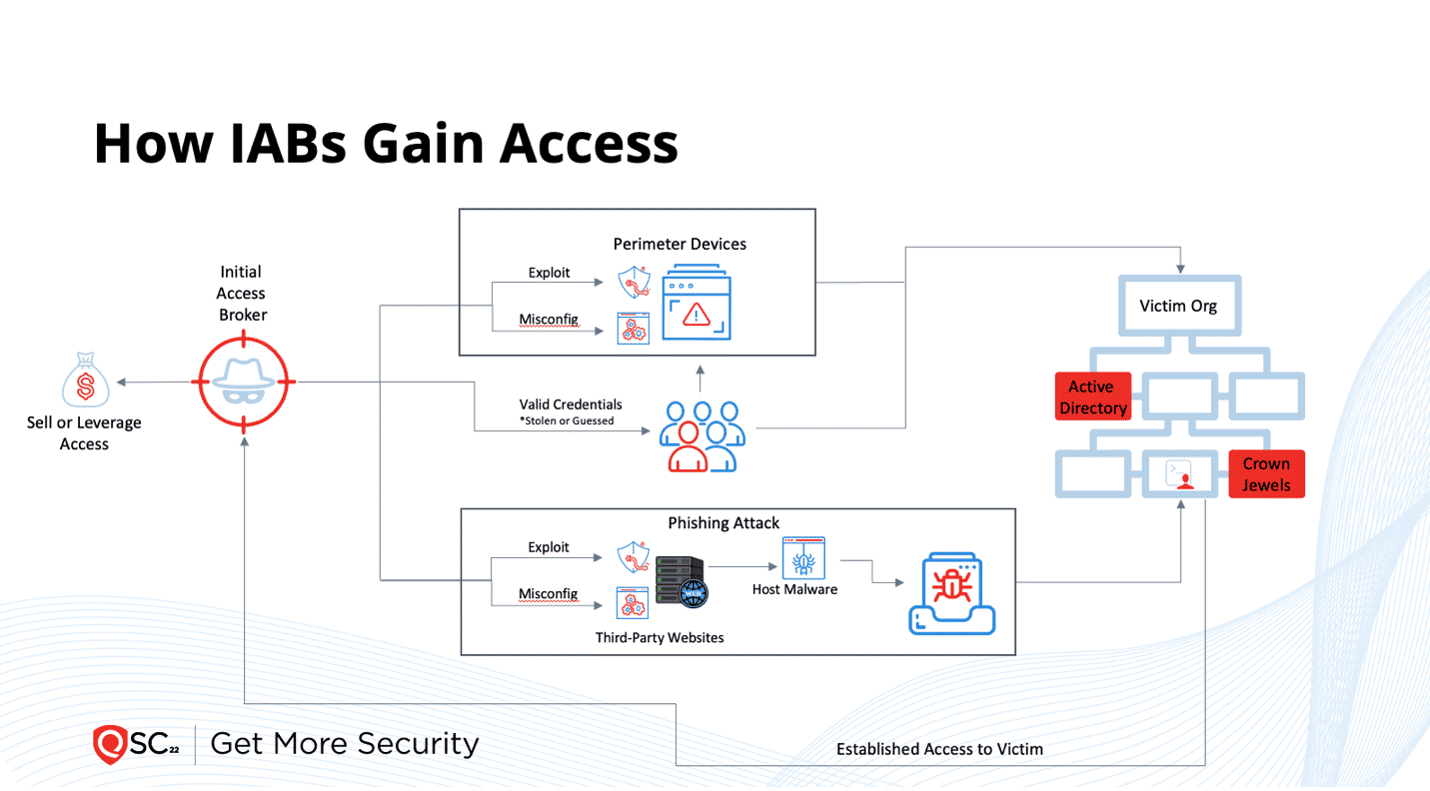
After successfully breaching an entity, the IAB sells related access instructions to another criminal gang specializing in scaled back-end ransomware or uses the information itself. Thus, money can be made from each part of the attack process. Table 3 in the 2023 Qualys TruRisk Research Report lists 17 new related CVEs added to the IAB toolkit during 2022.
Remediation Timelines for Initial Access Broker (IAB) Attacks
Many of the 17 CVEs affect perimeter devices or applications encountered when an IAB attacker attempts initial access. Remediation timelines for these CVEs are much worse than Windows and Chrome described in our last blog in this series. IAB vulnerabilities have a mean time to remediation of 45.5 days, compared to 17.4 days for Windows and Chrome. The patch rates are also lower, patched at a rate of 68.3% compared to 82.9% for Windows and Chrome.
Faster Initial Access Broker (IAB) Remediation: Stat!
Data from TRU research show that because organizations are getting quicker at patching Windows and Chrome, threat actors – especially IABs – are forced to leverage vulnerabilities outside of the “big two.” The data also suggest that when defenders control the narrative, threat actors are forced to switch their tactics, techniques, and procedures to more challenging attack paths. When this happens, threat actors tend to make more mistakes, create more noise, and generate more detection opportunities for defenders.
The key lesson from Risk Fact #3 is: Patch IAB vulnerabilities faster! Making this a priority will spoil the easy gains by attackers and help keep your critical IT assets safe from ransomware and other nefarious fallout. Check out details for Risk Fact #3 and the rest of TRU’s discoveries by downloading and reading the 2023 Qualys TruRisk Research Report.
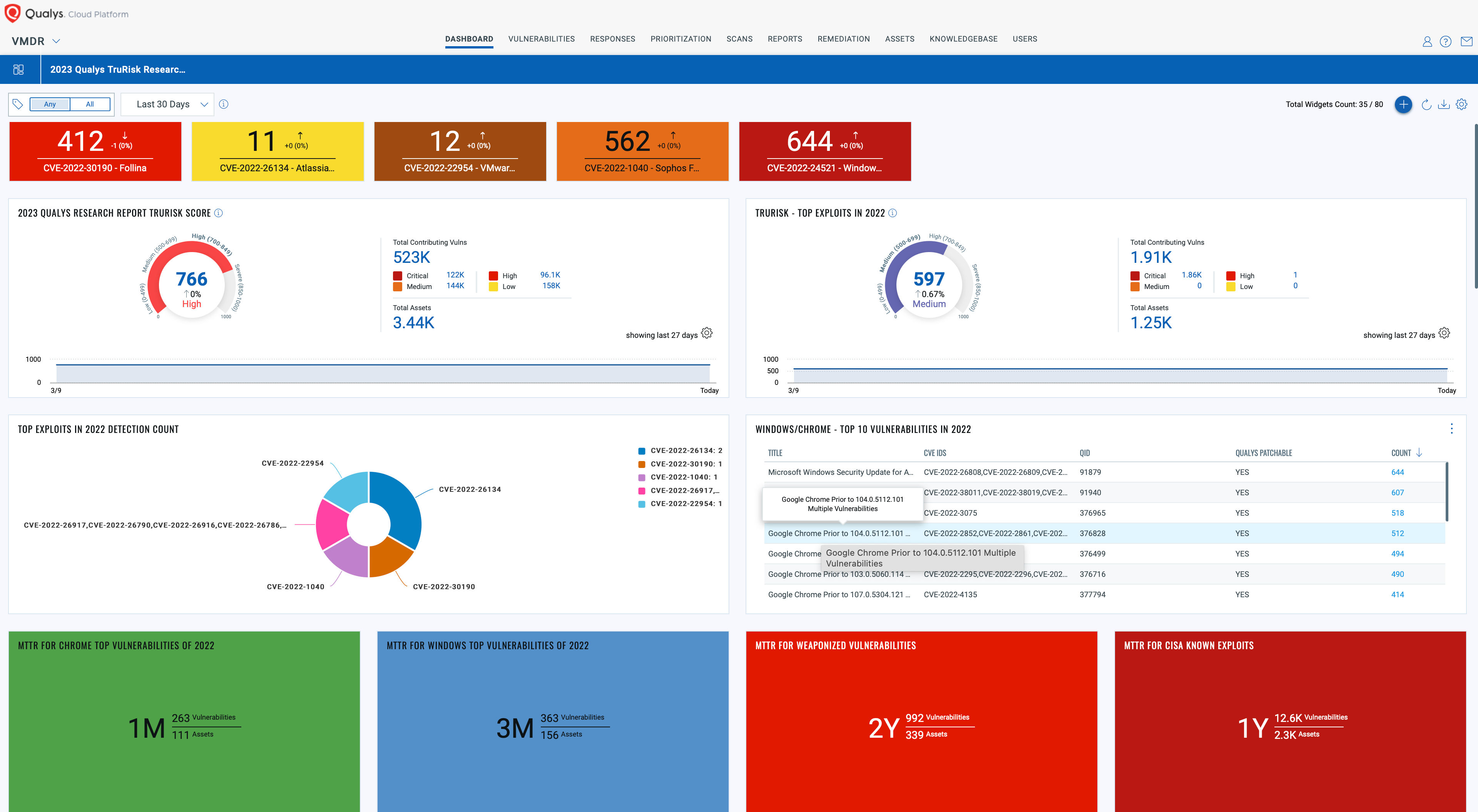
Unlock Unparalleled TruRisk Insights
Download and import the Qualys 2023 TruRisk Research Report into your Qualys VMDR subscription today!
This comprehensive dashboard sheds light on your organization’s exposure to risks highlighted in the report, empowering you to make informed decisions and bolster your defenses. Don’t miss out on the opportunity to improve your cybersecurity posture with the cutting-edge research and analysis from the Qualys Threat Research Unit (TRU).
Read the next blog in this series: Misconfigurations Still Prevalent in Web Applications
Get the full 2023 Qualys TruRisk Research Report and learn about all five Risk Facts now.