November 2022 Patch Tuesday | Microsoft Releases 65 New Vulnerabilities With 10 Critical; Adobe Releases Zero Advisories (for the First Time in Six Years).
Table of Contents
- Microsoft Patch Tuesday Summary
- The November 2022 Microsoft Vulnerabilities are Classified as Follows:
- OpenSSL 3.x Critical Vulnerability Highlights
- OpenSSL 3.x Related Blogs and Resources
- Microsoft Addressed Six Zero-Day Vulnerabilities
- Microsoft Patch Tuesday Critical Vulnerability Highlights
- Microsoft Release Summary
- Adobe Security Bulletins and Advisories
- About Qualys Patch Tuesday
- Qualys Threat Research Blog Posts
- Qualys Threat Protection High-Rated Advisories
- Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response(VMDR)
- Rapid Response with Patch Management (PM)
- Extend the Power of VMDR to Enterprise Mobile Devices With Qualys VMDR Mobile
- Execute Mitigation UsingCustom Assessment and Remediation(CAR)
- Patch Tuesday Is Complete.
- This Month in Vulnerabilities and Patches Webinar Series
- UPCOMING EVENTS
- WEBINARS
- CONFERENCES
- Qualys Security Blog | Expert Network Security Guidance and News
- This Months Blog Content Is the Result of Collaboration With and Contributions From:
Microsoft Patch Tuesday Summary
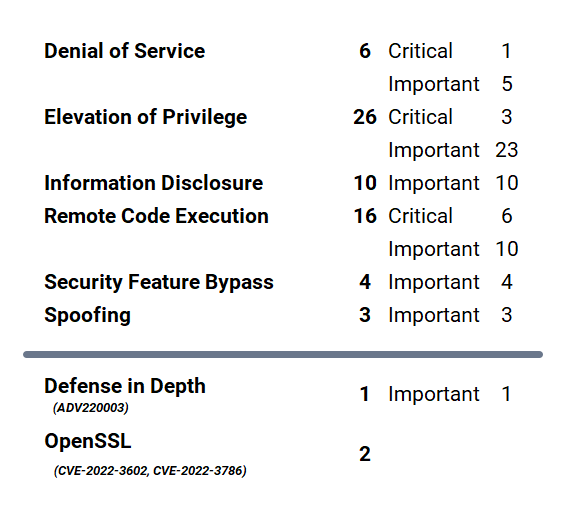
Microsoft has fixed 65 new vulnerabilities (aka flaws) in the November 2022 update, including ten (10) vulnerabilities classified as critical as they allow Denial of Service (DoS), Elevation of Privilege (EoP), and Remote Code Execution (RCE). This month’s Patch Tuesday included a Microsoft Defense in Depth Update (ADV220003) and addressed six (6) known exploited zero-day vulnerabilities. Earlier this month, on November 2, 2022, Microsoft also released two (2) advisories for OpenSSL 3.x for Azure SDK for C++, C++ Library Manager for Windows (vcpkg), and Microsoft Azure Kubernetes Service (CVE-2022-3602, CVE-2022-3786).
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution(RCE), Security Feature Bypass, and Spoofing.
The November 2022 Microsoft Vulnerabilities are Classified as Follows:
65 New CVEs on November 8th, two (2) CVEs on November 2nd,
and one (1) ADV220003.
OpenSSL 3.x Critical Vulnerability Highlights

CVE-2022-3602, CVE-2022-3786 | OpenSSL: X.509 Certificate Verification Buffer Overru
The vulnerability assigned to this CVE is in OpenSSL Software which is consumed by the Microsoft products listed in the Security Updates table and is known to be affected. It is being documented in the Security Update Guide to announce that the latest builds of these products are no longer vulnerable. Please see Security Update Guide Supports CVEs Assigned by Industry Partners for more information.
- For more information and guidance see Awareness and guidance related to OpenSSL 3.0 – 3.0.6 risk (CVE-2022-3786 and CVE-2202-3602).
- Products Affected: Azure SDK for C++, C++ Library Manager for Windows (vcpkg), and Microsoft Azure Kubernetes Service
OpenSSL 3.x Related Blogs and Resources
Microsoft Addressed Six Zero-Day Vulnerabilities
A vulnerability is classified as a zero-day if it is publicly disclosed or actively exploited with no official fix available.
Microsoft Exchange ProxyNotShell Zero-Day Fixed (CVE-2022-41040, CVE-2022 41082)
IMPORTANT: Qualys has updated QID 50122 – Microsoft Exchange Server Multiple Vulnerabilities (ProxyNotShell).
A rescan will be required to update existing detections with the updated Title, Threat, Solution, CVSSv2 Temporal Score, CVSSv3.1 Temporal Score, and multiple RTI updates including, but not limited to the addition of Exploit_Public, Unauthenticated_Exploitation, and Privilege_Escalation.
While CVE-2022-41040 and CVE-2022-41082 are not considered “new” advisories, per se, Microsoft has chosen to include them in their November 2022 Patch Tuesday release. The ProxyNotShell (CVE-2022-41040, CVE-2022-41082) advisories have been updated by Microsoft indicating that patches are now available along with this month’s Security Updates.
- Description of the security update for Microsoft Exchange Server 2019, 2016, and 2013: November 8, 2022 (KB5019758)
- Customer Guidance for Reported Zero-day Vulnerabilities in Microsoft Exchange Server
- Potential Impact HIGH for Confidentiality, Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Detected
CVE-2022-41128 | Windows Scripting Languages Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8 / 10.
This vulnerability affects the JScript9 scripting language, which is part of the component Scripting Language. Successful exploitation requires user interaction by the victim. The attack may be initiated remotely.
This vulnerability requires that a user with an affected version of Windows access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message.
- Potential Impact HIGH for Confidentiality, Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation Detected
CVE-2022-41073 | Windows Print Spooler Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 / 10.
The following content was corrected on 2022-11-26: Microsoft has not disclosed the technical details of this vulnerability in their advisory, stating only that an attacker who successfully exploited this Elevation of Privilege vulnerability could gain SYSTEM privileges. The advisory provides download links to address the flaw in 60 products.
- Potential Impact HIGH for Confidentiality, Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation Detected
CVE-2022-41125 | Windows CNG Key Isolation Service Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 / 10.
An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- Windows Next-generation Cryptography (CNG)
- Potential Impact HIGH for Confidentiality, Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Detected
CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 5.4 / 10.
The following content was corrected on 2022-11-26: An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office, which rely on MOTW tagging.
- In a web-based attack scenario, an attacker could host a malicious website that is designed to exploit the security feature bypass.
- In an email or instant message attack scenario, the attacker could send the targeted user a specially crafted .url file that is designed to exploit the bypass.
- Compromised websites or websites that accept or host user-provided content could contain specially crafted content to exploit the security feature bypass.
In all cases, an attacker would have no way to force a user to view the attacker-controlled content. Instead, an attacker would have to convince a user to take action. For example, an attacker could entice a user to either click a link that directs the user to the attacker’s site or send a malicious attachment.
Please see additional information about Mark of the Web for further clarification.
- Potential Impact LOW for Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation Detected
Microsoft Patch Tuesday Critical Vulnerability Highlights
CVE-2022-41080 | Microsoft Exchange Server Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8 / 10.
The technical details are unknown, and an exploit is not publicly available. Applying a patch can eliminate this problem. Customers are advised to update their Exchange Server systems immediately, regardless of whether any previously recommended mitigation steps have been applied. The mitigation rules are no longer recommended once systems have been patched.
- Potential Impact HIGH for Confidentiality, Integrity, and Availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
Exploitability Assessment: Exploitation More Likely
CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege (EoP) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 10.
Microsoft Released: Nov 8, 2022; Microsoft Last updated: Nov 17, 2022
Qualys blog updated Nov 26, 2022:
There is a known issue documented in the security updates that address this vulnerability, where Kerberos authentication might fail for user, computer, service, and GMSA accounts when serviced by Windows domain controllers that have installed Windows security updates released on November 8, 2022. Has an update been released that addresses this known issue?
Yes. The issue is addressed by out-of-band updates released to Microsoft Update Catalog on and after November 17, 2022. Customers who have not already installed the security updates released on November 8, 2022, should install the out-of-band updates instead. Customers who have already installed the November 8, 2022, Windows security updates and who are experiencing issues should install the out-of-band updates.
For more information about these updates, please see the OS version-specific info on Windows release health at the following links:
- https://learn.microsoft.com/en/windows/release-health/status-windows-11-22h2#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-11-21h2#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-server-2022#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-10-22h2#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-10-21h2#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-10-21h1#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-10-20h2#2953msgdesc
- https://learn.microsoft.com/en/windows/release-health/status-windows-10-1809-and-windows-server-2019#2953msgdesc
For more information please see the known issues section of How to manage the Kerberos Protocol changes related to CVE-2022-37966.
Successful exploitation of this vulnerability requires an attacker to gather information specific to the environment of the targeted component. An attacker who successfully exploited this vulnerability could gain administrator privileges. An unauthenticated attacker could conduct an attack that could leverage cryptographic protocol vulnerabilities in RFC 4757 (Kerberos encryption type RC4-HMAC-MD5) and MS-PAC (Privilege Attribute Certificate Data Structure specification) to bypass security features in a Windows AD environment.
- For more information, please see How to manage the Kerberos Protocol changes related to CVE-2022-37966.
- Potential Impact HIGH for confidentiality, integrity, and availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation More Likely
CVE-2022-41044 | Windows Point-to-Point Tunneling Protocol Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 10.
Successful exploitation of this vulnerability requires an attacker to win a race condition. An unauthenticated attacker could send a specially crafted connection request to a RAS server, which could lead to remote code execution (RCE) on the RAS server machine.
- Potential Impact HIGH for confidentiality, integrity, and availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation Less Likely
CVE-2022-41088 | Windows Point-to-Point Tunneling Protocol Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 10.
Successful exploitation of this vulnerability requires an attacker to win a race condition. This vulnerability requires that a user with an affected version of Windows access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message.
- Potential Impact HIGH for confidentiality, integrity, and availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation Less Likely
CVE-2022-41118 | Windows Scripting Languages Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5 / 10.
This vulnerability impacts both the JScript9 and Chakra scripting languages, which are both parts of the component Scripting Language. Successful exploitation requires user interaction by the victim. The attack may be initiated remotely.
This vulnerability requires that a user with an affected version of Windows access a malicious server. An attacker would have to host a specially crafted server share or website. An attacker would have no way to force users to visit this specially crafted server share or website, but would have to convince them to visit the server share or website, typically by way of an enticement in an email or chat message.
- Potential Impact HIGH for confidentiality, integrity, and availability.
- A complete vendor solution is available. Either the vendor has issued an official patch, or an upgrade is available.
- Extended Security Updates (ESU) Vulnerability
Exploitability Assessment: Exploitation More Likely
Microsoft Release Summary
This month’s Release Notes cover multiple Microsoft product families, including Azure, Developer Tools, Extended Security Updates (ESU), Microsoft Dynamics, Microsoft Office, Open Source Software, and Windows.
A total of 39 unique Microsoft products, features, and roles, including but not limited to Azure CLI, Microsoft Exchange Server Cumulative Update, Windows Endpoint, Windows Server, and Windows Server 2022 Datacenter: Azure Edition (Hotpatch) were included in this release.
Downloads include Cumulative Updates, IE Cumulative, Monthly Rollups, Security Hotpatch Updates, Security Only, and Security Updates.
Adobe Security Bulletins and Advisories
For November 2022, Adobe released no patches at all. They’ve released as few as one in the past, but this is the first month in the last six years where they had no fixes at all. Source
About Qualys Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts typically late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard by 1 pm PT on Wednesday.
Qualys Microsoft Security Alert, November 8, 2022
| QID | TITLE |
|---|---|
| 48223 | Microsoft Exchange Server Uniform Resource Locator (URL) Rewrite Mitigation Applied for ProxyNotShell |
| 50122 | Microsoft Exchange Server Multiple Vulnerabilities (ProxyNotShell) |
| 50123 | Microsoft Exchange Server Multiple Vulnerabilities for November 2022 |
| 91954 | Microsoft .NET Framework Information Disclosure Vulnerability for November 2022 |
| 91956 | Microsoft Windows Security Update for November 2022 |
| 91957 | Microsoft Windows Server Elevation of Privilege Vulnerability for November 2022 |
| 91958 | Microsoft Dynamics Business Central Information Disclosure Vulnerability for November 2022 |
| 91959 | Microsoft Azure Stack Hub Security Updates for November 2022 |
| 91960 | Microsoft Visual Studio Security Updates for November 2022 |
| 110419 | Microsoft Office Security Update for November 2022 |
| 110420 | Microsoft SharePoint Server and Foundation Update for November 2022 |
Qualys Threat Research Blog Posts
- OpenSSL Vulnerability Recap
- Qualys Research Alert: OpenSSL 3.0.7 – What You Need To Know
- Qualys Research Team: Threat Thursdays, October 2022
- Text4Shell: Detect, Prioritize and Remediate The Risk Across On-premise, Cloud, Container Environment Using Qualys Platform
- Leeloo Multipath: Authorization bypass and symlink attack in multipathd (CVE-2022-41974 and CVE-2022-41973)
- CVE-2022-42889: Detect Text4Shell via Qualys Container Security
- Creating Awareness of External JavaScript Libraries in Web Applications
- JSON Web Token (JWT) Weaknesses
Qualys Threat Protection High-Rated Advisories
- Open Secure Sockets Layer (OpenSSL) Patches High Severity Vulnerabilities (CVE-2022-3602 and CVE-2022-3786)
- Google Patches Zero-day vulnerability in Chrome Browser (CVE-2022-3723)
- Google Chrome Releases New Version to Address Multiple Vulnerabilities
- Oracle Releases 370 Security Patches for Various Oracle Products in October 2022 Patch Tuesday
- Apache Commons Arbitrary Code Execution Vulnerability (Text4Shell) (CVE-2022-42889)
Free Trial
Get started with 30-day Free Trial
Discover and Prioritize Vulnerabilities in Vulnerability Management Detection Response (VMDR)
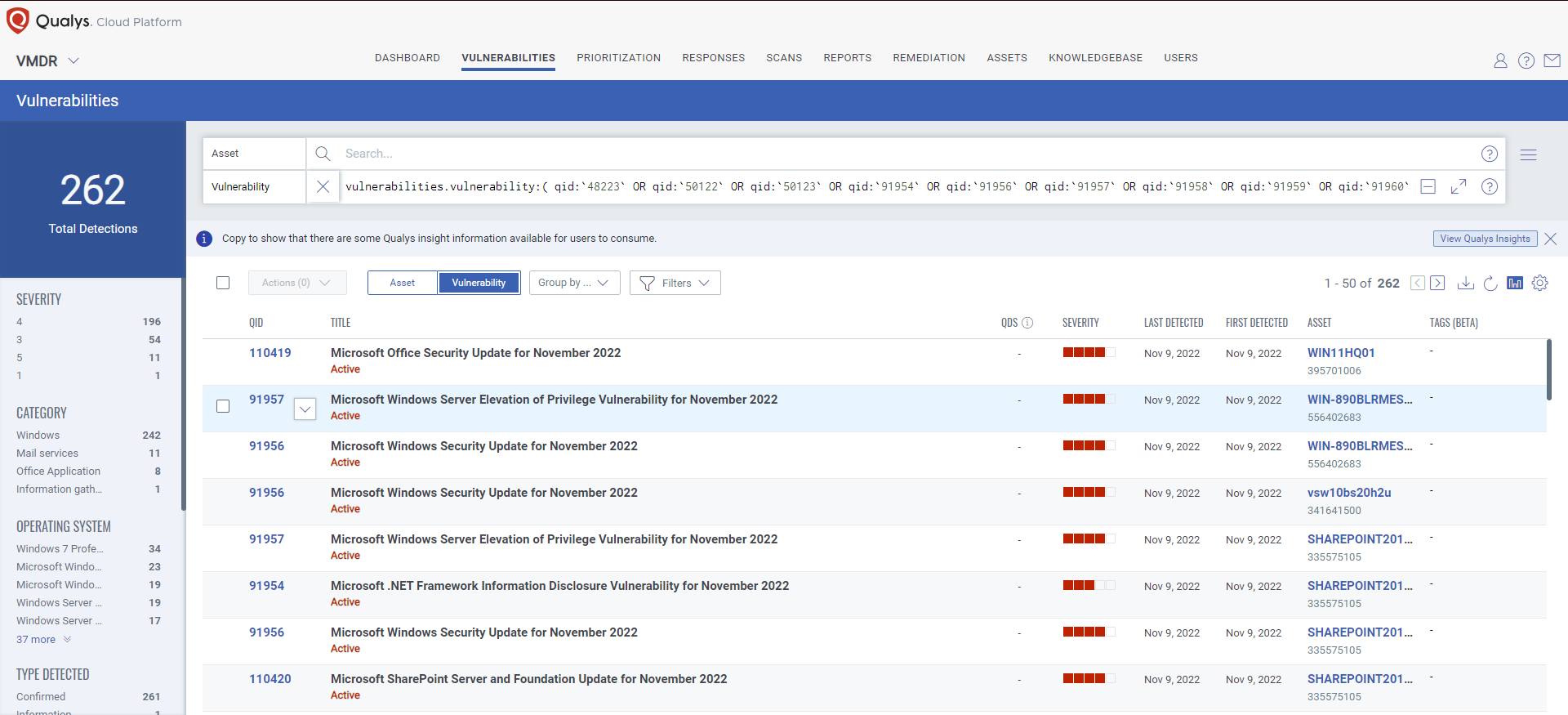
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its KnowledgeBase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
- In-Depth Look Into Data-Driven Science Behind Qualys TruRisk
- Qualys VMDR Recognized as Best VM Solution by SC Awards 2022 & Leader by GigaOm
- A Deep Dive into VMDR 2.0 with Qualys TruRisk™
Free Trial
Get started with 30-day Free Trial
Rapid Response with Patch Management (PM)
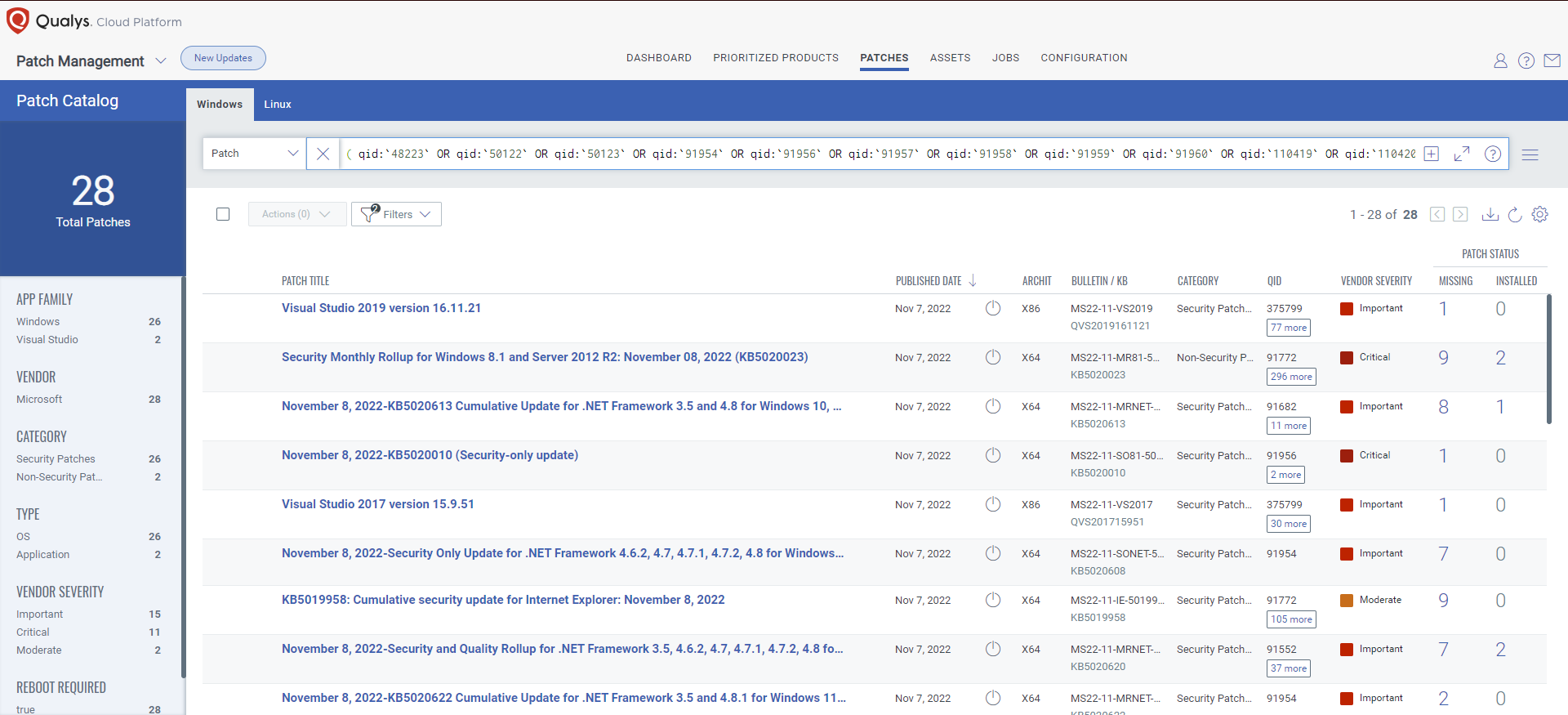
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
- Get Your Patch Tuesday Vulnerabilities Patched on Tuesday
- Why Organizations Struggle with Patch Management (and What to Do about It)
- Let Smart Automation Reduce the Risk of Zero-Day Attacks on Third-Party Applications
- Risk-based Remediation Powered by Patch Management in Qualys VMDR 2.0
Free Trial
Get started with 30-day Free Trial
Extend the Power of VMDR to Enterprise Mobile Devices With Qualys VMDR Mobile
Qualys VMDR for enterprise mobile devices provides comprehensive visibility and continuously assesses device, OS, apps, and network vulnerabilities including critical device configurations of mobile devices across your enterprise.
As mobile devices have become ubiquitous in almost every business process, whether in bank branches, manufacturing sites, or retail stores, they are now hosting business applications and data that is subject to regulatory compliance and security. With access to critical corporate resources inside the corporate network, these mobile devices have become critical assets for organizations, and organizations are facing a new set of security challenges and risks.
| QID | Title |
|---|---|
| 610439 | Google Android October 2022 Security Patch Missing for Huawei EMUI |
| 610440 | Apple iOS 15.7.1 and iPadOS 15.7.1 Security Update Missing |
| 610438 | Google Android October 2022 Security Patch Missing for Samsung |
| 610436 | Google Pixel Android October 2022 Security Patch Missing |
| 610437 | Google Android Devices October 2022 Security Patch Missing |
| 610441 | Apple iOS 16.1 and iPadOS 16 Security Update Missing |
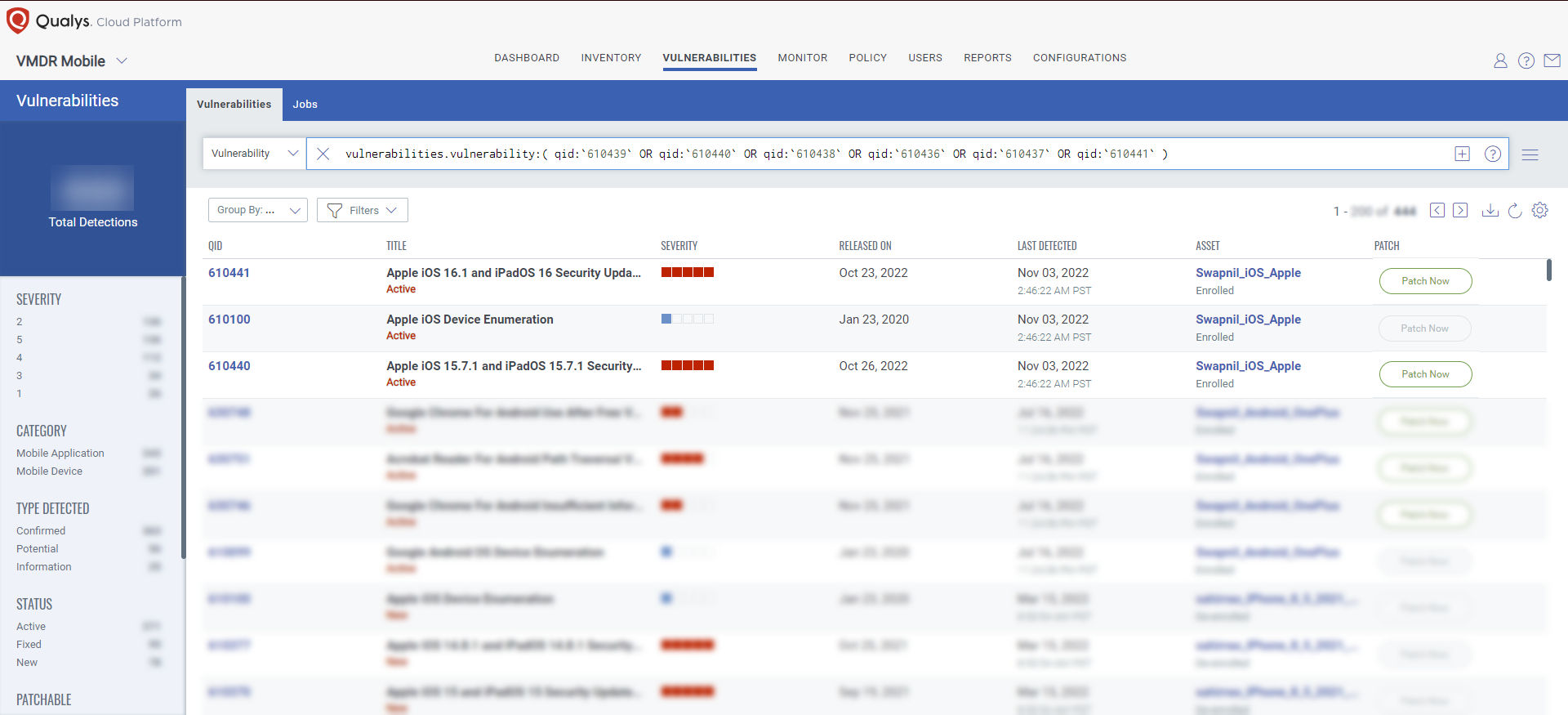
Qualys’ Vulnerability Management, Detection, and Response (VMDR) solution extends its power to mobile devices. It provides an in-depth inventory of mobile devices, real-time visibility into vulnerabilities and critical device settings, and built-in remediation with patch orchestration for all Android and iOS/iPadOS devices across the enterprise. An end-to-end solution for mobile device security.
You can visualize all your impacted mobile devices with vulnerabilities using the following QQL query:
VMDR Mobile Blogs | Qualys, Inc.
Qualys VMDR Mobile User Guide Version 1.5.0 (June 20, 2022) | Qualys, Inc > Documentation
VMDR Mobile is an out-of-the-box solution that’s centrally managed and self-updating.
Execute Mitigation Using Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation empowers a system administrator to quickly and easily perform configuration updates on your technology infrastructure when the current situation requires the implementation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best-practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
Customers can perform the provided mitigation steps by creating a PowerShell script and executing the script on vulnerable assets.
IMPORTANT: Scripts tend to change over time. Please refer to the Qualys GitHub Tuesday Patch link to ensure the most current version of a given Patch Tuesday script is in use.
CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.2 / 10.
Exploitability Assessment: Exploitation More Likely
Take Action > KB5020805: How to manage Kerberos protocol changes related to CVE-2022-37967
To help protect your environment and prevent outages, we recommend that you take the following steps:
- UPDATE your Windows domain controllers with a Windows update released on or after November 8, 2022.
- MOVE your Windows domain controllers to Audit mode by using the Registry Key setting section.
- MONITOR events filed during Audit mode to secure your environment.
- ENABLE Enforcement mode to address CVE-2022-37967 in your environment.
NOTE: Step 1 of installing updates released on or after November 8, 2022, will not address the security issues in CVE-2022-37967 for Windows devices by default. To fully mitigate the security issue for all devices, you must move to Audit mode (described in Step 2) followed by Enforcement Mode (described in Step 4) as soon as possible on all Windows domain controllers.
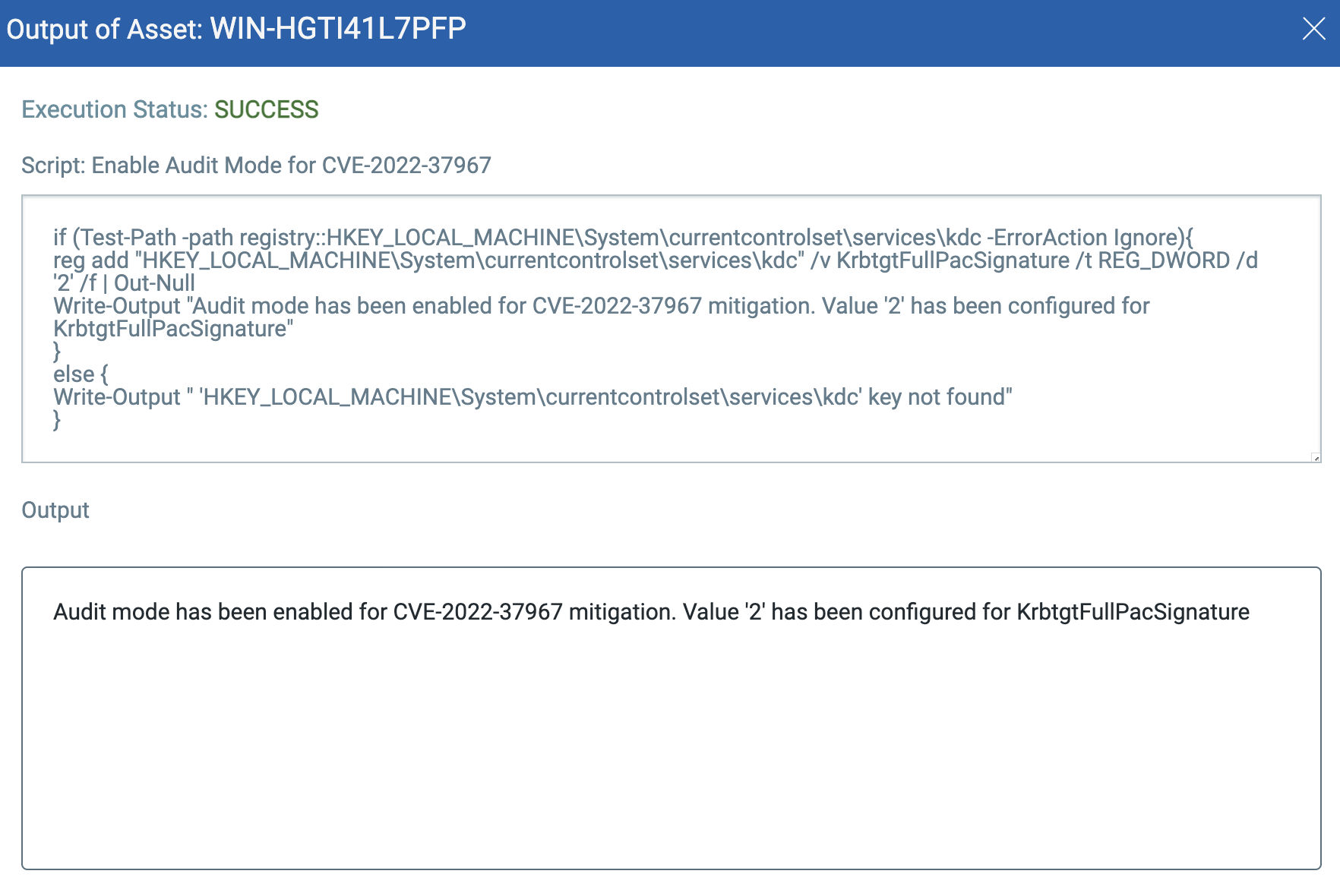
Leverage Custom Assessment and Remediation for CVE-2022-37967 Kerberos EOP Vuln to Execute Step #2: Enable Audit Mode:
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc -ErrorAction Ignore){ reg add "HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc" /v KrbtgtFullPacSignature /t REG_DWORD /d '2' /f | Out-Null Write-Output "Audit mode has been enabled for CVE-2022-37967 mitigation. Value '2' has been configured for KrbtgtFullPacSignature" } else { Write-Output " 'HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc' key not found" }
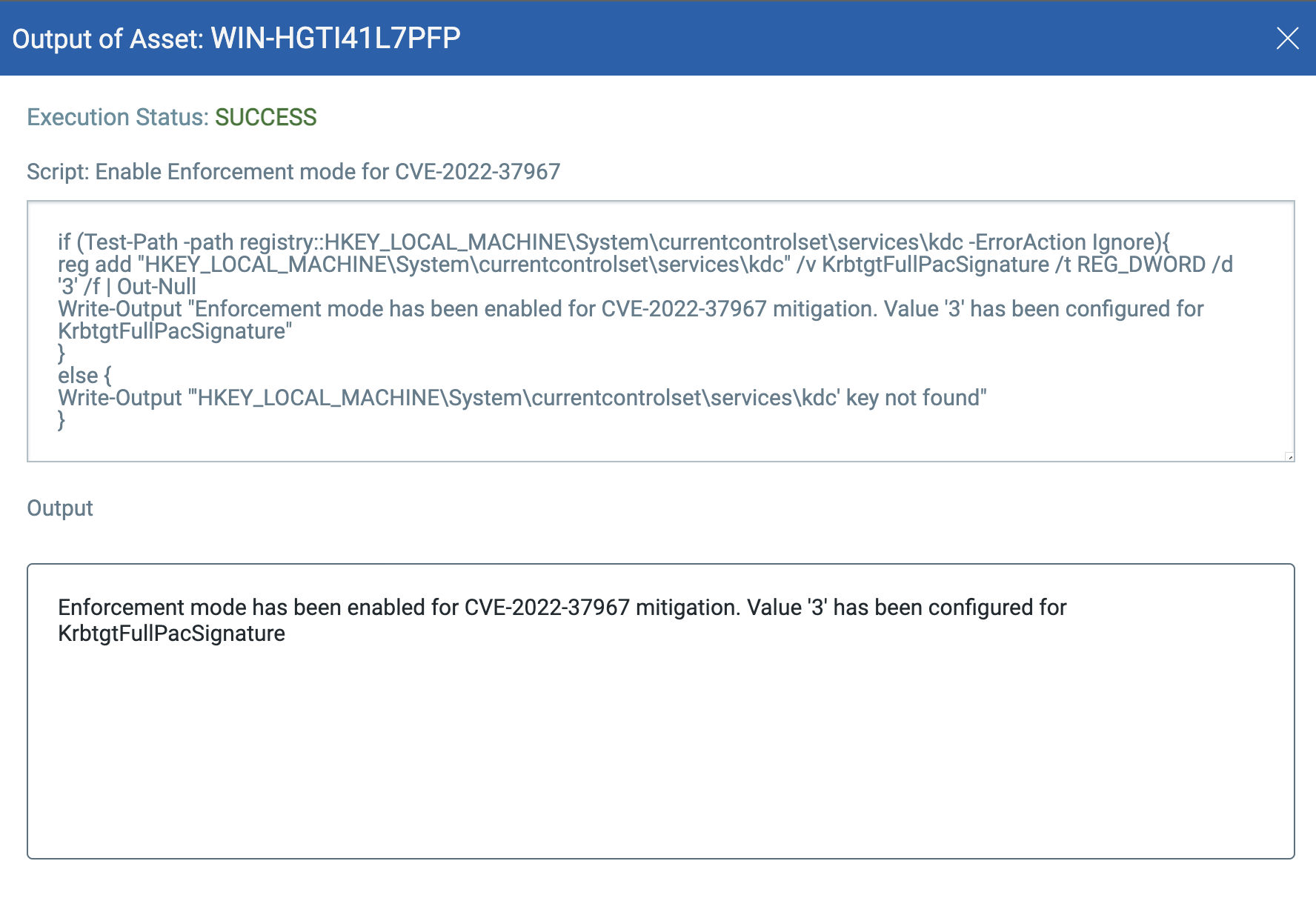
Leverage Custom Assessment and Remediation for CVE-2022-37967 Kerberos EOP Vuln to Execute Step #4: Enable Enforcement Mode:
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc -ErrorAction Ignore){ reg add "HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc" /v KrbtgtFullPacSignature /t REG_DWORD /d '3' /f | Out-Null Write-Output "Enforcement mode has been enabled for CVE-2022-37967 mitigation. Value '3' has been configured for KrbtgtFullPacSignature" } else { Write-Output "'HKEY_LOCAL_MACHINE\System\currentcontrolset\services\kdc' key not found" }
CVE-2022-38023 | Netlogon RPC Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 10.
Exploitability Assessment: Exploitation More Likely
Note: This update protects Windows devices from CVE-2022-38023 by default. For third-party clients and third-party domain controllers, the update is in Compatibility mode by default and allows vulnerable connections from such clients. Refer to the Registry Key settings section for steps to move to Enforcement mode.
Leverage Custom Assessment and Remediation for CVE-2022-38023 – Netlogon RPC EOP Vuln to Enable Enforcement Mode:
if (Test-Path -path registry::HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters -ErrorAction Ignore){ reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters" /v RequireSeal /t REG_DWORD /d '2' /f | Out-Null Write-Output "Enforcement mode has been enabled for CVE-2022-38023 mitigation for third-party clients and third-party domain controllers. Value '2' has been configured for RequireSeal" } else { Write-Output "'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters' key not found" }

Free Trial
Get started with 30-day Free Trial
EVALUATE Vendor-Suggested Mitigation With Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best-practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.2 / 10.
Policy Compliance Control IDs (CIDs):
- 25167 Status of the ‘KrbtgtFullPacSignature’ setting for the Kerberos
As per KB5020805, this mitigation should be applied after the patch
NOTE: To help protect your environment and prevent outages, we have outlined the Qualys recommended remediation steps above and provided Qualys Custom Assessment and Remediation (CAR) supporting scripts.
Exploitability Assessment: Exploitation More Likely
CVE-2022-38023 | Netlogon RPC Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1 / 10.
Policy Compliance Control IDs (CIDs):
- 25168 Status of the ‘RequireSeal’ setting for the Netlogon Remote Protocol
As per KB5021130, this mitigation should be applied after the patch
NOTE: To help protect your environment and prevent outages, we have outlined the Qualys recommended remediation steps above and provided Qualys Custom Assessment and Remediation (CAR) supporting scripts.
Exploitability Assessment: Exploitation More Likely
Free Trial
Get started with 30-day Free Trial
Patch Tuesday Is Complete.
This Month in Vulnerabilities and Patches Webinar Series
The Qualys Product Management and Threat Research team members host a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, this month’s Patch Tuesday high-impact vulnerabilities will be discussed. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
UPCOMING EVENTS
The content within this section will spotlight upcoming Vulnerability Management, Patch Management, Threat Protection, Custom Assessment and Remediation, and Policy Compliance adjacent events available to our prospective, new, and existing customers.
WEBINARS
Qualys Workshop Wednesday
At Qualys Inc, providing cybersecurity through technology is what we do. Join us each month as we tap into the minds of Qualys experts to share how you can get the most out of your investment and understand ways in which you can quickly reduce your cyber risk exposure using the Qualys Cloud Platform. Each 45-minute monthly session, hosted on the first Wednesday of the month, will showcase practical hands-on tips and tricks, news on new capabilities and services, as well as useful customer success stories that can help you get the most out of the Qualys Cloud Platform.
Qualys Threat Thursdays
The Qualys Threat Research team invites you to join their regular monthly webinar series covering the latest threat intelligence analysis and insight.
Never miss an update. Subscribe Today!
Click Here to quickly navigate to Qualys Threat Thursday blog posts.
CONFERENCES

Sessions and Keynotes will be available on the Qualys site in the coming days.
Qualys Security Blog | Expert Network Security Guidance and News

This Month’s Blog Content Is the Result of Collaboration With and Contributions From:
In order of appearance
- Quote: Travis Smith VP, Malware Threat Research, Qualys
- QID Content: Arun Kethipelly, Manager, Signature Engineering
- QID Content: Dianfang (Sabrina) Gao, Lead, QA Engineer
- VMDR Mobile Content: Swapnil Ahirrao, Principal Product Manager, VMDR
- VMDR Mobile Content: Swapnil Bhoskar, Lead, Security Signature Engineer
- CAR Content: Mukesh Choudhary, Compliance Research Analyst
- CAR Content: Lavish Jhamb, Solution Architect, Compliance Solutions
- PC Content: Xiaoran (Alex) Dong, Manager, Compliance Signature Engineering