Implementing the CIS 20 Critical Security Controls: Make Your InfoSec Foundation Rock Solid
For almost 10 years, thousands of organizations eager to solidify their security and compliance foundations have found clarity and direction in the the Center for Internet Security’s Critical Security Controls (CSCs).
This structured set of 20 foundational InfoSec best practices, first published in 2008, offers a methodical and prioritized approach for securing your IT environment. Mapping effectively to most security control frameworks, government regulations, contractual obligations and industry mandates, the CSCs can cut an organization’s risk of cyber attacks by over 90%, according to the CIS.
These battle-tested controls, described in a free document that has been downloaded more than 70,000 times, were developed and are maintained by a global team of expert volunteers from all cybersecurity sectors, including government, industry and academia.
A detailed plan that can help you boost your security and compliance posture is more relevant than ever, now that attacks are getting more sophisticated and aggressive, and that throwing money at the problem hasn’t proven to be the solution.
In the SANS Institute paper “Leading Effective Cybersecurity with the Critical Security Controls”, author Wes Whitteker noted that while investments in cybersecurity have boomed in recent years, so have the number of major data breaches.
According to Whitteker, the global cybersecurity problem is being met with ineffective responses due to organizations’ lack of a solid cybersecurity foundation.
“If the functions that set an organization’s cybersecurity foundation are flawed, it is very likely that the solutions they choose will be flawed, too,” he writes. “The CSCs offer a framework that provides the critical visibility needed to aid in strategy development and manage existing organizational environments.”
In this blog series, we’ve explained how Qualys Cloud Platform — a single, integrated, end-to-end platform for discovery, prevention, detection, and response — and its Qualys Cloud Apps can help security teams of any size to broadly and comprehensively adopt the CIS controls.
We first discussed how Qualys can help organizations slash risk of cyber attacks by 85% with the first five controls. In our second post, we explained the benefits of building upon that “foundational cyber hygiene” with controls six through 10. And last week we delved into more sophisticated techniques with controls 11 through 15.
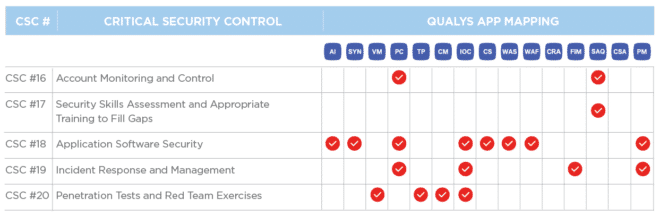
In this, our fourth and last installment, we’ll discuss controls 16 through 20.
CSC 16
Account Monitoring and Control
Actively manage the lifecycle of system and application accounts — their creation, use, dormancy, deletion — in order to minimize opportunities for attackers to leverage them.
Managing accounts is critical for protecting organizations’ data. Inadequate password rotation, accounts that have gained privileges as users change roles, and validation of account and privilege revocation are all critical user-account management tasks.
How Qualys Can Help
Qualys PC provides out-of-the-box content to validate the lifecycle of system/user accounts, their credentials, and privileges. PC can help organizations implement strong account controls by validating that the OS’s capabilities for account management, credential requirements, privileges, and other settings are in line with their password policy, auditor requirements, and industry best practices.
QUALYS SECURITY ASSESSMENT QUESTIONNAIRE (SAQ)
Qualys SAQ provides a shared assessment questionnaire template out-of-the-box, to assess the responses from internal and external parties regarding vendor access and monitoring, best practices for account management workflows, and monitoring that the organization’s resources are in place.
CSC 17
Security Skills Assessment and Appropriate Training to Fill Gaps
For all functional roles in the organization (prioritizing those mission-critical to the business and its security), identify the specific knowledge, skills, and abilities needed to support defense of the enterprise; develop and execute an integrated plan to assess, identify gaps, and remediate through policy, organizational planning, training, and awareness programs.
This control addresses the very important element of human behavior and its impact on security. Ensuring that individuals know what is expected of them as they participate in system design, implementation, operation, use, and oversight is critical to good information security practices.
How Qualys Can Help
QUALYS SECURITY ASSESSMENT QUESTIONNAIRE (SAQ)
Qualys SAQ supports a shared assessment template to assess the knowledge levels of internal and external parties on security training and awareness programs by consolidating their responses, allowing the organization to report on the programs.
CSC 18
Application Software Security
Manage the security lifecycle of all in-house developed and acquired software in order to prevent, detect, and correct security weaknesses.
Attacks often exploit vulnerabilities found in web-based and other application software. Vulnerabilities can be present for many reasons, including coding mistakes, logic errors, incomplete requirements, and failure to test for unusual or unexpected conditions. Attackers are attuned to the constant stream of vulnerability disclosures, because, when left unpatched, each represents an opportunity to breach a system by injecting specific exploits.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM can identify known vulnerabilities in application software such as databases, web servers, and middleware in the same way that it does for OS vulnerabilities. Multiple signatures exist to identify weak encryption configuration for legacy protocols, along with signatures to identify applications no longer supported by the vendor (EOL).
Qualys AI provides complete visibility and the ability to group software installations across the entire IT environment, so that organizations can plan and prioritize their efforts to secure applications.
Qualys PC provides controls to assess default configurations and security settings as per the best practices to prevent from the exploitable exposures. It provides recommended configurations including default credentials setup for many widely used applications.
QUALYS INDICATION OF COMPROMISE (IOC)
Qualys IOC provides the ability to continuously monitor applications and their hosting OS in order to detect suspicious activity, flagging telemetry data that could indicate malicious activity in the application.
BETA – QUALYS CONTAINER SECURITY (CS)
Qualys CS lets organizations discover, track, and protect containers in DevOps pipelines and deployments across cloud and on-premises environments, through continuous vulnerability assessments of Docker images and underlying hosts.
QUALYS WEB APPLICATION SCANNING (WAS)
Qualys WAS can insert security into application development and deployment in DevSecOps environments. With WAS and its API capability, you can automate scans as part of the build process to detect security flaws early and often, and automatically deliver detailed reports for review and remediation. With its flexible scheduling features and tight integration with Qualys WAF, WAS can continuously monitor and virtually patch vulnerabilities in production web apps.
UPCOMING – QUALYS PATCH MANAGEMENT (PM)
Qualys PM will allow organizations to assess the hosts and common applications against the latest patch levels, and update vulnerable libraries and database applications to ensure they are protected against exploitation in a secure, restricted way, allowing deployment of the latest patches on the assets.
QUALYS WEB APPLICATION FIREWALL (WAF)
Qualys WAF terminates http/s traffic towards web applications, using virtual, full-proxy architectured appliances that communicate with the Qualys Cloud Platform. Thanks to a powerful DAG oriented logic programmed by tailored rulesets, WAF protects live apps against malicious transactions and load-balances legitimate server-side traffic.
CSC 19
Incident Response and Management
Protect the organization’s information, as well as its reputation, by developing and implementing an incident response infrastructure (e.g., plans, defined roles, training, communications, management oversight) for quickly discovering an attack and then effectively containing the damage, eradicating the attacker’s presence, and restoring the integrity of the network and systems.
Organizations must assume that at some point they will have to deal with an attack that successfully breaches their defenses. That’s why they need to have a plan in place to respond and manage such an incident. The plan should include details on procedures, reporting, data collection, management responsibility, legal protocols, and communications strategy.
How Qualys Can Help
QUALYS FILE INTEGRITY MONITORING (FIM)
Qualys FIM monitors and tracks changes to critical files, including important information about security settings, attributes, and the processes involved in the change. This data is critical to helping you detect and identify critical changes and possible security incidents, but can also be priceless when investigating a breach.
QUALYS INDICATION OF COMPROMISE (IOC)
Qualys IOC can continuously monitor assets to detect suspicious activity, flagging telemetry data that could indicate malicious activity on the hosts. In the future, Qualys IOC will auto remediate infected assets by killing the malicious processes.
UPCOMING – QUALYS PATCH MANAGEMENT (PM)
Qualys PM will allow organizations to quickly deploy the latest patches, which can speed up recovery and prevent repeat attacks during the incident response process.
CSC 20
Penetration Tests and Red Team Exercises
Test the overall strength of an organization’s defenses (the technology, the processes, and the people) by simulating the objectives and actions of an attacker.
To determine how effective your security strategies and practices really are you need to subject your defenses to stringent tests that mimic real-world attacks via penetration tests and red team exercises.
How Qualys Can Help
Qualys TP continuously correlates external threat information against your vulnerabilities and IT asset inventory, leveraging Qualys Cloud Platform’s robust back-end engine to automate this large-scale and intensive data analysis process. TP can also provide direct links to exploit code for discovered vulnerabilities, helping security teams perform thorough penetration testing.
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM is widely used by consultants and pen-testers to perform network mapping and identify vulnerabilities. It can be leveraged internally using your scanner and agent deployments. Qulays Consultant licenses and offline scanner capabilities can also be used in limited and special engagements.
Qualys PC provides control assessment data that can supplement vulnerability details allowing pen testers more information to dig deeper into an environment.
To learn more about how Qualys Cloud Platform can help you drastically reduce your organization’s cyber risk and enhance compliance, download the Qualys Guide to Automating CIS 20 Critical Security Controls.