Steps to TruRisk™ – 2: Measure the Likelihood of Vulnerability Exploitation
Table of Contents
- Victory Belongs to the Well-Informed
- Defining the Components of Likelihood of Exploit
- The Role of CVSS, EPSS, and CISA KEV in Risk Assessment
- The Case for Context: Why Meaningful Remediation is Critical
- Qualys Vulnerability Score (QVS): A Unified Measure of Exploitability
- Qualys Detection Score (QDS): Operationalizing Risk
- Practical Evaluation of QDS vs CVSS
- From Overload to Actionable Insights
Cybersecurity programs rely on various methods to measure the risk associated with vulnerabilities for prioritization, such as CVSS, EPSS, CISA KEV, or even internally developed systems that combine multiple approaches. While these methods help assess whether a specific vulnerability exists on an asset and define its severity, traditional frameworks like CVSS often overlook the likelihood of exploitation. While EPSS and CISA KEV provide more direct insight into the likelihood of exploitation, many programs still rely heavily on severity scores alone, which can leave gaps in understanding the true risk. This oversight can hinder organizations from making fully informed decisions about managing risk for their business and digital assets.
To bridge this gap, Qualys Vulnerability Score (QVS) and Qualys Detection Score (QDS), key components of Qualys TruRisk™, leverage over 25 sources of threat intelligence to measure the likelihood of vulnerability exploitation. While other methods may only capture part of the picture or require additional calculations, we aggregate and analyze this data automatically through one comprehensive solution. Our continuously updated scores provide cybersecurity teams with confidence in their assessments, give remediation owners assurance that their efforts are making a measurable impact, and offer business stakeholders certainty that risk management strategies are effectively reducing organizational exposure.
This blog is the second installment in the five-part Steps to TruRisk™ series on operationalizing a risk-based vulnerability management program with Qualys TruRisk. In this post, we explore why adopting such a system is essential for driving meaningful risk reduction.
Before we dive into Step 2, explore the Step 1 of our five-part series to get insights into priority-driven risk management strategies!
Steps to TruRisk™
Ready to take the next step toward smarter Risk Management? Check out our exclusive webinar for a deeper dive into “Steps to TruRisk™: Step 2”!
Victory Belongs to the Well-Informed
Success in any battle, whether on the battlefield or in cybersecurity, depends on more than sheer strength. It requires intelligence, strategic insights, and the ability to act on the right information at the right time. Leaders throughout history have turned to covert networks to uncover critical information, disrupt enemy plans, and anticipate the next move. One of the most striking examples comes from the American Revolution, where intelligence networks provided critical insights that helped shape strategic decisions.
In 1775, thirteen American colonies stood on the brink of Revolutionary war against the most powerful military and colonial force in the world. Victory would demand more than sheer firepower, it would require intelligence, grit, and relentless innovation.
During the war, George Washington relied on an intelligence network to track enemy movements and gain a strategic edge—proving that timely, accurate insights can turn the tide of conflict. He authorized the Culper Ring, a covert intelligence network operating behind enemy lines. Its members risked their lives to gather and relay critical information, using coded messages, dead drops, and invisible ink to evade detection. Their intelligence shaped key strategic decisions, exposing threats, disrupting enemy plans, and keeping the Continental Army ahead of its adversaries. Victory in war was not won by force alone, but through precision, deception, and the mastery of strategy.
The necessity of procuring good Intelligence is apparent and need not be further urged.
– George Washington

This same principle applies to cybersecurity today. Organizations are constantly under siege by evolving cyber threats. But the challenge isn’t just about fending off attacks, it’s about knowing where to focus. With thousands of vulnerabilities and alerts flooding security teams daily, the real struggle is identifying which risks matter most and require immediate action.
By delivering clear, contextualized risk intelligence, Qualys TruRisk helps businesses cut through the noise, prioritize the most pressing threats, and allocate resources effectively. Just as intelligence networks shaped the outcomes of historic conflicts, actionable cybersecurity insights can mean the difference between a reactive defense and a proactive, strategic advantage.
Defining the Components of Likelihood of Exploit
The likelihood of vulnerability exploitation is a key part of the risk equation, expressed as Risk = Likelihood × Impact. Likelihood itself is determined by Threat × Vulnerability.
- A vulnerability is a weakness in a system or process that could be exploited by a threat.
- A threat is any action or event that could adversely affect that system or process.
- Exploitation occurs when an attacker takes advantage of a vulnerability.
For risk to exist, a vulnerability must have a corresponding threat that can exploit it. If a vulnerability exists but is not actively exploited and no known proof of concept is available, then the likelihood of exploitation is very low. Conversely, if a credible threat exists but the vulnerability has been patched, the likelihood of exploitation is effectively zero.
To truly manage risk, it’s important to understand how the likelihood of exploitation works. Think of it like this: a vulnerability is like an unlocked door, and a threat is someone who knows how to walk through it. But for risk to become real, there needs to be a perfect storm—an active threat ready to exploit that open door. If the door’s locked, even the most skilled intruder can’t get through. By assessing both vulnerabilities and active threats, organizations can focus on the risks that matter most. A well-informed approach ensures that resources are allocated efficiently, reducing exposure to real-world attacks while avoiding unnecessary panic over theoretical risks.
The Role of CVSS, EPSS, and CISA KEV in Risk Assessment
CVSS is the industry standard for measuring the severity of a vulnerability. However, CVSS lacks organizational context. It quantifies how dangerous a vulnerability could be, but not how dangerous it actually is to a specific organization. It does not consider security controls in place, the criticality of the affected asset, or environmental factors that may impact risk. Additionally, CVSS temporal metrics, which attempt to account for exploit code maturity, are not updated consistently, making them unreliable for dynamic risk assessment.
One challenge with CVSS is that over half of all vulnerabilities are categorized as Critical or High. Another challenge is that out of the full breadth of CVEs listed in the NVD, only about 3 to 4 percent contribute to the highest risk. These include vulnerabilities with active exploits, inclusion in the CISA KEV catalog, exploitation by malware or ransomware, use by threat actors, or widespread recognition, often called celebrity vulnerabilities. Without additional context, organizations struggle to determine which vulnerabilities should be prioritized. If everything is labeled critical, then nothing truly is, leading to inefficiencies in remediation efforts.
To address this, EPSS and CISA KEV focus on the likelihood of exploitation, providing valuable insight into which vulnerabilities pose the most immediate risk. However, these models do not factor in severity as defined by CVSS, meaning they must be used alongside other assessments to provide a complete risk picture.
Given the overwhelming number of vulnerabilities and limited remediation resources, organizations need a risk-based approach that incorporates both severity and likelihood while also factoring in asset context. While CVSS does provide mechanisms for integrating temporal and environmental factors, applying these consistently can be complex and time-consuming, requiring additional effort to define and maintain reliable metrics.
The Case for Context: Why Meaningful Remediation is Critical
One point of contention between IT and Cybersecurity is that the IT teams perceive that the Cybersecurity team which is going through and identifying a volume of vulnerabilities is not looking deeper into the how likely the vulnerability is to be an actual problem. IT teams often feel that they are being asked to remediate issues simply because a vulnerability appears technically severe under certain conditions—even when there is no proof of concept or active exploitation. This disconnect can create frustration, as teams struggle to prioritize meaningful security efforts over theoretical risks.
It is better if the IT teams know that their contributions for risk reduction highly matter to the organization and are a vital part of the business strategy. That they are truly helping defend the organization against a vulnerability that pose a legitimate threat, instead of digging the proverbial ditch that devolves into what feels like busywork by reducing a never-ending tumult of volumetrics that doesn’t really move the needle of risk in an organization. This deteriorates the credibility of the Cybersecurity team, and it leaves the IT teams doing work that feels devoid of meaning.
Restoring trust between IT and Cybersecurity starts with focusing on real threats. To shift from high-volume remediation to high-impact action, teams need risk context. This is where QVS and QDS become a game changer. QVS scores vulnerabilities by their likelihood of exploitation, while QDS applies that insight at the asset level—factoring in compensating controls to show true risk. Together, they provide a new kind of clarity to the teams and help them move from reactive remediation to strategic risk reduction.
Qualys Vulnerability Score (QVS): A Unified Measure of Exploitability
The Qualys Vulnerability Score (QVS) quantifies the likelihood of exploitation by consolidating all threat intelligence associated with a CVE into a single score. The risk factors that contribute to each QVS score provide clear evidence to stakeholders, making it easier to understand the risk associated with a vulnerability.
QVS is derived from two key factors:
- Technical Details (CVSS score)
- Temporal Details (External threat intelligence, exploit code maturity and trending data)
Qualys calculates a QVS for every vulnerability in the National Vulnerability Database (NVD), whether or not a Qualys detection has been built for it. This serves two purposes:
- The score is ready for when a Qualys detection is delivered to the platform.
- It enables Enterprise TruRisk Management (ETM) customers to measure the likelihood of exploit for vulnerabilities imported from other vulnerability detection tools that standardize at the CVE level.
This approach leads to a more comprehensive measure of risk across assets, helping organizations strengthen their cybersecurity posture.
Qualys Detection Score (QDS): Operationalizing Risk
For VMDR, the Qualys Detection Score (QDS) is derived from the highest Qualys Vulnerability Score (QVS) among any associated CVEs. When multiple CVEs contribute to a QID, the CVE with the highest CVSS score is used in the QDS calculation.
QDS is derived from two factors:
- The highest QVS of all associated CVEs
- Compensating Controls
To learn more, explore ‘Understanding Qualys Detection Scores’ in our TruRisk™ documentation, which includes a table listing the factors present at each QDS level.
QDS values assigned to vulnerabilities are also applied to web assets with Total Application Security (TAS), Container workloads in Container Security (CS), and are reflected on assets in Global AssetView/Cybersecurity Asset Management that are entitled for VMDR.
Compensating Controls
The QDS assigned to an asset represents the inherent risk of that vulnerability. With TruRisk™ Mitigate, part of our TruRisk™ Eliminate portfolio, customers can apply compensating controls to endpoints, reducing the QDS score to reflect residual risk. This is particularly valuable when a vendor has not yet released a patch for a new vulnerability, and a configuration change on the asset can reduce its exposure risk.
When reviewing the TruRisk™ score for an asset, the individual vulnerability scores that contribute to that score are expressed as QDS values. We will explore this further in Step 3 of our Five-Steps to TruRisk blog series.
For example, with CVE-2021-34527 (Print Nightmare), stopping the print service would prevent exploitation of the vulnerability. However, since the underlying code facilitating the vulnerability remains on the system, the risk is still assessed, but the QDS score for that asset will be reduced. When prioritizing vulnerabilities across your environment, those that remain unmitigated will receive higher scrutiny.
Additionally, we offer a beta feature for PC Control mitigation. If a PC Control passes for certain vulnerabilities, we’ll reduce the QDS for affected assets. To learn more about activating this beta feature and to obtain release notes, please reach out to your TAM.
Using QDS Beyond Vulnerabilities
QDS score assessments are not limited to vulnerabilities found throughout the Qualys platform. Risk factors beyond vulnerabilities can generate their own QDS scores, which contribute to an asset’s TruRisk score provided the subscription owner has adopted the Cybersecurity Asset Management (CSAM) and Policy Compliance modules.
- Unauthorized Ports (CSAM) – Assigns a QDS score based on the risk posed by open ports..
- End of Support (CSAM) – Assigns a QDS score based on vulnerabilities associated with End of Life or End of Service status of operating systems or software.
- Missing Required Software (CSAM) – Applies a custom QDS score when defined software required for asset protection is missing.
- Unauthorized Software (CSAM) – Applies a QDS score when defined rules identify software on an asset that poses organizational risk.
- Misconfigurations (PC) – Applies a QDS score to assets based on failed controls linked to misconfigurations.
Practical Evaluation of QDS vs CVSS
Risk appetite refers to the level of risk an organization is willing to accept in pursuit of its objectives before requiring mitigation or action. In vulnerability prioritization, organizations may choose to accept the risk associated with certain vulnerabilities such as those with low CVSS or Qualys Severity scores while placing greater emphasis on remediating vulnerabilities with higher scores, even if no immediate threat is detected.
However, a vulnerability with a low CVSS score can still have a high QDS score. This often happens because attackers tend to exploit overlooked vulnerabilities, leveraging them to evade detection. Organizations relying solely on CVSS or traditional vulnerability management policies and SLAs may miss these risks, leaving them exposed.
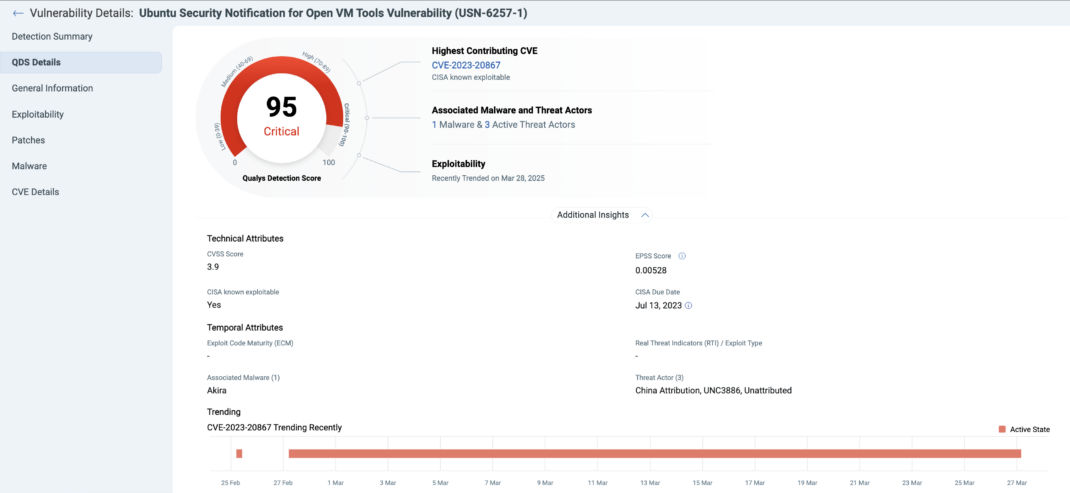
Low CVSS criticality, with high QDS
To identify vulnerabilities with a QDS of 90 or higher and Low CVSS criticality, use the following QQL query:
vulnerabilities.detectionScore>=90 and vulnerabilities.vulnerability.criticality:LOW
In the example result below, CVE-2023-20867 has a CVSS score of 3.9, yet it appears on the CISA KEV list, is linked to an active malware campaign, and is being exploited by multiple threat actors demonstrating why QDS provides critical insights beyond CVSS alone.
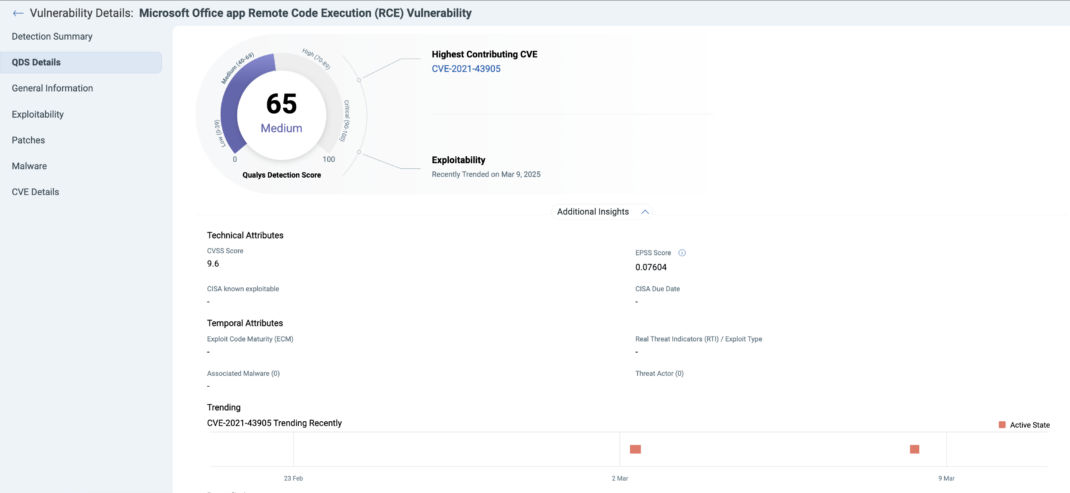
High to Critical CVSS, Low QDS
Conversely, some vulnerabilities may have a high CVSS score but a low QDS score if they lack active exploitation or associated threats.
To identify vulnerabilities with a QDS of 70 or lower and Critical CVSS classification, use the following QQL query:
vulnerabilities.detectionScore>=70 and vulnerabilities.vulnerability.criticality:LOW
For example, CVE-2021-43905 has a critical CVSS score of 9.6, yet its QDS remains low due to the absence of known exploits or malware activity so the likelihood of exploitation is low.
Understanding the distinction between CVSS and QDS will enable you to fine-tune your organization’s vulnerability strategy. Rather than solely relying on static severity scores, prioritize efforts using real world risk factors will ensure remediation efforts are directed where they matter most.
From Overload to Actionable Insights
Security teams often face an overwhelming number of vulnerabilities, many of which may never be exploited. The challenge isn’t just finding vulnerabilities but knowing which ones actually matter. TruRisk Step 2 provides the intelligence needed to move from raw data to actionable insights, ensuring that security efforts are focused on the threats that pose the greatest risk to the organization. By combining real-time threat intelligence with asset context and exploitability data, security teams can prioritize remediation with confidence.
With tools like the Qualys Vulnerability Score (QVS) and Qualys Detection Score (QDS), teams can go beyond generic severity ratings and understand the real likelihood of exploitation. This shifts security from a reactive approach—where teams chase every possible risk—to a strategic model that balances efficiency with effectiveness. The result is a security program that not only reduces risk but also aligns with broader business objectives, ensuring that resources are used where they have the most impact.
If you’re not yet using VMDR to measure, communicate, and eliminate risk, we invite you to start a risk-free 30-day trial.
Contributors
Anthony Williams, Subject Matter Expert, VMDR