April 2022 Patch Tuesday: Microsoft Releases 145 Vulnerabilities With 10 Critical; Adobe Releases 4 Advisories, 78 Vulnerabilities With 51 Critical.
Table of Contents
- Microsoft Patch Tuesday Summary
- Notable Microsoft Vulnerabilities Patched
- Notable Adobe Vulnerabilities Patched
- About Qualys Patch Tuesday
- Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
- Rapid Response With Patch Management (PM)
- Monthly Webinar Series: This Month in Vulnerabilities & Patches
- Join the Webinar This Month in Vulnerabilities & Patches
- Contributor
Microsoft Patch Tuesday Summary
Microsoft has fixed 145 vulnerabilities, including 17 Microsoft Edge vulnerabilities, in the April 2022 update, with ten classified as critical as they allow Remote Code Execution (RCE). This month’s Patch Tuesday release includes fixes for two zero-day vulnerabilities as well, one known to be actively exploited (CVE-2022-24521) and the other to be publicly exposed (CVE-2022-26904).
Microsoft has fixed several problems in their software, including Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, and Spoofing vulnerabilities.
Notable Microsoft Vulnerabilities Patched
This month’s advisory covers multiple Microsoft products, including, but not limited to, Azure, Browser (Edge – Chromium), Developer Tools, Extended Security Update (ESU), Microsoft Dynamics, Microsoft Office, SQL Server, System Center, and Windows.
CVE-2022-23259 | Microsoft Dynamics 365 (on-premises) Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
An authenticated user could run a specially crafted trusted solution package to execute arbitrary SQL commands. From there the attacker could escalate and execute commands as db_owner within their Dynamics 356 database.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-24491 and CVE-2022-24497 | Windows Network File System Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
An attacker could send a specially crafted NFS protocol network message to a vulnerable Windows machine, which could enable remote code execution. NOTE: This vulnerability is only exploitable for systems that have the NFS role enabled.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-24500 | Windows SMB Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This vulnerability requires that a user with an affected version of Windows access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message. For vulnerability to be exploited, a user would need to access a malicious SMB server to retrieve some data as part of an OS API call. Microsoft offers mitigations for this vulnerability; Block TCP port 445 at the enterprise perimeter firewall, and follow Microsoft guidelines to secure SMB traffic.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-24541 | Windows Server Service Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
This vulnerability requires that a user with an affected version of Windows access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message. Microsoft offers mitigations for this vulnerability; Block TCP port 445 at the enterprise perimeter firewall, and follow Microsoft guidelines to secure SMB traffic.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-26809 | Remote Procedure Call (RPC) Runtime Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
To exploit this vulnerability, an attacker would need to send a specially crafted Remote Procedure Call (RPC) to an RPC host. This could result in remote code execution (RCE) on the server-side with the same permissions as the RPC service. Microsoft offers mitigations for this vulnerability; Block TCP port 445 at the enterprise perimeter firewall, and follow Microsoft guidelines to secure SMB traffic.
Exploitability Assessment: Exploitation More Likely.
Notable Adobe Vulnerabilities Patched
Adobe released four advisories with updates to fix 78 vulnerabilities affecting Acrobat, Acrobat Reader, Adobe After Effects, Adobe Commerce, Magento Open Source, and Photoshop. Of these 78 vulnerabilities, 51 are rated as critical.
APSB22-13 | Security Updates Available for Adobe Commerce
This update resolves one critical vulnerability.
Adobe Priority: 3
Adobe has released a security update for Adobe Commerce and Magento Open Source. This update resolves a critical Arbitrary code execution vulnerability. Successful exploitation could lead to arbitrary code execution.
APSB22-16 | Security Updates Available for Adobe Acrobat and Reader
This update resolves multiple critical, important, and moderate vulnerabilities and addresses 62 CVEs.
Adobe Priority: 2
Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. Successful exploitation could lead to arbitrary code execution, memory leak, security feature bypass, and privilege escalation.
APSB22-19 | Security Updates Available for Adobe After Effects
This update addresses two critical security vulnerabilities.
Adobe Priority: 3
Adobe has released an update for Adobe After Effects for Windows and macOS. Successful exploitation could lead to arbitrary code execution in the context of the current user.
APSB22-20 | Security Updates Available for Adobe Photoshop
This update addresses 13 critical security vulnerabilities.
Adobe Priority: 3
Adobe has released an update for Photoshop for Windows and macOS. Successful exploitation could lead to arbitrary code execution.
About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
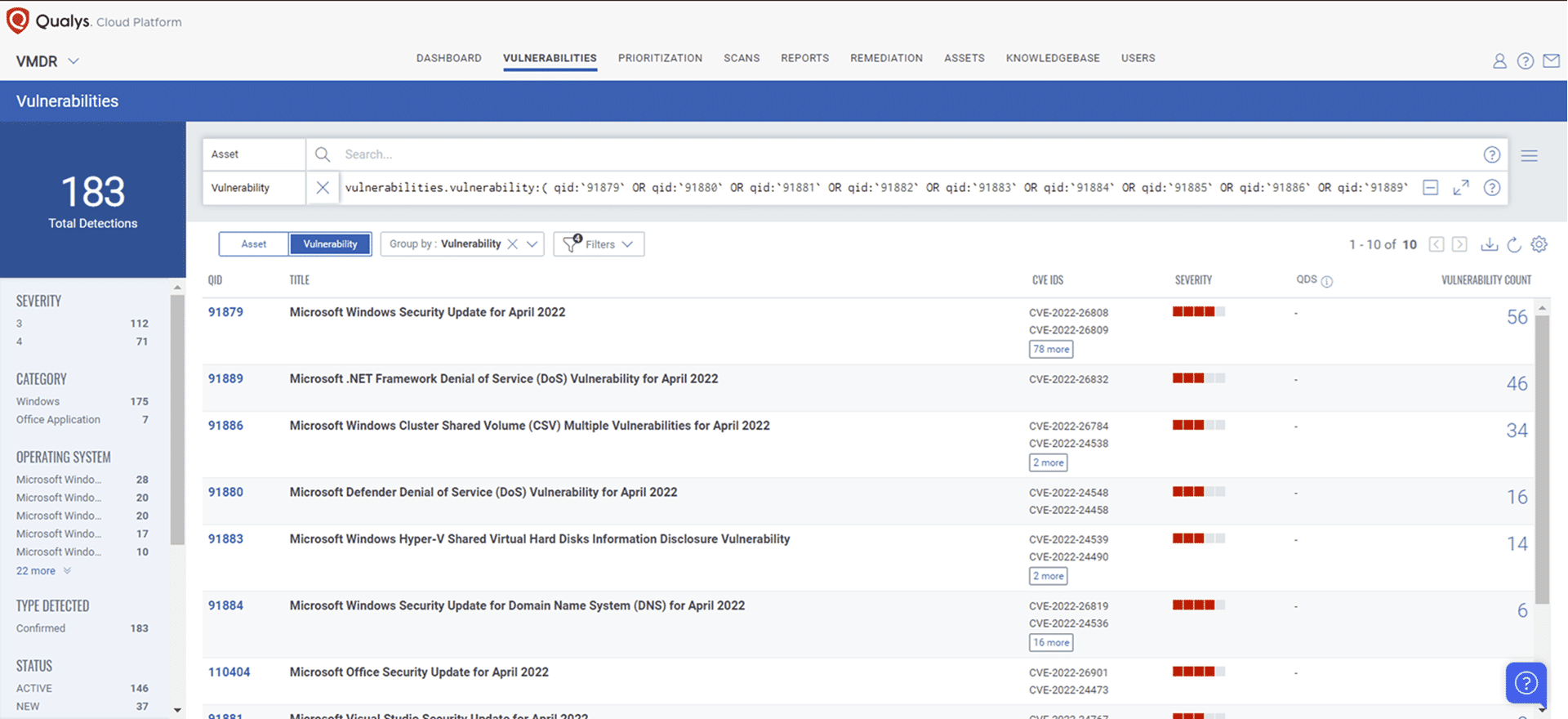
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:91879 OR qid:91880 OR qid:91881 OR qid: 91882 OR qid:91883 OR qid:91884 OR qid:91885 OR qid:91886 OR qid:91889 OR qid:91890 OR qid:110404 OR qid:110405 OR qid:110406 OR qid:376535 )
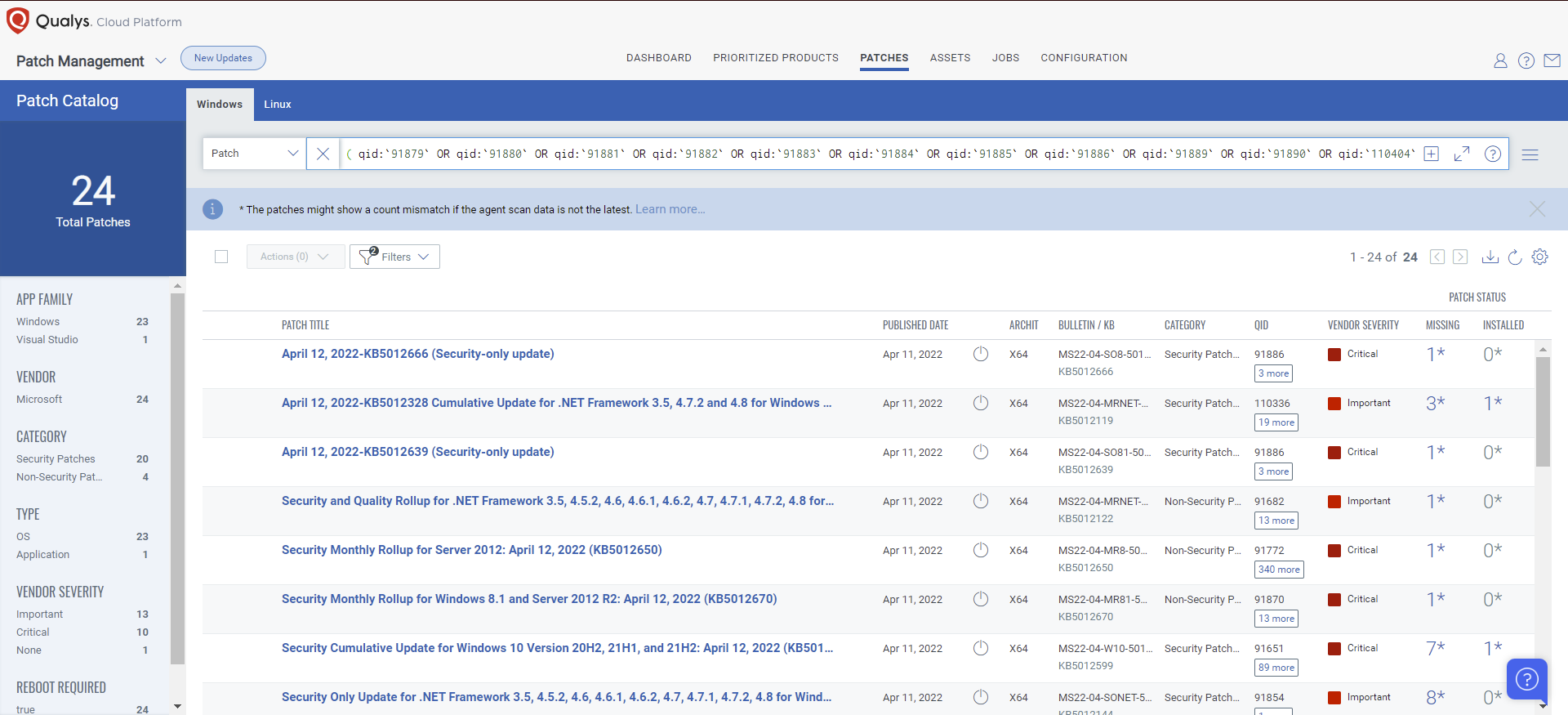
Rapid Response With Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday:
( qid:91879 OR qid:91880 OR qid:91881 OR qid:91882 OR qid:91883 OR qid:91884 OR qid:91885 OR qid:91886 OR qid:91889 OR qid:91890 OR qid:110404 OR qid:110405 OR qid:110406 OR qid:376535 )
Monthly Webinar Series: This Month in Vulnerabilities & Patches

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Patch Management (PM). Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Patch Management.
Join the Webinar This Month in Vulnerabilities & Patches
Contributor
Bharat Jogi, Director, Vulnerability and Threat Research, Qualys