Part 2: An In-Depth Look at the Latest Vulnerability Threat Landscape (Attackers’ Edition)
Table of Contents
- Top Ten Vulnerabilities Exploited by Threat Actors
- Top Ten Highly Active Threat Actors
- Top Ten Most Exploited Vulnerabilities by Malware
- Top Ten Most Active Malware
- Top Ten Vulnerabilities Exploited by Ransomware
- Prioritizing Exploited Vulnerabilities with TheQualys VMDR and TruRisk
- Assess Your Organizations Exposure to Risk / TruRisk Dashboard
- Key Insights & Takeaways
- References
- Additional Contributor
The previous blog from this three-part series showcased an overview of the vulnerability threat landscape. To summarize quickly, it illustrated the popular methods of exploiting vulnerabilities and the tactical techniques employed by threat actors, malware, and ransomware groups. Perhaps more crucially, we stated that commonly used solutions (CISA KEV/EPSS) often fall short in identifying high-risk vulnerabilities.
In this blog, we will focus on an insider’s perspective on the threat landscape, viewing it through the eyes of an attacker. We will examine how quickly vulnerabilities get exploited in the wild, identify popularly sought-after vulnerabilities by threat actors, malware, and ransomware groups, and explore their underlying motives.
We will also provide insights on what measures to take you can take to safeguard your organizations from these vulnerabilities.
So, let’s dive headfirst into this intriguing world without further ado.
How Fast Are Vulnerabilities Getting Exploited (Time to CISA KEV)?
We’ve already highlighted one of the most noteworthy efforts by the team at CISA – the creation of the known exploited vulnerabilities catalog in our previous blog. Initiated as part of Binding Operational Directive 22-01 in 2021, this project was born out of the need to minimize risks associated with these vulnerabilities. In its early years, there was a substantial backlog to address. Still, by 2023, the CISA team has had their operation running like a well-oiled machine and is swiftly updating the catalog with newly exploited vulnerabilities as soon as evidence emerges.
So, let’s dive deep into understanding how quickly the vulnerabilities get exploited in the wild, as disclosed by the National Vulnerability Database(NVD).
The following graph illustrates the average duration it takes to include a vulnerability in the Known Exploited Vulnerabilities (KEV) catalog from when it was published in NVD.
For those CVEs disclosed in 2023, the gap to time to KEV was just eight days.
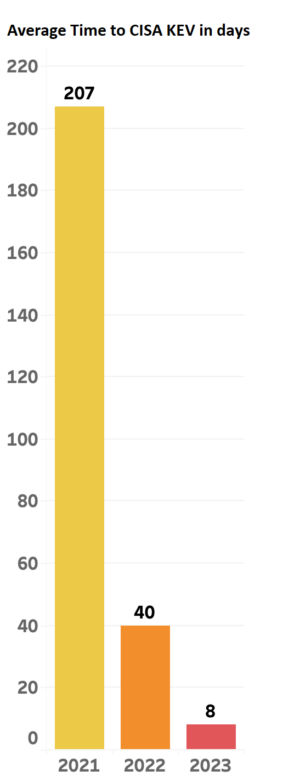
Defenders, therefore, have limited time to respond to vulnerabilities. The only viable response is through automation to patch these vulnerabilities before attackers can exploit them. Note that the average timeframe mentioned here, as in some instances, vulnerabilities are exploited almost instantly.
Which Vulnerabilities Are Exploited and by Whom?
So which vulnerabilities are exploited in the wild? And who is exploiting them? Are there any specific vulnerabilities that are more sought-after than others? If so, which ones?
To understand these questions, let’s examine three main groups of attackers.
- Threat Actor groups
- Malwares
- Ransomware groups
Although there is some overlap within each group, it appears to favor a slightly different set of vulnerabilities depending on the use case.
Top Ten Vulnerabilities Exploited by Threat Actors
Here’s a list of the top ten vulnerabilities exploited by threat actors.
The chart below shows the number of threat actors known to exploit a given vulnerability.
| Title | CVEs | Threat Actor Count | TruRisk Score (QVS) | Description |
|---|---|---|---|---|
| Microsoft Office/WordPad Remote Code Execution Vulnerability | CVE-2017-0199 | 53 | 100 | Allows a malicious actor to download Visual Basic script containing PowerShell commands. Works reliably well across a wide attack surface. Popular with APT Groups. |
| Microsoft Office Equation Editor Remote Code Execution Vulnerability | CVE-2017-11882 | 52 | 100 | Exploits Office’s default Equation Editor feature by tricking the user to open a malicious file. This one is the hacking group’s most favorite vulnerability, especially groups such as Cobalt or other malware as you will see in the next section. |
| Windows Common Controls Remote Code Execution Vulnerability | CVE-2012-0158 | 45 | 100 | Executes remote code by tricking the user to click on a malicious link or specially crafted malicious file. |
| Apache Log4j RCE (Log4Shell) | CVE-2021-44228 | 26 | 100 | Log4Shell. Do we need to say anything more? |
| Microsoft Office Memory Corruption Vulnerability | CVE-2018-0802 | 24 | 100 | Executes remote code by tricking the user to open a specially crafted malicious file in Office or WordPad. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyLogon) | CVE-2021-26855 | 22 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server in its default configuration. Heavily exploited by the Hafnium group among others. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-34473 | 20 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server. Can be clubbed with other CVE’s CVE-2021-34523 and CVE-2021-31207 making it more attractive to cybercriminals. |
| Arbitrary file write vulnerability in Exchange | CVE-2021-27065 | 19 | 95 | Requires authentication that can then write arbitrary file write vulnerability in Exchange. Leveraged as part of the attack chain once an attacker has initial access. Exploited by Hafnium group among others. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-34523 | 17 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server. Can be chained with other CVE’s CVE-2021-34473 and CVE-2021-31207 making it more attractive to cybercriminals. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-31207 | 17 | 95 | Allows an unauthenticated user to run arbitrary commands on the exchange server. Can be chained with other CVE’s CVE-2021-34473 and CVE-2021-31207 making it more attractive to cybercriminals. |
Table 1. Top 10 Vulnerabilities Exploited by Threat Actors for High-Risk Vulnerabilities
Top Ten Highly Active Threat Actors
Next, let’s talk about some of the most active threat actors known to leverage the maximum number of vulnerabilities as part of their arsenal capable of compromising systems across the globe.
| Threat Actor | CVEs Exploited | Description |
|---|---|---|
| Equation Group | 51 | Uses a variety of malware, including backdoors, trojans, and rootkits, often targeting zero-day vulnerabilities. Such kinds of malware are often challenging to detect and remove. |
| Fancy Bear | 44 | Best known as APT28 or Sofacy, it uses advanced malware and spear-phishing tactics. The group is also known for using “watering hole” attacks. In 2016, APT28 reportedly attempted to interfere with the U.S. presidential elections. |
| Wicked Panda | 30 | Also known by Axiom, Winnti, APT41, or Bronze Atlas. This group conducts financially motivated operations. It’s been observed to target healthcare, telecom, technology, and video game industries in 14 countries. |
| Ricochet Chollima | 26 | Also known as APT37, Reaper, and ScarCruft, they primarily target financial institutions, academics, and journalists. |
| Labyrinth Chollima | 24 | This is a sub-group of the Lazarus Group that has been attributed to the Reconnaissance General Bureau. It was reportedly responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment as part of a known campaign called The Operation Blockbuster campaign by Novetta. |
| Stardust Chollima | 22 | Also known as BlueNoroff, it is a sub-group of the Lazarus Group and has been attributed to the Reconnaissance General Bureau, target banks, financial institutions, casinos, cryptocurrency exchanges, SWIFT system endpoints, and ATMs in at least 38 countries worldwide. |
| Carbon Spider | 22 | Also known as Carbanak, FIN7, and Anunak, this threat actor is a financially motivated threat group that targets the U.S. retail, restaurant, and hospitality sectors, often using point-of-sale malware. |
| Cozy Bear | 20 | Also known as APT29, often targets government networks in Europe and NATO member countries, research institutes, and think tanks. |
| APT37 | 20 | It is also linked to the following campaigns between 2016-2018: Operation Daybreak, Operation Erebus, Golden Time, Evil New Year, Are You Happy? FreeMilk, North Korean Human Rights, and Evil New Year 2018. |
Table 2. Most Active Threat Actors for High-Risk Vulnerabilities
Top Ten Most Exploited Vulnerabilities by Malware
Now, let’s check some of the commonly exploited vulnerabilities by malware.
| Title | CVEs | Malware Count | TruRisk Score (QVS) | Description |
|---|---|---|---|---|
| Microsoft Office Equation Editor Remote Code Execution Vulnerability | CVE-2017-11882 | 467 | 100 | The absolute granddaddy of all CVEs most exploited by malware. In the history of CVEs, this would be the most beloved malware CVE of all time. |
| Microsoft Office/WordPad Remote Code Execution Vulnerability | CVE-2017-0199 | 92 | 100 | Allows a malicious actor to download Visual Basic script containing PowerShell commands. Works reliably well across a wide attack surface. Popular with APT Groups. |
| Java Applet Field Bytecode Verifier Cache RCE | CVE-2012-1723 | 91 | 100 | Exploits the vulnerability in JRE to download and install files of an attacker’s choice onto the system. |
| Microsoft Office Remote Code Execution Vulnerability | CVE-2017-8570 | 52 | 100 | Executes remote code by tricking the user to open a malicious RTF file. Bypasses the patch from CVE-2017-0199. Known to be used in malware spam campaigns. |
| Windows Graphics Device Interface (GDI) RCE | CVE-2019-0903 | 30 | 93 | Exploits vulnerability in the Graphics Component which is fundamental part of the Windows OS used for rendering graphics. |
| Microsoft Office Memory Corruption Vulnerability | CVE-2018-0802 | 29 | 100 | Exploits a vulnerability that was not patched by CVE-2017-11882. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyLogon) | CVE-2021-26855 | 19 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server in its default configuration. Heavily exploited by Hafnium group among others. |
| Microsoft Windows Netlogon Privilege Escalation (ZeroLogon) | CVE-2020-1472 | 17 | 100 | Allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. Lets the attacker instantly become an admin on enterprise networks. |
| Microsoft Windows CryptoAPI Spoofing Vulnerability | CVE-2020-0601 | 17 | 95 | Enables attackers to execute spoofing attacks, masquerading malicious programs as legitimate software, apparently authenticated with a genuine digital signature. This essentially allows for the delivery of malware under the guise of legitimate software. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-34473 | 12 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server. It can be chained with other CVE’s CVE-2021-34523 and CVE-2021-31207 making it more attractive to cybercriminals. |
Table 3. Top Ten Vulnerabilities Exploited by Malware for High-Risk Vulnerabilities
Top Ten Most Active Malware
And here’s a list of the ten most common malware names that are known to exploit vulnerabilities that compromise systems.
| Malware | CVEs Count | Description |
|---|---|---|
| Heuristic | 117 | Heuristic viruses can refer to malware detected by heuristic analysis or the virus Heur. The Invader, which compromises a device’s security and antivirus measures. Some examples of heuristic viruses include adware and Trojans. |
| Wacatac | 94 | Also known as Trojan: Win32/Wacatac.B, is a trojan horse that is designed to steal personal information, such as passwords, credit card numbers, and other sensitive data. |
| Pidief | 73 | Pidief malware is a file infector, that can infect executable files, such as .exe files, it will modify the file to execute the Pidief malware. |
| Skeeyah | 52 | Skeeyah malware is a file infector that can infect executable files, such as .exe files. It will modify the file in a way that will execute the Skeeyah malware when the file is opened. |
| Bitrep | 49 | Trojan horse virus that infiltrates a computer via a vulnerability in Adobe Flash. Swifi is downloaded from a malicious website without user knowledge or consent and may cause performance degradation, and security malfunctions leading to unauthorized users gaining remote access |
| Meterpreter | 46 | Meterpreter is a malicious trojan-type program that allows cyber criminals to remotely control infected computers, without writing anything to disk. This malware can log keystrokes – recording keyboard input (keys pressed) to steal credentials (logins, passwords) linked with various accounts and personal information. |
| Swifi | 42 | Trojan horse virus that infiltrates a computer via a vulnerability in Adobe Flash. Swifi is downloaded from a malicious website without user knowledge or consent, and may cause performance degradation, and security malfunctions leading to unauthorized users gaining remote access |
| IFrame | 38 | The iframes are used to inject malicious content into a website and can be spread through malicious websites that contain iframes with malicious content. |
| Lotoor | 35 | It can infect Android devices, often spread through malicious apps available on third-party app stores. These apps may appear to be legitimate, but they actually contain the Lotoor malware. |
| Redirector | 34 | Redirects users to malicious websites without their knowledge or consent. This type of malware can be very dangerous, leading users to download other malicious software or enter personal information. |
Table 4. Most Active Malware for High-Risk Vulnerabilities
Top Ten Vulnerabilities Exploited by Ransomware
Lastly, let’s examine the vulnerabilities that ransomware tends to exploit. Ransomware is a particular type of malware that encrypts data on storage systems, rendering them inaccessible unless the victim pays a ransom, typically in Bitcoin. Since the notorious WannaCry crypto-ransomware incident in May 2017, the use of such malicious software has notably escalated.
The latest report on such escalating threat involves a data breach during a MOVEit transfer, for which the BlackCat ransomware gang claimed responsibility. This same group alleges to be behind the data theft attack on Reddit.
| Title | CVEs | Ransomware Count | TruRisk Score (QVS) | Description |
|---|---|---|---|---|
| Microsoft Office Equation Editor Remote Code Execution Vulnerability | CVE-2017-11882 | 14 | 100 | Allows an unauthenticated attacker to exploit the vulnerability in SMBv1 to completely compromise systems. It was used by the WannaCry crypto worm as part of a worldwide cyberattack. |
| Java AtomicReferenceArray deserialization RCE | CVE-2012-0507 | 42 | 100 | Exploits the vulnerability in JRE to download and install files of an attacker’s choice onto the system by tricking the user to visit a malicious link. Old CVE, but still relevant. |
| Java Applet Field Bytecode Verifier Cache RCE | CVE-2012-1723 | 13 | 100 | Exploits the vulnerability in JRE to download and install files of an attacker’s choice onto the system. |
| Windows SMB v1 Remote Code Execution (WannaCry) | CVE-2017-0145 | 13 | 100 | Allows an unauthenticated, remote attacker to read arbitrary files allowing the attacker to access private keys or user/password information, which is then used to gain further unauthorized access. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-34473 | 12 | 100 | Allows an unauthenticated user to run arbitrary commands on the exchange server. It Can be chained with other CVE’s CVE-2021-34523 and CVE-2021-31207 making it more attractive to cybercriminals. |
| Pulse Connect Secure SSL VPN Vulnerability | CVE-2019-11510 | 12 | 100 | Allows an unauthenticated attacker to exploit the vulnerability in SMBv1 that completely compromises systems. It was leveraged by the WannaCry crypto worm as part of a worldwide cyberattack. |
| Windows SMB v1 Remote Code Execution (WannaCry) | CVE-2017-0144 | 12 | 95 | Allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. It lets the attacker instantly become an admin on enterprise networks. |
| Microsoft Windows Netlogon Privilege Escalation (ZeroLogon) | CVE-2020-1472 | 11 | 93 | Allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. It lets the attacker instantly become an admin on enterprise networks. |
| Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyShell) | CVE-2021-34523 | 10 | 100 | Allows an unauthenticated attacker with network access to a domain controller to completely compromise all Active Directory identity services. It lets the attacker instantly become an admin on enterprise networks. |
| Citrix Application Delivery Controller/NetScaler RCE | CVE-2019-19781 | 10 | 100 | Allows an unauthenticated attacker to execute arbitrary code on the system. Was leveraged to drop NOTROBIN malware to maintain persistent access. |
Table 5. Top 10 Vulnerabilities Exploited by Ransomware for High-Risk Vulnerabilities
| Ransomware | CVEs Count | Description |
|---|---|---|
| Conti | 30 | “Conti” is a Ransomware-as-a-Service (RaaS) targeting corporations and agencies by stealing and threatening to publish their sensitive data unless a ransom is paid. It uses unique encryption keys for each file and victim and leverages the Windows Restart Manager to unlock files for encryption. |
| Cerber | 30 | This modular ransomware can spread through email attachments, exploit kits, and drive-by downloads. It encrypts files and demands a ransom payment in Bitcoin. |
| REvil | 25 | This modular ransomware can spread through email attachments, exploit kits, and drive-by downloads. It encrypts files and demands a ransom payment in Bitcoin. |
| Sodinokibi | 21 | A successor to REvil that is even more sophisticated. It can encrypt files on all types of devices, including servers, laptops, and mobile phones. |
| Lucky | 21 | This ransomware is known for its aggressive spam campaigns. It sends emails with malicious attachments that, when opened, infect the victim’s computer with ransomware. |
| GandCrab | 19 | This ransomware is known for its high ransom demands. It has targeted businesses in various industries, including healthcare, finance, and manufacturing. |
| Ryuk | 17 | This ransomware is known for its high ransom demands. It has targeted businesses in various industries, including healthcare, finance, and manufacturing. |
| Reveton | 16 | Known for its scareware tactics, this ransomware displays a fake warning message claiming the victim’s computer has been infected with malware. The message demands that the victim pay a ransom to remove the malware. |
| STOP | 15 | Ransomware operators are known to be aggressive and persistent, often threatening to release stolen data or to attack systems again if the ransom is not paid. |
| Satan | 15 | Satan ransomware can be very high, and there is no guarantee that victims will get their data back even if they pay the ransom. Used in attacks against high-profile organizations, healthcare, education, government, and businesses of all sizes. |
Table 6. Most Active Ransomware for High-Risk Vulnerabilities
Prioritizing Exploited Vulnerabilities with The Qualys VMDR and TruRisk
Oftentimes, malicious actors frequently target diverse sets of vulnerabilities to accomplish their objectives. As such, keeping track of who is exploiting what can be daunting, and it’s certainly not an efficient use of the time for practitioners or security & risk management leaders.
Hence, The Qualys VMDR with TruRisk facilitates this process, substantially simplifying the prioritization process by translating the risk associated with vulnerabilities, assets, and asset groups into an easily understandable score that both technical and non-technical teams can comprehend this scoring system.
When you carefully observe, each vulnerability mentioned above has a TruRisk Score (QVS) of over 90. TruRisk considers these factors daily, consistently assigning a score higher than 90.
So, from a prioritization standpoint, any issue with a score of 90 or above should be immediately prioritized and remedied.
Let’s take CVE-2017-11882 as an example. The TruRisk score clearly indicates why this is a high-risk vulnerability, with more than 400 malware and 50 threat actors exploiting it, and we see evidence of exploitation as recently as July 16th, 2023, for a 6-year-old vulnerability.
Fig 8. Microsoft Office Memory Corruption Vulnerability: CVE-2017-11882
Assess Your Organizations Exposure to Risk / TruRisk Dashboard
The Qualys VMDR helps organizations get instant visibility into high-risk vulnerabilities, especially those exploited in the wild.

Fig 9. Qualys VMDR TruRisk Dashboard for High-Risk Vulnerabilities
The fastest method to gain insights into your TruRisk is by downloading and importing the TruRisk Dashboard into your VMDR subscription.
The TruRisk VMDR Dashboard is available – Download the Dashboard Here
And once you have the visibility patch with Qualys Patch management instantly reduce the risk.
Get The Free Trial
Sign up for a Free Trial and See your TruRisk
Key Insights & Takeaways
- The time to Known Exploited Vulnerability (KEV) is down to eight days for CVEs published in 2023. Defenders should leverage automation to patch high-risk vulnerabilities.
- CVE-2017-11882 stands out as the pinnacle among CVEs in its exploitation by malware, threat actors, and ransomware groups. With over 400 malware, 50 threat actors, and 14 ransomware groups taking advantage of this vulnerability, it will likely be remembered as the most cherished attacker CVE ever.
- Attackers prominently exploit vulnerabilities in popular applications such as Microsoft Office, Microsoft Exchange, Windows Operating systems, Java, Pulse Secure SSL VPN, and Citrix ADC/NetScaler. Attackers seek these applications primarily due to their widespread usage and potential for exploiting security weaknesses.
- Organizations should leverage threat intelligence to prioritize vulnerabilities that reduce the risk of exploitation.
- The Qualys VMDR with TruRisk automatically prioritizes vulnerabilities exploited in the wild with a TruRisk score of 90 or higher, greatly simplifying the prioritization process.
Concluding this series in the next blog we will discuss the 15 most exploited vulnerabilities ever.
Watch out for our next blog.
References
- https://blog.qualys.com/product-tech/2023/07/11/an-in-depth-look-at-the-latest-vulnerability-threat-landscape-part-1
- https://blog.qualys.com/qualys-insights/2022/10/10/in-depth-look-into-data-driven-science-behind-qualys-trurisk
- https://blog.qualys.com/vulnerabilities-threat-research/2022/12/16/implement-risk-based-vulnerability-management-with-qualys-trurisk-part-2
- https://blog.qualys.com/qualys-insights/2022/08/08/a-deep-dive-into-vmdr-2-0-with-qualys-trurisk
Additional Contributor
Shreya Salvi, Data Scientist, Qualys






