GDPR 101: Monitoring & Maintaining Compliance After the Deadline
Discussions about the EU’s General Data Protection Regulation (GDPR) reached a crescendo on May 25, the compliance deadline, but many companies continue seeking guidance.
The reason: A majority of companies missed the deadline, according to estimates from various sources, including Gartner, Crowd Research, IDC, Spiceworks, TrustArc, and Ponemon Institute, so it’s very likely that millions are still working on GDPR compliance.
Although GDPR has been in effect for months, “it’s clear that many organizations lack such a strategy or the tools needed to effectively protect sensitive data and maintain privacy and protection,” Gartner analyst Deborah Kish said in August.
To help companies still in the process of meeting the regulation’s requirements, the IT GRC Forum recently held a webcast titled “GDPR 101: Monitoring & Maintaining Compliance After the Deadline.” The webcast’s panelists included Qualys expert Tim White, who spoke about the importance of managing vendor risk and leveraging a control framework.

White explained that IT security is a small yet key subset of GDPR. “The need to protect the privacy of the information, to prevent accidental or intentional disclosure, is a critical sub-component,” he said.
It’s also important to know that GDPR offers vague, general requirements for IT security, unlike other industry mandates and regulations that are very specific and prescriptive in this regard, said White, Qualys’ Director of Product Management for Policy Compliance.
“In GDPR, you’ve got to implement a good security program and apply the appropriate technical compensating and procedural controls to do due diligence to protect the information privacy,” he said.
The best way to achieve this is by leveraging a technical control framework, like the Center for Internet Security’s (CIS) Critical Security Controls or the National Institute for Standards and Technology’s (NIST) 800-53 controls.
“It’s really important to make sure you have comprehensive coverage of all aspects of IT security, including vulnerability management, configuration management and patching, as well as all appropriate detection and preventative controls at the network layers,” White said.
“Implementing a control framework will ensure that you have all the appropriate coverage in place and that you can demonstrate that coverage,” he added.
White also addressed vendor risk management. GDPR holds an organization liable when its customer data is compromised during a breach suffered by one of its third parties, like a vendor or partner.
 “You need to make sure that whatever you do internally for your organization, that you expect that of your vendors as well. Vendor risk management is a huge component of GDPR,” White said.
“You need to make sure that whatever you do internally for your organization, that you expect that of your vendors as well. Vendor risk management is a huge component of GDPR,” White said.
This means spelling out GDPR-compliance requirements in your vendor contracts, including the provision of a variety of audit data and the adoption of necessary controls, and holding these third-parties accountable when they violate the terms.
“That end-to-end lifecycle management of vendor risk is really critical,” he said. “You’re ultimately responsible as the data owner to make sure your vendors are meeting GDPR requirements.”
You can listen to a recording of the webcast, where White and the other panel experts covered topics including:
- The latest techniques to protect data and remediate breaches.
- How GDPR can support your corporate values and drive business value for customers and partners.
- What your organization needs to uncover data risks and avoid fines.
- How technology can enable continuous monitoring, maintenance, and demonstration of GDPR compliance, in an ongoing and efficient manner.
How Qualys can help
Qualys offers an integrated suite of Cloud Apps that span a broad array of security and compliance functions, and can thus help with multiple elements of GDPR compliance.
For example, the Qualys Vulnerability Management (VM) and Threat Protection (TP) apps can help you continuously detect vulnerabilities, and prioritize their remediation, while Qualys Policy Compliance lets you track and validate access to files and databases where protected data is stored and analyzed. Qualys Security Assessment Questionnaire (SAQ) helps organizations automate and streamline the process of collecting information about EU residents’ data from both internal teams and external third parties.
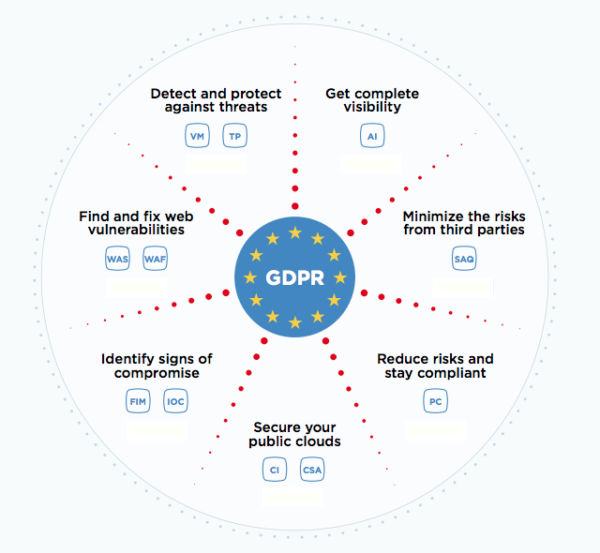
The Qualys Cloud Platform, which powers the Cloud Apps, provides end-to-end prevention and response capabilities. Its cloud-based architecture, with its software-as-a-service (SaaS) delivery and licensing model, slashes the costs and complexity associated with on-premises software.
The platform offers customers ease of deployment and scalability, and provides continuous assessment of their security and compliance posture, with instant visibility across all IT assets, wherever they reside. It gives customers the scale, flexibility, agility and versatility required for protecting the hybrid, distributed IT environments that support organizations’ digital transformation efforts.
The platform’s massively scalable backend has centralized capabilities for reporting, storage, data analysis, search indexing and asset tagging, among other functionality. IT, security and compliance data is collected using a variety of sensors – including physical, virtual and cloud appliances, and lightweight agents – that are always on, remotely deployable, centrally managed and self-updating, enabling true distributed scanning and monitoring.
A centralized, web-based, single-pane-of-glass UI gives organizations a complete and continuously updated view of their IT environment’s security and compliance posture.
With Qualys, you will be able to do the end-to-end management of your GDPR readiness from a security and compliance perspective.
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
- GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
- GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
- GDPR Is Here: Assess Risk from Vendors and from Internal Teams
- GDPR Is Here: Assess the Security Configurations of Your IT Systems
- GDPR Is Here: Put File Integrity Monitoring in Your Toolbox
- GDPR Is Here: Indication of Compromise: Another Key Practice for GDPR Compliance
- GDPR Is Here: Web App Security Is a Must
- GDPR Is Here: Don’t Neglect Public Cloud Security