Why Organizations Struggle with Patch Management (and What to Do about It)
The cybersecurity attack surface continues to grow exponentially. Modern technologies are being deployed on-premises and in the cloud as part of digital transformation journeys. Meanwhile, the current practice of identifying, classifying, prioritizing, and remediating vulnerabilities has become strained and ineffective at many enterprises. The question is: Why?
In speaking to CISOs, CIOs, and practitioners at Qualys customer organizations and beyond, one thing is clear. Many are struggling to keep up amidst the cyber risk crisis that’s being exacerbated by a number of trends. These include the exponential increase in exploits, too many cybersecurity tools, IT complexity, the industry skills gap, and internal misalignment between security and IT teams. The result: prolonged exposure to risk to the business (see Figure 1).
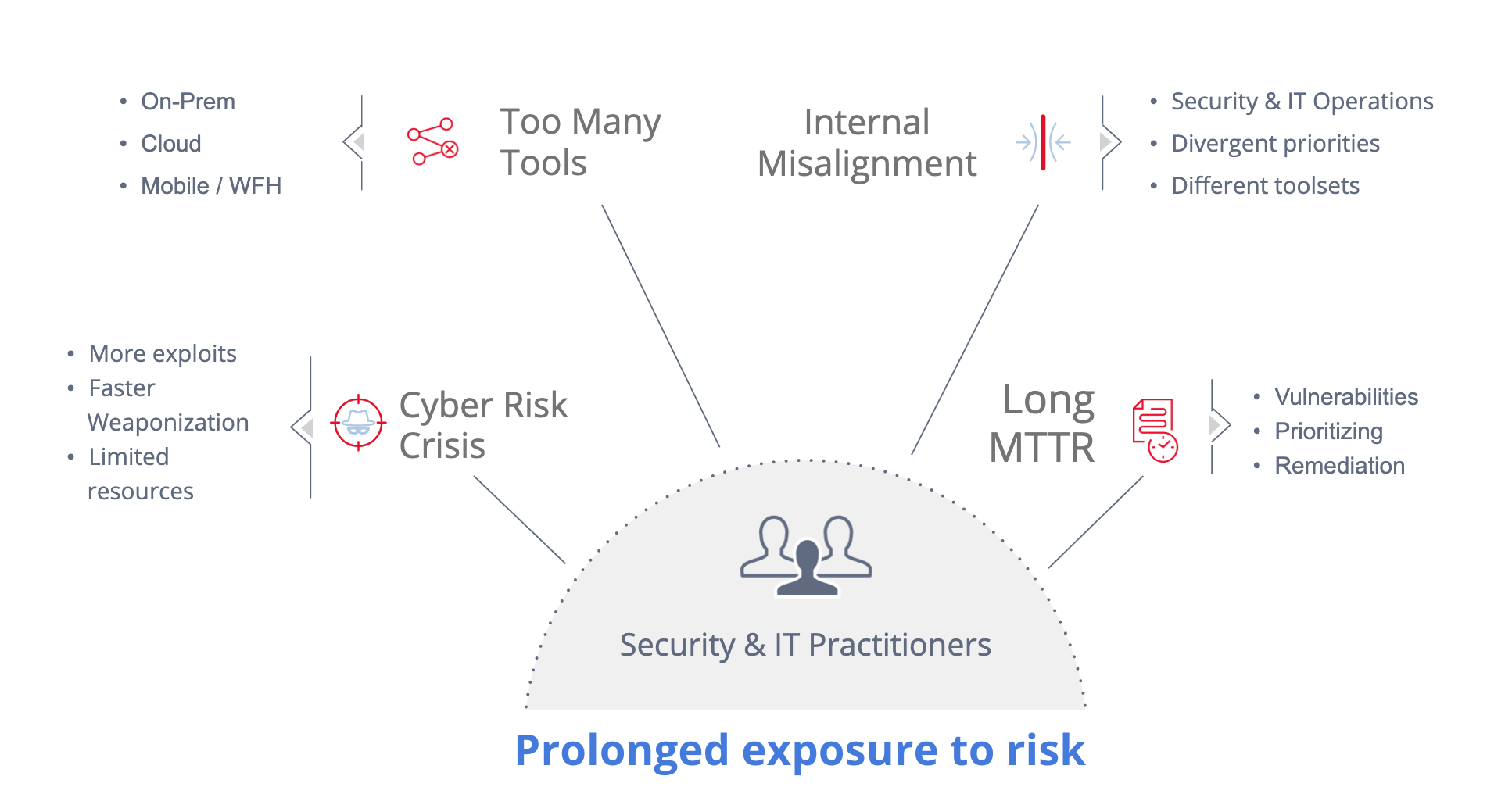
Figure 1: The Cyber Risk Crisis
4 Challenges that Complicate Patch Management
In particular, recent industry research reveals the following four challenges that all Cybersecurity professionals must confront:
- Rising vulnerabilities – According to the latest Verizon DBIR, the increase in ransomware attacks in 2021 was more than the last five years combined
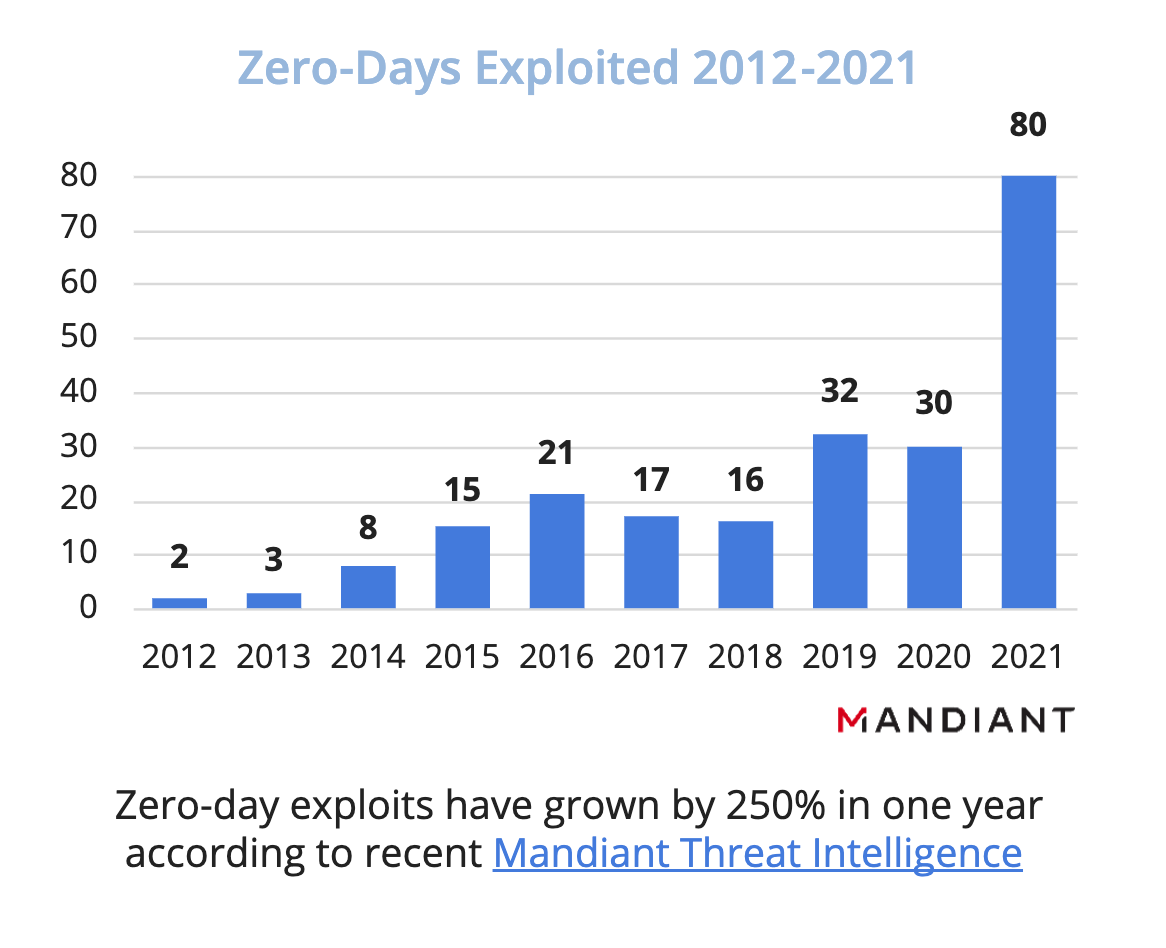
- More Exploits – Zero-day exploits reached an all-time high in 2021, more than doubling from 2020
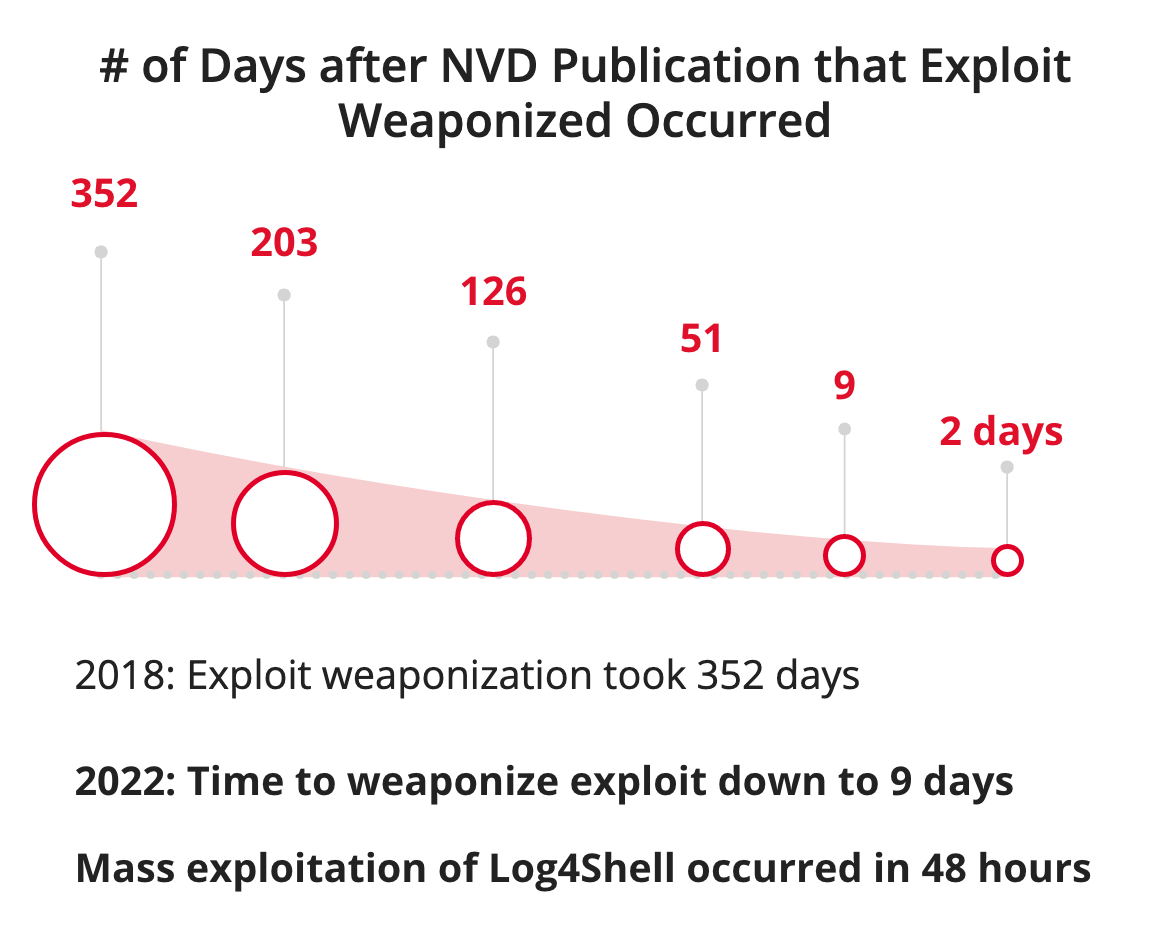
- Faster Weaponization – Weaponization of exploits has accelerated – with higher speed and greater quantity
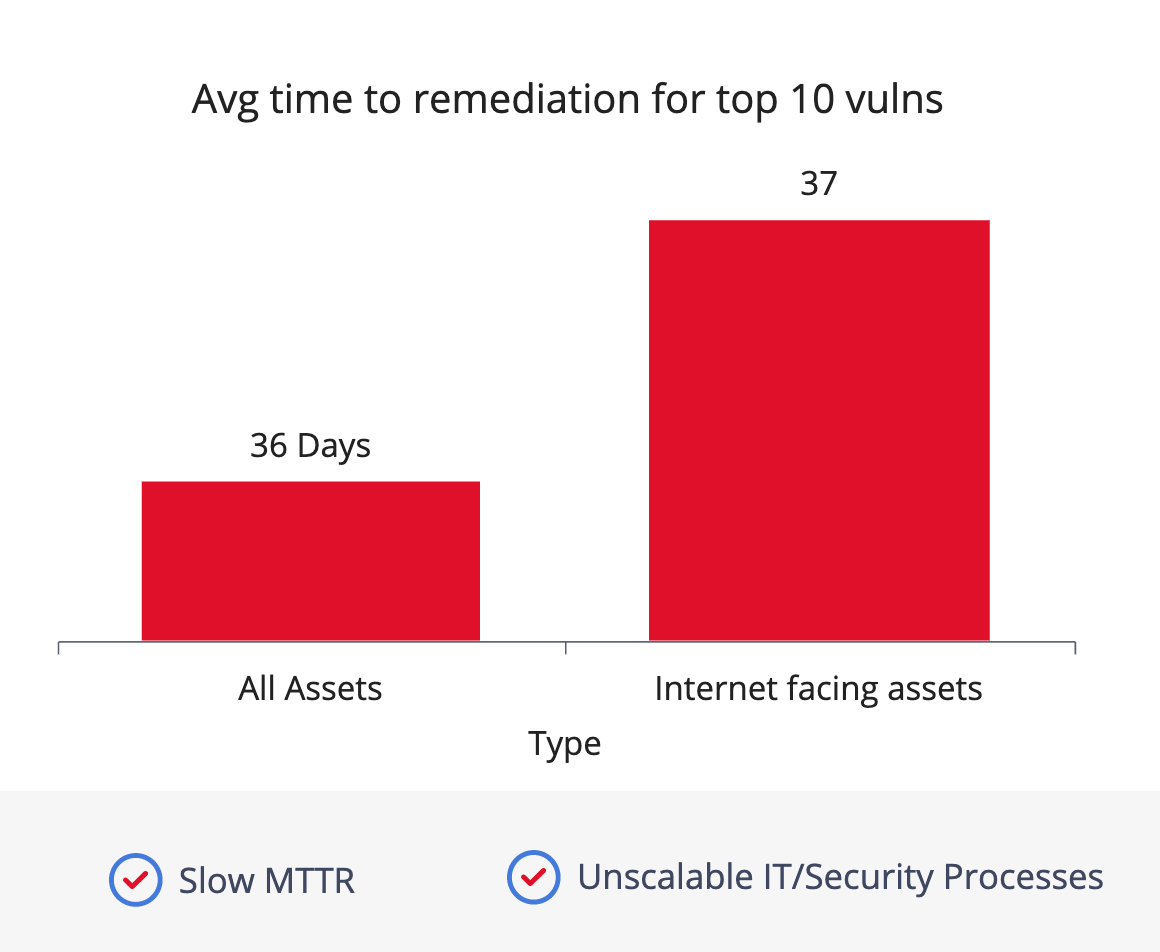
- Slow Remediation Times – Slow response can mean the difference between a business that is up & running and one that is offline for days, harming both revenue and reputation
To further complicate these issues for many enterprises, the IT resources required to patch all these vulnerabilities have not kept up with the pace at which new ones are disclosed and exploited. While small to mid-size enterprises may lack available staff; larger enterprises have too many IT assets to patch quickly. Add to these sobering statistics the fact that the correct remediation process is not always straightforward. In some cases, patching a vulnerability can require deploying a patch, making a configuration change, or both. All of these actions can introduce operational risk. Finally, IT teams responsible for ensuring systems are always up and running rightfully want to vet these changes before they go live.
4 Actions to Improve Patch Management
But hope is not lost. Here are a few key actions that organizations can take to get a better handle on patch management efficiency:
Look for flexibility – A vulnerability does not equal a patch. Remediation can take different forms. Look for a solution that is flexible and can support deploying patches, configuration changes, and updates to third-party applications.
Tame complexity with automation – Trying to tackle the exponential rise in threats manually is like trying to bail a sinking boat with a Dixie cup. Many patch deployments – even complex ones – can be completely automated through policy orchestration that drives operational efficiencies and MTTR improvements.
Take a risk-based approach – Prioritize vulnerabilities and patches from a risk-driven perspective. What are the threats that pose the greatest risk to your specific business, industry, or IT environment? Do you need to eliminate all vulnerabilities, or only those that have weaponized exploit code and are being utilized by threat actors in the wild? This implies pulling threat feeds into your analysis and/or integrating them with your platform of choice.
Strive for better alignment between Cybersecurity and IT Teams – Collaboration starts with working off a ‘single source of truth’ for assets and vulnerabilities that need to be discovered, assessed, prioritized, and remediated. No more complex handoff processes, non-normalized and/or inconsistent data, and disagreements on what needs to be tackled first. This alignment helps use resources more efficiently, lowers costs, and minimizes exposure time. These benefits ultimately result in improvement to your organization’s risk posture. Seek platforms with unified views, a single data model, and real-time dashboards that are aligned NOT to CVSS scores, but with true business risk.