GDPR Is Here: Don’t Neglect Public Cloud Security

With organizations aggressively moving workloads to public cloud platforms, such as Amazon’s AWS, protecting these environments is critical for complying with the EU’s General Data Protection Regulation (GDPR).
GDPR, which went into effect in May, imposes strict requirements on millions of businesses worldwide that control and process the personal data of EU residents.
Public cloud platforms are being used to power digital transformation initiatives across many business functions where EU residents’ personal data is likely to be stored, processed and shared.
Thus, organizations need complete visibility into their public clouds, and they must have a solid security and compliance posture in these environments that includes vulnerability management, asset inventory, web app scanning, DevSecOps pipeline protection, and IT configuration controls.
The challenges of public cloud security
It can be difficult to adapt and map on-premises security controls and processes to public clouds, primarily because organizations have less control over their IT assets in these environments.
Organizations also may lack the know-how, processes and tools needed to secure public clouds. This may help explain why so many organizations have left cloud storage buckets unprotected, exposing confidential data publicly on the Internet.
Among the many security and compliance issues faced by organizations moving to the cloud are these “Treacherous 12” that the Cloud Security Alliance (CSA) has identified as the most significant:
- Data Breaches
- Weak Identity, Credential and Access Management
- Insecure APIs
- System and Application Vulnerabilities
- Account Hijacking
- Malicious Insiders
- Advanced Persistent Threats (APTs)
- Data Loss
- Insufficient Due Diligence
- Abuse and Nefarious Use of Cloud Services
- Denial of Service
- Shared Technology Vulnerabilities
For starters, it’s key to understand that public cloud platform providers operate on a “shared security responsibility” model: The burden is split between them and their customers.
These vendors take care of the security of the cloud. Customers, in turn, are responsible for defining their controls to protect their data and software on these platforms.
As more and more business units move workloads to the cloud, InfoSec teams lose sight of who’s doing what, and what resources they’re using. This problem gets compounded if the organization is using cloud platforms from more than one vendor.
A November 2017 SANS Institute survey of organizations using public cloud services found that only 17% of them had one provider. Almost 41% were using two or three providers, and 23% were using between four and six, according to the report, titled “Cloud Security: Defense In Detail If Not In Depth.”
Once InfoSec teams have clarity into these public cloud workloads, they often discover that their traditional security and compliance toolsets aren’t effective for monitoring and protecting these environments.
“Traditional perimeter-based security tools do little to protect cloud workloads,” Jennifer Adams, senior forecast analyst at Forrester, writes.
Specifically, security teams should look at products born in the cloud and designed specifically with these environments in mind.
“Securing new cloud infrastructure with old processes and controls is simply a recipe for failure,” Enterprise Strategy Group’s Jon Oltsik writes.
This becomes especially evident when InfoSec teams are called upon to embed security tools and processes transparently into DevOps CI/CD (continuous integration and delivery) pipelines, so that security and compliance tasks are automated throughout the software lifecycle.
“Security professionals will be looking for cloud security technology architectures capable of handling hybrid cloud security, integrating with DevOps tools, and scaling to meet enterprise needs,” Oltsik writes.
Qualys has got you covered
Qualys provides a full set of security and compliance solutions for public cloud hosts and instances, including vulnerability management, policy compliance, file integrity monitoring and web application scanning. These solutions can help you meet your obligations in the “shared security responsibility model” of public cloud platform vendors by letting you do such tasks as:
- Identify, classify, and monitor assets and vulnerabilities
- Comply with internal and external policies
- Prioritize vulnerability remediation
- Automatically find and eradicate malware infections on your websites
- Integrate and automate security and compliance throughout your DevOps pipelines
Securing cloud workloads
Qualys provides vulnerability management, policy compliance, and web application security for cloud hosts deployed across AWS, Azure and GCP.
Qualys collects complete metadata information for these deployments. For AWS environments, the Qualys Connector for Amazon continuously discovers Amazon EC2 and VPC assets using an Amazon API integration. Connectors may be configured to connect to one or more Amazon accounts with user-provided, read-only credentials. That way, they can automatically detect and synchronize changes to virtual machine instance inventories from all Amazon EC2 Regions and Amazon VPCs.
Users can get complete vulnerability analysis for cloud hosts via internal and external scanning, covering vulnerability detections for internal hosts and also the hosts that are exposed at the perimeter.
Qualys virtual scanner appliances are available to be deployed directly from the marketplaces into the clouds’ virtual private networks, and they are pre-authorized. Users can avoid signing up a penetration testing for AWS by using the pre-authorized scanner appliance.
The lightweight Qualys Cloud Agents can be easily deployed across the cloud hosts either during creation, or they can be baked into the AMI/Image to ease distribution and deployment.
With Azure, Qualys has a special integration where Cloud Agent deployments are also deeply integrated into Azure Security Center – a unified security management and monitoring console – making it possible to detect Azure virtual machines and deploy Qualys Cloud Agents in bulk to them. The agents gather vulnerability data and send it to the Qualys Cloud Platform, which in turn, provides vulnerability and system health monitoring data back to Azure Security Center.
Securing cloud infrastructure
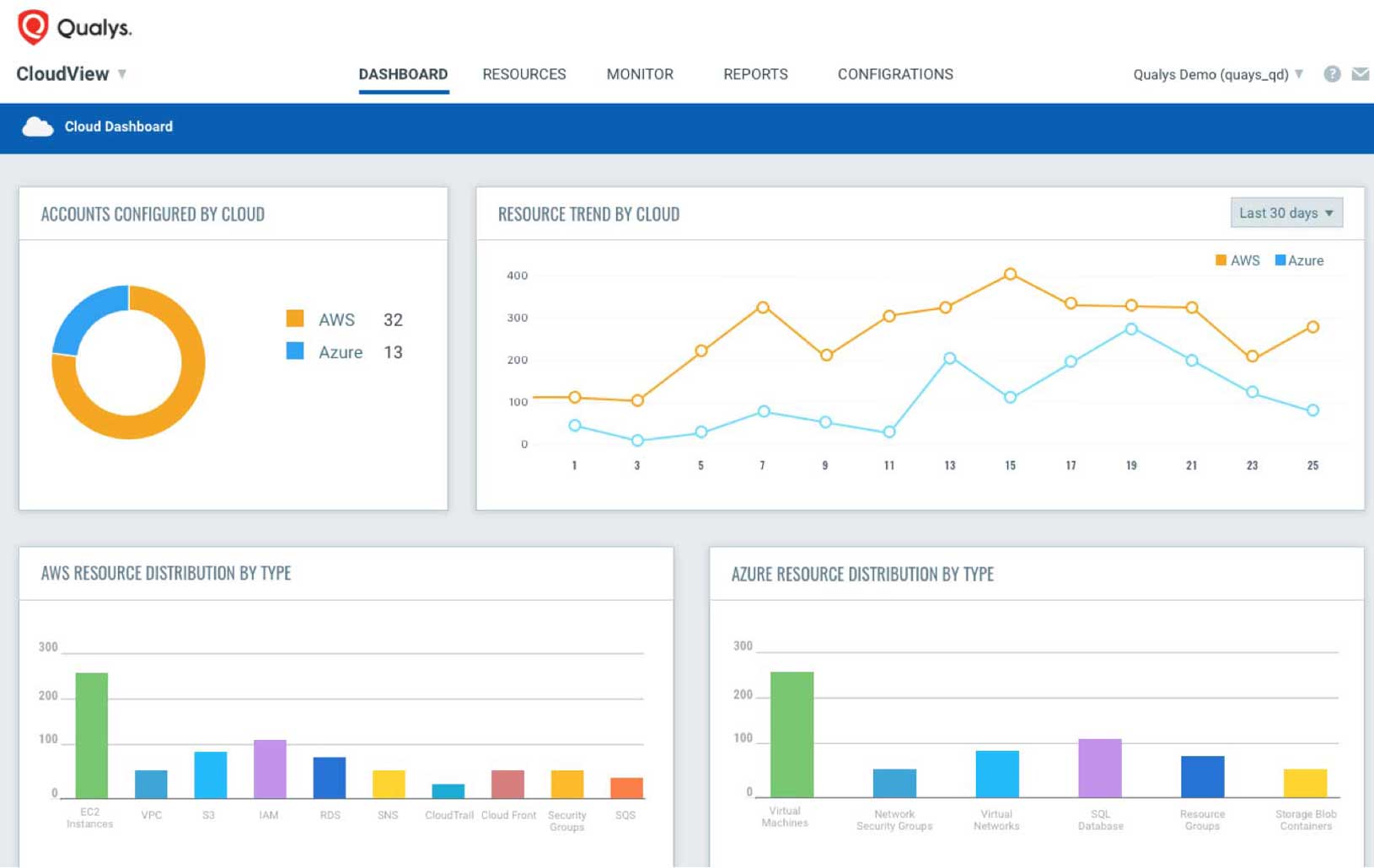
Qualys also has new apps for protecting public cloud environments beyond the host’s operating system and applications: Cloud Inventory and Cloud Security Assessment.
Cloud Inventory provides you with continuous inventory of resources and assets across public cloud platforms. Its features include:
- Discovery and inventory of assets
Qualys Cloud Inventory continuously discovers and tracks assets and resources such as instances and virtual machines, storage buckets, databases, security groups, ACLs, ELBs, and users, across all regions, multiple accounts and multiple cloud platforms. You can view all this information in one central place.
- Comprehensive, multi-faceted searches
You can use Qualys Cloud Inventory’s fast and powerful search engine to look for assets and discover their threat posture based on their attributes and relationships. The search engine lets you find leaky storage buckets, ungoverned instance spin ups, and instances scheduled for retirement. You can also do complex lookups to identify assets that are at greater risk of attack.
- Quick and easy setup
Qualys Cloud Inventory can be set up in less than 5 minutes, without the need to deploy agents or configure anything. Using the cloud providers’ APIs, Qualys Cloud Inventory connectors collect data from your accounts without disrupting your workloads.
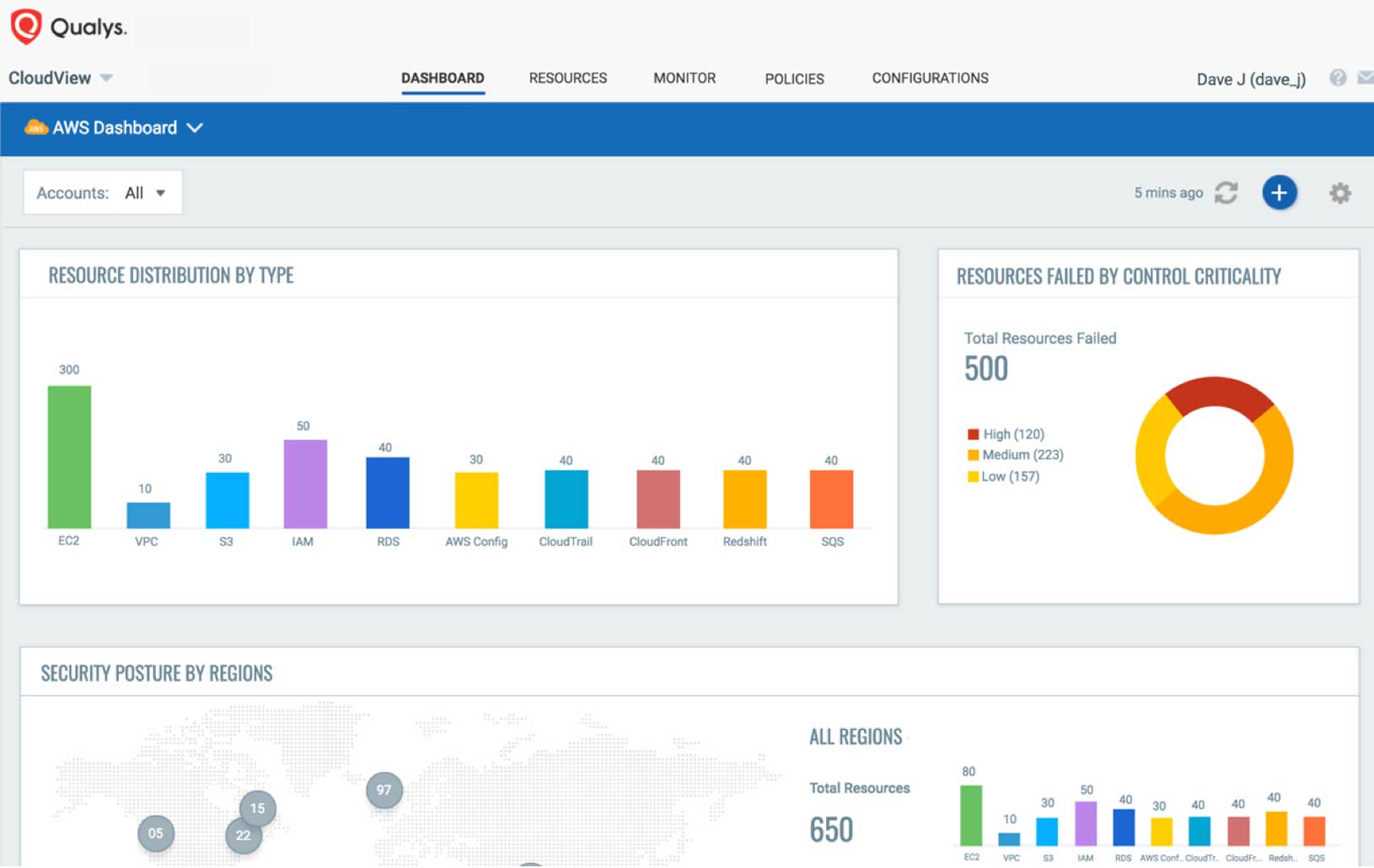
Meanwhile, Cloud Security Assessment continuously monitors and assesses your cloud assets and resources for misconfigurations and non-standard deployments.
Its features include:
- Complete view of your cloud security posture
Qualys Cloud Security Assessment gives you an “at-a-glance” comprehensive picture of your cloud inventory, the location of assets across global regions, and full visibility into the public cloud security posture of all assets and resources. It provides a quick overview of inventory and security posture via dashboards, and lets you personalize or build your own with custom widgets based on queries or on other criteria, such as “Top 10 accounts based on failures” and “Top 10 controls that are failing.”
- Continuous security checks
Qualys Cloud Security Assessment runs continuous security checks on your cloud assets and resources. The data is quickly synchronized for new and updated assets. The analysis provides clear evidence of security and compliance issues, and offers remediation methods to mitigate issues.
- Automated security using REST APIs
Qualys Cloud Security Assessment fully supports REST APIs for seamless integration with the CI/CD tool chain, providing DevSecOps teams with real-time assessments of potential risks and exposures, so that they can mitigate risks before deploying apps into production. This also enables integration with GRC, SIEM, and ticketing service providers to help InfoSec teams automate process threats and remediation.
Qualys Container Security
Qualys also recently launched Container Security, an app for protecting their container deployments and DevOps processes. It lets organizations integrate results into one unified view, breaking down silos and lowering ownership cost.
Qualys Container Security features include:
- Visibility into container projects: Qualys CS provides auto-discovery that gives customers complete visibility of container hosts wherever they are within their global IT environment via dynamic, customizable dashboards.
- Security for full DevOps pipeline: Security teams can block images with specific vulnerabilities, or vulnerabilities above a severity threshold. DevOps teams can perform continuous vulnerability detection and remediation with plugins for CI/CD tools, or via REST APIs.
- Threat identification, impact assessment and remediation prioritization: Teams can search for images with high-severity vulnerabilities, unapproved packages, and older or test release tags. They can assess the impact by identifying all containers using unapproved, vulnerable images.
- Container runtime protection: CS helps teams scan, protect and secure their running containers. Customers can also detect runtime security and configuration drift that breaks the parent image’s immutable behavior by using a different vulnerability posture and software configuration.
In short, with Qualys, you’ll be able to secure your public cloud infrastructure and your DevOps pipelines, so you’ll reduce your risks of data breaches that would put you in non-compliance with GDPR.
In our next post, we’ll wrap up this blog series by outlining business benefits you can derive from your GDPR compliance efforts.
(Hari Srinivasan is a Director of Product Management at Qualys.)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
GDPR Is Here: Assess Risk from Vendors and from Internal Teams
GDPR Is Here: Assess the Security Configurations of Your IT Systems
GDPR Is Here: Put File Integrity Monitoring in Your Toolbox
GDPR Is Here: Indication of Compromise: Another Key Practice for GDPR Compliance
GDPR Is Here: Web App Security Is a Must