Recline on the Qualys Couch: Examining Patching Behavior
Last updated on: September 6, 2020
In a perfect world, organizations would patch vulnerabilities immediately after they’re disclosed, preemptively blocking exploits and dodging most cyber attacks.
Of course, reality is far from that hypothetically ideal state. Organizations often leave critical vulnerabilities unpatched for months, even years. Hackers routinely feast on all that low-hanging fruit to hijack systems, steal data, deface websites and disrupt operations.
We all know it’s impossible to patch every single vulnerability. Thousands are disclosed every year, and patching systems can be complicated, time-consuming and inconvenient. But InfoSec teams agree that fixing the most dangerous bugs on a timely basis is not only doable but also necessary.
The problem is that prioritizing remediation and pinpointing those critical vulnerabilities is difficult when — as is often the case — organizations lack continuous and automated vulnerability management, asset inventorying and threat analysis.
Unsurprisingly, recent Qualys data on patching behavior shows that remediation activity is directly related to the level of risk attached to specific vulnerabilities. And in some cases, specifically when it comes to the realm of IoT devices, patching is always slow, and often non-existent.
What WannaCry taught us
As featured in Cisco’s 2018 Annual Cybersecurity Report, published last week, Qualys’ data on patch management behavior before and after the WannaCry campaign is very illuminating.
The WannaCry ransomware, which infected 300,000-plus systems and disrupted critical operations globally in May, spread using the EternalBlue exploit for a Windows vulnerability (MS17-010) Microsoft had patched in March.
Qualys data shows that between mid-March, when the vulnerability in the Windows SMB Server is disclosed, and mid-April, detection of affected devices spikes and gradually declines “as organizations scan their systems and apply the patch,” the report reads.
However, the number of vulnerable systems shoots up after April 14, when the ShadowBrokers hacker group released the EternalBlue exploit. In fact, the number of impacted devices detected with the vulnerability nearly doubled in the ensuing days.
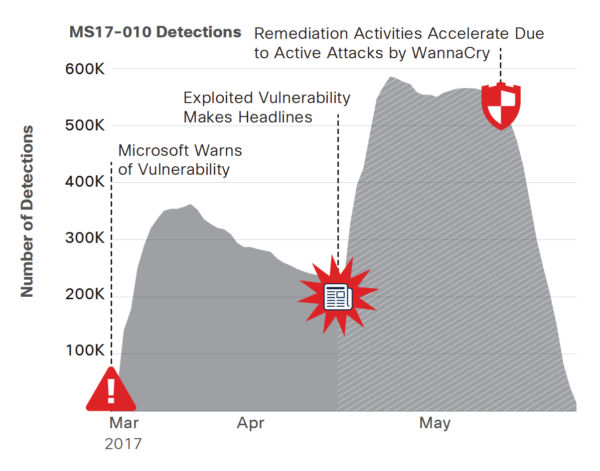
“That happened as organizations learned of the exploit and its potential to impact both supported and unsupported versions of Windows through a remote check from Qualys that used a portion of the exploit code,” the report reads.
However, widespread patching didn’t fully kick in until after the WannaCry attacks began in mid-May.
“Qualys’ research into its customers’ patching behavior indicates that it takes a major event to motivate many organizations to patch critical vulnerabilities — even knowledge of an active exploit is not enough to accelerate remediation,” the report reads.
With a patch available since mid-March — two months before the ransomware attacks — organizations had plenty of time to fix their affected systems. Had a majority of organizations done so, WannaCry would have been a minor event, instead of the global cyber disaster that it turned into.
IoT unpatched
Qualys also looked at patching trends for IoT devices, and the findings were alarming.
Qualys sampled HVAC systems, door locks, fire alarm panels, card readers and other IoT devices vulnerable to several known threats, and found that only 17% of the devices had been patched, a staggeringly low number.
Among the possible reasons for the dismal percentage of patched systems are:
- Some devices may be impossible to update.
- Patching other devices may require direct involvement from their vendor.
- The organization may not know who is accountable for remediating IoT devices.
Also of concern is the low visibility of IoT devices, caused by organizations’ ignorance about their presence in the network. “That lack of visibility puts them at serious risk of compromise,” reads the report.
To address this visibility issue, organizations must first inventory all IoT devices on the network, and then assess which ones can be scanned and patched, and which employees use them.
Hackers are upping their game
The need for foundational InfoSec practices, such as comprehensive IT asset visibility, continuous vulnerability management, precise threat prioritization, and automated patch management, has never been higher.
As the 68-page Cisco report explains in detail, the bad guys — malicious hackers, data thieves, hostile nation states — are getting more aggressive, more effective, and more sophisticated.
Based on research and insights from researchers from Cisco and its partners, including Qualys, the report centers around three main findings:
- Malware creation is reaching levels of sophistication and impact never before seen, as evidenced by developments such as network-based ransomware cryptoworms
- Hackers have made major strides in making their attacks more stealthy and evasive, making them significantly harder to block and detect
- Hackers are making hay of the sorry state of IoT and cloud security, taking advantage of millions of vulnerable and improperly configured systems
(Jimmy Graham is a Director of Product Management at Qualys)
Download the complete Cisco 2018 Annual Cybersecurity Report