Steps to TruRisk™ – 1: Shift to Priority-Driven Strategies
“If you know the enemy and know yourself, you need not fear the result of a hundred battles.” — Sun Tzu
Security and IT teams are drowning in alerts, scrambling to patch everything they can, yet breaches still happen. Not all vulnerabilities pose the same risk. While reducing totals may seem like progress, without clear priorities, security teams risk treating symptoms instead of addressing the root causes of risk to the business.
The cybersecurity landscape is seeing an unprecedented surge in vulnerabilities. As of early 2025, the National Vulnerability Database (NVD) documented over 280,000 vulnerabilities, with 33% classified as high to critical. In 2023 alone, 28,817 vulnerabilities were disclosed, surpassing the previous year’s total by more than 3,700. This trend continued into 2024, with a staggering 22,254 vulnerabilities reported by mid-year, marking a 30% increase over the same period in 2023. These numbers are a wake-up call: organizations must rethink their security strategies to zero in on what truly matters.
The chart below shows that over half of all published vulnerabilities are now rated as high-to-critical, reflecting a steady upward trend:
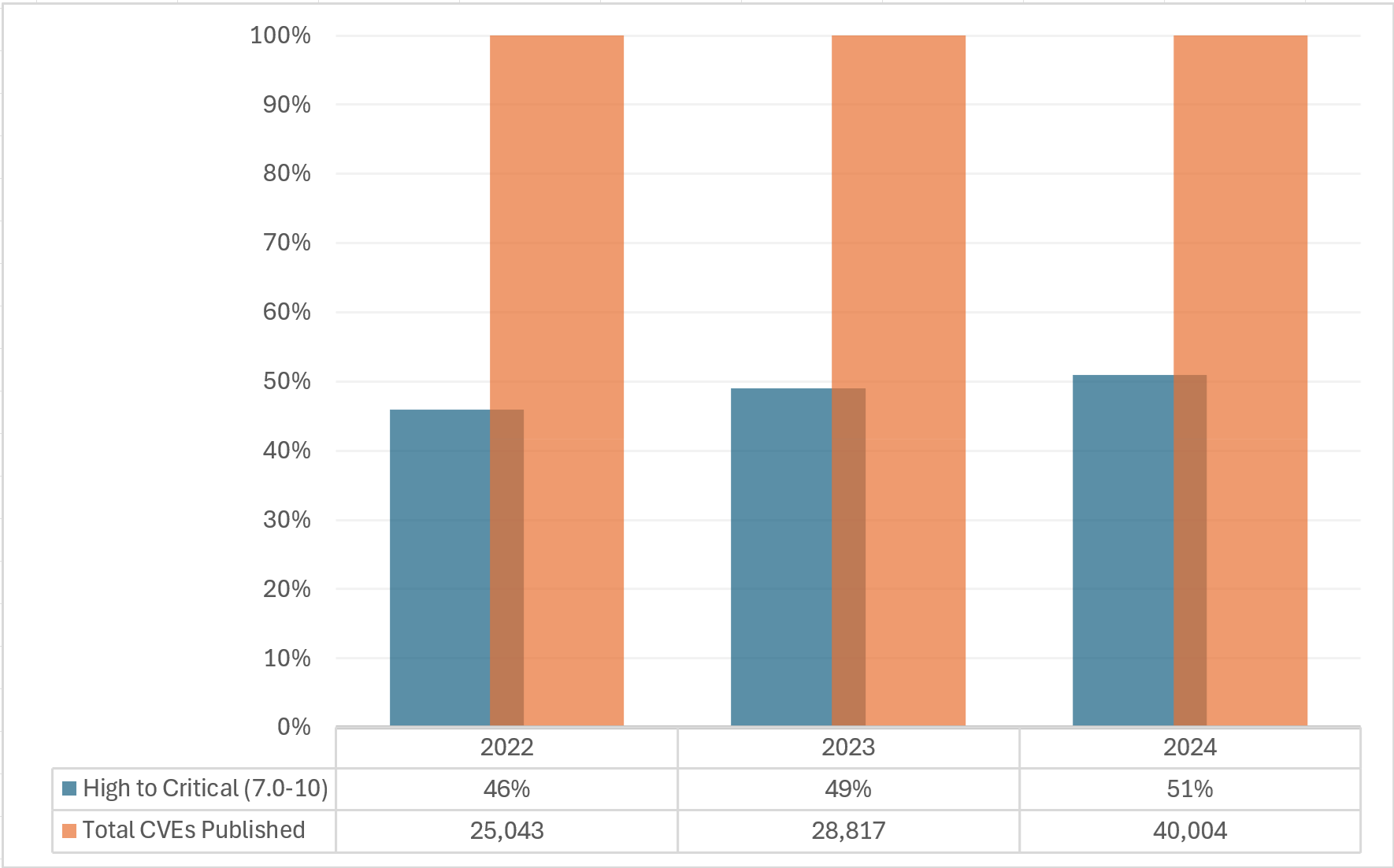
This is set to continue into 2025, putting further pressure on security teams.
Treating All Vulnerabilities Equally – The Hidden Costs
As we’ve learned recently, treating all assets and vulnerabilities equally leads to inefficiency and often overwhelms. True risk reduction isn’t about fixing more vulnerabilities; it’s about fixing the right ones. This requires a decisive shift in mindset and tactics toward risk-based prioritization, aligning security efforts closely with overarching business priorities.
A global financial institution learned this the hard way. Their one-size-fits-all approach, mandating patches across all systems equally, led to significant operational setbacks, unnecessary downtime, and exasperated teams. When maintenance windows opened, teams patched without strategic order, remediating critical transaction systems at the same pace as non-essential development environments. The result? Critical business operations suffered unnecessary downtime, while low-risk assets received equal attention as mission-critical systems. Instead of reducing risk, teams were overwhelmed, wasting valuable time and effort while key systems remained exposed longer than necessary.
This example highlights why targeted action is more effective than indiscriminate patching. The goal isn’t to fix everything, but to fix what matters most. Prioritization is the foundation of risk-based security and the essential first step in embarking on the TruRisk journey.
Qualys CEO Sumedh Thakar succinctly pointed out in a recent SC Magazine podcast that “simply reducing vulnerability counts is not enough to achieve meaningful risk reduction.” Organizations must quantify risk in business terms, bridging the gap between technical teams and decision-makers to drive accountability and strategic action.
To begin this process, organizations must answer two pivotal questions:
- What is your organization’s risk tolerance?
- Which assets are most critical, and what are the repercussions if they are compromised?
Developing a shared language for risk not only strengthens prioritization but also improves resource allocation, effectively breaking down silos between security and business leaders and paving the way for meaningful and measurable risk reduction. Security leaders play a critical role in this transformation.
As John C. Maxwell insightfully articulated, “A leader is one who knows the way, goes the way, and shows the way.” This means understanding the risks, taking proactive measures, and guiding teams toward a structured, impactful strategy.
At Qualys, we’ve seen firsthand how organizations achieve breakthroughs and transform security cultures by shifting to risk-based tactics and remediation. TruRisk provides the vehicle to drive measurable risk reduction and meet critical business objectives.
Efficiency and Consistency – A Unified Risk Approach
“If everyone is moving forward together, then success takes care of itself.” – Henry Ford
In any industry, chaos and inefficiency hinder progress. Early vehicle production lines were no exception, plagued by unpredictability, excessive costs, and slow output. At the time, building a car was an inconsistent and expensive process.
Drawing inspiration from steam engines, meatpacking plants, and watch factories, Ford and his team refined the moving assembly line, cutting production times from over 12 hours to just 90 minutes.
Ford didn’t just build cars; they revolutionized the entire process (and the world). Their success stemmed from meticulous planning, adaptation, precision tooling, and a culture of collaboration. Through relentless iteration, they distilled disorder into a structured system that reshaped manufacturing forever.
Before the assembly line, automobiles were a luxury only the wealthy could afford. Thanks to Ford’s vision and execution, vehicle ownership quickly became a staple of modern life. Ford’s assembly line proved that efficiency and consistency could turn innovation into a widespread impact. Cybersecurity must take the same approach, moving beyond reactive fixes to structured, repeatable strategies that prioritize what truly matters.
By embedding security into the fabric of business operations, organizations streamline their protection, safeguard critical assets, and cultivate resilience. Just as Ford’s vision redefined manufacturing, a risk-based approach transforms cybersecurity into a scalable, precision-driven system that keeps businesses secure in a chaotic threat landscape.
Strategy into Action – Shared Risk Language
Successful risk management strategies aren’t about fixing vulnerabilities but about protecting assets that drive business success. Achieving successful organizational alignment will require effective leadership, clear strategy, and confident execution.
The Risk = Likelihood x Impact, formula provides a solid foundation for clear strategy and a shared risk language. While originally rooted in general risk management, this formula has become essential across disciplines, including cybersecurity, where it drives organizational awareness and effective strategies.
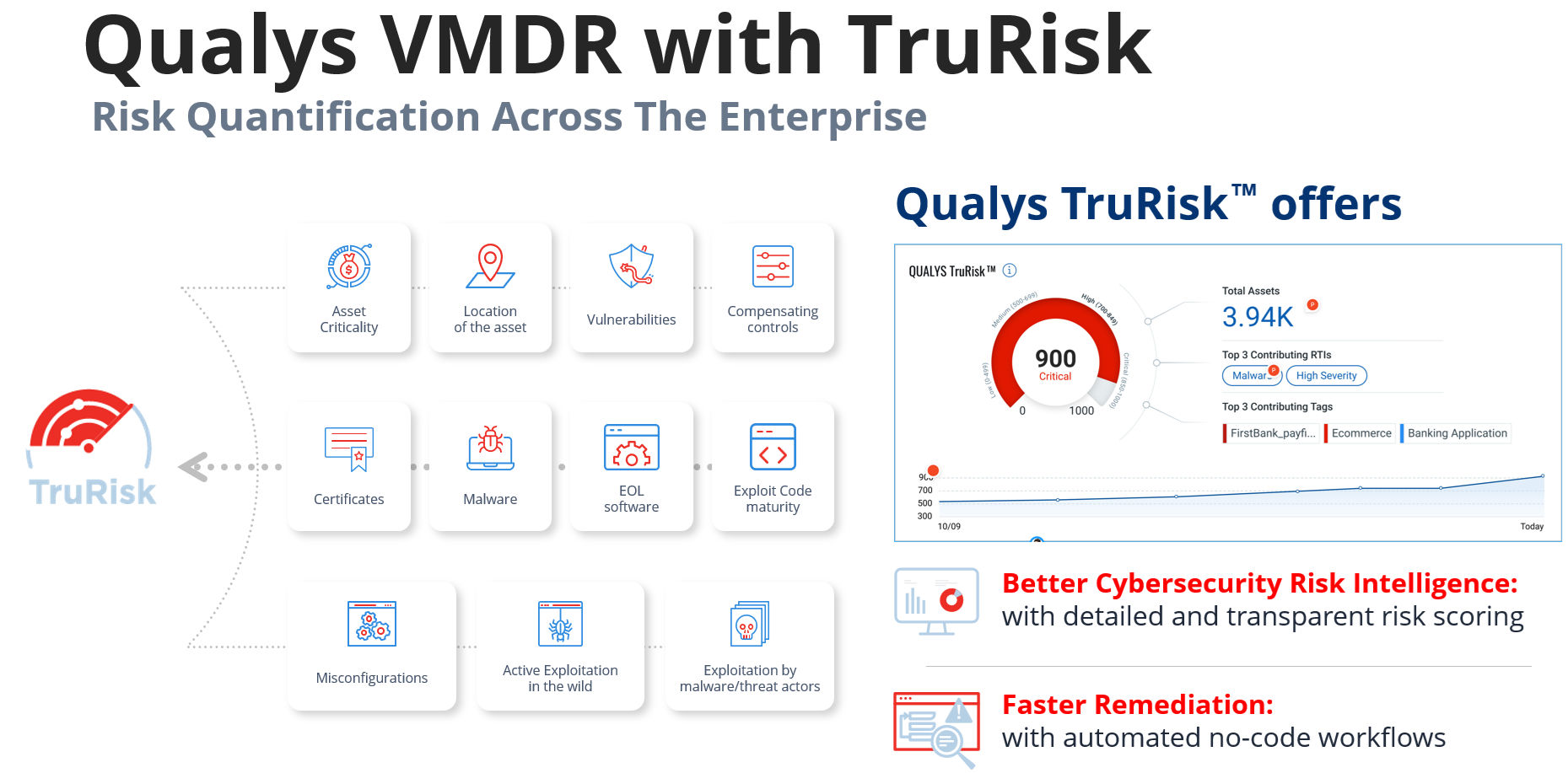
With TruRisk™ integrated into Qualys VMDR 2.0, this formula transforms into a measurable and actionable component:
Risk (TruRisk) = Likelihood (Qualys Detection Score) x Impact (Asset Criticality Score)
With a TruRisk™ view, you can quickly see asset details, criticality, and key risk factors. The interface shows the risk calculation with the full formula displayed, so you can see exactly how each asset’s score was determined.
Later in our series, we’ll demonstrate how you can tune your prioritization while driving down remediation times, all from the same pane of glass.
These tools and tactics empower organizations to:
- Quantify risk in business terms, transforming technical findings into guided strategic action.
- Enable teams to prioritize vulnerabilities with the highest potential impact.
By embedding this shared language into organizational processes and conversations, you plant the seeds for stronger alignment between cybersecurity and business objectives. With consistent nurturing through collaboration, strategy, and execution, this foundation not only grows stronger but flourishes. Resilience strengthens, and decision-making sharpens as technical and business growth takes root, creating a dynamic, robust, and thriving security ecosystem.
Organizational Alignment – From Vulnerability to Risk Reduction
When security teams and business leaders align on a shared approach to risk, the entire organization becomes more agile, focused, and resilient in facing modern threats. Targeting high-value assets and the most pressing threats streamlines risk management, ensuring even resource-limited teams can maximize impact and reduce risk effectively.
With a committed team, a shared vision, and the right tools in place, security leaders transform into trusted advisors who drive effective risk reduction and link security efforts with business priorities.
Aligning vulnerability management with business goals is the first step to achieving the TruRisk™ parameters. VMDR with TruRisk™ empowers organizations to confidently navigate threats, accelerate remediation, and safeguard critical operations.
Key Step 1 Takeaways
- Align risk management with business priorities: Foster strong leadership, collaboration, and clear communication to create synergy between security and business objectives.
- Leverage unified risk prioritization framework: Risk = Likelihood (Qualys Detection Score) x Impact (Asset Criticality Score) formula to guide decision-making and focus efforts on what truly matters.
No matter their starting point, Qualys empowers organizations to elevate their risk strategies with clarity and precision. The Qualys Enterprise TruRisk™ platform transforms risk reduction into a measurable, strategic advantage, ensuring security efforts are focused, efficient, and impactful. By embracing a risk-based approach, organizations don’t just react to threats; they proactively safeguard critical operations, adjust to shifting business needs, and drive continuous, measurable risk reduction. With TruRisk™, security becomes a business enabler, ensuring resilience in an ever-changing threat landscape.
What’s next?
Step 2 of this series, Take Inventory: Measuring Threats Accurately, will explore the importance of understanding your battlefield. The next step is all about moving beyond traditional scoring models and tapping into dynamic, real-time insights. We’ll discuss how Qualys Detection Score (QDS) integrates data from over 25 threat feeds while leveraging CVSS, CISA KEV, and EPSS to give you a more comprehensive and continuously updated picture of threat likelihood.
Stay tuned as we continue through Steps 2, 3, 4, and 5, offering actionable insights to help you turn knowledge into impactful action with Qualys TruRisk. Future blogs and webinars will go deeper into each principle, equipping you with practical tools to strengthen your organization’s cybersecurity resilience.
Do more with less—Thanks to Qualys TruRisk™!
You May Also Like:
“Steps to TruRisk™ – Insight to Action” blog
Contributor/s:
- Russ Sanderlin, VMDR Director and SME
- Saeed Abbasi, Product Manager of Vulnerability Research
Ready to Leverage Qualys to Reduce Your Risk? Explore How!