Comprehensive Steps to TruRisk™: From Insight to Action Using VMDR
Transitioning from Traditional Vulnerability Management to Business-Centric Risk Reduction & management
In cybersecurity, numbers can be deceptive. The sheer volume of vulnerabilities does not equate to risk. Instead, resilience depends on understanding which vulnerabilities pose the greatest threat to your business—and acting on them. This is where Qualys VMDR with TruRisk empowers organizations, enabling a shift from traditional vulnerability management to risk-based prioritization, aligning technical efforts with organizational goals.
Preparation Phase: Establishing a Strong Foundation for Risk Management
George Washington’s words, “To be prepared for war is one of the most effective means of preserving peace,” highlight the importance of strategy and readiness—whether in national defense or cybersecurity. Today, organizations must move beyond reacting to every threat and focus on prioritizing the vulnerabilities that matter most. This approach turns raw data into clear, actionable insights that directly reduce business risk and align cybersecurity efforts with broader organizational goals.
By prioritizing risks based on their potential impact and likelihood, companies can focus their resources on the vulnerabilities that truly matter.
This proactive strategy is built on three key actions:
- Measure: Assess your organization’s risk exposure, identify critical assets, and evaluate the potential impact of threats.
- Communicate: Align technical findings with business priorities, ensuring a common understanding of risk across all stakeholders.
- Eliminate: Take decisive action to reduce the vulnerabilities that pose the greatest risk to the organization.
The foundation of this approach lies in a simple but powerful formula:
Understanding Risk: How Likelihood and Impact Drive Business Decisions
The formula Risk = Likelihood x Impact helps ensure all stakeholders speak the same language while aligning efforts with business goals. This shared approach simplifies decision-making, optimizes resource allocation, and aligns cybersecurity efforts with organizational goals.
These core principles form the foundation of a comprehensive, risk-based framework that drives tangible business value.
Five Key Steps to Reduce Risk Effectively Using Qualys TruRisk
Step 1: Identify Gaps and Shift Towards Priority-Driven Risk Management Strategies
Risk Alignment – Using a Shared Language
“If you know the enemy and know yourself, you need not fear the result of a hundred battles.” — Sun Tzu
Effective cybersecurity begins by aligning technical and business priorities. Moving beyond vulnerability reduction to measurable risk reduction requires answering key questions:
- What is your organization’s risk tolerance?
- What is the value of each asset to the business?
- What would be the impact if critical assets were compromised?
By using the formula Risk = Likelihood x Impact, organizations can identify vulnerabilities that pose the greatest risk while simultaneously ensuring remediation efforts focus on prioritizing what is most important to the business.
Step 2: Conduct an Accurate Inventory and Measurement of Threats
Likelihood of Threat – QDS Insights
“The first step to victory is knowing your battlefield.” — Field Marshal Bernard Montgomery
Knowing your environment is foundational, but understanding real-world risks is transformative. Traditional vulnerability management often relies on CVSS scores alone, which may not account for the evolving threat landscape. For example, a vulnerability with a medium CVSS score could be far more dangerous if it’s tied to ransomware or listed in CISA’s Known Exploitable Vulnerabilities (KEV) catalog.
Qualys Detection Score (QDS) enhances visibility by integrating:
- Technical severity (e.g., CVSS score),
- Temporal details (e.g., exploit code maturity and threat intelligence), and
- Mitigation details (e.g., compensating controls).
With QDS, security teams gain actionable insights, enabling clear prioritization of high-confidence, high-impact threats. This focused approach narrows workloads while addressing vulnerabilities most likely to be exploited.
Resources and tooling such as MITRE ATT&CK, EPSS, and CISA KEV provide additional insight beyond technical severity, considering evidence of exploitation and evolving threats in cybersecurity.
For teams managing risk with custom workflows, multiple tools, and a variety of threat feeds, the process can feel overwhelming and fragmented. The need to reconcile conflicting data sources, align team priorities, and make sense of evolving threats often slows progress and increases the risk of overlooking critical vulnerabilities. Qualys Detection Score (QDS) eliminates these challenges by centralizing and simplifying ‘likelihood of threat’ assessment.
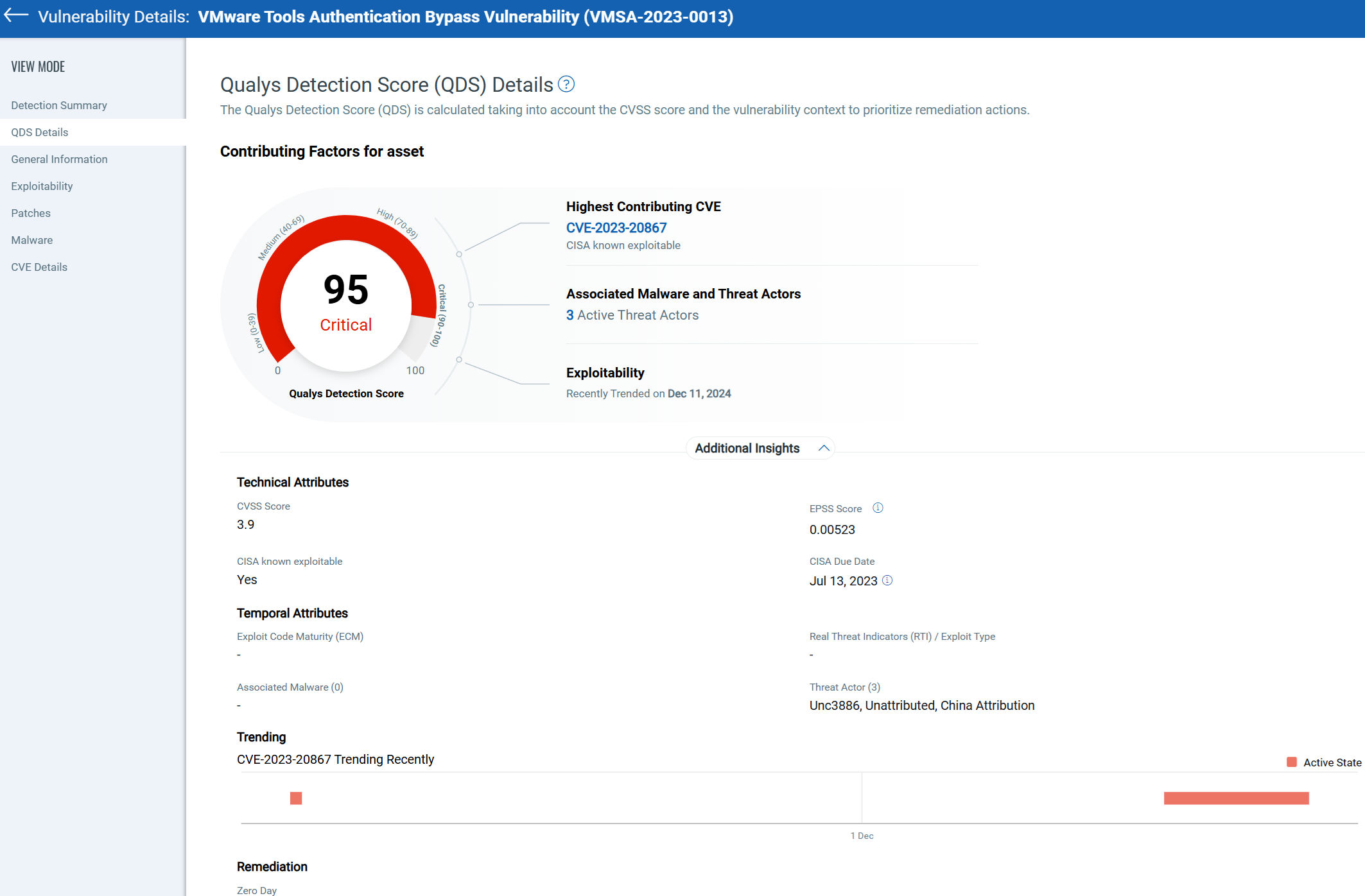
By distilling complex data into actionable insights, QDS removes guesswork, streamlines decision-making, and empowers teams to focus on high-impact, data-driven actions with confidence.
Step 3: Identify and Prioritize Critical Business Assets for Risk Mitigation
Assigning Business Impact
“In preparing for battle — plans are useless, but planning is indispensable.” — Dwight D. Eisenhower
Understanding asset importance is essential for effective risk prioritization. Many organizations struggle with this, often overlooking tools they already have, such as Business Continuity and Disaster Recovery Plans (BCP/DRP).
Conducting a Business Impact Analysis (BIA) and assigning Asset Criticality Scores (ACS) simplifies this process. ACS incorporates the Confidentiality, Integrity, and Availability (CIA) of each asset, aligning technical exposure risk with its potential business impact.
Start with “Crown Jewel” assets—those critical to operations—and assign them the highest ACS values.
Incorporating ACS into your strategy connects technical insights with business priorities, forming a crucial component of the Risk = Likelihood (QDS) x Impact (ACS) formula to enhance risk visibility. This provides a solid foundation for risk-based prioritization and drives targeted remediation efforts where they matter most.
Reference: Calculating Asset Risk Score in Qualys VMDR
Step 4: Communicate, Track, and Quantify Risk Reduction Progress Over Time
“Leadership and learning are indispensable to each other.” — John F. Kennedy
Quantifying risk is critical in linking technical data with business impact, ensuring decisions stay relevant as situations change. Regular validation and verification of risk assessments help maintain confidence in your approach, allowing teams to adjust strategies as new information and threats emerge. Frameworks such as NIST SP 800-37, ISO 31000, COSO, and COBIT can guide risk management efforts, but tracking must remain dynamic and integrated with existing tools to stay ahead of emerging threats.
Good News: Qualys TruRisk is included with VMDR, enabling an instant shift from traditional vulnerability tracking to risk-based prioritization!
Or stated differently… Risk (TruRisk) = Likelihood (QDS) x Impact (ACS)
- Likelihood: Measured using QDS, which incorporates threat intelligence and exploitability.
- Impact: Represented by ACS, reflecting the value of assets to the business.
- Actionable metrics: Use risk scores to guide decisions, measure progress, and refine your strategy over time.
With just a few clicks—like creating your first tag and assigning an ACS score—you will be on your way to managing risks based on genuine business impact. TruRisk ensures that efforts align with business priorities, helping to reduce risk where it matters most.
Step 5: Implement Risk Reduction Tactics to Eliminate Threats
“The art of communication is the language of leadership.” — James Humes, former Presidential speechwriter and author.
Effective risk management doesn’t stop at identification—it’s about clear communication and decisive action. With TruRisk, organizations can align cybersecurity efforts with business goals, ensuring meaningful and measurable risk reduction.
Here are four powerful methods to show the value of VMDR with TruRisk:
1. VMDR Prioritization – Getting Started
- TruRisk mode: Prioritize remediation based on Qualys TruRisk.
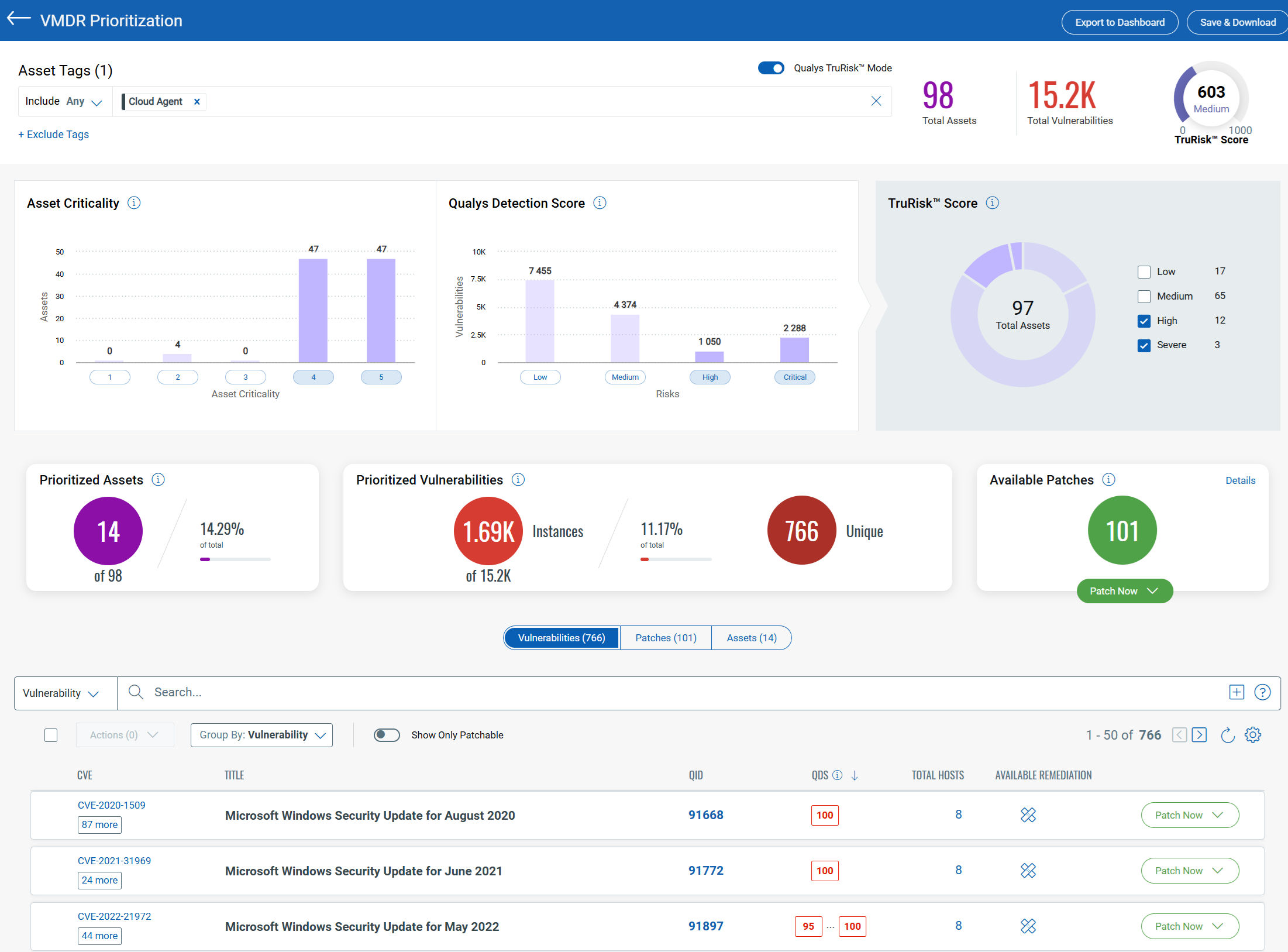
- Custom mode: Tailor your strategy with traditional scoring, real-time threat indicators, detection age, and attack surface insights.
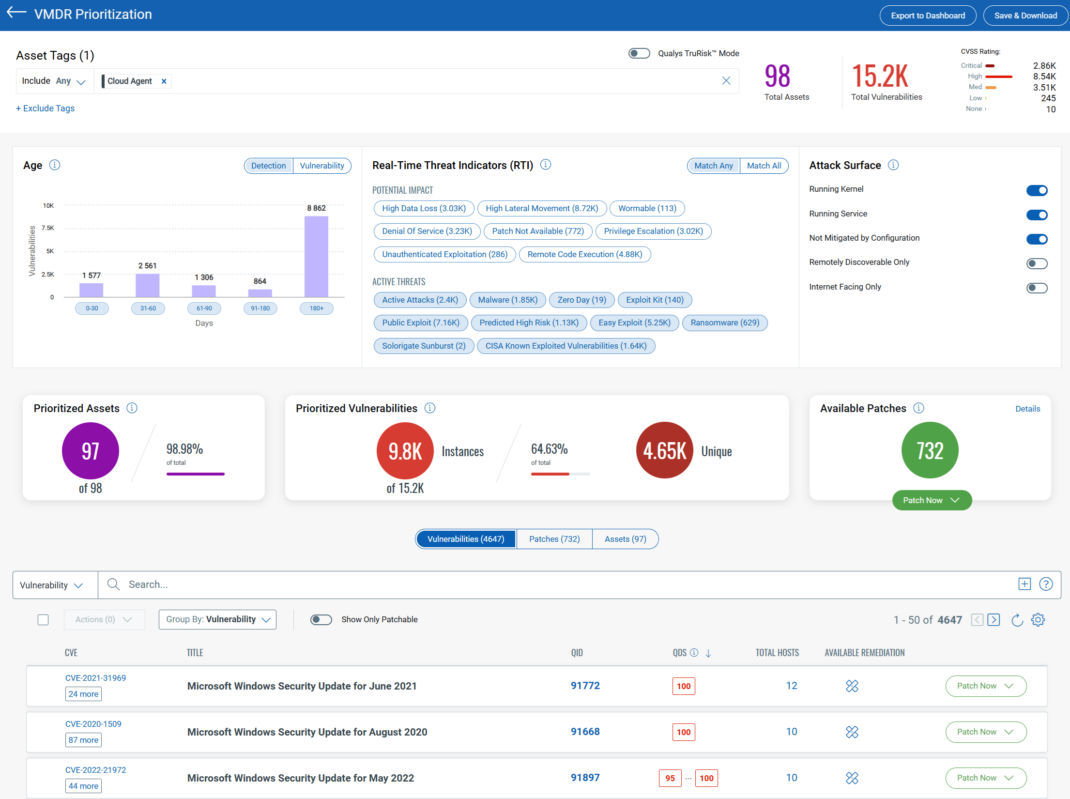
- Quick Tip: Patch Management subscribers create instant remediation jobs directly from this screen!
2. Patch and Remediate: Shift to a patch-prioritized view for streamlined remediation efforts.
3. MITRE ATT@CK Prioritized view – Leverage the MITRE ATT@CK Matrix framework to refine your prioritization strategy further.
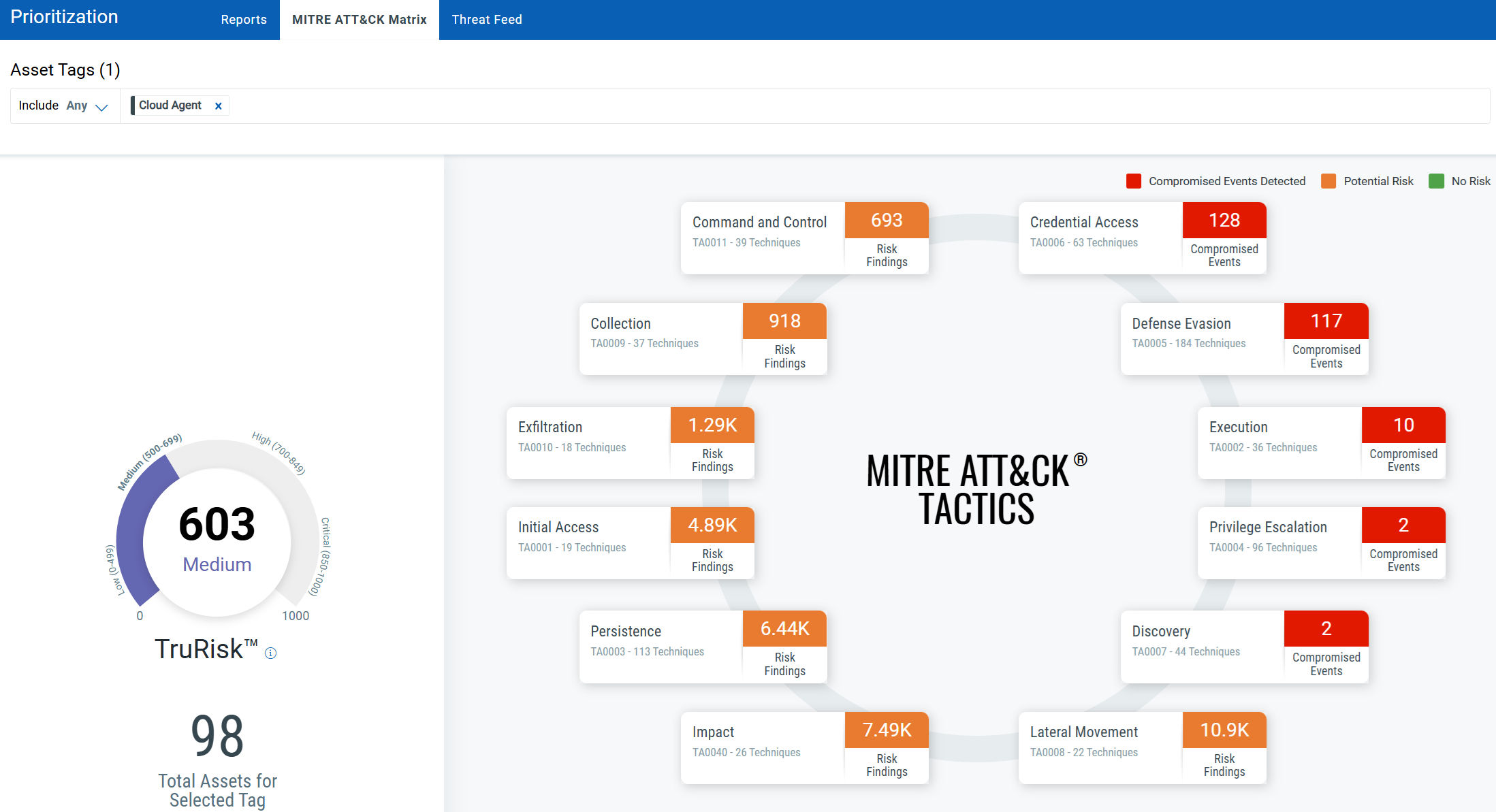
4. Our brand-new dashboard, “Steps to TruRisk,” has no tags to build, and TruRisk trends are enabled the moment you click import!
- Track vulnerabilities, CISA KEV, and risk factors, and compare CVSS vs. QDS.
- Real-time risk tracking and recalculation as assets check in.
- Business Impact and recent assignment awareness.
Get started now!
Steps To TruRisk Dashboard
These capabilities reduce noise, drive efficiency, and foster proactive risk management, allowing teams to focus on meaningful outcomes rather than simply chasing numbers.
Achieving Organizational Objectives Through Effective Risk Reduction
Qualys VMDR with TruRisk offers a structured framework that empowers organizations to align technical efforts with business objectives. By focusing on the core pillars of measurement, communication, and elimination, teams can not only reduce risk effectively but also demonstrate their value to key stakeholders.
- Measure: Utilize Qualys’ QDS and ACS to assess risk, pinpoint high-priority vulnerabilities, and track meaningful progress.
- Communicate: Bridge the gap between technical findings and business impact by translating risk into actionable insights. Risk (TruRisk) = Likelihood (QDS) x Impact (ACS).
- Eliminate: Optimize remediation workflows to tackle the most critical threats, continuously improving your security posture.
Wherever your organization stands today, Qualys supports your existing methods and meets you where you are. When the time is right, VMDR with TruRisk is ready, providing a practical, business-oriented pathway to risk-based prioritization.
By leveraging these strategies, you’re not just reducing risk — you’re positioning your organization as a leader in proactive, business-aligned cybersecurity, setting the stage for sustainable success and long-term resilience.
SPECIAL THANKS FROM THE AUTHOR TO CONTRIBUTORS:
- Russ Sanderlin, VMDR Director, Subject Matter Expert, Qualys
- Marcus Burrows, Lead Technical Trainer, Qualys
- Ramesh Ramachandran, Principal Product Manager, VMDR, Qualys
- Kevin O’Keefe, Lead Security Solutions Architect, Qualys
WHAT’S COMING?
- Enhanced Qualys Enterprise TruRisk Platform User Interface
- Announcing TruRisk 2.0
- Qualys TruRisk Eliminate
- Qualys Enterprise TruRisk Management (ETM)
Excellent write up!
Thanks so much Adam! Appreciate your live attendance and great questions!
Have a happy New Year, sir!
All the best,
Thanks so much Adam – Appreciate your live attendance and great questions!
Hope you and yours have a blessed New Year!
All the best,