Risk Fact #4: Misconfigurations Still Prevalent in Web Applications
Qualys Blog Series – Threat Research Unit Report
The Open Web Application Security Project (OWASP) Top 10 is a list of the most common and most critical vulnerabilities that can impact a web application. Security experts rely on the OWASP Top 10 when talking about web app security. The list helps developers prioritize and understand what to fix to make their applications more secure. Remarkably, while the Top 10’s vulnerabilities incur minor repositioning from year to year, most have maintained a persistent presence since the Top 10 was first published in 2003!
In the 2023 Qualys TruRisk Research Report, analysis by our Threat Research Unit (TRU) discovered Risk Fact #4: Misconfigurations still prevalent in web applications. Exposure creates tremendous risk, both for the personally identifiable information (PII) owners and for the organizations hosting it within insecure web applications.
Read the previous blog in this series: Initial Access Brokers Attack What Organizations Ignore
Misconfigured Web Apps Pose the Most Risk
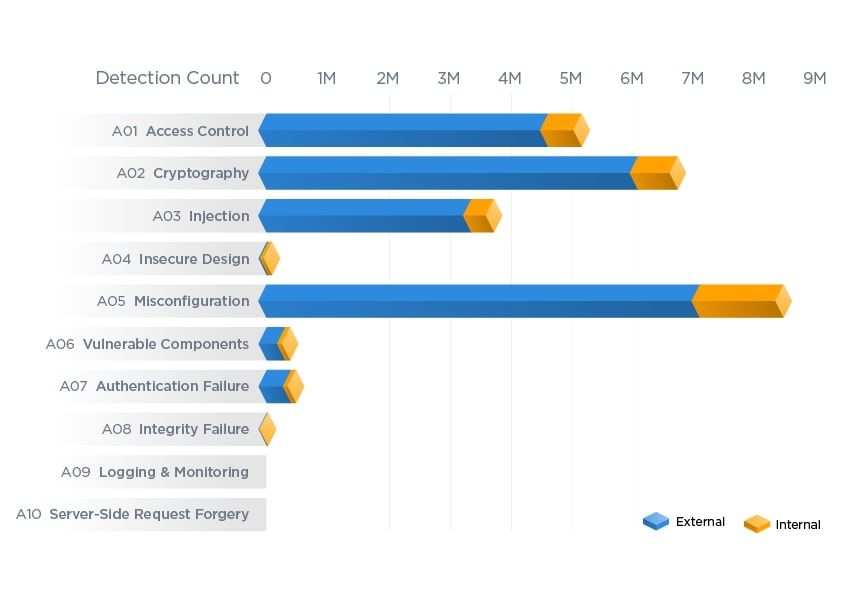
The TRU study included anonymous detections in 2022 from the Qualys Web Application Scanner, which globally scanned 370,000 web applications and correlated data against the OWASP Top 10. The scans revealed more than 25 million vulnerabilities, 33% of which were classified as OWASP Category A05: Misconfiguration. These misconfiguration vulnerabilities provided malicious actors with the capability to spread malware in about 24,000 web applications.
Misconfigurations largely entail improper controls used to protect web applications. Oftentimes this occurs when security best practices are not followed, such as not changing default permissions or passwords. Another type of misconfiguration can be applications that share too much information, such as detailed stack traces for errors. By not following security best practices, these web applications are vulnerable to a variety of attacks. For example, sophisticated attackers may use information disclosed in a verbose stack trace to identify web application technologies and mount a more advanced attack to breach a site. Even a simple error, such as not disabling directory listings, can trigger long-term issues if PII is inadvertently exposed through misconfigurations.
Other Top-detected Web App Vulnerabilities
The other top-detected categories are A02: Cryptographic Failures, A01: Broken Access Control, and A03: Injection. Cryptographic Failures can expose sensitive data by weak cryptographic controls (or worse, no cryptography). Misconfigurations enabling these attacks can cause session hijacking, stolen user credentials, and attacks against other data at rest or in transit.
Broken Access Control errors leverage violations of permission rights to gain access to web applications or resources. Examples include forced browsing to pages behind authentication or unauthorized privilege escalation for authenticated users. In some cases, access control is completely missing, such as the Optus data breach where malicious actors discovered an unprotected API endpoint that allowed access to over 10 million customer records.
Finally, the injection category is culprit to many common web application attacks, such as SQL and command injection attacks, Cross-Site Scripting (XSS), and Cross-Site Request Forgeries (CSRF). Many of these attack techniques have existed since the first web applications switched to dynamic content in the late 1990s. While mechanics of these attacks are still evolving, the bedrock error of improper or unsanitized user input has plagued web application security for decades.
Facing Web App Vulnerability Fallout
Once exploited, web applications themselves can become tools of malicious actors via web malware. A survey of Qualys Web Malware Detection scans identified nearly 65,000 instances of malware in the dataset of 200,000 external-facing web applications used by Qualys customers. For these, adversaries inserted custom source code to infect client browsers with the goal of skimming payment card information, stealing credentials, mining cryptocurrency, sending users to blacklisted sites, and other nefarious actions. These attacks brought reputational damage and downstream implications to the organization and website visitors.
The lesson for Risk Fact #4 is security and compliance stakeholders need to get serious about a very old, persistent problem: insecure web apps. Check out more details for Risk Fact #4 and all of our study’s insights by downloading and reading the 2023 Qualys TruRisk Research Report.
Unlock Unparalleled TruRisk Insights
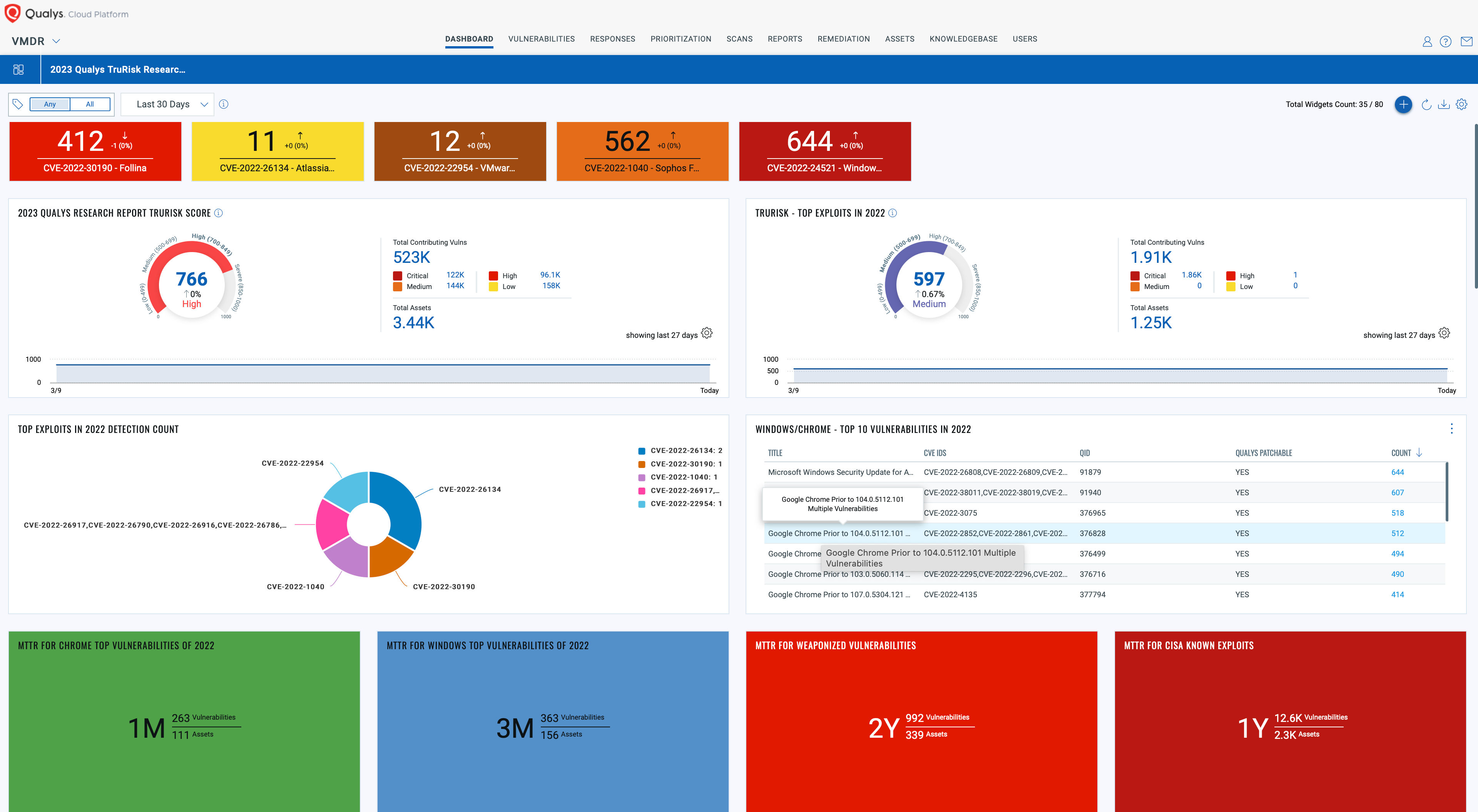
Download and import the Qualys 2023 TruRisk Research Report into your Qualys VMDR subscription today!
This comprehensive dashboard sheds light on your organization’s exposure to risks highlighted in the report, empowering you to make informed decisions and bolster your defenses. Don’t miss out on the opportunity to improve your cybersecurity posture with the cutting-edge research and analysis from the Qualys Threat Research Unit (TRU).
Read the next blog in this series: Infrastructure Misconfigurations Open the Door to Ransomware
Get full 2023 Qualys TruRisk Research Report and learn about all five Risk Facts now.