October 2022 Patch Tuesday | Microsoft Releases 84 Vulnerabilities With 13 Critical, Plus 12 Microsoft Edge (Chromium-Based); Adobe Releases 4 Advisories, 29 Vulnerabilities With 17 Critical.
Table of Contents
- Microsoft Patch Tuesday Summary
- Microsoft Exchange ProxyNotShell Zero-Days Not Yet Addressed (QID 50122)
- The October 2022 Microsoft Vulnerabilities Are Classified As Follows:
- Two Zero-Day Vulnerabilities Addressed
- Microsoft Critical Vulnerability Highlights
- Microsoft Release Summary
- Microsoft Edge | Last But Not Least
- Adobe Security Bulletins and Advisories
- About Qualys Patch Tuesday
- Qualys Threat Research Blog Posts
- Qualys Threat Protection High-Rated Advisories
- Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response(VMDR)
- Rapid Response With Patch Management (PM)
- EXECUTE Mitigation Using Custom Assessment and Remediation (CAR)
- EVALUATE Vendor-Suggested Mitigation With Policy Compliance (PC)
- This Month in Vulnerabilities and Patches Webinar Series
- UPCOMING EVENTS
- WEBINAR
- Qualys Threat Thursdays
- CONFERENCES
- Qualys Annual Security Conference #QSC22
- We Are Pleased To Announce the Keynote Speaker for the 2022 Qualys Annual Security Conference in Las Vegas
- Live Training Sessions
- Live Conference Sessions
- #QSC22 Location and Reservation Information
- This Months Blog Content Is the Result of Collaboration With and Contributions From:
Microsoft Patch Tuesday Summary
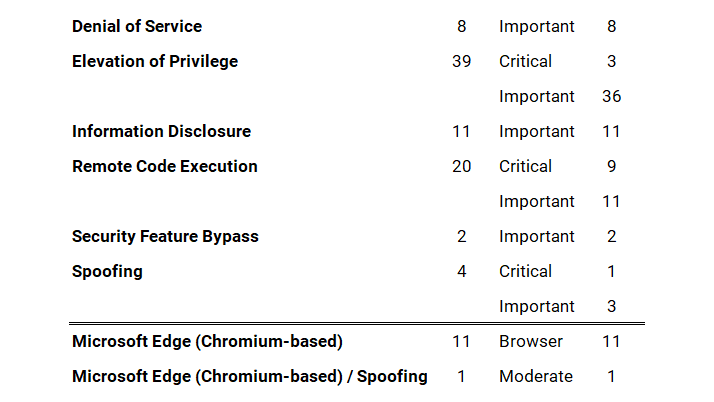
Microsoft has fixed 84 vulnerabilities (aka flaws) in the October 2022 update, including 13 vulnerabilities classified as critical as they allow Elevation of Privilege (EoP), Remote Code Execution (RCE), and Spoofing. This month’s Patch Tuesday fixes two zero-day vulnerabilities, with one actively exploited in attacks (CVE-2022-41033*, CVE-2022-41043). Earlier this month, on October 3 and 6, 2022, Microsoft also released a total of 12 Microsoft Edge (Chromium-Based) updates, one (1) addressing Spoofing (CVE-2022-41035) ranked moderate.
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, Spoofing, Microsoft Edge (Chromium-based), and Microsoft Edge (Chromium-based) / Spoofing.
Microsoft Exchange “ProxyNotShell” Zero-Days Not Yet Addressed (QID 50122)
Unfortunately, Microsoft has not released security updates to address ProxyNotShell which includes two actively exploited zero-day vulnerabilities tracked as CVE-2022-41040 and CVE-2022-41082.
Released: October 2022 Exchange Server Security Updates provides the following update:
NOTE: The October 2022 SUs do not contain fixes for the zero-day vulnerabilities reported publicly on September 29, 2022 (CVE-2022-41040 and CVE-2022-41082). Please see this blog post to apply mitigations for those vulnerabilities. We will release updates for CVE-2022-41040 and CVE-2022-41082 when they are ready.
Ankit Malhotra, Manager, Signature Engineering suggests, “It’s worth noting that Microsoft has had to revise the mitigation for CVE-2022-41040 more than once, as the suggested URL rewrite Mitigation was bypassed multiple times. Organizations that reacted to the ProxyShell vulnerability should also pay close attention to this, taking their lessons learned on rapid remediation, as this vulnerability can potentially see increased exploitation.”
- Qualys Response to ProxyNotShell Microsoft Exchange Server Zero-Day Threat Using Qualys Cloud Platform | QUALYS BLOG
The October 2022 Microsoft Vulnerabilities Are Classified As Follows:
Two Zero-Day Vulnerabilities Addressed
A vulnerability is classified as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
CVE-2022-41033 | Windows COM+ Event System Service Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
Classified as critical, this issue affects an unknown function of the component COM+ Event System Service. The impact of exploitation is loss of confidentiality, integrity, and availability.
Microsoft has not disclosed how the vulnerability is being exploited or if it is being exploited in targeted or more widespread attacks. They only say that the attack complexity is low and that it requires no user interaction for the attacker to be able to achieve SYSTEM privileges.
An attacker who successfully exploited this vulnerability could gain system privileges.
Patch Installation should be considered critical.
Saeed Abbasi, Manager, Vulnerability Signatures adds, “This patch fixes a security vulnerability that Microsoft stated is under active attack. However, it is not clear how severe these attacks are. Due to the nature of this vulnerability, a privilege escalation that often engages some social engineering (e.g. requiring the user to open a malicious attachment), history shows that it potentially needs to be chained with a code execution bug to exploit.”
Exploitability Assessment: Exploitation Detected
CVE-2022-41043 | Microsoft Office Information Disclosure Vulnerability
This vulnerability has a CVSSv3.1 score of 3.3/10.
The type of information that could be disclosed if an attacker successfully exploited this vulnerability is user tokens and other potentially sensitive information. The impact of exploitation is loss of confidentiality.
This vulnerability demands that the victim is doing some kind of user interaction. As of the time of publishing, neither technical details nor an exploit is publicly available.
Exploitability Assessment: Exploitation Less Likely
Microsoft Critical Vulnerability Highlights
CVE-2022-37968 | Azure Arc-Enabled Kubernetes Cluster Connect Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 10/10.
Microsoft has identified a vulnerability affecting the cluster connect feature of Azure Arc-enabled Kubernetes clusters. This vulnerability could allow an unauthenticated user to elevate their privileges and potentially gain administrative control over the Kubernetes cluster. Additionally, because Azure Stack Edge allows customers to deploy Kubernetes workloads on their devices via Azure Arc, Azure Stack Edge devices are also vulnerable to this vulnerability.
Customers using Azure Stack Edge must update to the 2209 release (software version 2.2.2088.5593). Release notes for the 2209 release of Azure Stack Edge can be found here: Azure Stack Edge 2209 release notes.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-37976 | Active Directory Certificate Services Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
A malicious DCOM client could coerce a DCOM server to authenticate to it through the Active Directory Certificate Service (ADCS) and use the credential to launch a cross-protocol attack.
An attacker who successfully exploited this vulnerability could gain domain administrator privileges.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-41038 | Microsoft SharePoint Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
In a network-based attack, an authenticated attacker with Manage List permissions could execute code remotely on the SharePoint Server.
The attacker must be authenticated to the target site, with permission to use Manage Lists within SharePoint.
NOTE: Customers running SharePoint Server 2013 Service Pack 1 can install the cumulative update or the security update, which is the same update as for Foundation Server 2013.
Exploitability Assessment: Exploitation More Likely
CVE-2022-38048 | Microsoft Office Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
The word remote in the title refers to the location of the attacker. This type of exploit is sometimes referred to as Arbitrary Code Execution (ACE). The attack itself is carried out locally.
When a particular vulnerability allows an attacker to execute “arbitrary code”, it typically means that the bad guy can run any command on the target system the attacker chooses. Source
For example, when the score indicates that the Attack Vector is Local and User Interaction is Required, this could describe an exploit in which an attacker, through social engineering, convinces a victim to download and open a specially crafted file from a website which leads to a local attack on their computer. The impact of exploitation is loss of confidentiality, integrity, and availability.
NOTE: Customers should apply all updates offered for the software installed on their systems. If multiple updates apply, they can be installed in any order.
Exploitability Assessment: Exploitation More Likely
CVE-2022-34689 | Windows CryptoAPI Spoofing Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
An attacker could manipulate an existing public x.509 certificate to spoof their identify and perform actions such as authentication or code signing as the targeted certificate.
The technical details are unknown, and an exploit is not publicly available. The impact is known to affect integrity.
Exploitability Assessment: Exploitation More Likely
Microsoft Release Summary
This month’s Release Notes cover multiple Microsoft product families, including Azure, Browser, Developer Tools, Extended Security Updates (ESU), Microsoft Office, System Center, and Windows.
A total of 78 unique Microsoft products/versions are affected, including but not limited to .NET and .NET Core, Azure Arc-enabled Kubernetes cluster, Azure Service Fabric Explorer, Azure Stack Edge, Azure StorSimple 8000 Series, Jupyter Extension for Visual Studio Code, Microsoft 365 Apps for Enterprise, Microsoft Edge (Chromium-based), Microsoft Malware Protection Engine, Microsoft Office, Microsoft SharePoint Enterprise Server, Microsoft SharePoint Foundation, Microsoft SharePoint Server, Microsoft Visual Studio, Visual Studio and Visual Studio Code, Windows Desktop, and Windows Server.
Downloads include Cumulative Updates, Monthly Rollups, Security Only, and Security Updates.
Microsoft Edge | Last But Not Least
Earlier in October 2022, Microsoft released Microsoft Edge (Chromium-based) vulnerabilities including CVE-2022-41035. The vulnerability assigned to the CVE is in the Chromium Open Source Software (OSS) which is consumed by Microsoft Edge. It is being documented in the Security Update Guide to announce that the latest version of Microsoft Edge (Chromium-based) is no longer vulnerable. For more information, please see Security Update Guide Supports CVEs Assigned by Industry Partners.
CVE-2022-41035 | Microsoft Edge (Chromium-based) Spoofing Vulnerability
This vulnerability has a CVSSv3.1 score of 8.3/10.
In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerability. However, an attacker would have no way to force the user to visit the website. Instead, an attacker would have to convince the user to click a link, typically by way of an enticement in an email or Instant Messenger message, and then convince the user to open the specially crafted file.
Per Microsoft severity guidelines, the amount of user interaction or preconditions required to allow this sort of exploitation downgraded the severity. The CVSS scoring system doesn’t allow for this type of nuance. Severity: Moderate
Exploitability Assessment: Exploitation Less Likely
Did you know? Microsoft Security Response Center (MSRC) | Improvements in Security Update Notifications Delivery – And a New Delivery Method.
Adobe Security Bulletins and Advisories
Adobe released four (4) security bulletins and advisories with updates to fix 29 vulnerabilities affecting Adobe ColdFusion, Adobe Reader, Adobe Commerce, and Adobe Dimension applications. Of these 29 vulnerabilities, 17 are rated as critical, ten (10) are rated as Important and two (2) are rated as moderate; ranging in severity from a CVSS score of 4.4/10 to 10/10, as summarized below.
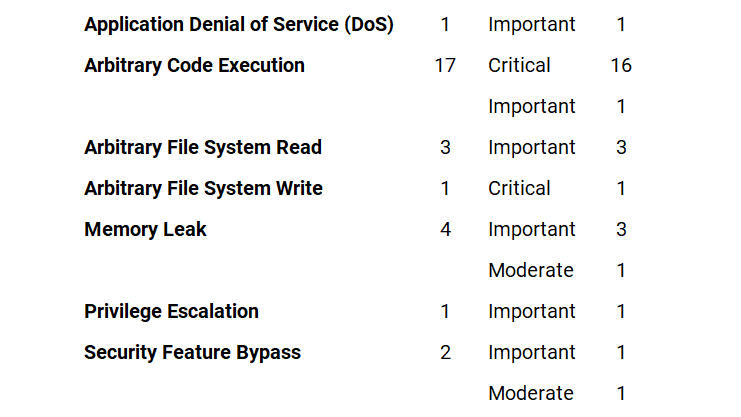
APSB22-42 | Security Updates Available for Adobe ColdFusion
This update resolves six critical, six important, and one moderate vulnerability.
Adobe Priority: 3
Adobe has released security updates for ColdFusion versions 2021 and 2018. These updates resolve Critical, Important, and Moderate vulnerabilities that could lead to arbitrary code execution, arbitrary file system write, security feature bypass, and privilege escalation.
APSB22-46 | Security Update Available for Adobe Acrobat and Reader
This update resolves two critical, and two important vulnerabilities.
Adobe Priority: 3
Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. These updates address critical and important vulnerabilities. Successful exploitation could lead to application denial-of-service and memory leak.
APSB22-48 | Security update available for Adobe Commerce
This update resolves two critical, and two important vulnerabilities.
Adobe Priority: 3
Adobe has released a security update for Adobe Commerce and Magento Open Source. This update resolves a critical vulnerability. Successful exploitation could lead to arbitrary code execution.
APSB22-57 | Security updates available for Adobe Dimension
This update resolves eight critical, and one moderate vulnerability.
Adobe Priority: 3
Adobe has released an update for Adobe Dimension. This update addresses critical and moderate vulnerabilities. Successful exploitation could lead to arbitrary code execution and memory leak in the context of the current user.
About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by Noon on Wednesday.
Qualys Threat Research Blog Posts
Published in the Last 30 days; Most Recent First
- NSA Alert: Topmost CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors
- Qualys Response to ProxyNotShell Microsoft Exchange Server Zero-Day Threat Using Qualys Cloud Platform
Qualys Threat Protection High-Rated Advisories
Published between September 14 – October 12, 2022, Most Recent First
- Microsoft Patch Tuesday, October 2022 Edition: 84 Vulnerabilities patched including 12 Microsoft Edge (Chromium-Based), 2 Zero-days, and 13 Rated as Critical
- Zimbra Collaboration Suite Remote Code Execution Vulnerability (CVE-2022-41352)
- FortiGate and FortiProxy Authentication Bypass Vulnerability on Administrative Interface (HTTP/HTTPS) (CVE-2022-40684)
- Microsoft Exchange Server Zero-day Vulnerabilities (CVE-2022-41040 and CVE-2022-41082) (ProxyNotShell)
- Sophos Firewall Remote Code Execution Vulnerability (CVE-2022-3236)
- Zoho ManageEngine PAM360, Access Manager Plus, and Password Manager Pro Remote Code Execution Vulnerability (CVE-2022-35405)
- Trend Micro Patches Multiple Vulnerabilities in Apex One (On-Premise) Including One Zero-day (CVE-2022-40139)
- Cisco Patched Multiple Vulnerabilities in Multiple Products including NVIDIA Data Plane Development Kit
- Apple Patches Multiple Vulnerabilities in macOS Big Sur and macOS Monterey including One Zero-day (CVE-2022-32894)
- Microsoft Patches Vulnerabilities 79 including 16 Microsoft Edge (Chromium-Based); with 2 Zero-days and 5 Critical in Patch Tuesday, September 2022 Edition
Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its KnowledgeBase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
- In-Depth Look Into Data-Driven Science Behind Qualys TruRisk
- Qualys VMDR Recognized as Best VM Solution by SC Awards 2022 & Leader by GigaOm
- A Deep Dive into VMDR 2.0 with Qualys TruRisk™
Free Trial
Get started with 30-day Free Trial
Rapid Response With Patch Management (PM)
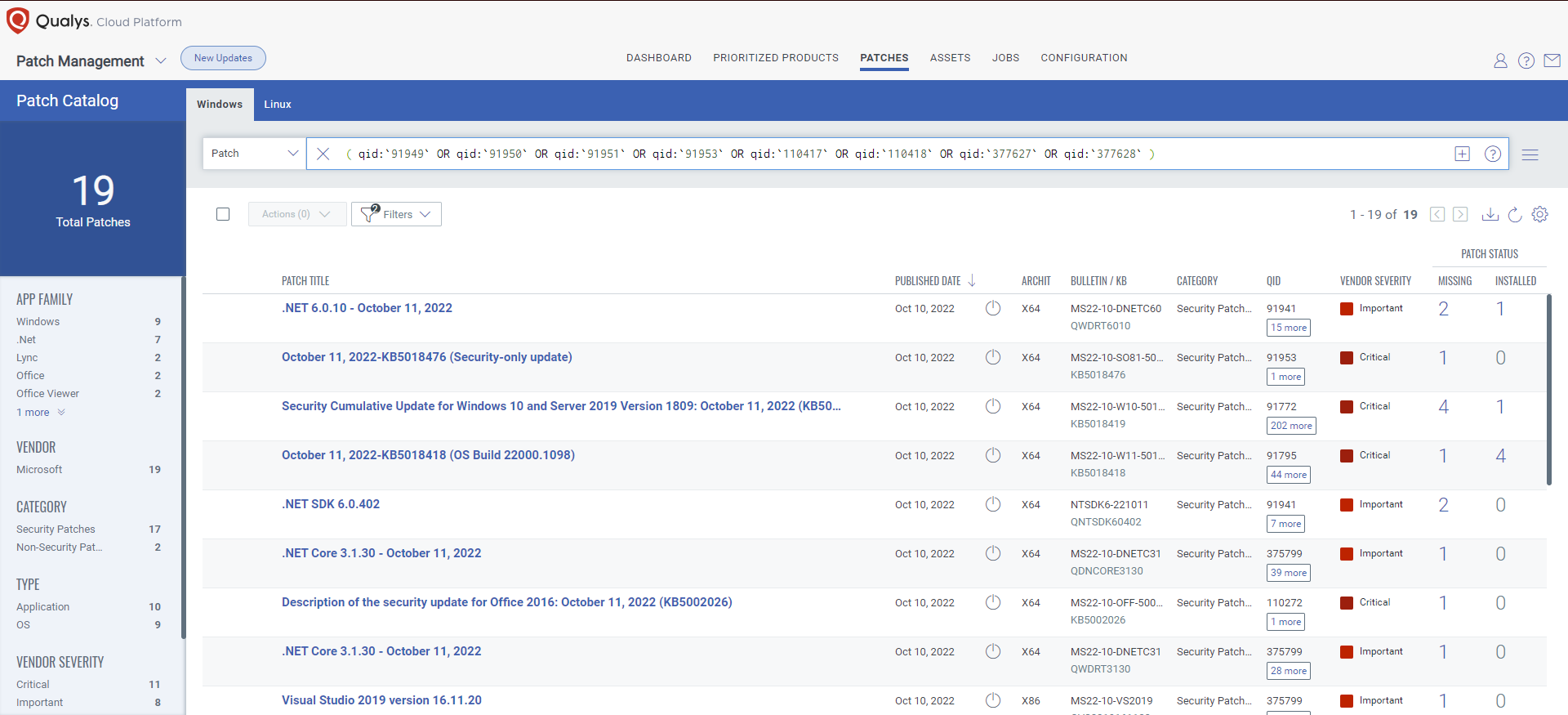
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
- Why Organizations Struggle with Patch Management (and What to Do about It)
- Let Smart Automation Reduce the Risk of Zero-Day Attacks on Third-Party Applications
- Risk-based Remediation Powered by Patch Management in Qualys VMDR 2.0
EXECUTE Mitigation Using Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation empowers a system administrator to quickly and easily perform configuration updates on your technology infrastructure when the current situation requires the implementation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
Customers can perform the provided mitigation steps by creating a PowerShell script and executing the script on vulnerable assets.
IMPORTANT: Scripts tend to change over time. Referring back to a portion of our quote from Ankit Malhotra at the top of this blog, “It’s worth noting that Microsoft has had to revise the mitigation for CVE-2022-41040 more than once, as the suggested URL rewrite Mitigation was bypassed multiple times.” Please refer to the Qualys GitHub Tuesday Patch link to ensure the most current version of a given Patch Tuesday script is in use.
Related Blog Content
- Zimbra Collaboration Suite Remote Code Execution Vulnerability (CVE-2022-41352)
- Remediate Your Vulnerable Lenovo Systems with Qualys Custom Assessment and Remediation
CVE-2022-37976 | Active Directory Certificate Services Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
Exploitability Assessment: Exploitation Less Likely
GitHub Link for CVE-2022-37976 Script
$ServiceName = "CertSvc" $ServiceStatus = (Get-Service -Name $ServiceName).status if($ServiceStatus -eq "Running") { reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\" /v LegacyAuthenticationLevel /t REG_DWORD /d '5' /f | Out-Null if($?) { Write-Host "ADCS found running. LegacyAuthenticationLevel is set to 5. Mitigation for CVE-2022-37976 has been applied as per MSRC guidelines. " } else { Write-Host "command failed" } } else { Write-Host "ADCS not running. No action required" }

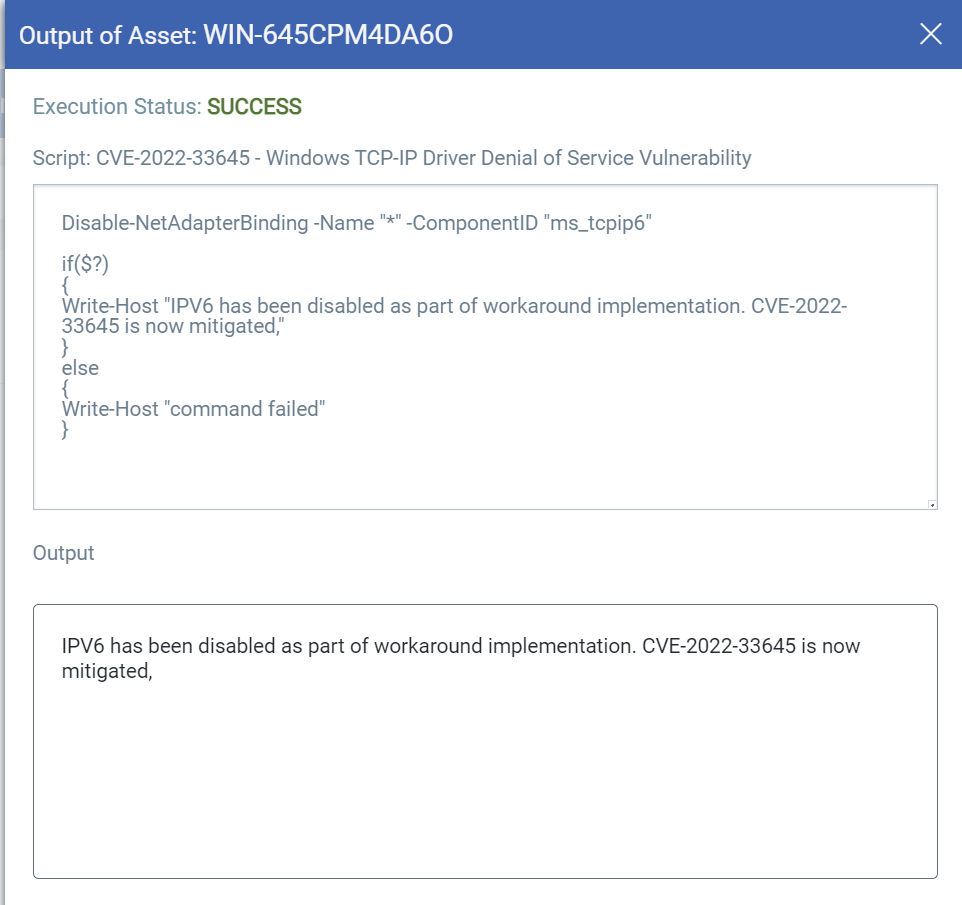
CVE-2022-33645 | Windows TCP/IP Driver Denial of Service (DoS) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
Exploitability Assessment: Exploitation Less Likely
GitHub Link for CVE-2022-33645 Script
Disable-NetAdapterBinding -Name "*" -ComponentID "ms_tcpip6" if($?) { Write-Host "IPV6 has been disabled as part of workaround implementation. CVE-2022-33645 is now mitigated," } else { Write-Host "command failed" }
EVALUATE Vendor-Suggested Mitigation With Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
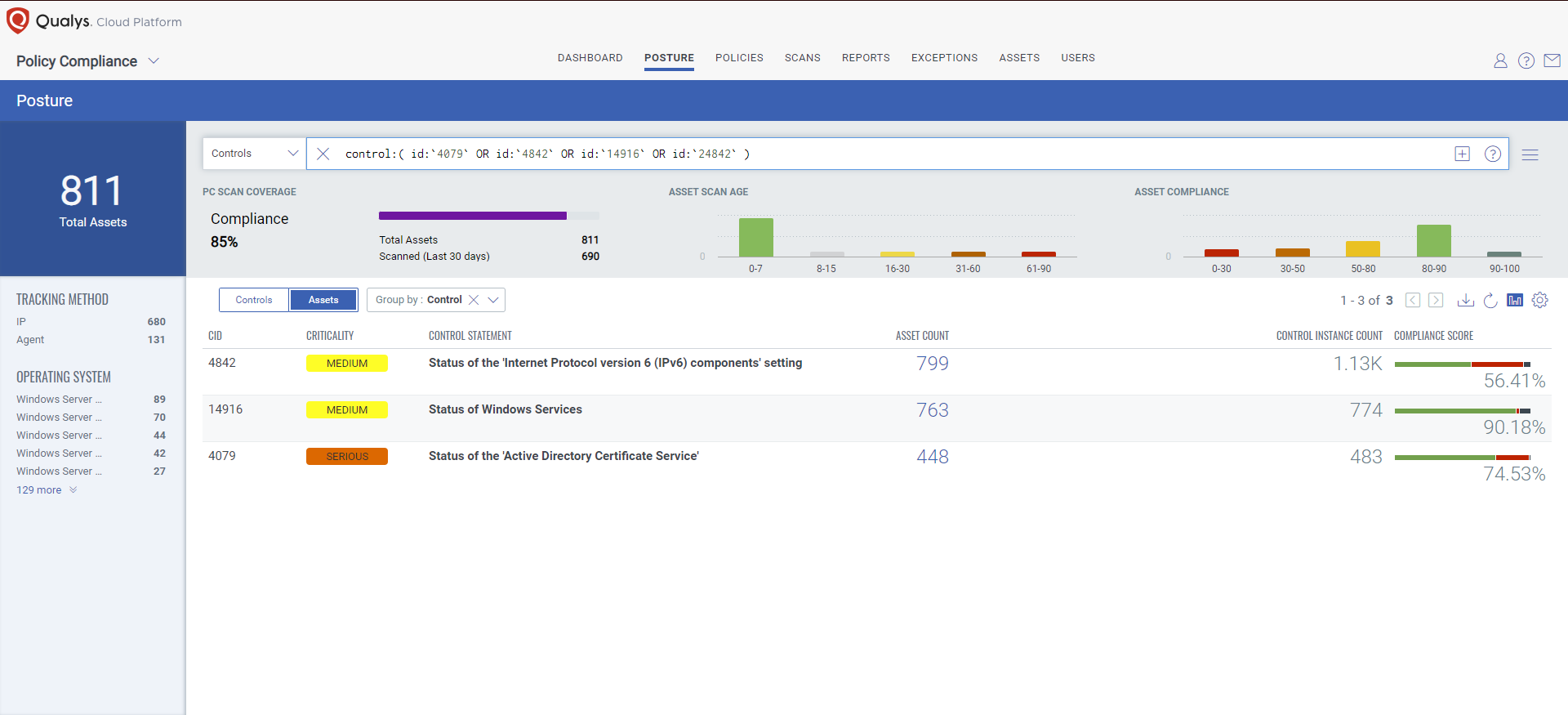
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2022-37976 | Active Directory Certificate Services Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
Policy Compliance Control IDs (CIDs):
- 4079 Status of the ‘Active Directory Certificate Service’
- 14916 Status of Windows Services
- 24842 Status of the ‘LegacyAuthenticationLevel’ setting
Exploitability Assessment: Exploitation Less Likely
CVE-2022-33645 | Windows TCP/IP Driver Denial of Service (DoS) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
Policy Compliance Control IDs (CIDs):
- 4842 Status of the ‘Internet Protocol version 6 (IPv6) components’ setting
Exploitability Assessment: Exploitation Less Likely
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
- Prepare Your Organization for Compliance with the NYDFS Cybersecurity Regulation
- Mitigating the Risk of Zero-Day Vulnerabilities by using Compensating Controls
- Policy Compliance (PC) | Policy Library Update Blogs
This Month in Vulnerabilities and Patches Webinar Series
The Qualys Product Management and Threat Research team members host a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, this month’s Patch Tuesday high-impact vulnerabilities will be discussed. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
UPCOMING EVENTS
The content within this section will spotlight upcoming Vulnerability Management, Patch Management, Threat Protection, Custom Assessment and Remediation, and Policy Compliance adjacent events available to our prospective, new, and existing customers.
WEBINAR
Introducing Qualys Workshop Wednesday
At Qualys Inc, providing cybersecurity through technology is what we do. Join us each month as we tap into the minds of Qualys experts to share how you can get the most out of your investment and understand ways in which you can quickly reduce your cyber risk exposure using the Qualys Cloud Platform. Each 45-minute monthly session, hosted on the first Wednesday of the month, will showcase practical hands-on tips and tricks, news on new capabilities and services, as well as useful customer success stories that can help you get the most out of the Qualys Cloud Platform.
Join us for the first Workshop Wednesday on Nov 2, 2022, at 9:00 AM PDT.
Qualys Threat Thursdays
The Qualys Threat Research team invites you to join their regular monthly webinar series covering the latest threat intelligence analysis and insight.
October 2022 Threat Thursday Topic is AsyncRAT.
Never miss an update. Subscribe Today!
Click Here to quickly navigate to Qualys Threat Thursday blog posts.
CONFERENCES
Qualys Annual Security Conference #QSC22
Qualys Security Conference (QSC) is a unique opportunity for the Qualys community to get together to hear the latest developments in cybersecurity, view the latest innovations from Qualys, trade best practices, share feedback, and learn tips and tricks on how security professionals work to keep their organizations secure.
We Are Pleased To Announce the Keynote Speaker for the 2022 Qualys Annual Security Conference in Las Vegas

Robert Herjavec is a globally recognized motivational, business, and cyber security leader. For the last 14 years, Robert has been well known as one of the Sharks, and executive producer of the Emmy Award-winning hit show, Shark Tank. He has served as a Cybersecurity Advisor for the Government of Canada, participated in the White House Summit on Cybersecurity, and is a member of the US Chamber of Commerce Task Force for Cybersecurity.
Robert’s keynote will highlight the growing importance of cybersecurity in today’s world.
Explore and secure the digital journey. Dive into the profound impact of the digital journey and explore how to build security automation from the data center to the cloud. Industry experts and Qualys leaders discuss automation strategies, preview product roadmaps, listen to your challenges, and answer your questions.
Get inspired. Engage with Qualys’ customer-facing teams and your peers around best practices and user case studies for applying security automation to real-world challenges.
Sharpen your expertise. Two days of free training cover forward-looking strategies, best practices to improve effectiveness and productivity, and core/expanded product features to up-level your security program.
Who Should Attend? CIOs, CSOs, and CTOs; directors and managers of network, security, and cloud; developers and DevSecOps practitioners; Qualys partners and consultants; or any forward-thinking security professional.
Live Training Sessions
November 7 and November 8
Live Conference Sessions
November 9 and November 1
Attendance at QSC is complimentary. This includes access to all general sessions, breakout sessions, breakfast, lunch, breaks, and receptions.
#QSC22 Location and Reservation Information
November 7-10, 2022
The Venetian Resort Las Vegas, 3355 Las Vegas Blvd. South, Las Vegas, NV 89109, US
Book your hotel here & take advantage of the discounted QSC rate of $229+ per night
Or find a conference near you.
This Month’s Blog Content Is the Result of Collaboration With and Contributions From:
In Order of Appearance:
- Quote: Ankit Malhotra, Manager, Signature Engineering
- Quote: Saeed Abbasi, Manager, Vulnerability Signatures
- QID Content: Arun Kethipelly, Manager, Signature Engineering
- QID Content: Dianfang (Sabrina) Gao, Lead, QA Engineer
- CAR Content: Mukesh Choudhary, Compliance Research Analyst
- CAR Content: Lavish Jhamb, Solution Architect, Compliance Solutions
- PC Content: Xiaoran (Alex) Dong, Manager, Compliance Signature Engineering
- Webinars: Thomas Nuth, Senior Director, Product Marketing
- Webinars: Nihal Adav, Email Marketing Specialist
- #QSCLV22 Content: Anna Moraleda, Sr. Marketing Events Specialist

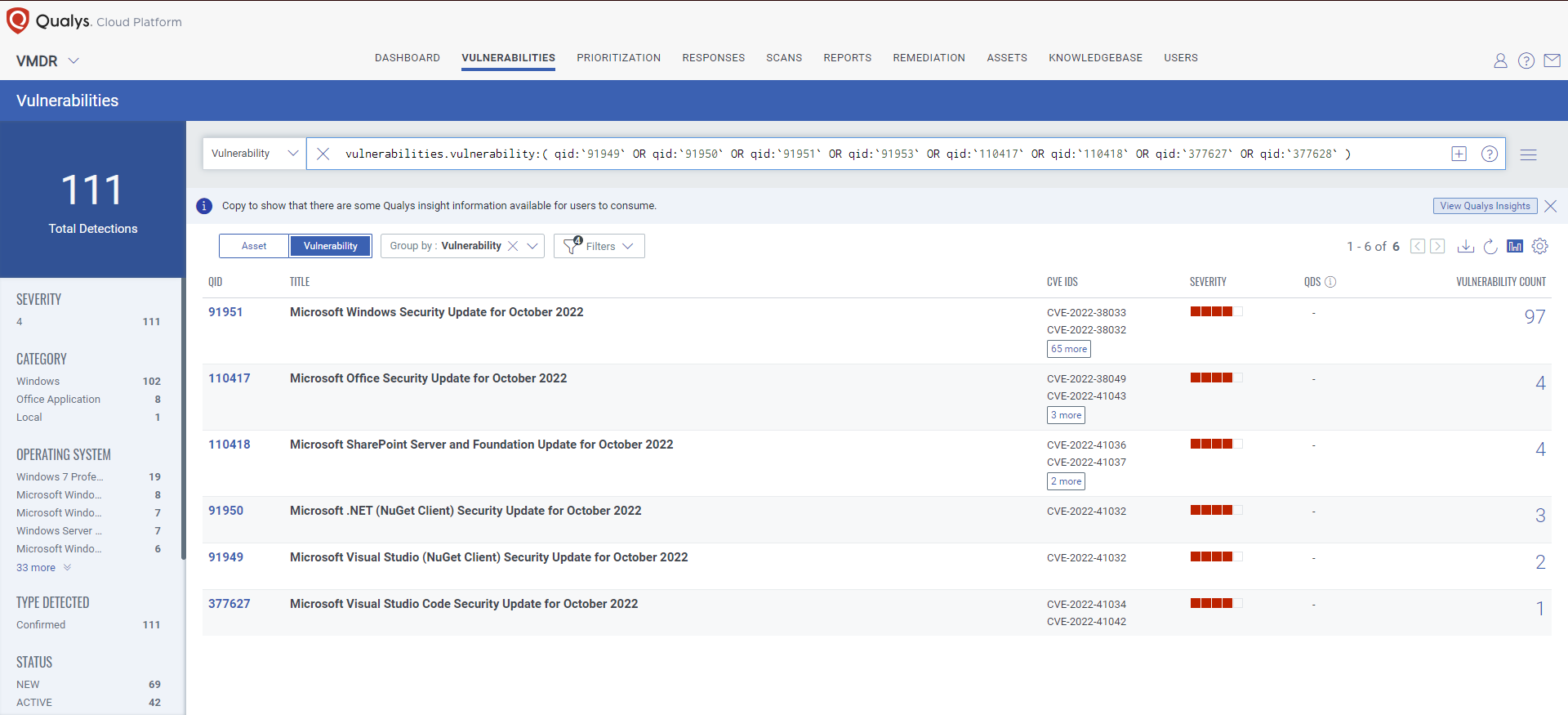



What is the QID for October 2022 “Exchange Server Security Updates “
ProxyNotShell which includes two actively exploited zero-day vulnerabilities is being tracked in Qualys as QID 50122 (CVE-2022-41040 and CVE-2022-41082).