GDPR Is Here: Indication of Compromise – Another Key Practice for GDPR Compliance
In this blog series, we’re discussing solid security practices that are key for General Data Protection Regulation (GDPR) compliance, and today we’ll address another crucial one: Indication of compromise (IOC).
In a nutshell, IOC can help customers who are dealing with unauthorized access to customer personal data by an external threat actor or adversary.
This makes IOC particularly relevant to GDPR’s stringent requirements for providing integrity, control, accountability and protection of EU residents’ personal data.
Read on to learn why IOC is critical for complying with GDPR, which went into effect in May, and how Qualys can help you.

Qualys IOC and GDPR
Privacy and data breaches are increasingly caused by external threat actors or adversaries seeking financial gain.
Qualys IOC can help organizations by empowering security analysts to more quickly detect, investigate, research, and remediate external threats against computing systems that contain customer personal data, as well as the organization’s own sensitive data. This includes identifying modern non-malware and fileless attacks that are more easily able to bypass traditional endpoint prevention security technologies.
More specifically, Qualys IOC can help with two specific GDPR requirements:
- the ability of the organization to protect personal data
- complying with breach notification rules, for which the organization must know the extent of the breach in order to alert affected parties
GDPR doesn’t change how mature and lean-forward organizations have been implementing detection and response technology like Qualys IOC. However, it does change how those organizations that haven’t deployed such a technology need to implement it in a way that’s scalable, easy-to-use, cost effective, and non-impactful on their endpoint systems.
Qualys IOC: Cloud based, scalable, precise, versatile and intuitive
Let’s look more in detail at Qualys IOC.
Qualys IOC integrates endpoint detection, behavioral malware analysis, and pre-defined threat hunting techniques that incorporate a continuous view of an asset’s vulnerability posture along with suspicious activity monitoring.
With Qualys IOC, security analysts and incident responders can correlate endpoint activity with threat intelligence, network alerts, and sandbox analysis to quickly determine exactly when and where a compromise took place.
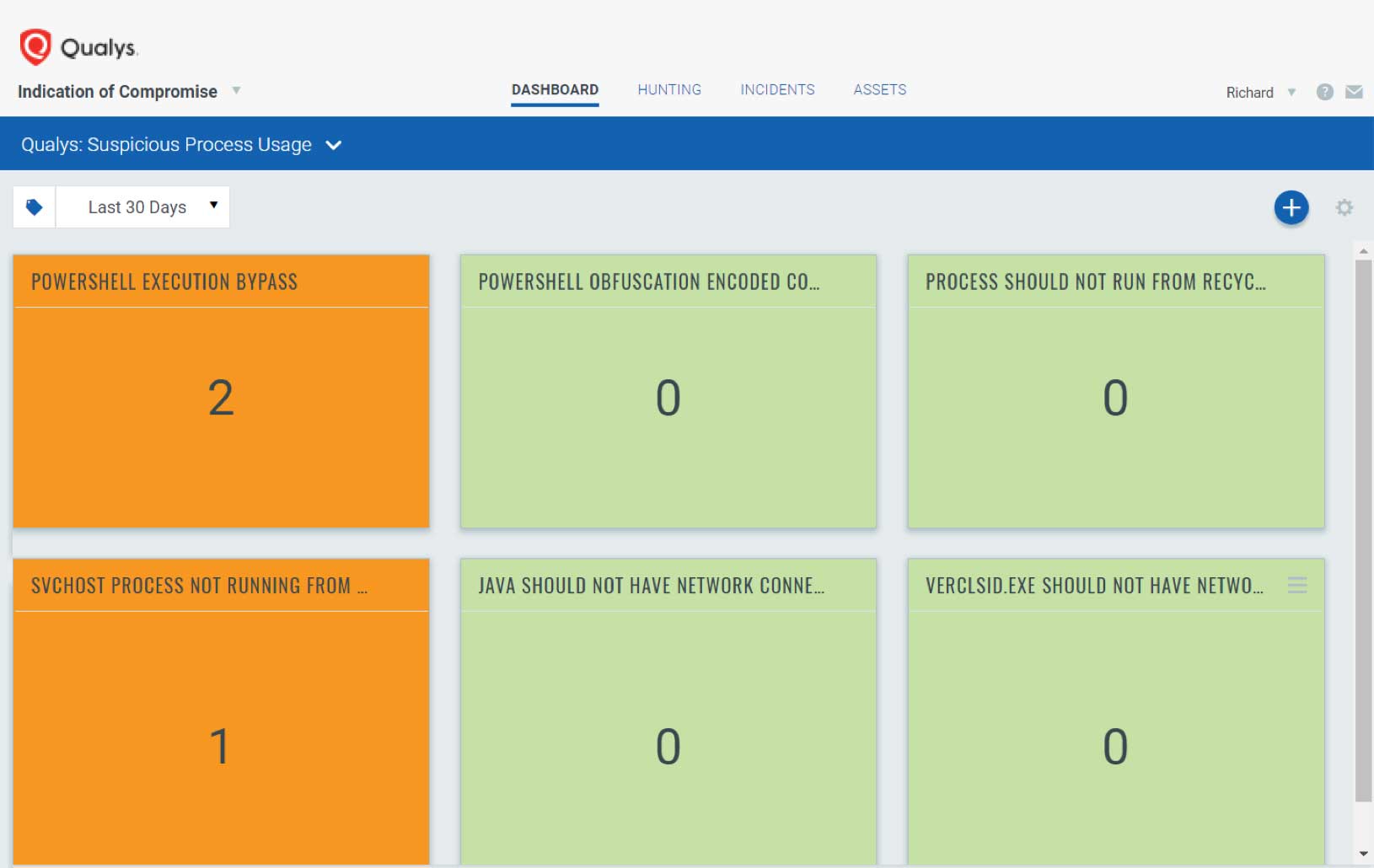
Key Qualys IOC benefits include:
- Unified agent event collection: Qualys IOC uses the Qualys Cloud Agent’s non-intrusive data collection and delta processing techniques to transparently capture endpoint activity information from assets on and off the network in a way that is more performant than query-based approaches or log collectors. This is the same agent used by other Qualys Cloud Apps, including Qualys Vulnerability Management and Qualys Policy Compliance, so there’s no need to deploy, configure and maintain an additional agent for Qualys IOC.
- Highly scalable detection processing: Threat hunting, suspicious activity detection, and OpenIOC processing is performed in the Qualys Cloud Platform on billions of active and past system events, and is coupled with threat intelligence data from Qualys Malware Labs to identify malware infections (indicators of compromise) and threat actor actions (indicators of activity).
- Actionable intelligence for security analysts: Customers can use pre-defined threat hunting rules and easily import indicators of compromise artifacts into widgets, dashboards, and saved searches to quickly verify threat intelligence, scale of infections, first-infected asset (“Patient Zero”), and timeline of compromises — even for assets that are currently offline or have been re-imaged by IT.
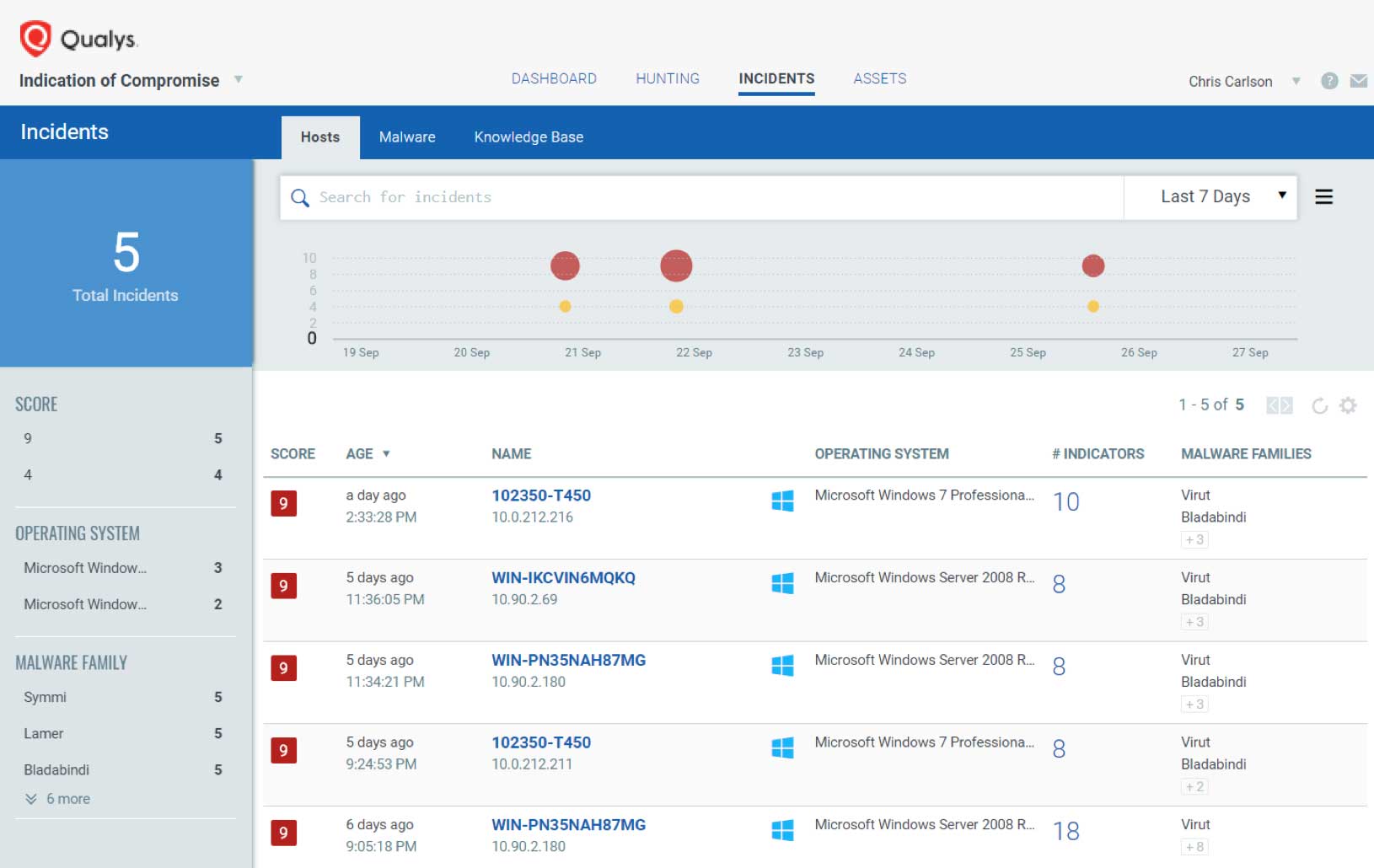
- Streamlined investigations with a Single View of Asset: Qualys IOC creates a Single View of the Asset, showing threat hunting details unified with other Qualys Cloud Apps for hardware and software inventory, vulnerability posture, policy compliance controls, and file integrity monitoring change alerts for on-premises servers, cloud instances, and off-net remote endpoints. A single user interface significantly reduces the time required for incident responders and security analysts to hunt, investigate, detect, and respond to threats before a breach or compromise can occur.
In short, when an endpoint is infected and a breach happens, Qualys IoC helps you detect it faster, ideally before any damage is done and any information is stolen.
For your organization’s overall security posture, and for GDPR compliance specifically, It’s critical to prevent intruders from prowling around inside your network undetected for months.
In our next post in this blog series, we’ll look into the importance of web application security within the realm of your GDPR readiness efforts.
(Chris Carlson is a Vice President, Product Management at Qualys)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
GDPR Is Here: Assess Risk from Vendors and from Internal Teams
GDPR Is Here: Assess the Security Configurations of Your IT Systems