May 2022 Patch Tuesday | Microsoft Releases 75 Vulnerabilities With 8 Critical; Adobe Releases 5 Advisories, 18 Vulnerabilities With 16 Critical.
Table of Contents
- Microsoft Patch Tuesday Summary
- Notable Microsoft Vulnerabilities Patched
- Microsoft Last But Not Least
- Notable Adobe Vulnerabilities Patched
- About Qualys Patch Tuesday
- Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
- Rapid Response with Patch Management (PM)
- Qualys Monthly Webinar Series
- Join the webinar this Month in Vulnerabilities & Patches
Microsoft Patch Tuesday Summary
Microsoft has fixed 75 vulnerabilities in the May 2022 update, including one advisory ( ADV220001 ) for Azure in response to CVE-2022-29972, a publicly exposed Zero-Day Remote Code Execution (RCE) Vulnerability, and eight vulnerabilities classified as critical as they allow Remote Code Execution (RCE) or Elevation of Privileges. This month’s Patch Tuesday release includes fixes for two other zero-day vulnerabilities as well: one known to be actively exploited (CVE-2022-26925) and the other for being publicly exposed (CVE-2022-22713).
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege, Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing vulnerabilities.

Notable Microsoft Vulnerabilities Patched
This month’s advisory covers multiple Microsoft product families, including Azure, Developer Tools, Extended Security Update (ESU), Exchange Server, Microsoft Office, and Windows. A total of 97 unique Microsoft products/versions are affected.
Downloads include Monthly Rollup, Security Only, Security Update, and ServicingStackUpdate.
The most urgent bug Microsoft addressed this month is CVE-2022-26925, a weakness in a central component of Windows security (the “Local Security Authority” (LSARPC) process within Windows). CVE-2022-26925 has been publicly disclosed and it is now actively being exploited in the wild.
CVE-2022-26925 | Windows LSA Spoofing Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Please note that the combined CVSS score would be 9.8 when this vulnerability is chained with the noted NTLM Relay Attacks on Active Directory Certificate Services (AD CS). Please see ADV210003 Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS) for additional information.
The vulnerability affects Windows 7 through 10 and Windows Server 2008 through 2022. While this vulnerability affects all servers, domain controllers should be prioritized in terms of applying security updates. After applying the security updates, please see KB5005413 for more information on further steps that you need to take to protect your system.
An unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate to the attacker using NTLM. This security update detects anonymous connection attempts in LSARPC and disallows it.
According to the CVSS metric, the attack complexity is high. The attacker must inject themselves into the logical network path between the target and the resource requested by the victim in order to read or modify network communications. This is called a man-in-the-middle (MITM) attack.
Exploitability Assessment: Exploitation Detected
CVE-2022-21978 | Microsoft Exchange Server Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.2/10.
Successful exploitation of this vulnerability requires the attacker to be authenticated to the Exchange Server as a member of a high privileged group.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-22012 and CVE-2022-29130 | Windows LDAP Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
An unauthenticated attacker could send a specially crafted request to a vulnerable server. Successful exploitation could result in the attacker’s code running in the context of the SYSTEM account.
This vulnerability is only exploitable if the MaxReceiveBuffer LDAP policy is set to a value higher than the default value. Systems with the default value of this policy would not be vulnerable. For more information, please see Microsoft’s LDAP policies.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-22017 | Remote Desktop Client Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
An attacker would have to convince a targeted user to connect to a malicious RDP server. Upon connecting, the malicious server could execute code on the victim’s system in the context of the targeted user.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-26913 | Windows Authentication Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 7.4/10.
An attacker who successfully exploited this vulnerability could carry out a Man-in-the-Middle (MITM) attack and could decrypt and read or modify TLS traffic between the client and server. There is no impact to the availability of the attacked machine.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-26923 | Active Directory Domain Services Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
An authenticated user could manipulate attributes on computer accounts they own or manage, and acquire a certificate from Active Directory Certificate Services that would allow elevation of privilege.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-26937 | Windows Network File System Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
This vulnerability could be exploited over the network by making an unauthenticated, specially crafted call to a Network File System (NFS) service to trigger a Remote Code Execution (RCE).
This vulnerability is not exploitable in NFSV4.1. Prior to updating your version of Windows that protects against this vulnerability, you can mitigate an attack by disabling NFSV2 and NFSV3. This may adversely affect your ecosystem and should only be used as a temporary mitigation.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-29108 | Microsoft SharePoint Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
The attacker must be authenticated and possess the permissions for page creation to be able to exploit this vulnerability.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-29133 | Windows Kernel Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
In this case, a successful attack could be performed from a low privilege AppContainer. The attacker could elevate their privileges and execute code or access resources at a higher integrity level than that of the AppContainer execution environment.
Exploitability Assessment: Exploitation Less Likely.
Microsoft Last But Not Least
On April 28, 2022, Microsoft released 36 vulnerabilities for Microsoft Edge (Chromium-based) including CVE-2022-29144 which is classified as important, and CVE-2022-29146 which is classified as moderate. Both flaws are Elevation of Privilege vulnerabilities and have been assigned a CVSSv3.1 score of 8.3/10.
On May 6, 2022, Microsoft Build announced that there are some Site compatibility-impacting changes coming to Microsoft Edge for developers. This article lists differences between the schedule of changes for Microsoft Edge versus the Chromium project, and high-impact changes that the Microsoft Edge team is tracking especially closely.
Notable Adobe Vulnerabilities Patched
Adobe released five advisories with updates to fix 18 vulnerabilities affecting Character Animator, ColdFusion, Framemaker, InCopy, and InDesign. Of these 18 vulnerabilities, 16 are rated as Critical.
APSB22-21 | Security Updates Available for Adobe Character Animator
This update resolves one critical vulnerability.
Adobe Priority: 3
Adobe has released an update for Adobe Character Animator for Windows and macOS. This update resolves a critical vulnerability. Successful exploitation could lead to arbitrary code execution.
APSB22-22 | Security Updates Available for Adobe ColdFusion
This update resolves one important vulnerability.
Adobe Priority: 3
Adobe has released security updates for ColdFusion versions 2021 and 2018. These updates resolve an important vulnerability that could lead to arbitrary code execution.
APSB22-23 | Security Updates Available for Adobe InDesign
This update resolves three critical vulnerabilities.
Adobe Priority: 3
Adobe has released a security update for Adobe InDesign. This update addresses critical vulnerabilities. Successful exploitation could lead to arbitrary code execution.
APSB22-27 | Security Updates Available for Adobe Framemaker
This update resolves nine critical and one important vulnerability.
Adobe Priority: 3
Adobe has released a security update for Adobe Framemaker. This update addresses one important and multiple critical vulnerabilities. Successful exploitation could lead to arbitrary code execution and memory leaks.
APSB22-28 | Security Updates Available for Adobe InCopy
This update resolves three critical vulnerabilities.
Adobe Priority: 3
Adobe has released a security update for Adobe InCopy. This update addresses critical vulnerabilities. Successful exploitation could lead to arbitrary code execution.
About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
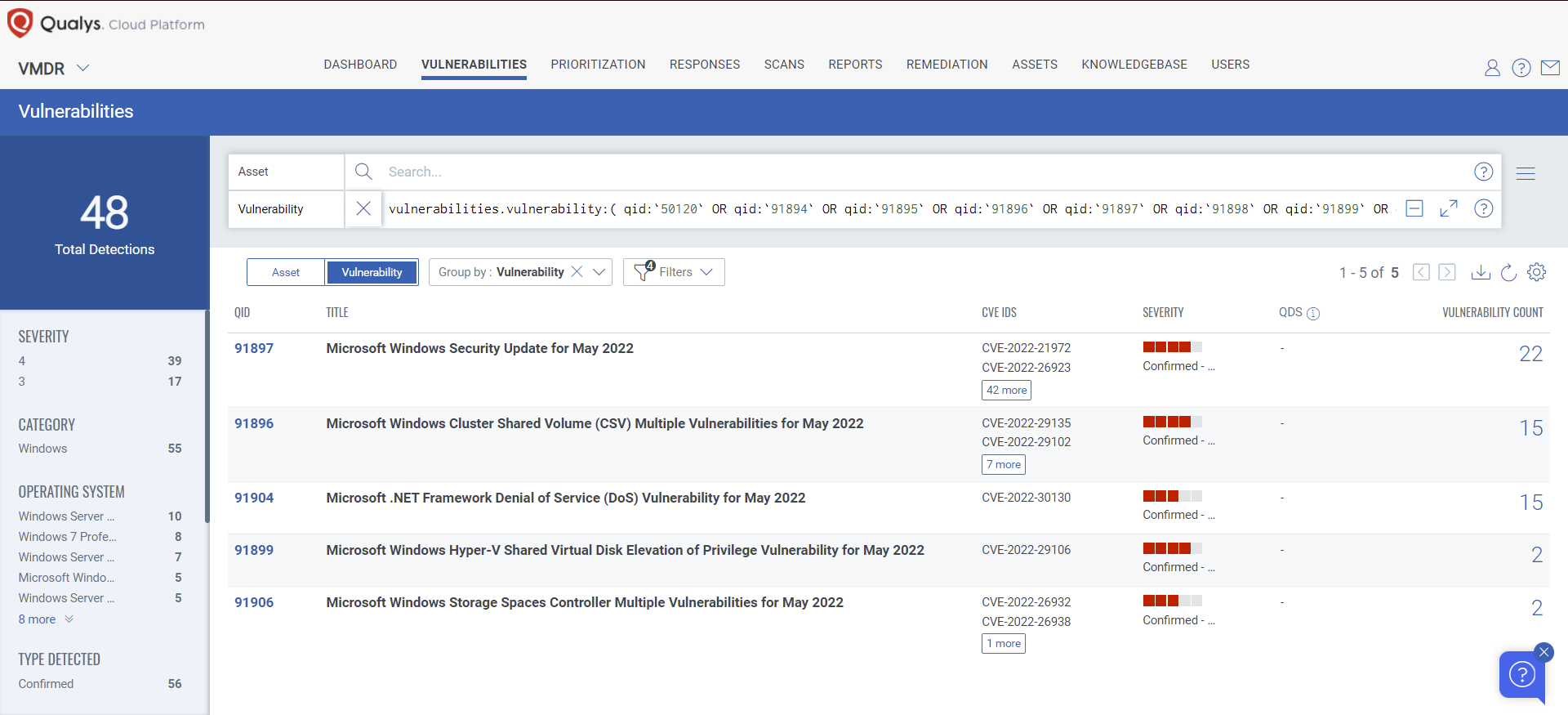
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
( qid:`50120` OR qid:`91894` OR qid:`91895` OR qid:`91896` OR qid:`91897` OR qid:`91898` OR qid:`91899` OR qid:`91900` OR qid:`91901` OR qid:`91903` OR qid:`91904` OR qid:`91905` OR qid:`91906` OR qid:`110407` OR qid:`110408` OR qid:`376584` )
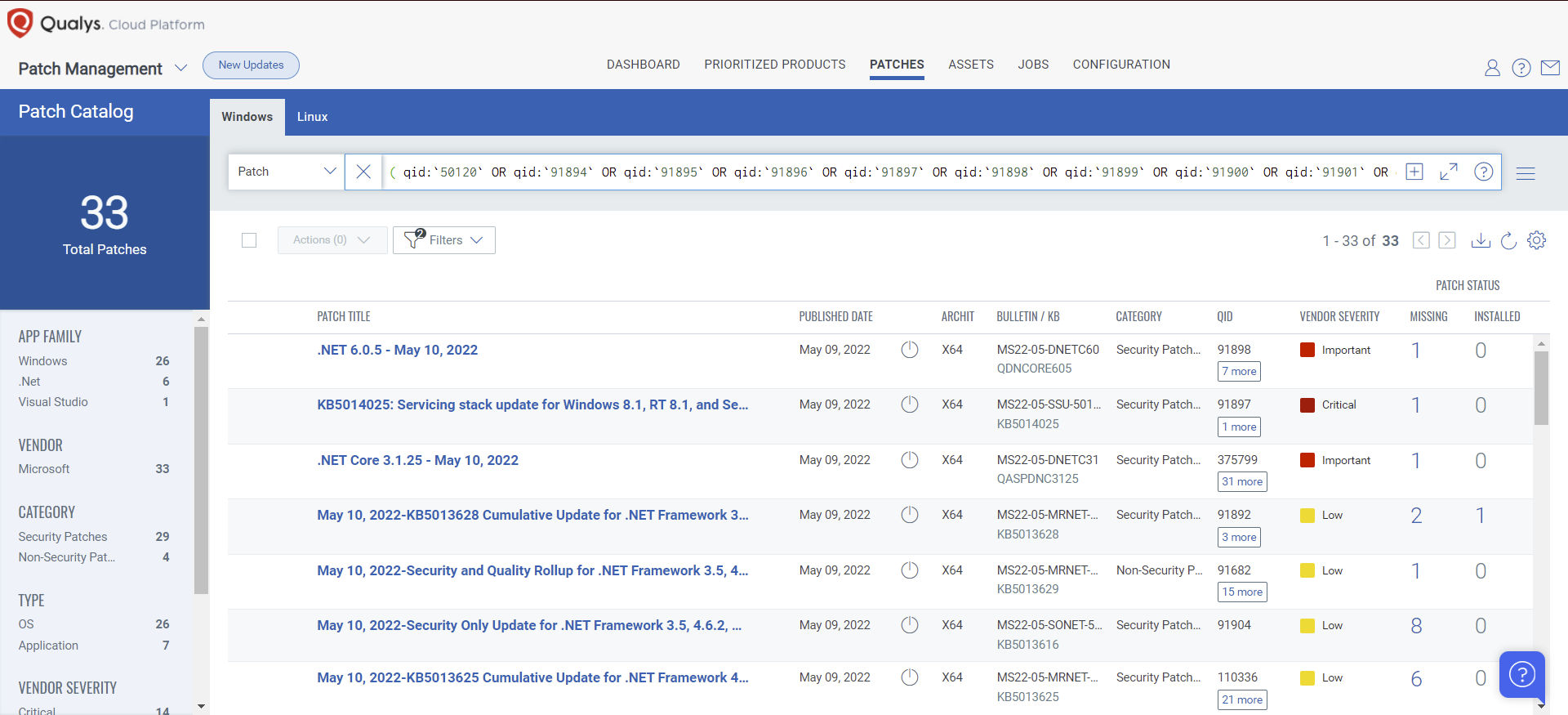
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday:
( qid:`50120` OR qid:`91894` OR qid:`91895` OR qid:`91896` OR qid:`91897` OR qid:`91898` OR qid:`91899` OR qid:`91900` OR qid:`91901` OR qid:`91903` OR qid:`91904` OR qid:`91905` OR qid:`91906` OR qid:`110407` OR qid:`110408` OR qid:`376584` )
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar this Month in Vulnerabilities & Patches
Please Visit Qualys Threat Protection Blog For Additional Information About Microsoft Advisory ADV220001.